Reflecting on (One of) Gartner’s Cybersecurity Predictions
One of the stand outs across the eight predictions:
Late last month, Gartner released its top eight cybersecurity predictions for 2022-23, encouraging cybersecurity leaders to use their eight predictions as a guide to build a security strategy around.
Does this pose the question, should we be less worried about our data security and more worried about our personal safety?
“By 2025, threat actors will have weaponized operational technology environments successfully to cause human casualties. Attacks on OT – hardware and software that monitors or controls equipment, assets and processes – have become more common and more disruptive. In operational environments, security and risk management leaders should be more concerned about real world hazards to humans and the environment, rather than information theft.”
But what happens when next time the goal is to create problems? Casualties even.
The impact to a nation state if attacked via their critical infrastructure could be catastrophic. We only need to look back to 2021 to the Colonial Pipeline ransomware attack. Despite the intended target being the billing infrastructure, operations were halted to contain the attack, and panic spread to the public causing widespread petrol shortages. With U.S President Joe Biden, declaring a state of emergency 2 days after the attack had occurred. The attackers responsible, DarkSide, released a statement saying, “our goal is to make money, and not creating problems for society.”
In the opening keynote at the Gartner Security & Risk Management Summit in Sydney, Australia, Senior Director Analyst Richard Addiscott stated “We can’t fall into old habits and try to treat everything the same as we did in the past. Most security and risk leaders now recognize that major disruption is only one crisis away. We can’t control it, but we can evolve our thinking, our philosophy, our program and our architecture.”
What is required from organisations to protect not only their company, and data, but the safety of the public?
As outlined by Gartner, “we can’t control it, but we can evolve our thinking.” Is it time to pivot our cyber defenses from detection to prevention based cybersecurity?
We have created a peculiar 21st century problem for ourselves, a huge attack surface for cybercriminals. Organizations are so tightly integrated together, and are part of complex technological ecosystems, with the digital information being shared and communicated with business partners, customers, supply chains, and as local and remote workers. We know that detection based defenses are no longer capable of consistently defeating today’s cybercriminals.
Looking forward to protecting the safety of our critical industries, a truly effective defense must utilize prevention technologies such as transformation as well as detection. Forcepoint’s new approach to cybersecurity is game-changing, a true Zero Trust approach to exchanging information without malware. It has the potential to deliver complete immunity from malware now and in the future. Transformation is the logical evolutionary next step for defenses because it is the best way to be certain that a file is threat-free, robbing the attacker of their ability to hide from detection and cause unpredicted destruction.
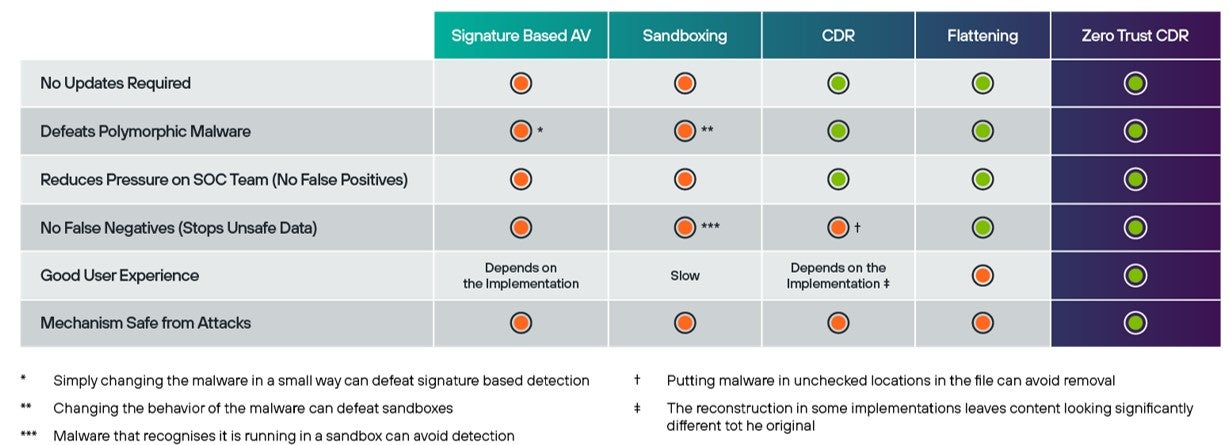
Start your Zero Trust cyber strategy today with Forcepoint.
For organisations that are responsible for the critical infrastructure on which we all depend, the IT/OT boundary has long been a potential Achilles heel. At Forcepoint we believe the risk is best mitigated utilising a combined hardware and software solution that includes, both a High Speed Verifier or Data Diode and Zero Trust CDR.
Related Content:
This post was first first published on Forcepoint website by Joanna Crossley. You can view it by clicking here

