CVE-2020-35774: twitter-server XSS Vulnerability Discovered
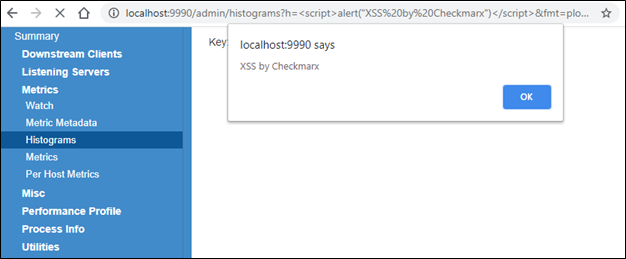
After researching twitter-server, the Checkmarx Security Research Team discovered a reflected cross-site scripting (XSS) vulnerability, assigned CVE-2020-35774, that exists in the administration panel of twitter-server in the “histograms” component.
According to its official documentation, “twitter-server” is a Twitter OSS project used to provide a template from which servers at Twitter are built. It provides common application components such as an administrative HTTP server, tracing, stats, and more, and is used, amongst other things, by both the Finagle and Finatra frameworks.
Score: 6.1 (Medium)
CVSS: 3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N
An XSS vulnerability exists in “twitter-server” in the “h” GET parameter in /admin/histograms, when the “fmt” parameter is set to either “plot_cdf” or “plot_pdf.” Note that this webpage is only available, and vulnerable, if the “finagle-stats” dependency is included, either on its own or via other dependencies such as Finatra.
Successful exploitation of the vulnerability could have allowed attackers to retrieve information presented in the twitter-server admin dashboard web-application, and potentially access additional functionality, such as shutting down the server or services. However, overall impact would be determined by functionality exposed by the specific twitter-server instance’s admin panel.
2. Add “finagle-stats” dependency to project to enable histograms tab.
1. Create basic twitter-server instance by following the guide here.
- Can be added explicitly – e.g. in build.sbt – libraryDependencies += “com.twitter” %% “finagle-stats” % “20.10.0”
- Implicitly as part of the finatra-http dependency – e.g. in build.sbt – libraryDependencies += “com.twitter” %% “finatra-http” % “20.10.0
3. Run project.
A quick manual analysis shows the tainted flow in code is quite clear:
- Oct 29, 2020 – Disclosure via HackerOne
- Oct 30, 2020 – Issue acknowledged by Twitter
- Nov 10, 2020 – Fix committed
- Dec 11, 2020 – Fixed version released
- Dec 29, 2020 – CVE-2020-35744 assigned
- Jan 6, 2021 – Public disclosure
Update twitter-server to version 20.12.0 or above.
- Request matches /admin/histograms – https://github.com/twitter/twitter-server/blob/develop/server/src/main/scala/com/twitter/server/handler/HistogramQueryHandler.scala#L353
- “fmt” parameter is either “plot_pdf” or “plot_cdf” which renders HTML response – https://github.com/twitter/twitter-server/blob/develop/server/src/main/scala/com/twitter/server/handler/HistogramQueryHandler.scala#L357
- Response content type is set to HTML – https://github.com/twitter/twitter-server/blob/develop/server/src/main/scala/com/twitter/server/handler/HistogramQueryHandler.scala#L278
- “h” GET parameter, as value of the “query” variable, is rendered into the string “Key: $query is not a valid histogram.”, which is returned as raw HTML https://github.com/twitter/twitter-server/blob/develop/server/src/main/scala/com/twitter/server/handler/HistogramQueryHandler.scala#L283
The Checkmarx Security Research Team suggested the best fix location is likely HTML encoding HTML meta-characters in the “query” variable before it is set into an HTML response string, right before line 283. This was the fix that was eventually applied by the package maintainer.
Solutions like Checkmarx SCA (CxSCA) are essential in helping organizations identify, prioritize, and remediate open source vulnerabilities more efficiently to improve their overall software security risk posture. CxSCA customers receive notice of issues like the ones described above in advance of public disclosure. For more information or to speak to an expert about how to detect, prioritize, and remediate open source risks in your code, contact us.
Discovering vulnerabilities like the ones documented in this report is why the Checkmarx Security Research Team performs investigations into open source projects. With open source making up the vast majority of today’s commercial software, security vulnerabilities must be taken seriously and handled carefully across the industry.
Dor Tumarkin is a Security Researcher and Team Leader at Checkmarx, and former Security Consultant. With 10 years of security experience, he has been an application security researcher for the past three years. Prior to this, he was a Senior Consultant at Cisco’s Center of Excellence, conducting penetration tests and operating organization-wide Red-Teams on many of Cisco’s major clients. He won at most, if not all of those engagements. When he isn’t staring at code so hard until either of them breaks, Dor has a massive passion for video games, both old and new. He has a BA in Computer Science and Business Management, and is OSCP certified.
This post was first first published on Blog – Checkmarx’s website by Dor Tumarkin. You can view it by clicking here