More Is Not Merrier: Point Products Are Dead
Organizations using more than 50 tools to manage their security environment and respond to incidents ranked 8% lower in their ability to detect an attack. And, each additional tool increases complexity in a way that adversely affects the security team’s capacity to detect, prevent, contain, and respond to incidents.
Information technology infrastructures have grown more complex, threats have become more sophisticated, and organizations find themselves managing a large investment in a ballooning assortment of technologies and solutions. Unfortunately, according to the latest research from the Ponemon Institute and IBM Security, increasing the number of tools in an organization’s security stack leads to diminishing returns in terms of efficiency and performance.
So Many Tools, So Much Complexity
How did we get here?
Even when point products do interoperate, they don’t enable implementing security policies consistently across the myriad of products a customer has Instead, security personnel must manually process information from multiple tools to respond to security events. If vendors can’t integrate products, why should you be expected to?
Traditional cybersecurity solutions for the problems faced by organizations are inherently reactive. Whenever a new problem is discovered that cannot be solved effectively by existing products, customers deploy new products to address it. The result? Increased labor costs and a greater need for training and support. Operational efficiency and effectiveness suffer, and it can be nearly impossible to derive the full—or promised—value from any individual point solution.
What Category Consolidation Means for Cybersecurity
And that brings us to a bigger question: Why choose between best of breed and an integrated product if you can have both in an integrated solution?
During that period, closely related products in various categories are commonly used together. When these solutions become commonplace as best practices, mergers and acquisitions abound and each vendor’s stable of partners tends to grow. Talk of formal integration begins. This happened in the firewall space and resulted in the Next-Generation Firewall. It represented integration of the capabilities of individual point products collapsed into a single solution. From a customer perspective, that consolidation resulted in a larger portfolio of capabilities within a single product.
When a new product category is introduced, attributes and specialized functionalities are unique to each vendor. Over time, competitive pressures reduce the disparity in offerings, categories standardize and the real technical differences between products become minimal.
Cloud Security Takes a Leap Forward
We are at one of those turning points.
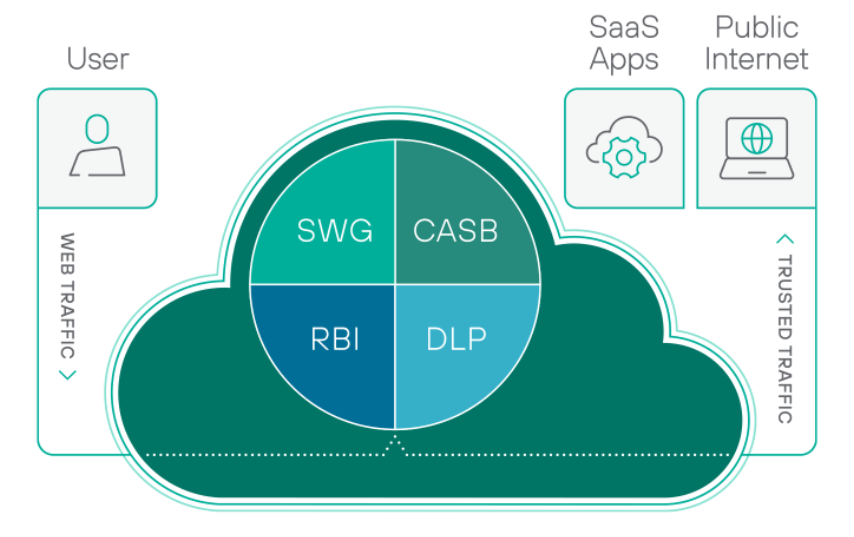
That’s why Forcepoint has introduced Cloud Security Gateway (CSG), a new converged cloud security service that provides visibility, control, and threat protection for users and data wherever they are. It combines the capabilities previously found in Forcepoint Data Loss Prevention (DLP), Cloud Access Security Broker (CASB) and Secure Web Gateway (SWG), within a single product that’s quick and easy to adopt. What’s more, Forcepoint has integrated its flagship behavior-based technology that understands people’s actions, to stop the bad and free the good.
At Forcepoint, we believe it’s time for a change. A status quo approach to a changing security landscape simply won’t do. In today’s world of shrinking budgets and ever-increasing operational complexity, what’s needed are ways to make life simpler and easier. A collection of products is not enough.
 Stay tuned to the Forcepoint Insights blog to learn more about the new security architecture securing the cloud of today and tomorrow. For now, here’s a list of resources for those interested in learning more about Forcepoint’s new Cloud Security Gateway:
Stay tuned to the Forcepoint Insights blog to learn more about the new security architecture securing the cloud of today and tomorrow. For now, here’s a list of resources for those interested in learning more about Forcepoint’s new Cloud Security Gateway:
It’s the only 100% cloud-native best-of-breed, centrally-managed security platform that protects users and data wherever they are, delivering more value than any collection of individual products. Working from home has never been more secure.
RESOURCES
This post was first first published on Forcepoint website by Wassim Tawbi. You can view it by clicking here

