ISO 27001 welcomes Threat Intelligence
ISO 27001 welcomes Threat Intelligence
Ramiro Céspedes
Introduction
In my previous article I defined what is Cyber Threat Intelligence (CTI), described how to measure it and explained why it is important to implement a CTI program that can serve different stakeholders with different types of intelligence requirements in order to have a proactive security approach.
2022 was a productive year for ISO (International Organization for Standardization) security standards. In February, ISO published a new version of ISO/IEC 27002 and more recently, in October, a new version of ISO/IEC 27001. Considering that the previous versions had been published in 2015 (ISO/IEC 27001) and 2014 (ISO/IEC 27002) and that the technology and the threat landscape evolves exponentially, these new versions are very much welcomed.
So how does ISO/IEC 27000 and CTI relate to each other?
A brief introduction to the ISO/IEC 27000 family
The ISO/IEC 27000 family of standards, also known as the Information Security Management System (ISMS) family of standards, cover a broad range of information security standards published by both the ISO and International Electrotechnical Commission (IEC). The first version of ISO/IEC 27001 was published in 1999 whereas the first version of ISO/IEC 27002 in 1995.
The objective of these standards are to address and provide guidance on security, privacy and IT challenges so that organizations of all shapes and sizes could benefit from it.
The difference between ISO/IEC 27001 and ISO/IEC 27002 is that ISO/IEC 27001 is actually a management standard that can be certified. i.e. It must be planned, implemented, monitored, reviewed, and improved and can be audited. On the other hand, ISO/IEC 27002 is a detailed list of security controls that can be implemented or used to meet ISO/IEC 27001 requirements. ISO 27002 goes deeper by defining how the requirements and standards should be implemented by the organization. It may also be used as a best practices guide for how to best leverage the controls when they are put in place.
Why is ISO/IEC 27001 relevant to Information Security Leaders and their organizations?
Implementing ISO 27001, no matter the size of the organization, allows InfoSec leaders to prove the board and customers that their organization is striving to:
- Carry out comprehensive risk assessments
- Reduce identified risks to an acceptable level
- Manage the risks effectively
- Strengthen trust and improve the organization’s reputation
In other cases, ISO 27001 can also help the organization comply with other regulations and standards, such as privacy regulation GDPR, infosec standards, or business standards like PCI DSS.
What’s new in ISO/IEC 27001/27002 and how does it relate to CTI?
There are many changes and new features in the latest version of ISO/IEC 27001, starting by the name.

It is safe to say that ISO has certainly looked to broaden the scope of this standard by not just covering IT but also privacy and cybersecurity.
Overall, some security controls were removed, 24 controls were merged, 58 controls were revised and 11 new security controls were created, designed to address the new cybersecurity landscape.
All the security controls are organized in 4 sec categories:
- Organizational,
- People,
- Physical and
- Technological
Moreover, ISO 27002 adds to each security control 5 new attributes:
- Control Type,
- IInformation Security Properties,
- Cybersecurity Concepts,
- Operational Capabilities and
- Security Domains
It may, or may not, come as a surprise to you but one of the 11 new ISO 27001 controls is Threat Intelligence.
ISO defines Threat Intelligence as: “Information relating to information security threats shall be collected and analysed to produce threat intelligence”. In order to be able to follow this guideline and to collect, analyze and produce threat intelligence the organization can benefit from a Threat Intelligence Platform like ThreatQ, powerful enough to do all the collection and processing needed to correlate information coming from different information sources and generate new threat intelligence products.
Let’s take a sneak peek into ISO’s 27002 Threat Intelligence control.
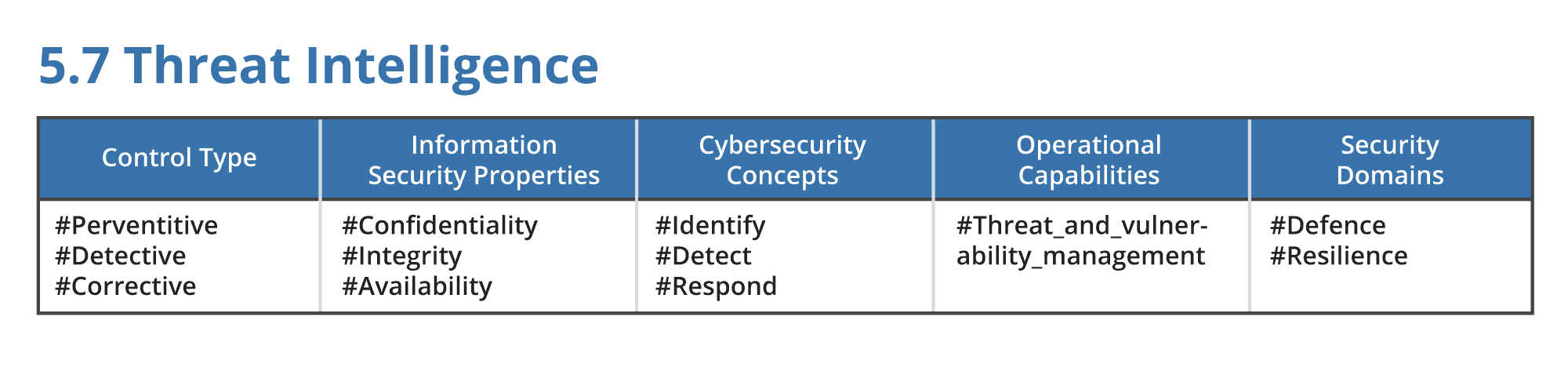
As you can expect, ISO has clearly defined what is Threat Intelligence and what’s the objective and benefits from implementing it in the organization. I am pleased to see that they have made a clear distinction between different types of Threat Intelligence in the following way:
- Strategic: high level information about the threat landscape
- Operational: details about specific attacks, including technical indicators (IOCs)
- Tactical: information about attacker methodologies, TTP
While it is difficult to always agree on definitions and categories of Threat Intelligence, this is a great step forward to provide a framework in which organizations can consume, produce and share the correct type of threat intelligence.
To continue with, there is also something important to mention here and it is that according to ISO 27002:

These are:
5.25 – Assessment and decision on information security events
8.7 – Protection against malware
8.16 – Monitoring activities
8.23 Web filtering
It is interesting to note that there are other controls that heavily rely on, or can benefit from, Threat Intelligence for them to be effective.
Conclusion
According to the 2022 Global Cybersecurity Outlook Report by the World Economic Forum, new threats require “a layered security model that includes network, endpoint and data-centre controls powered by proactive global threat intelligence”. We know that Threat Intelligence can be used by many different teams in an organization to prevent, detect, or respond to threats. Furthermore, even organizations that don’t produce threat intelligence can leverage finished intelligence products received from different sources if they have the correct capabilities to do so.
We may agree that getting access to information sources or open-source intelligence is not a problem and while there are several very good threat intelligence vendors in the industry organizations are still missing the piece that solves the puzzle. Which puzzle you may ask, and it is the one of high volume of information or intelligence products with very few capabilities to actually leverage it. We have intelligence vendors and information providers on one side and security tools and technologies on the other. A Threat Intelligence Platform like ThreatQ is the missing piece, it is what connects everything together and allows the organization to leverage all its telemetry by contextualizing it with external intelligence and helping the organization to make informed decisions.
With regards to ISO including Threat Intelligence as a control, I believe it shows the importance of better threat intelligence for today’s organizations. Standardizing threat intelligence products enables better and more relevant actionable intelligence and facilitates more effective management of security controls across the organization’s security perimeter and beyond. Threat intelligence can inform security strategies and identify vulnerabilities and weaknesses not just in the organization’s perimeter but also in the supply chain, third parties, and even physical or environmental threats.
The post ISO 27001 welcomes Threat Intelligence appeared first on ThreatQuotient.

