DDoS to Loom Large in the 5G Era

Today, 5G is around the corner and, in the foreseeable future, it will definitely bring more convenience to our lives. Higher rates of mobile terminals, more devices connected to the Internet of Things (IoT), more convenient remote services… All these will lead us to a brand new era of the Internet of Everything (IoE). With constant breakthroughs in technological innovation, cybersecurity should also move at the same rate.
In the past few years, cyberattack methods have been diversified. Worse still, the advent of 5G will open windows to more attack scenarios and attack approaches for cyber criminals. In our opinion, distributed denial of service (DDoS) will remain one of the most important methods of attack, among others. How to defeat DDoS attacks more effectively in 5G scenarios is the top concern of security researchers.
5G Usage Scenarios
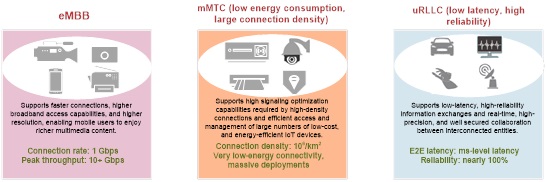
5G will be used in three scenarios, each of which has different requirements for network capabilities. In terms of cybersecurity, there is no silver bullet. For 5G security issues, there is no one-size-fits-all solution.
Enhanced Mobile Broadband (eMBB) and Massive Machine-Type Communications (mMTC) services are characterized by huge quantities of terminals and traffic data. Therefore, the key to securing these two types of services is to overcome volumetric and overlarge-volume attacks, which, in turn, requires high-capacity and flexible defense solutions.
Ultra-Reliable, Low-Latency Communications (uRLLC) services, as the name implies, are characterized by low latency and high reliability. These services, however, generate smaller volumes of traffic than eMBB and mMTC services. This is somewhat like online gaming. A bit of network jitter will cause a serious impact on user experiences. To counter DDoS attacks targeting such services is usually the most challenging and sophisticated part of cybersecurity in the 5G era. To defend against this type of DDoS attacks, it is crucial to promptly identify attack traffic and normal traffic and cause very low delay in normal traffic.
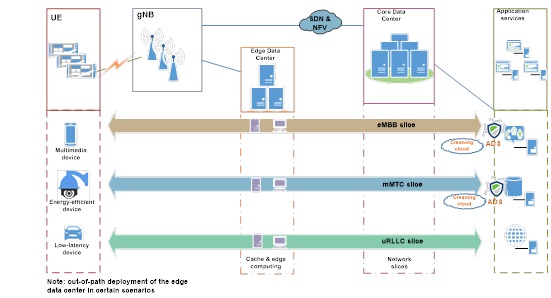
Protection Against DDoS Attacks on 5G Networks
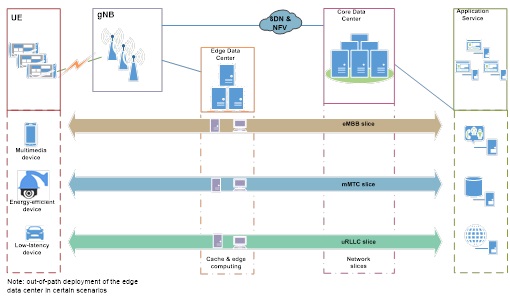
The 5G network architecture will incorporate emerging techniques, including network slicing, software-defined network (SDN), network functions virtualization (NFV), and edge computing. The introduction of SDN and NFV enables building of logically isolated network slices to support differentiated requirements of the preceding 5G usage scenarios. However, this also adds to the challenge of securing networks because it blurs their boundaries, rendering previous security mechanisms relying on physical perimeter protection useless. That is why we say that a new security mechanism is in urgent need to meet virtualization and cloud-based development requirements.
Moreover, for uRLLC applications that require sub-millisecond latency, edge computing will play a critical role. Specifically, an edge data center will take over some tasks from the core data center to achieve faster access and computation. Edge data centers will become new network platforms requiring robust protections in the 5G era. DDoS attacks against them will have a direct bearing on critical services such as the Internet of Vehicles (IoV) and remote health care.
Considering the network composition and usage scenarios of 5G technology, we believe that zones vulnerable to DDoS attacks are mainly the edge data center and application services.
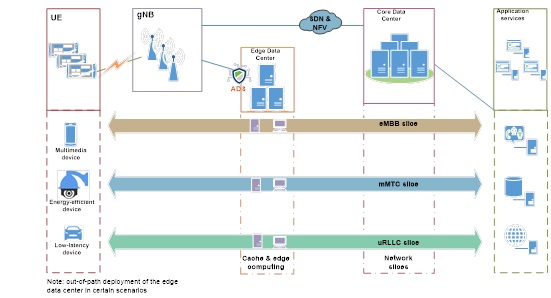
DDoS Protection for the Edge Data Center
On a 5G network, the edge data center is responsible for a large proportion of cache and edge computing tasks. For the scenario where low latency is required (uRLLC), we can use the cache mechanism and edge computing to handle requests from terminals more efficiently. Another issue that calls for special attention is this scenario requires high reliability. Once the network is attacked, tremendous losses will be incurred. Currently, it is yet to be decided whether standardized hardware is required for the edge data center.
If standardized hardware is required, a feasible option is to deploy virtual anti-DDoS products to effectively protect the edge data center from both network-layer and application-layer attacks and at the same time to ensure fast response of the defense process. The ultimate purpose is to provide protection that results in such low latency that normal services are hardly affected.
If no standardized hardware is required, users can consider deploying hardware anti-DDoS devices or virtual anti-DDoS devices, depending on actual network conditions.
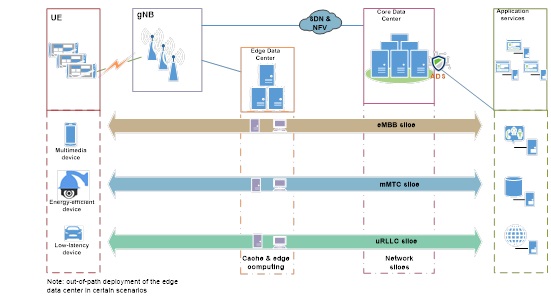
DDoS Protection for Application Services
- DDoS Protection at the Egress of the Core Data Center
Currently, it has been decided that standardized devices will be adopted for the core data center. In this case, users can deploy virtual anti-DDoS devices at the egress of the core data center to filter out DDoS attack traffic before such traffic reaches application services.
- DDoS Protection Before Application Services
For applications of eMBB slicing and mMTC slicing, it is advisable to deploy anti-DDoS devices at the perimeters of the application server zone. These two types of applications feature large numbers of terminals and short bursts of traffic. Therefore, a feasible solution is to deploy anti-DDoS devices with a Tbps-level cleaning capacity. In collaboration with cloud-based cleaning services, the solution can filter out DDoS attack traffic to the best effect. Moreover, by incorporating a threat intelligence system, the solution can implement active defense to block source devices marked by the threat intelligence system as dangerous, nipping potential DDoS attacks in the bud and improving the DDoS protection efficiency.
The post DDoS to Loom Large in the 5G Era appeared first on NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.