Uber Hack – What we know so far
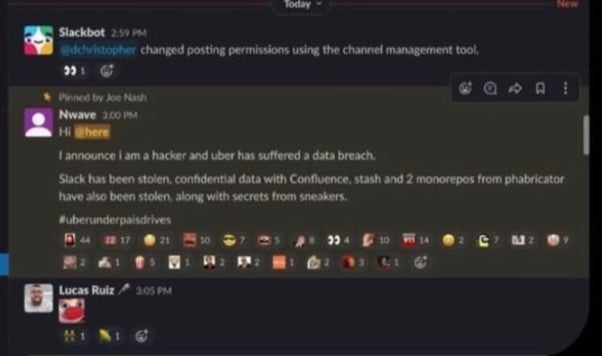
Inside the internal intranet were some PowerShell scripts that the attacker supposedly used to access core services such as AWS, Slack and SentinelOne administrator accounts. The attacker in question used the following hashtag when they posted into the Slack channel:
The hack has reportedly left multiple production systems down and internal employees unable to use the company’s main communication tool, Slack. Allegedly, the initial intrusion was orchestrated through social engineering, using a ‘MFA Fatigue’ technique to spam an internal employee with multiple multi-factor authentication prompts, until the internal employee hits accept to make the prompts disappear. Once inside, the attacker alleges (via a Telegram account that was referenced in the attack itself) that they logged into the VPN and scanned the internal intranet.
This may signal some intentions behind the attack, or be intended as a form of hacktivism. However, this is still unconfirmed. As you may remember, Uber was victim to a 2016 breach, which it initially tried to cover up and ultimately paid a $148 million fine in relation to the botched response to the attack.
- This attack has shown it’s important to not simply rely upon two-factor authentication as a way of authenticating users, with contextual information like location of the user signing in and anomaly detection on user sign in being key.
- The second key takeaway is that if the attacker has managed to get access to all key systems internally, then there was not enough segregation of internal systems.
This potential attack has confirmed the importance of implementing Zero Trust principles. In the meantime, see security updates from Uber here.
More concrete information will emerge about the attack in the coming days. In the meantime, there are some key takeaways:
This post was first first published on Forcepoint website by Aaron Mulgrew, Forcepoint Senior Solutions Architect . You can view it by clicking here

