Real-Time Defense of Multi-Cloud Environments From Malicious Attacks and Threats
Table of Contents
Organizations today cannot detect real-time threats at runtime due to the multi-cloud infrastructure, resulting in the possibility of malicious actors exploiting the environment. It is imperative for the modern organization to have a solution to detect advanced run-time threats in real-time to protect their systems.
As a result of our commitment to supporting organizations globally to operate a secure multi-cloud infrastructure, we are pleased to announce the launch of Qualys Cloud Detection and Response (CDR) (formerly Blue Hexagon CDR). This solution provides multi-cloud threat detection at runtime across multiple cloud environments, enabling you to detect both known and unknown threats across the entire kill chain in real-time across all cloud environments to keep your cloud safe. Qualys CDR uses deep learning artificial intelligence to detect threats that frequently evolve, making traditional signature-based approaches ineffective.
With Qualys CDR organizations can not only start secure in their cloud journey but more importantly, stay secure – before launch and during the cloud execution process.
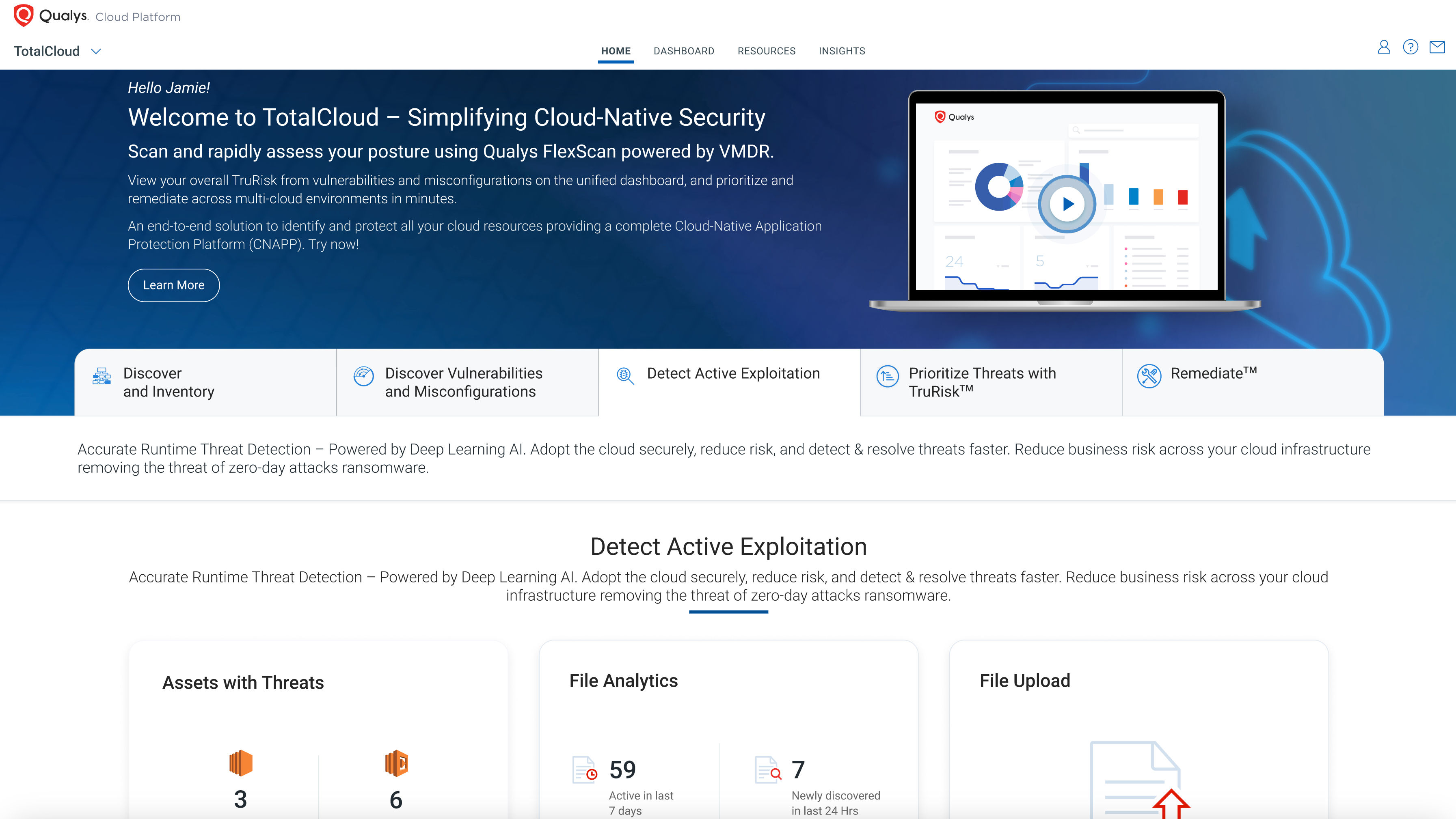
Qualys CDR is available as a module of the Qualys TotalCloud release (link to GA blog), which combines world-class vulnerability management, container security, cloud asset, and misconfiguration management at scale in a seamless manner.
Tackling Present-day Cloud Security Challenges
The security of key cloud assets can be potentially compromised by a variety of threats that could have the potential to undermine the operational safety and efficiency of an organization operating a multi-cloud infrastructure. This would require a new security paradigm to address the concerns outlined below.
1. Focus Only on Hardening and Not Threat Detection
In many cloud security tools, the focus is on hardening the infrastructure of the cloud by detecting misconfigurations and compliance violations that may exist. This approach has resulted in high severity vulnerabilities remaining unpatched for weeks because it is very difficult to update production systems without taking down the entire system.
With Qualys Cloud Detection and Response, users can monitor their cloud assets continuously as workloads run, thus ensuring that they are protected against threats and attacks as they execute.
2. Signature-Based Threat Detection and Malware Sandboxes Are Still the Default
There is still a large majority of security tools that rely on signature-based engines and malware sandboxes to detect threats, which assumes that all threats are known in advance and will be detected according to their characteristics. The legacy-based systems can be evaded with a simple modification of a known threat to avoid detection.
Qualys Cloud Detection and Response uses deep-learning artificial intelligence to detect known threats as well as unknown ones – a highly effective way of catching threats that are not recognized by traditional detection methods.
3. Periodic Agent-Less Scanning Misses Malware and Protocol Threats
To provide security software services without requiring the use of agents, some security tools have implemented an approach that utilizes periodic snapshots of the file systems to scan virtual machines or containerized environments without requiring the use of agents. There is a possibility that this approach will not be able to detect threats that are not written to a file system; such threats manifest themselves only in network traffic or in-memory. A problem with such solutions is they are blind to typical manifestations of infection, such as command and control traffic (which is a key component of determining if supply chain attacks have been carried out), network scanning and brute-force attacks, lateral movement, and data exfiltration.
To identify all threats, Qualys Cloud Detection and Response continuously monitors cloud network traffic in real time.
Benefits of the Qualys Cloud Detection and Response Platform
Qualys Cloud Detection and Response brings many benefits to organizations for multi-cloud security.
Detect Active Exploitation and Mitigate Runtime Risks
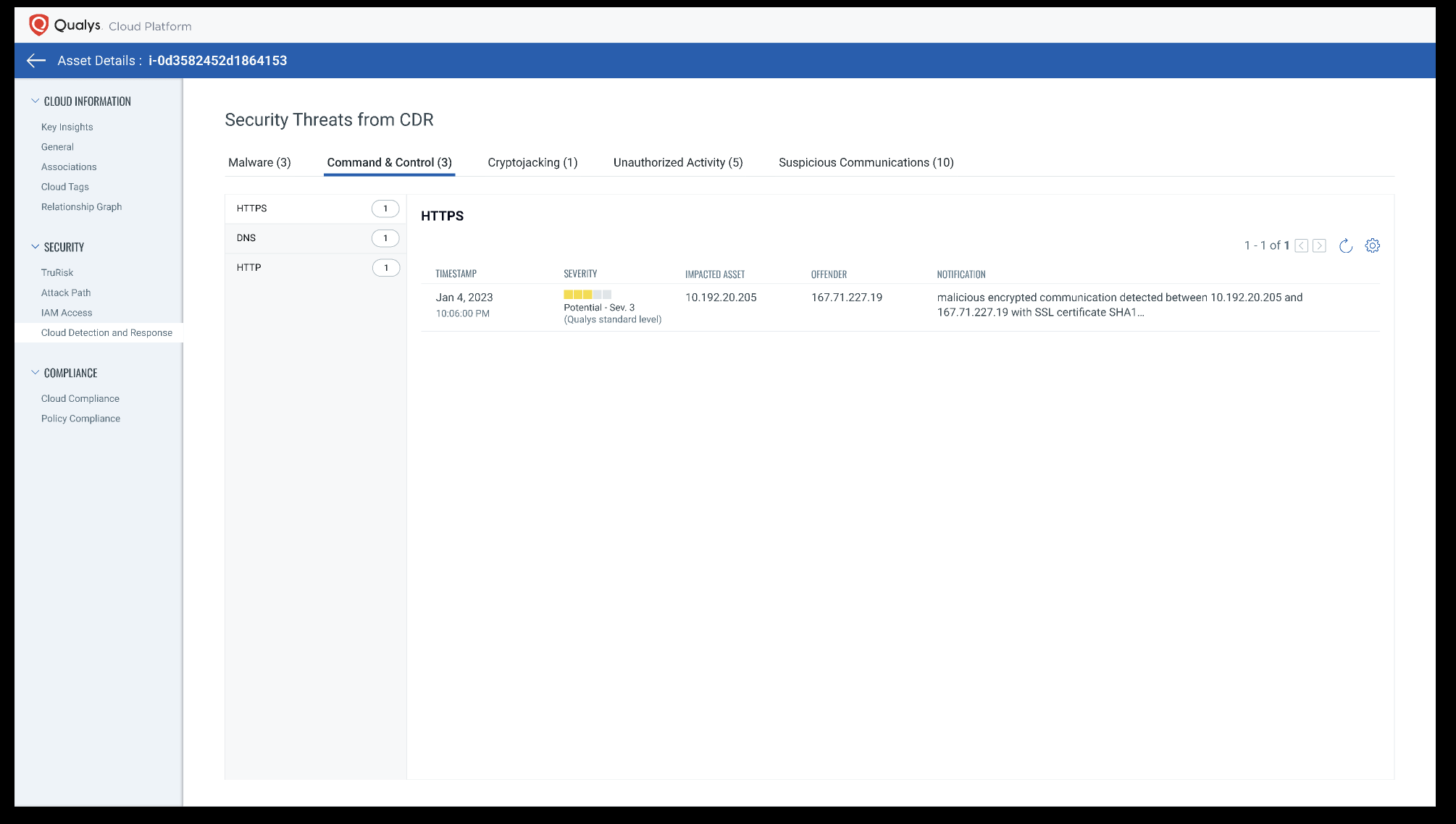
Qualys Cloud Detection Response inspects cloud network traffic for suspicious communications, unauthorized activity, crypto miners, malware, and C2 communications using deep-learning AI algorithms.
Detect Zero-day Threats
Threats are detected in near-real-time using deep-learning AI. Unlike legacy signature-based approaches, an AI-based approach can detect new threats from a myriad of data points.
Detect Threats at All Points of the Kill Chain
By inspecting network traffic, Qualys CDR can detect attacks at various points along the MITRE ATT&CK kill chain, thus providing additional protection against emerging cloud-based attacks.
No-Friction Multi-Cloud Agentless Deployment
Agentless multi-cloud deployment enables rapid time-to-value across multiple clouds.
Better Risk Prioritization Based on Runtime Data
Qualys CDR improves your security, identifies assets that are being actively probed, and automatically takes the necessary action.
Qualys Cloud Detection & Response (CDR) – Defend Your Cloud Infrastructure From Malicious Attacks
With Qualys cloud detection & response (CDR), customers can detect active threats without having to rely on outdated signatures.]. With deep-learning technology applied to network traffic, the solution provides accurate threat detection for both known and unknown threats in just a few seconds, and it works natively with cloud infrastructure to provide visibility and enforcement across the entire ecosystem.
All cloud workloads can be protected with Qualys CDR without requiring any in-line devices or agents to be installed.
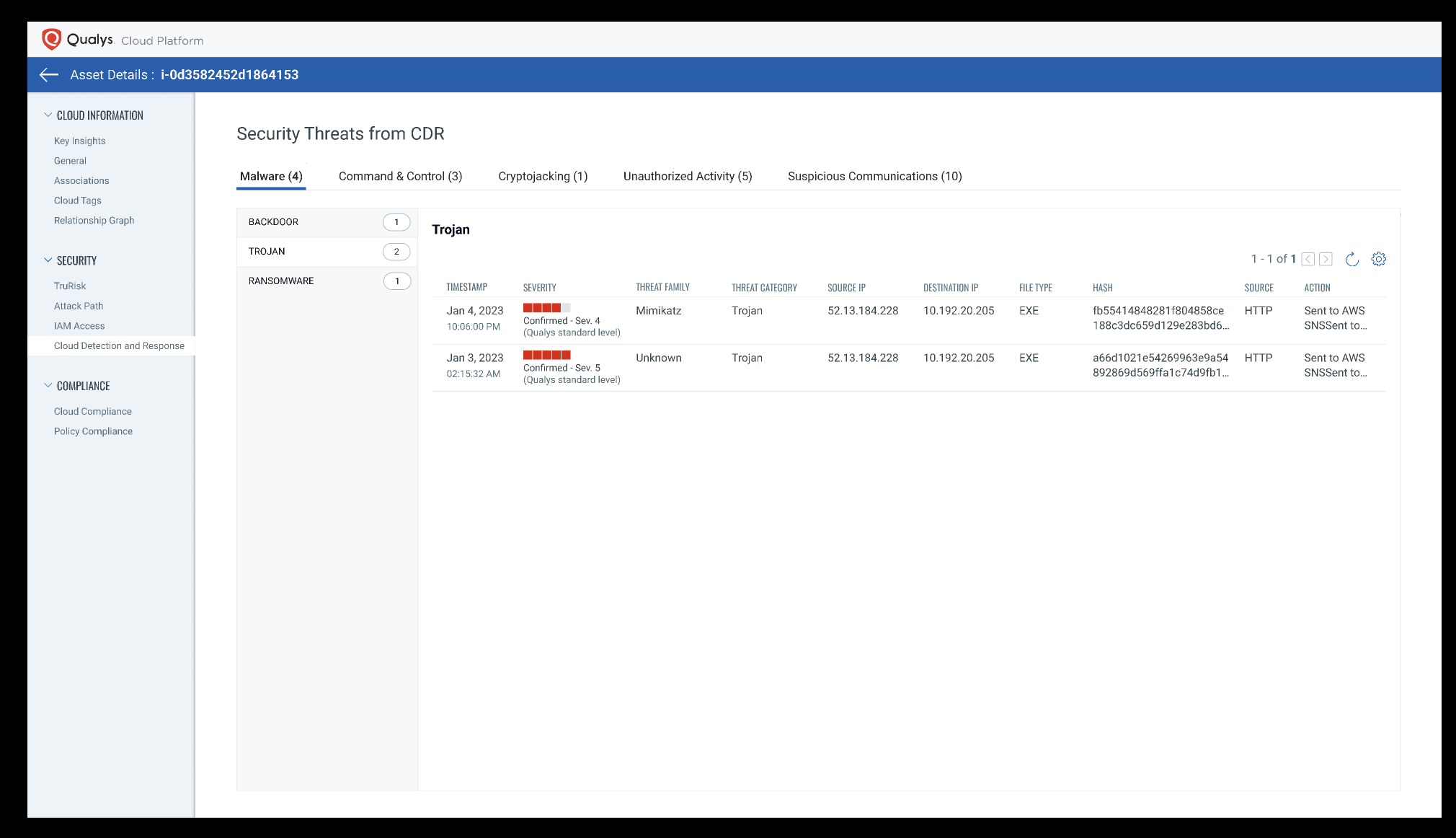
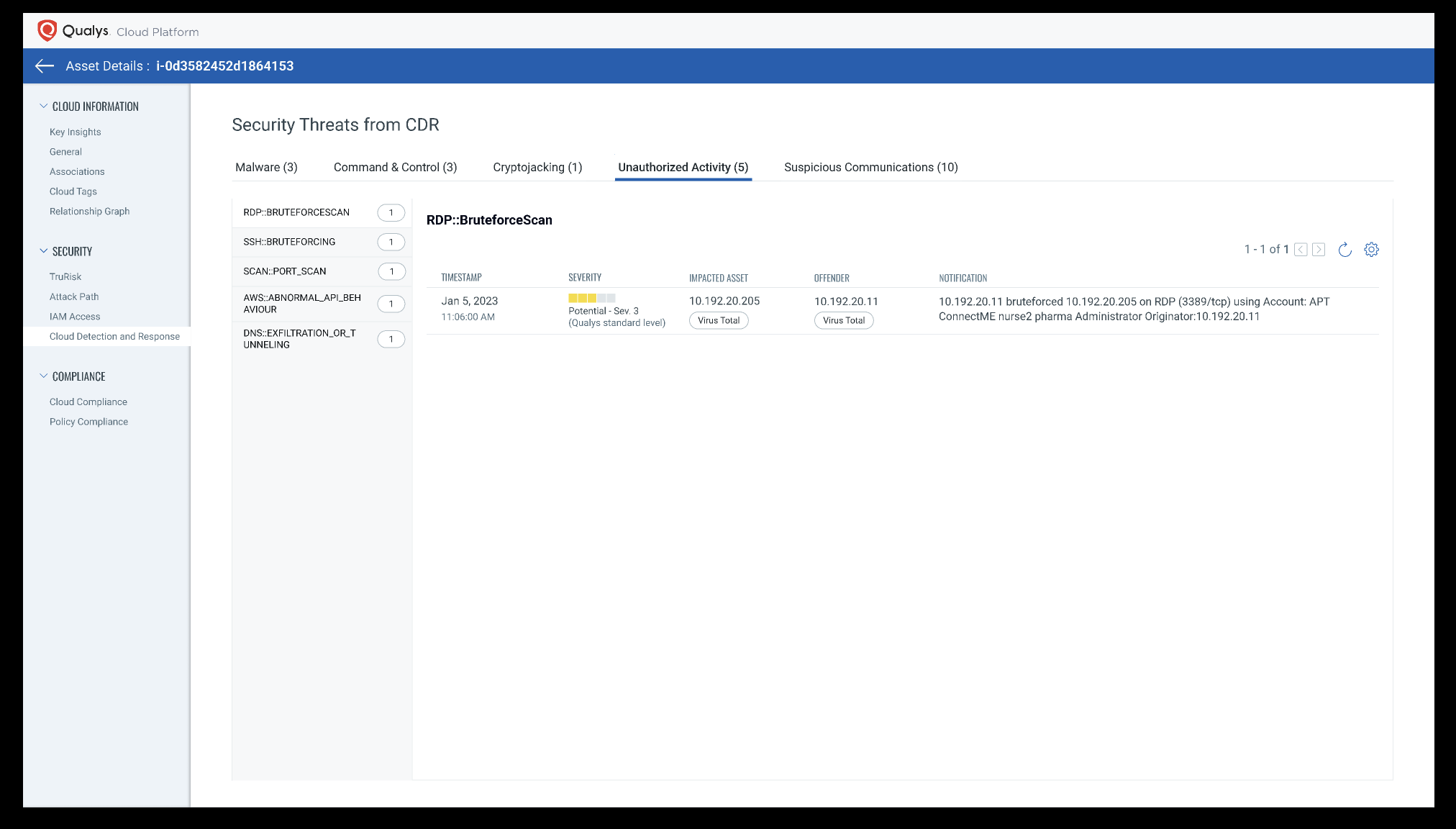
Qualys CDR will detect the following types of threats:
Command and Control, Including Beaconing
An analysis of north-south traffic such as beaconing can identify specific threat actors or malware communicating with their command centers. Beaconing lets threat actors know that malware has infected a target system and is ready for commands to continue to the attack.
Lateral Movement
When the attacker gains access to a public facing instance, their next step is lateral movement. The first step of this process is to conduct reconnaissance and determine where to move next or what resources are available for infiltration. SSH and RDP are two protocols that are helpful for detecting lateral movement.
Data Exfiltration
After valuable assets are compromised, the attacker will either steal the data or issue a ransom request. Qualys CDR reveals potential data exfiltration attempts in cloud assets connected to the Internet.
Initial Access and Brute-Forcing
Usually access to the cloud is gained by exploiting a public-facing application or a misconfiguration. Qualys CDR identifies these moves to block the offending hosts, then prioritizes the victim assets and configurations for remediation or patching.
Crypto Mining
Qualys CDR identifies crypto-mining traffic that uses the JSON-RPC interface over HTTP to identify crypto-jacking malware executing on cloud assets.
Malware
Malware files are inspected in the network using deep-learning AI. The deep-learning algorithms detect malware in less than a second with high accuracy.
“We handle over 7 billion interactions every year for 125 million consumers in 38 countries, and those numbers have been rising exponentially since the onset of the coronavirus pandemic,” says Ram Ravichandran, CTO of Narvar. “Securing the cloud infrastructure is paramount for business continuity, and we realized we needed to deploy a security solution that can scale with our operations without creating any disruptions or delays in how consumers interact with their favorite retail brands.”
– Ram Ravichandran, CTO of Narvar
The Solution for the Modern Cloud
There is a problem with the legacy approach to cloud security because it relies on siloed, manual data collection and analysis, which increases response times and increases risk as a result. Qualys Cloud Detection and Response allows security teams to get rid of this siloed, disconnected approach to detecting and responding to attacks, by providing a single integrated solution for securing access to cloud infrastructures and cloud-native workloads.
Get started with Qualys Cloud Detection and Response Today:
This post was first first published on Qualys Security Blog’ website by Nayeem Islam. You can view it by clicking here

