Coronavirus Screening and Testing, and a Sense of Urgency Among Employees
The Cofense PDC (Phishing Defense Center) has seen a continuous campaign by malicious actors exploiting the COVID-19 pandemic by using cleverly crafted phishing–email campaigns to harvest sensitive user data and spread malicious payloads across industry sectors.
By Ala Dabat, Cofense Phishing Defense Center
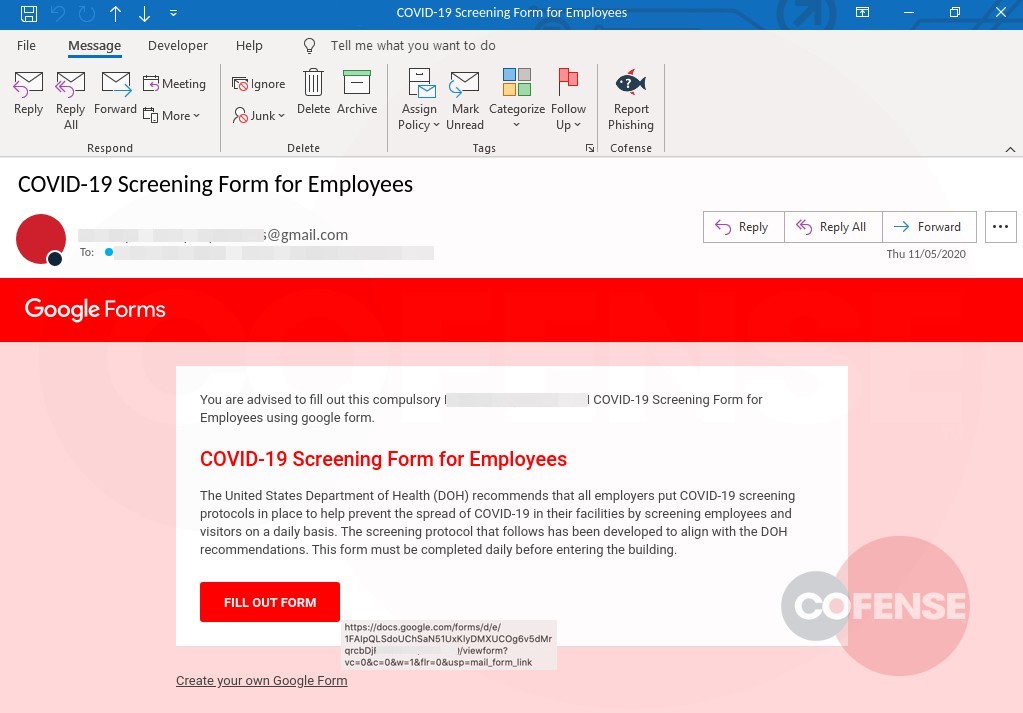
One such example seems to exploit the sense of urgency felt among employees for tests to screen for the COVID-19 virus. Recipients’ vulnerability is leveraged in attacks such as the one in Figure 1, a seeming Google form issued to employees by the targeted company(s).
The aesthetics of this particular campaign are solid and simple enough to reach users in environments protected by secure email gateways (SEGs).
Figure 1
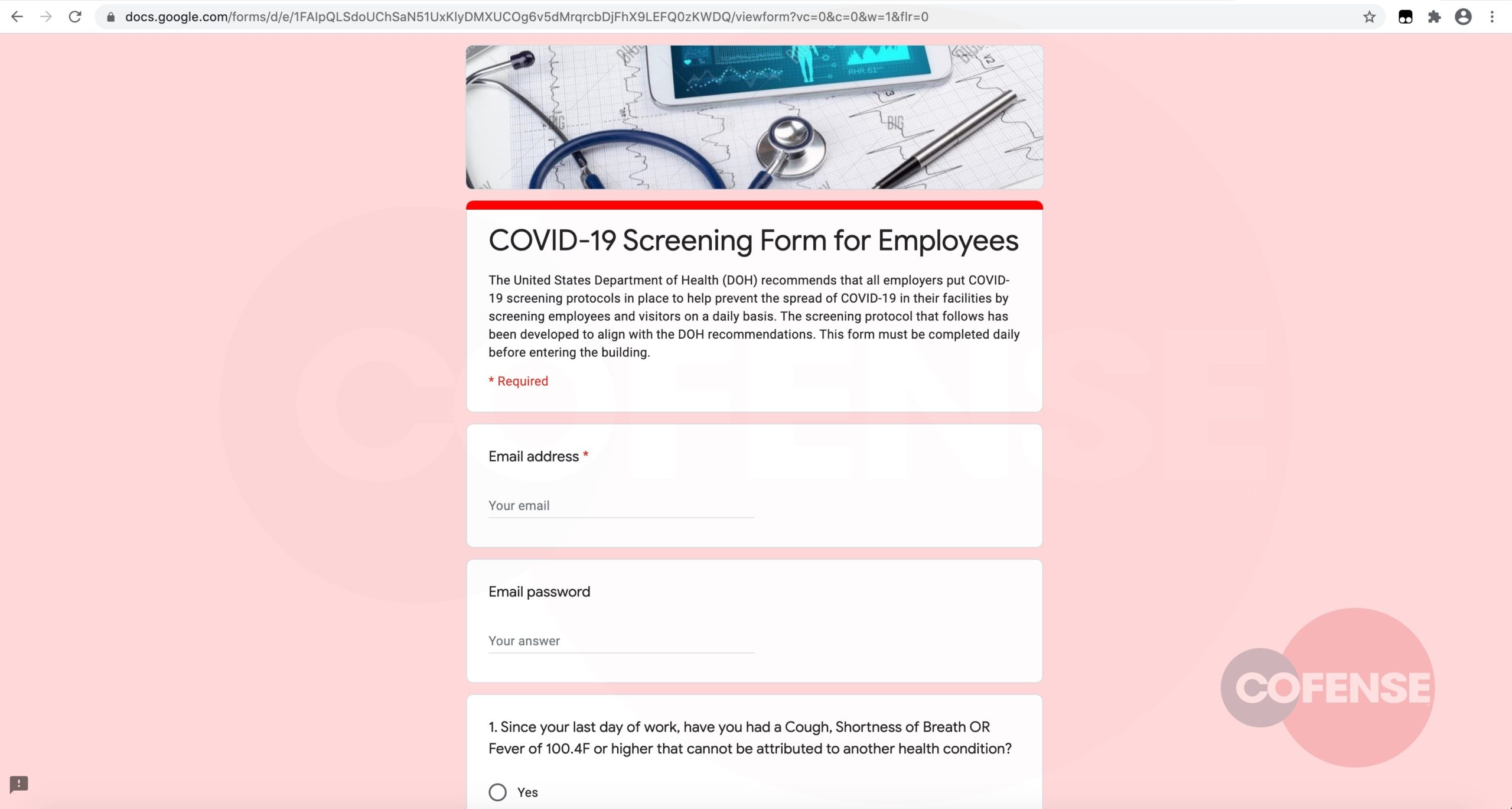
The email appears to be from the target company and its legitimacy is reenforced by references to guidelines and protocols issued by the “United States Department of Health.” Employees are advised that these protocols will facilitate the screening process, a clever way to persuade recipients to hand over credentials and other sensitive information (Figure 2).
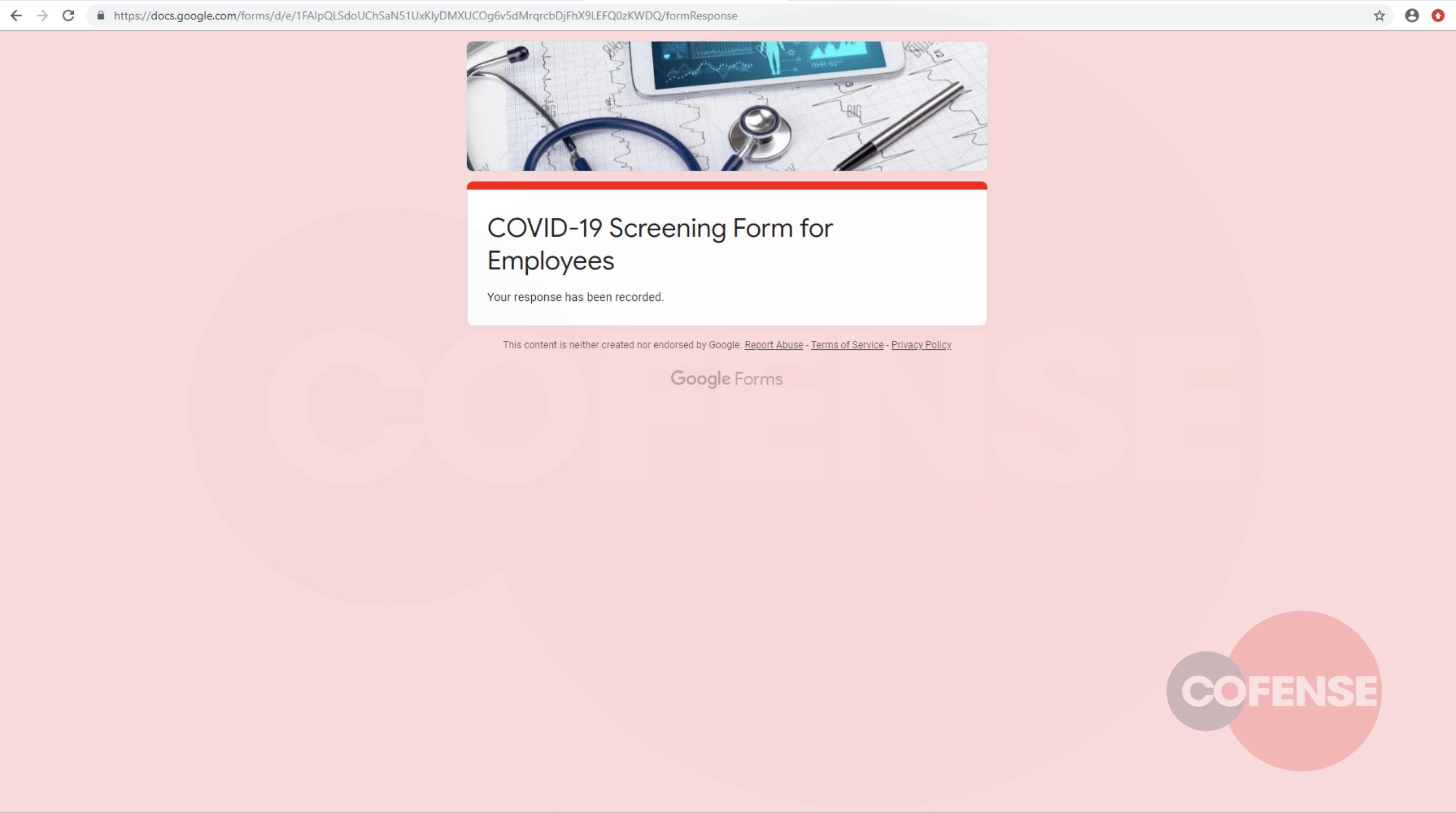
In the above example, targeted users are redirected to a Google Doc landing page hosting the malicious website. A legitimate Google–registered URL can often convince even security conscious users into handing over their information.
Figure 2
Figure 3
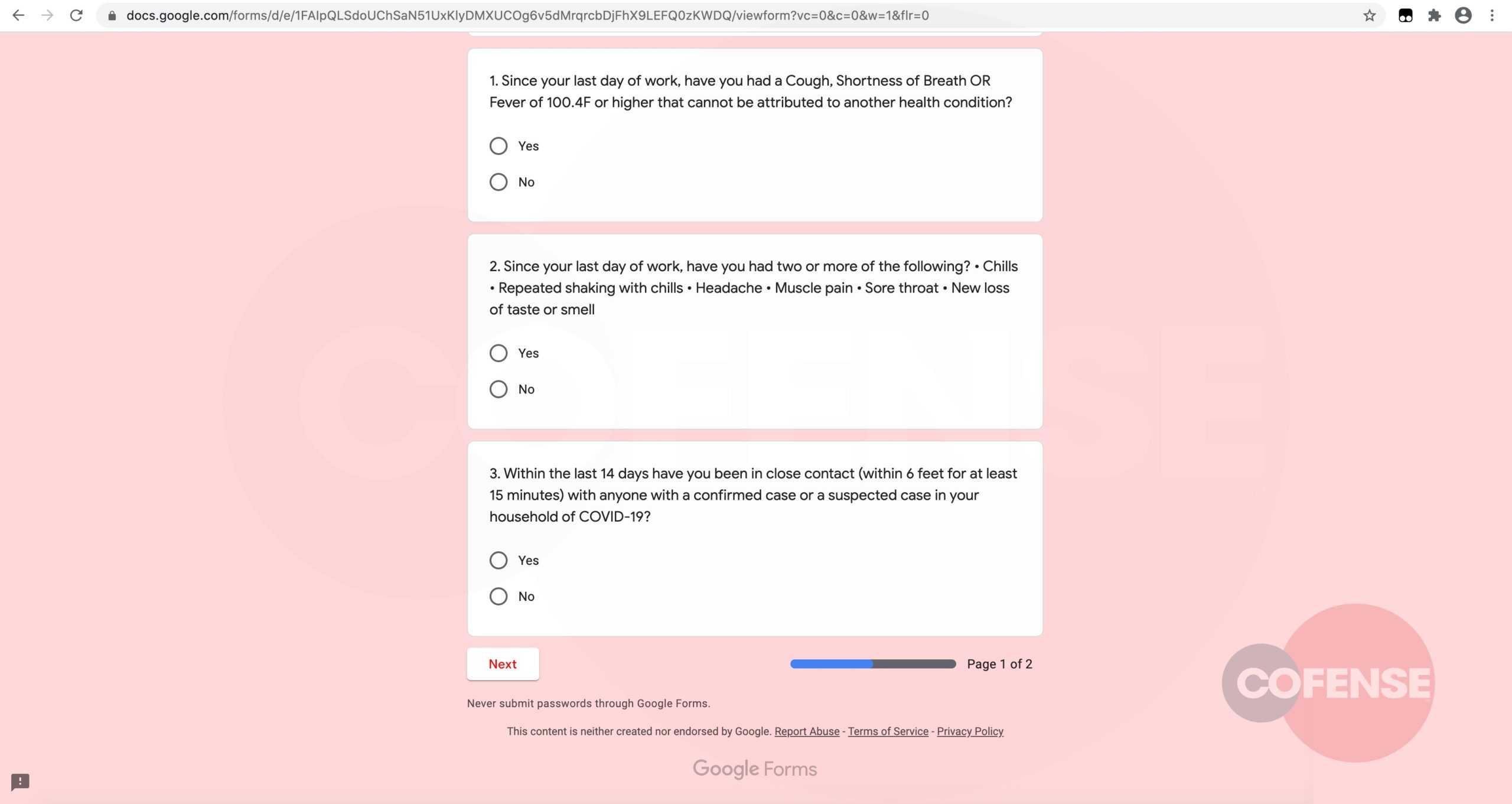
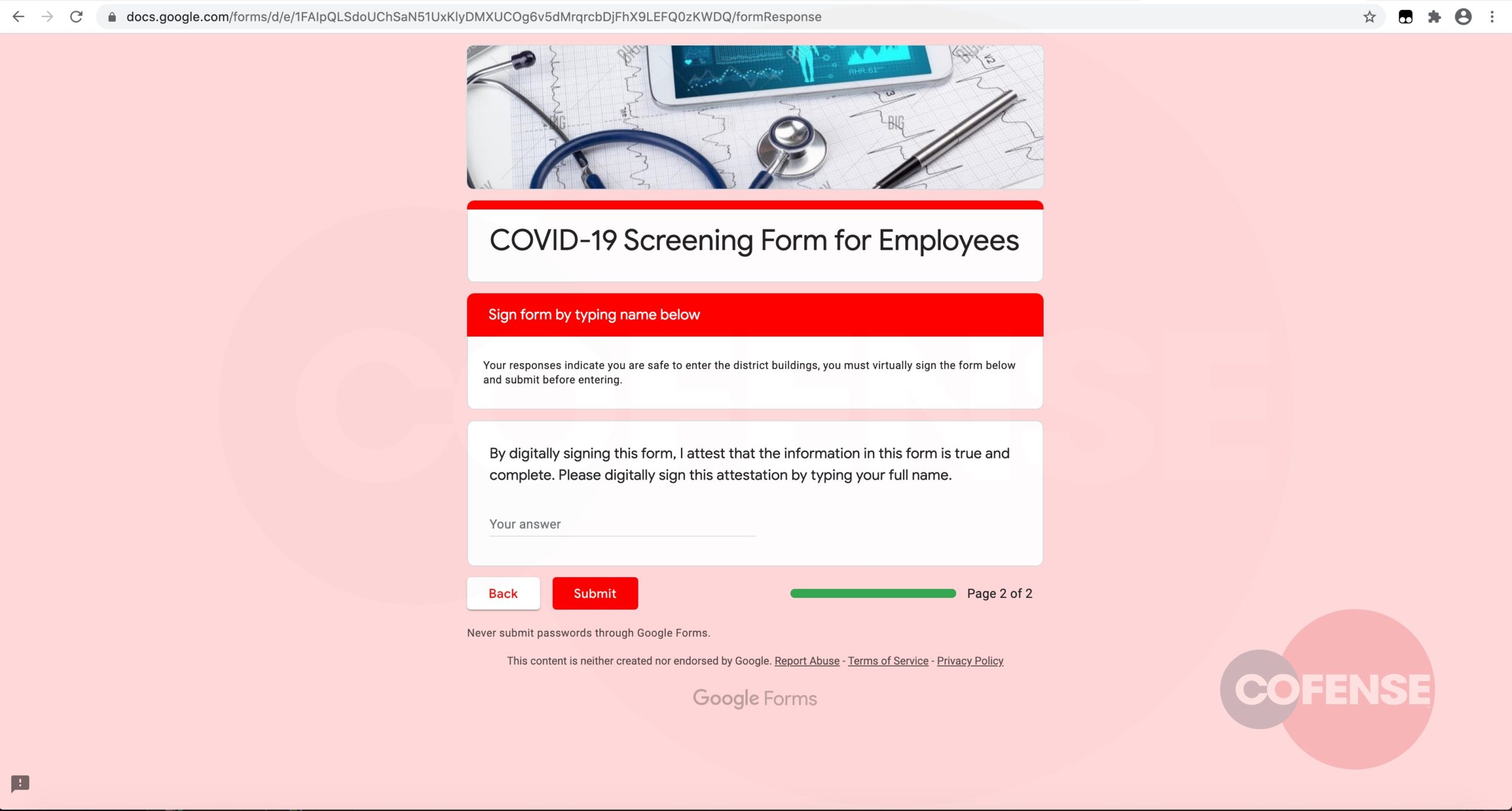
Figure 3 shows that the threat actor is blending common screening questions with the request for sensitive credentials, possibly to divert recipients from the threat.
Once the form has been completed, recipients are told to provide a digital signature to wrap up the fraudulent screening application and submit the data to a command-and-control server that stores the harvested information.
Figure 4
Figure 5
| Link | IP |
| hXXps://docs[.]google[.]com/forms/d/e/1FAIpQLSdoUChSaN51UxKlyDMXUCOg6v5dMrqrcbDjFhX9LEFQ0zKWDQ/viewform?vc=0&c=0&w=1&flr=0&usp=mail_form_link
Indicators of Compromise |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.
This post was first first published on Cofense’s website by Cofense. You can view it by clicking here

