CISA BOD 23-01: Meeting and Exceeding CISA Requirements with Qualys
The latest Binding Operational Directive from the Cybersecurity and Infrastructure Security Agency (CISA) BOD 23-01 requires agencies to implement an essential cybersecurity practice within the next 6 months. While this new mandate impacts agencies directly, it also impacts their supply chain partners as well. Here’s why and what Qualys is doing to help customers succeed with CISA.
What You Need to Know:
Binding Operational Directive – BOD 23-01 – Improving Asset Visibility and Vulnerability Detection on Federal Networks, was released in early October of 2022 and requires all Federal Civilian Executive Branch (FCEB) departments & agencies to comply with a list of security requirements before or by April 3, 2023. Of course, many private sector organizations are also following suit.
The directive includes the following criteria:
- Ability to perform automated asset discovery every seven days
- Initiate vulnerability enumeration across all discovered assets nomadic / roaming devices every two weeks, including servers, workstations, laptops, printers, and managed network devices.
- Automate ingestion of vulnerability enumeration results into CDM agency dashboard within 72 hours of discovery
- Develop and maintain the operational capability to initiate on-demand asset discovery
- Report vulnerability enumeration performance data into a CDM Dashboard
Asset Discovery and Vulnerability Enumeration
The compulsory order titled “Improving Asset Visibility and Vulnerability Detection on Federal Networks” outlines the requirement for relevant organizations to make “measurable progress” regarding asset visibility over agency assets and vulnerabilities. This is critical because CISA language suggests that not only FCEB departments & agencies must improve their asset discovery and vulnerability enumeration capabilities, but they must illustrate and document improvements over time.
What does ‘good’ look like to CISA for Asset Inventory and Vulnerability Enumeration?
- Asset Inventory
When it comes to BOD 23-01, it all starts with asset inventory. Specifically, the directive specifies that asset inventory functionality is the capability that allows organizations to identify IP assets within their network, as well as ‘associated IP addresses.” With this language, it is safe to assume that anyone striving to comply with BOD 23-01 should institute a program where both internal known assets and external internet-facing assets, which may not yet be visible to security practitioners, must be logged and managed in the future. This can be achieved through a comprehensive Vulnerability Management (VM) and Attack Surface Management (ASM) program that supports External Attack Surface Management (EASM). This is a vital part of any modern ASM solution, but not all EASM capabilities are equal. Ensure your ASM can monitor and reduce cyber risk across your entire attack surface.
To learn more about key ASM capabilities, download the Essential Must-Haves for ASM from Qualys.
- Vulnerability Enumeration
According to CISA, vulnerability enumeration is defined as a security program’s ability to identify and report asset-specific vulnerabilities. Asset vulnerabilities are defined as operating systems, software and version, missing updates, misconfigurations, asset and vulnerability discovery, and requirements from CISA BOD 23-01.
How Qualys Helps with BOD 23-01
The Qualys Cloud Platform is built around one of the world’s most comprehensive vulnerability management capabilities with its’ own asset discovery & inventory, threat database, and now with natively integrated and continuous external attack surface monitoring, supporting both internal-known and unknown internet-connected assets. All these solutions are delivered via one platform and controlled with one dashboard. In many ways, the Qualys Cloud Platform was purpose-built to drive compliance with CISA BOD 23-01 before its’ inception. Here are just a few ways customers can leverage VMDR 2.0 with TruRisk, CyberSecurity Asset Management with EASM, Patch Management, and more to meet this recent directive.
Here’s how:
Continuous Asset Discovery of both internal and external-facing assets
CISA requires all Federal Civilian Executive Branch to “develop and maintain the operational capability to initiate on-demand asset discovery.” Thankfully, Qualys’ native asset discovery sensors eliminate blind spots that are created by unknown assets.
With Qualys CyberSecurity Asset Management, security practitioners leverage network scans, passive traffic monitoring, and External Attack Surface Monitoring (EASM) to find every asset and related IPs. In addition, security practitioners can monitor traffic in real-time to find new devices that connect to their network, even if they were not previously scanned or do not have a Qualys Agent. For cloud environments, organizations can use cloud connectors that list all cloud instances as part of their inventory, allowing security practitioners to find out which of these instances are not scanned for vulnerabilities and one-click workflow to scan them of deploying the Qualys agents.
Discover all known and unknown assets that connect to your global hybrid-IT environment
Comprehensive Asset Inventory with Cybersecurity and Business context
Qualys enables organizations to comprehensively inventory all hardware and software, classify and tag critical assets, providing a complete 360-degree view of a network with contextual information, including asset ownership and business criticality through bi-directional integration with CMDB.
Quickly achieve a categorized inventory with hardware and software details
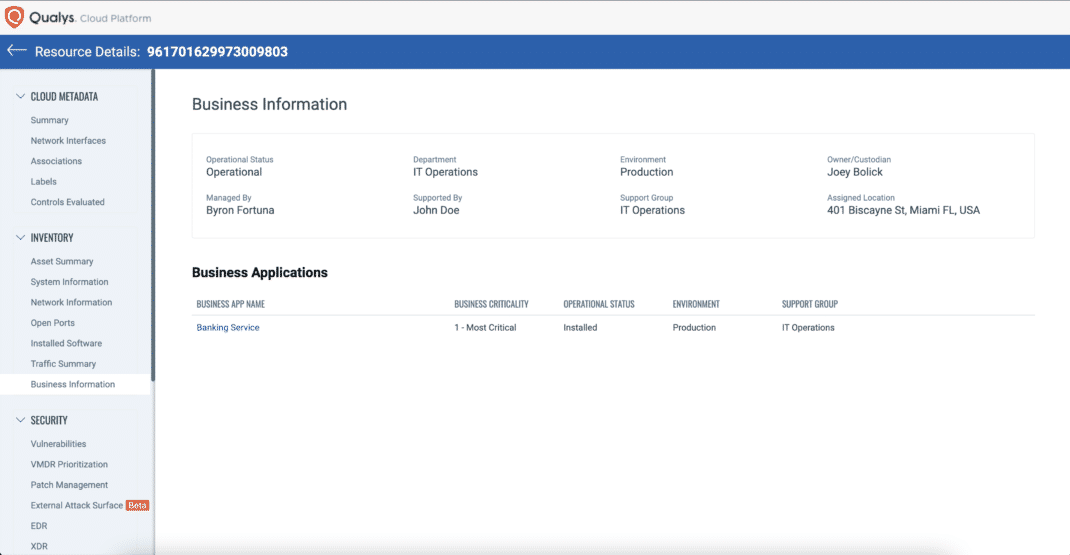
BOD 23-01 clearly states that asset visibility is a prerequisite for determining where to deploy any endpoint detection and response (EDR) solution. Qualys customers leverage CSAM’s purpose-built capability to monitor required security tools, such as EDR, and alert IT and security teams when missing. With CSAM, security practitioners are armed with playbooks that can be easily customized to define what agents and security software is required on what type of assets, hence ensuring overall coverage.
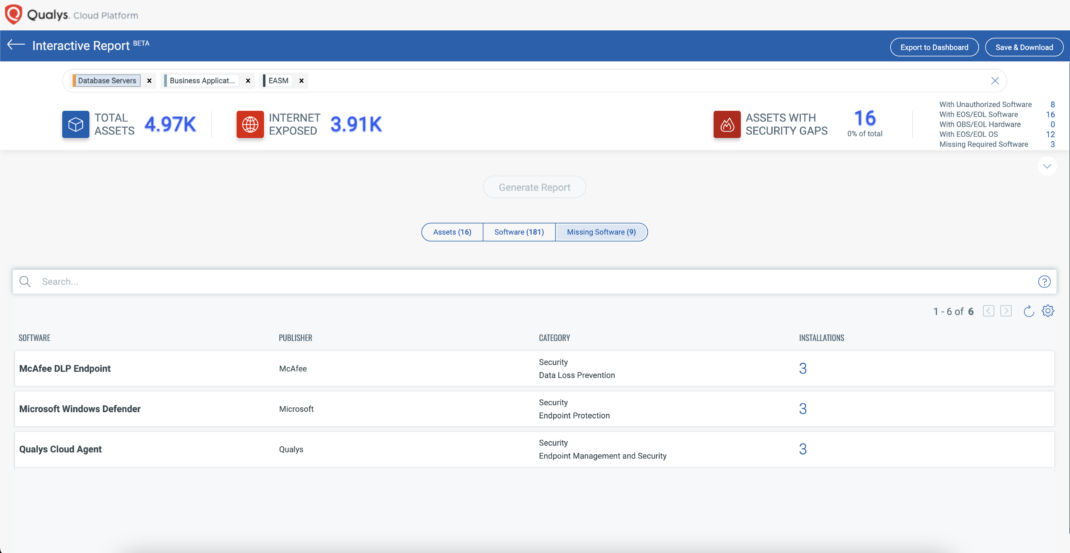
Continuous Vulnerability Management Detection and Response (VMDR) with Six Sigma accuracy
BOD 23-01 mandates that agencies “initiate vulnerability enumeration across all discovered assets, including nomadic / roaming devices, every two weeks to include servers, workstations, desktops, laptops, network devices.” This requires security practitioners to continuously detect software vulnerabilities across a wide range of asset categories.
Qualys Cloud Platform, combined with its powerful lightweight Cloud Agent, Virtual Scanners, and Network Analysis (passive scanning) capabilities bring together all four key elements of an effective vulnerability management program.
As the market leader in VM, Qualys VMDR empowers security practitioners to assess all assets for the latest vulnerabilities and applies the latest threat intel to prioritize remediation. VMDR also automatically detects the latest superseding patch for vulnerable assets, unifying VM and Patch Management together. In addition, cloud agents enable organizations to continuously monitor nomadic and roaming devices, allowing security practitioners to assess vulnerabilities without requiring VPN connections. By delivering all of this in a single app workflow, VMDR automates the entire process to accelerate an organization’s ability to respond to threats and prevent possible exploitation.
A look at how VMDR 2.0 with TruRisk supports a risk-based approach to VM
Automated Ingestion of Vulnerability Results in CDM
Finally, CISA BOD 23-01 requires agencies to “automate the ingestion of vulnerability enumeration results into CDM agency dashboard within 72 hours,” as well as “report vulnerability enumeration performance data into a CDM Dashboard.” In general, this criterion speaks to data management and reporting capabilities.
To meet this demand, the Qualys Platform is architected from the ground up to enable integrations with third-party systems and tools through highly scalable application programming interfaces (APIs). Qualys has customers that scan millions of assets and pull and push this information into various systems daily.
Unified Dashboard visibility in one single view
BOD 23-01 mandates agencies to a single view to “Improve Asset Visibility and Vulnerability Detection” This requires a Unified Dashboard continuous view capability so the security practitioners can continuously monitor progress across a wide range of assets.
Qualys Cloud Platform, combined with its powerful lightweight sensors gathers, correlates, and provides a Unified Dashboard for CISOs and Operational teams.
Using the Unified Dashboard, you can track CISA Vulnerabilities, impacted hosts, their status, and overall management in real-time. With trending enabled for dashboard widgets, you can keep track of vulnerability, and asset trends in your environment using the CISA BINDING OPP DIRECTIVE | 23-01 Unified Dashboard.
Read the Article (Qualys Customer Portal): CISA BINDING OPP DIRECTIVE | 23-01
Read the Article (Qualys Customer Portal): CISA Shields-UP | In-Depth View
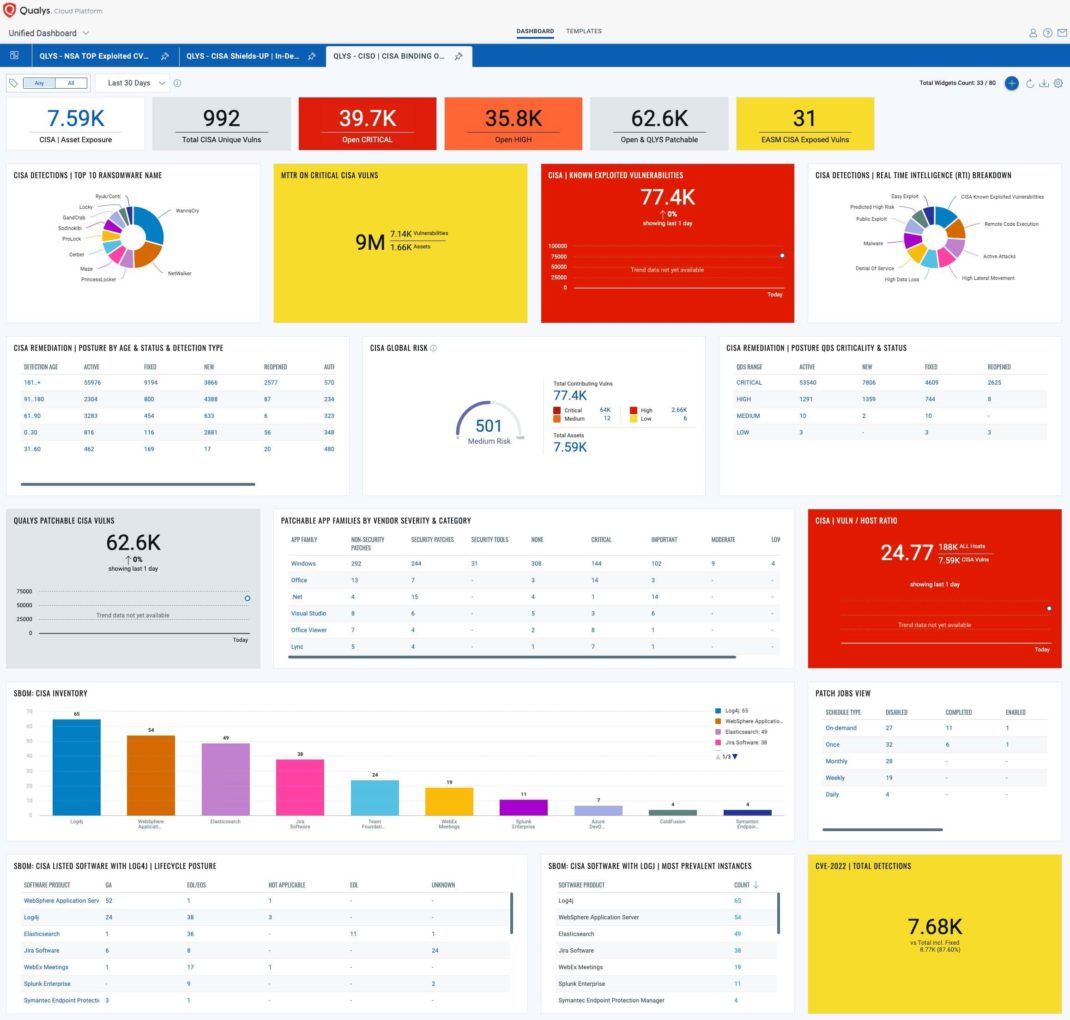
The Power of the Qualys Cloud Platform
As the attack surface expands, and malicious actors grow more innovative in their attacks, organizations will need to drive faster and more scalable security programs that meet the demands of regulators as reflected in CISA BOD 23-01 and the CISA Strategic Plan for 2023-2025. The Qualys Cloud Platform is one of few platforms today that can help organizations and security stakeholders keep pace with CISA requirements with continuous asset visibility, advanced attack surface management, patching, Unified Dashboard visibility and more. Rely on Qualys for scalable protection for on-premises, remote endpoints, and cloud environments.
Contributors
- Felix Jimenez Saez, Director, Product Management
- Pablo Quiroga, Director, Product Management.
To learn more about Qualys and how the Qualys Cloud Platform can help security practitioners comply with CISA guidelines, go to: https://www.qualys.com/apps/cybersecurity-asset-management/. Want to how see for yourself? Give EASM a try here: https://www.qualys.com/forms/cybersecurity-asset-management
This post was first first published on Qualys Security Blog’ website by Kunal Modasiya. You can view it by clicking here

