How CASB and EDR Protect Federal Agencies in the Age of Work from Home
McAfee’s global network of over a billion threat sensors affords its threat researchers the unique advantage of being able to thoroughly analyze dozens of cyber-attacks of this kind. Based on this analysis, McAfee supports CISA’s recommendations to help prevent adversaries from successfully establishing persistence in agencies’ networks, executing malware, and exfiltrating data. However, McAfee also asserts that the nature of this environment demands that additional countermeasures be implemented to quickly detect, block and respond to exploits originating from authorized cloud services.

Malicious actors are increasingly taking advantage of the burgeoning at-home workforce and expanding use of cloud services to deliver malware and gain access to sensitive data. According to an Analysis Report (AR20-268A) from the Cybersecurity and Infrastructure Security Agency (CISA), this new normal work environment has put federal agencies at risk of falling victim to cyber-attacks that exploit their use of Microsoft Office 365 (O365) and misuse their VPN remote access services.
The Anatomy of a Cloud Services Attack
McAfee’s analysis supports CISA’s findings that adversaries frequently attempt to gain access to organizations’ networks by obtaining valid access credentials for multiple users’ O365 accounts and domain administrator accounts, often via vulnerabilities in unpatched VPN servers. The threat actor will then use the credentials to log into a user’s O365 account from an anomalous IP address, browse pages on SharePoint sites, and then attempt to download content. Next, the cyberthreat actor would connect multiple times from a different IP address to the agency’s Virtual Private Network (VPN) server, and eventually connect successfully.
Read on to learn from McAfee’s analysis of these attacks and understand how federal agencies can use cloud access security broker (CASB) and endpoint threat detection and response (EDR) solutions to detect and mitigate such attacks before they have a chance to inflict serious damage upon their organizations.
- Begin performing discovery and enumerating the network
- Establish persistence in the network
- Execute local command line processes and multi-stage malware on a file server
- Exfiltrate data
Basic SOC Best Practices
McAfee’s comprehensive analysis of these attacks supports CISA’s proposed best practices to prevent or mitigate such cyber-attacks. These recommendations include:
Once inside the network, the attacker could:
Why Best Practices Should Include CASB and EDR
Organizations will gain a running start to identifying and thwarting the attacks in question by implementing a full-featured CASB such as McAfee MVISION Cloud, and an advanced EDR solution, such as McAfee MVISION Endpoint Threat Detection and Response.
- Hardening account credentials with multi-factor authentication,
- Implementing the principle of “least privilege” for data access,
- Monitoring network traffic for unusual activity,
- Patching early and often.
While these recommendations provide a solid foundation for a strong cybersecurity program, these controls by themselves may not go far enough to prevent more sophisticated adversaries from exploiting and weaponizing cloud services to gain a foothold within an enterprise.
When specific anomalies appear concurrently—e.g., a Brute Force anomaly and an unusual Data Access event—MVISION Cloud automatically generates a Threat. In the attacks McAfee analyzed, Threats would have been generated early on since the CASB’s user behavior analytics would have identified the cyber actor’s various activities as suspicious. Using MVISION Cloud’s activity monitoring dashboard and built-in audit trail of all user and administrator activities, SOC analysts can detect and analyze anomalous behaviors across multiple dimensions to more rapidly understand what exactly is occurring when and to what systems—and whether an incident concerns a compromised account, insider threat, privileged user threat, and/or malware—to shrink the gap to remediation.
Deploying MVISION Cloud for Office 365 enables agencies’ SOC analysts to assert greater control over their data and user activity in Office 365—control that can hasten identification of compromised accounts and resolution of threats. MVISION Cloud takes note of all user and administrative activity occurring within cloud services and compares it to a threshold based either on the user’s specific behavior or the norm for the entire organization. If an activity exceeds the threshold, it generates an anomaly notification. For instance, using geo-location analytics to visualize global access patterns, MVISION Cloud can immediately alert agency analysts to anomalies such as instances of Office 365 access originating from IP addresses located in atypical geographic areas.
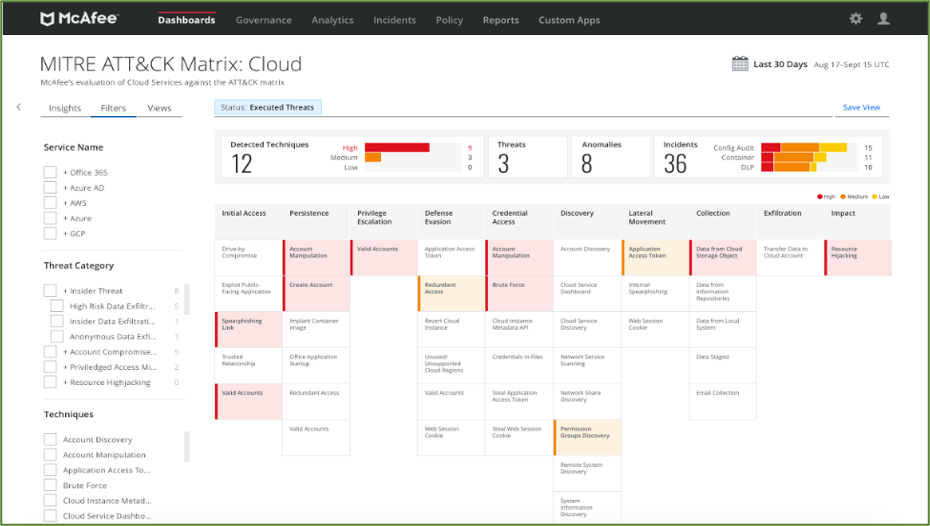
In addition, with MVISION Cloud, an agency security analyst can clearly see how each cloud security incident maps to MITRE ATT&CK tactics and techniques, which not only accelerates the entire forensics process but also allows security managers to defend against similar attacks with greater precision in the future.
Furthermore, using MVISION Cloud for Office 365, agencies can create and enforce policies that prevent the uploading of sensitive data to Office 365 or downloading of sensitive data to unmanaged devices. With such policies in place, an attacker’s attempt to exfiltrate sensitive data will be mitigated.
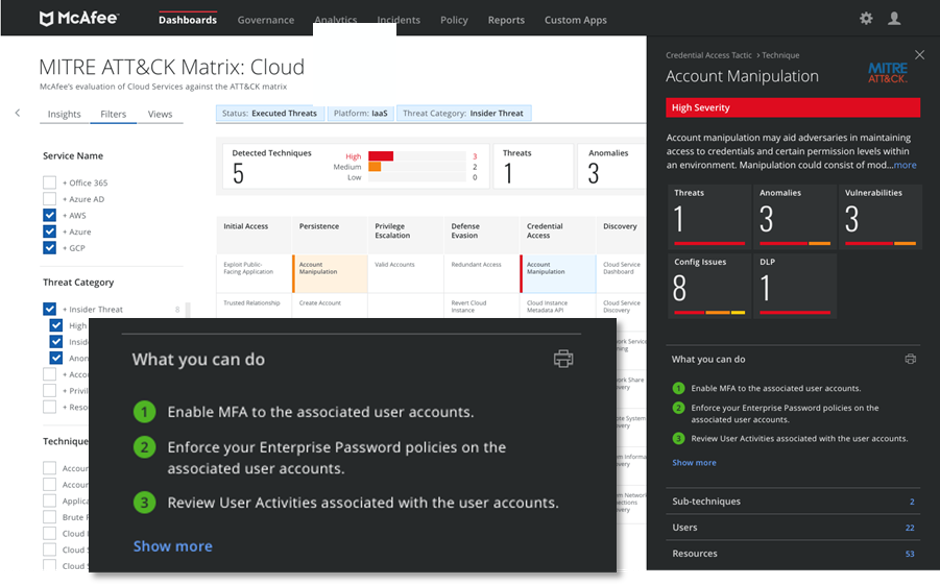
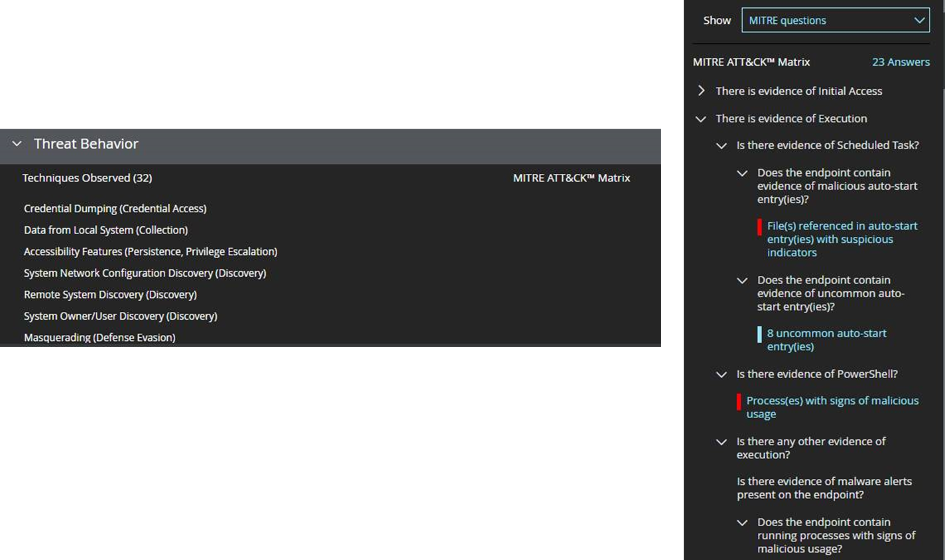
With a threat landscape that is constantly evolving and attack surfaces that continue to expand with increased use of the cloud, it is now more important than ever to embrace CASB and EDR solutions. They have become critical tools to actively defend today’s government agencies and other large enterprises.
In addition to deploying a CASB, implementing an EDR solution like McAfee MVISION EDR to monitor endpoints centrally and continuously—including remote devices—helps organizations defend themselves from such attacks. With MVISION EDR, agency SOC analysts have at their fingertips advanced analytics and visualizations that broaden detection of unusual behavior and anomalies on the endpoint. They are also able to grasp the implications of alerts more quickly since the information is presented in a format that reduces noise and simplifies investigation—so much so that even novice analysts can analyze at a higher level. AI-guided investigations within the solution can also provide further insights into attacks.
The post How CASB and EDR Protect Federal Agencies in the Age of Work from Home appeared first on McAfee Blogs.
Learn more about the cloud-native, unified McAfee MVISION product family. Get your questions answered by tweeting @McAfee
This post was first first published on Enterprise – McAfee Blogs’s website by John Amorosi. You can view it by clicking here

