DDoS: It’s Not a Matter of If, But When

A distributed-denial-of-service or DDoS attack is a cyber-attack that renders a machine or network resource that is connected to the Internet temporarily unreachable to its intended users. The attacker’s goal is to disrupt business by consuming your Internet bandwidth and/or slowing your systems to the point of inaccessibility.
In a DDoS attack, a perpetrator uses one or more Internet connections to exploit a software vulnerability or flood the target with fake requests. This causes that site to be made unavailable and prevents it from responding to requests from legitimate users.
Why DDoS?
An attacker may use a DDoS attack to extort money—for blackmail or as a paid hacktivist (yes, there are even DDoS-as-a-service!). Others do it as a political protest like the attack on the DreamHost hosting provider on a libertarian website. Sometimes, DDoS attacks are initiated as a distraction to hide other malicious activities.
How common are DDoS attacks?
One thing is for sure, cyber-crimes are on the rise and DDoS attacks are among the most common. About half of all companies today have been victims of DDoS attacks, temporarily bringing business to a halt. Organizations such as online retailers, real-time services companies, and banks that have a heavy web services component or depend on internal network services are frequent targets. In 2017, DDoS attacks increased by 91% and they continue to grow in terms of scope, frequency and complexity, making them harder and harder to fend off.
Three types of DDoS attacks
In addition to causing so much damage, one of the biggest challenges with DDoS attacks is that they are so varied and nuanced. There are many, many varieties to contend with, but they fall into three main categories:
Volumetric Attacks
Volumetric or network attacks saturate the bandwidth of the target site, making it unreachable. Examples of volumetric attacks include DNS and NTP amplification, UDP floods, ICMP floods, and other spoofed-packet floods.
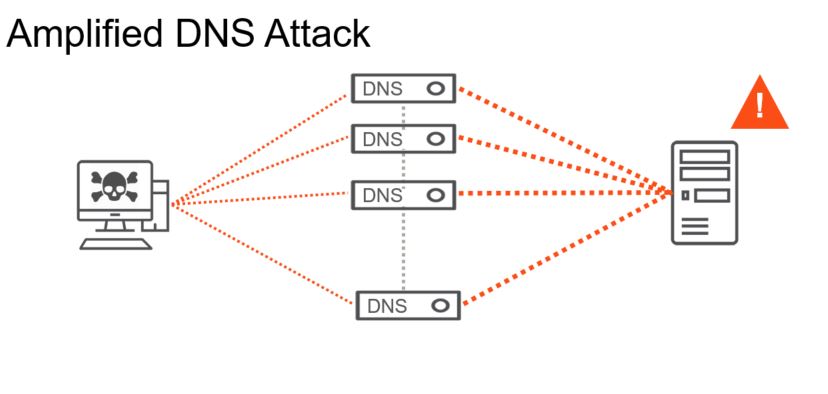
Amplified DNS attack is an example of a volumetric DDoS attack.
Using DNS as an example volumetric attack, an attacker sends DNS requests to multiple public DNS servers, using the target’s IP address as the source IP. All the DNS servers then respond to the target, overwhelming it. This works because UDP does not validate the source IP addresses. As such, it is easy to forge the IP addresses to include any arbitrary IP address as the source.
Protocol Attacks
Protocol attacks consume server resources or the intermediate communication equipment resources, such as firewalls and load balancers. Protocol attacks include attacks like Ping of Death, Smurf DDoS, SYN floods, and fragmented packet attacks.
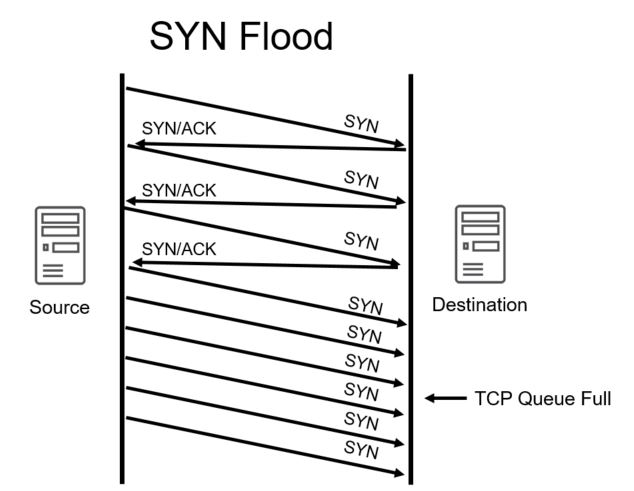
SYN Flood is an example of a protocol-based DDoS attack.
The most commonly used attack method is the protocol-based DDoS attack SYN Flood. This attack exploits the TCP handshake by sending the target a large number of TCP “Initial Connection Request” SYN packets with a spoofed source IP addresses. The target machine responds to each connection request and then waits for the final step in the handshake—the ACK—to be sent, which never occurs. When this waiting consumes enough server resources, it makes the system unresponsive to legitimate traffic.
Application-layer Attacks
Application Level attacks exploit vulnerabilities in applications. The goal of this type of attack is not to go after the entire server, but target applications with known weaknesses. Examples of application-layer attacks include low-and-slow attacks, like Slowloris and R.U.D.Y., GET/POST floods, attacks that target Apache, Windows or OpenBSD vulnerabilities, and more.
Hackers consider many application-layer attacks to be “low and slow” attacks. Low and slow attacks rely on a small stream of slow or infrequent traffic that can target application or server resources. Unlike more traditional brute-force attacks, low and slow attacks require very little bandwidth and can be hard to mitigate as they generate traffic that is seemingly legitimate and is therefore very difficult to distinguish from normal traffic. Because they don’t require many resources to pull off, low and slow attacks can be successfully launched using a single computer.
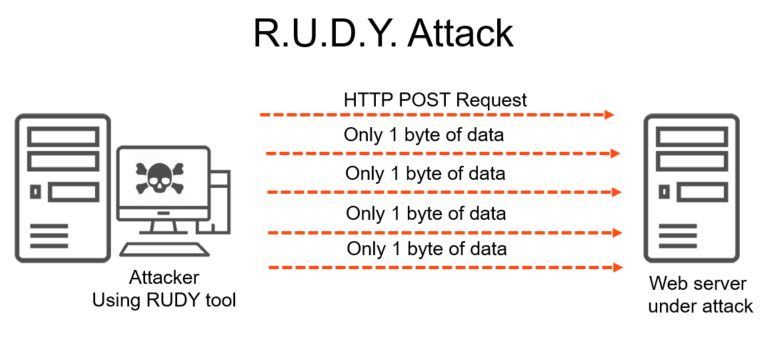
R.U.D.Y which stands for “aRe yoU Dead Yet?” is an example of an application type DDoS attack.
An example of an application-layer attack is R.U.D.Y., which is short for R U Dead yet. This is a DoS (denial-of-service) tool used to perform a “low and slow” attack by directing long form fields to the targeted server. The R.U.D.Y. attack opens concurrent POST HTTP connections to the HTTP server and delays sending the body of the POST request to the point that the server resources are saturated. This attack sends numerous small packets at a very slow rate to keep the connection open and the server busy. Hence the name “low and slow.”
How do you protect against DDoS attacks?
Protecting your business from security threats should be a crucial part of securing your business. During a DDoS attack, you need to be able to identify what is under attack, where is it coming from, and which attack variations are being used. To defend your organization against an array of DDoS attacks, you should deploy an approach that automates the attack vector detection, identification and mitigation processes.
SteelCentral NetProfiler Advanced Security Module detects a large range of DDoS attacks within 10 to 30 seconds and can strategically trigger mitigations. It characterizes the exact type and target of the attack and gives precise instructions to the mitigation solution of your choice. This ensures that you drop only the DDoS traffic so that your service remains up and available to your employees, partners, and customers.
Learn more about how SteelCentral NetProfiler Advance Security Module detects DDoS or other cyber security threats.
Also, check out this white paper: Never Fall Victim to DDoS

