XDR best of breed, and how an open architecture will get you there
XDR best of breed, and how an open architecture will get you there
ED YOUNG
The security landscape is continually changing and the race to stay ahead is often one of both victory and failure. As organizations globally continue to expand, security professionals are struggling to update operations quickly enough to ensure effective monitoring and response to incidents in their environment. The lack of security professionals makes this even more challenging. Patching systems, scanning for vulnerabilities, protecting against malware and viruses are essential and just plain smart. Why make it easy for the attacker when you can eliminate paths of entry by keeping current with your security practices?
When attackers breach the network, and yes they will, that is when we need to know there is a real breach with good visibility and alerting based on security telemetry from multiple sources within the enterprise. You have invested time, money and resources in acquiring multiple best in class products to enable your teams to build a process and deliver a more complete security solution. Extended Detection and Response (XDR) is that security solution. A best of breed XDR architecture is the continued evolution of current capabilities in threat detection and response.
“Think of XDR as a modern SOC-in-a-box designed to integrate controls, normalize telemetry, provide advanced analytics and automate responses.”
– Jon Oltsik, Senior Principal Analyst – ESG
Some have tried to define XDR as an extension of EDR, while others claim that XDR is a product that will be delivered from a single vendor. EDR is an important piece of the security solution, but there are many other pieces to the puzzle. XDR relies on the ingestion of data from a variety of sources but needs to be flexible enough to work with the sources that are already deployed in the customer environment. A recent survey found that 60% of the executives polled said they use two to four vendors as part of their XDR Solution (18% claimed 5-7)(1). There is no need to rip and replace these solutions to get the XDR value that an open architecture can provide when you are data driven.
The ThreatQ Platform and product suite were built to meet an organization’s XDR need and empower their teams to work more collaboratively and efficiently. The DataLinq Engine is designed to deliver an effective XDR outcome, while working with your existing security products your teams know and work with today. You chose the vendors, you established the process and ThreatQ will enable you to maximize the value by integrating systems to extend their capabilities.
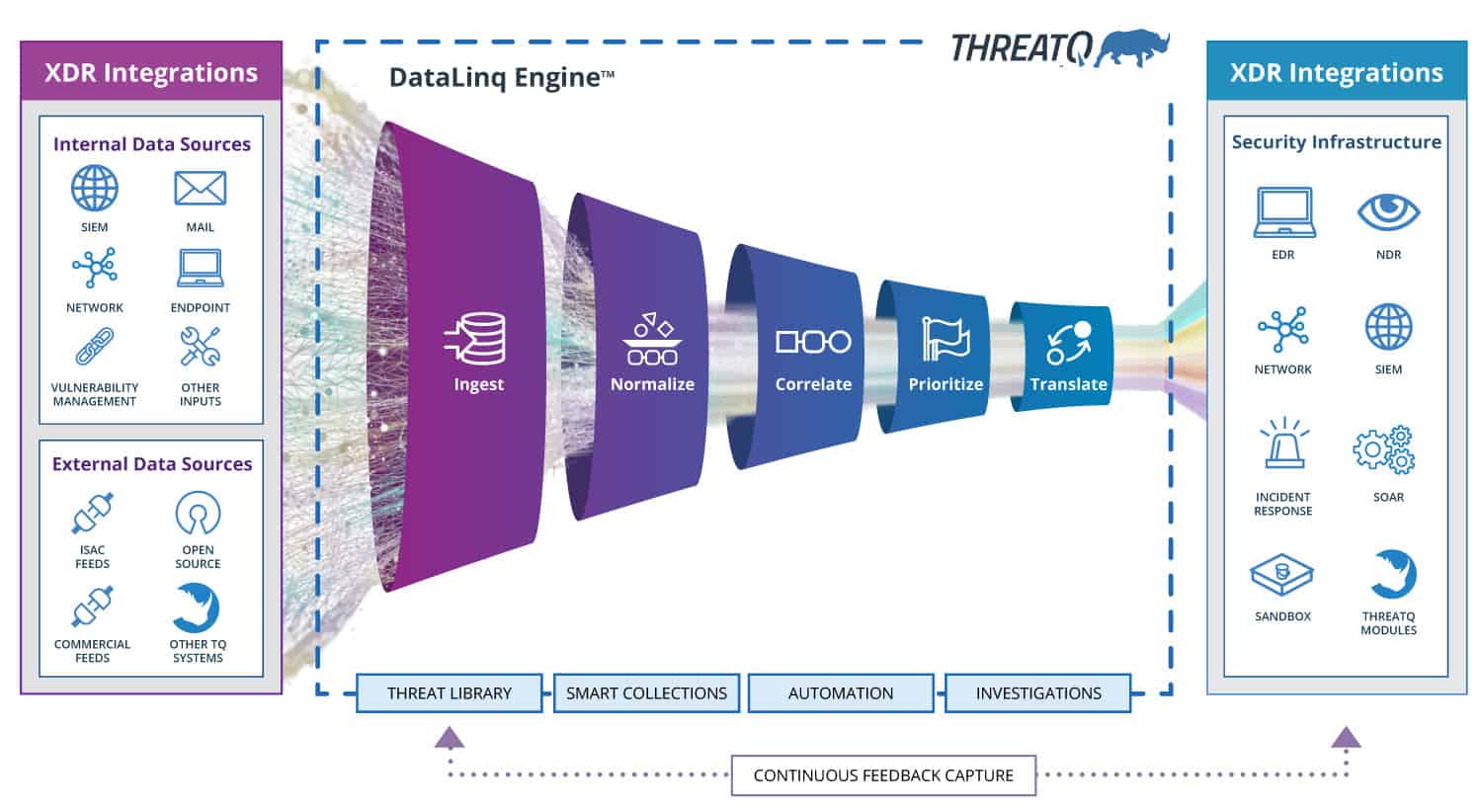
The ThreatQ DataLinq Engine will ingest Security Telemetry from both Internal and external sources, normalize the data and correlate the relationships to be prioritized.
The data can then be distributed to other systems and other teams, providing cross team visibility and collaboration. Partnering with the best of breed solutions (https://marketplace.threatq.com), an open API and the ability to create custom integrations to support the customer use case, ThreatQ enables the “D” in XDR.
The ThreatQ DataLinq Engine, while providing constantly updated threat intelligence, will eliminate the noise by automatically deduplicating and correlating the data and exposing the threats that need to be prioritized. Smart collections and custom scoring enables the customer to further elevate that visibility to the proper teams.
ThreatQ provides the tools for the security professional to be more efficient and the ability to respond in a timely manner. Capturing and storing data related to sightings, campaigns, investigations and resolutions provides a continuous information source to be used for learning and improvement to your security process. The data can be used for simple automation or more complex orchestration with the ability to initiate the process based on criteria that is important to you, reducing dwell time by detecting and responding to threats more quickly.
An example use case could include setting a Smart Collection to group indicators based on a relationship to a certain adversary that has been seen in the environment. The data returned can be automatically enriched against a single source or multiple sources to collect additional indicators and attributes. The enriched data can then be shared with the team for a follow on task.
Other use cases may include the detection of unexpected behavior on the network such as traffic to/from a certain location. Adding data previously ingested and correlated by the DataLinq Engine will assist in providing context from threat intelligence and security telemetry detected from sensors deployed on the network that show sightings and identify the affected systems.
By applying Smart Collection and Custom Scoring, ThreatQ will prioritize the threats that are important for remediation. That could be simple automation to quarantine the device or more complicated steps to remediate the threat by shutting down a service, removing the malware, restoring the system, submitting an alert, create a ticket or initiate an investigation. The Extended Detection and Response process could involve any number of tools and should provide cross team visibility for a more complete security solution.
The SOC of the future is data-driven and ThreatQ’s open architecture combined with the extensive partnerships through our integrations ecosystem will enable a best of breed XDR solution for your security teams.
Want to jump ahead? Download your copy of Accelerate Threat Detection & Response with DataLinq Engine.
- Pulse Survey October 12, 2021
The post XDR best of breed, and how an open architecture will get you there appeared first on ThreatQuotient.

