5 Steps to SASE: Safeguarding the Usage of Data Everywhere
In our first two episodes about the 5 Steps to SASE, we discussed the most common ways organizations begin using SASE: protecting access to the web and cloud and controlling access cloud & private applications. While many SASE vendors see access as the finish line, Forcepoint sees it as the starting line.
Virtual Series – 5 Steps to SASE: Step 3 June 9
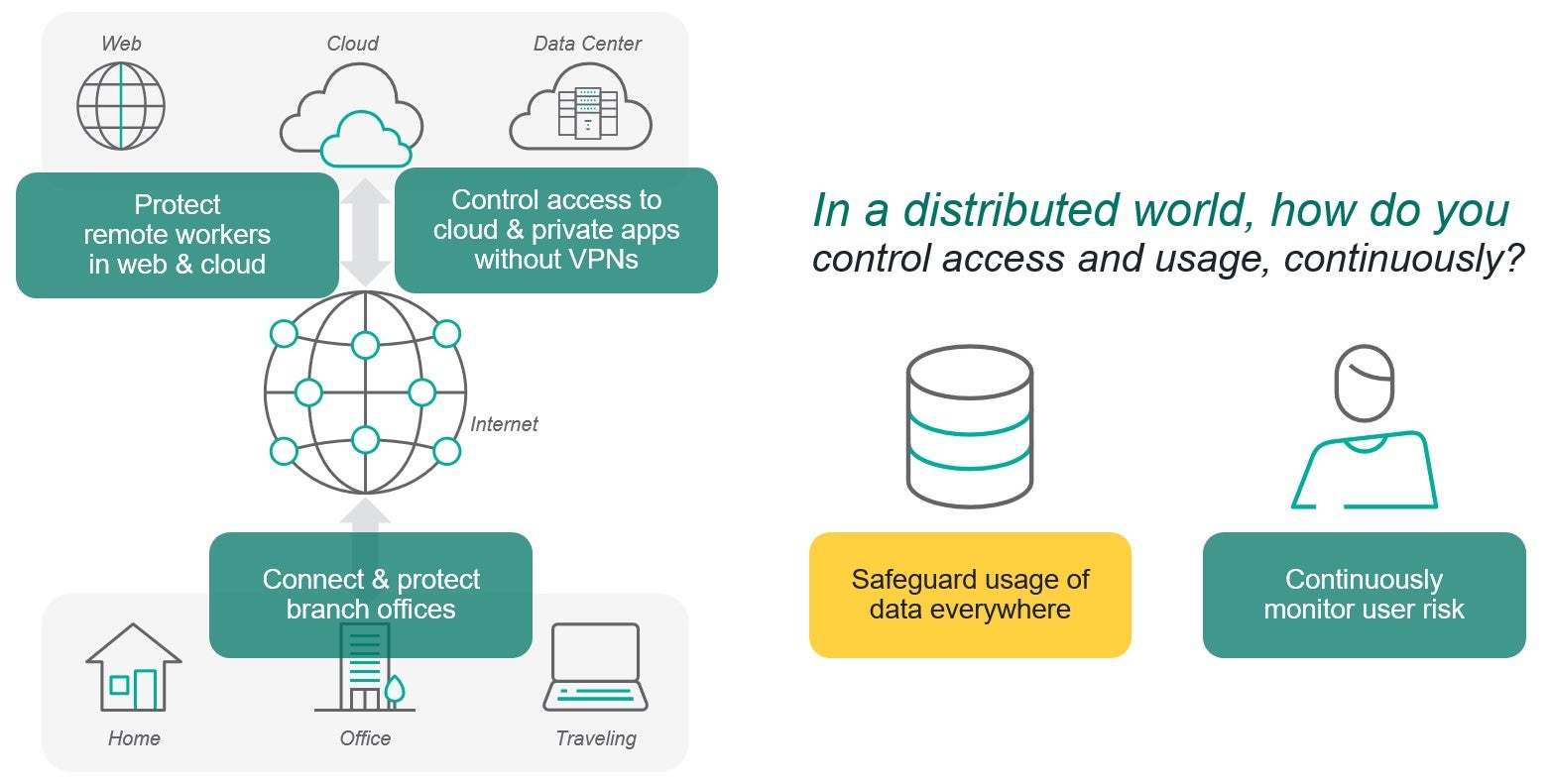
You see, we believe cybersecurity is all about enabling people to use information safely. To do that, not only do you have to protect how people get to data such as spreadsheets in an app, you also have to safeguard how such a spreadsheet can be used even after it’s been downloaded. We call this approach Data-first SASE.
Erik doesn’t just talk about the real-world implications of cybersecurity, he lives them.
To talk about how SASE can deliver data protection seamlessly from the endpoint through the network into the web and cloud, I’ll sit down with Erik Scoralick, one of Forcepoint’s most senior global Consulting Solutions Engineers. Erik has spent years helping highly distributed organizations deploy sophisticated technologies like data loss prevention (DLP), cloud application security brokers (CASB), secure web gateways (SWG) and more.
No slides, just a good conversation. We hope you enjoy it as well. Register for the step 3 conversation today.
We’ll discuss how today’s remote workers have changed how organizations think about protecting data, in particular the importance of enforcing data security policies consistently everywhere, across every channel. As a bonus, we’ll also touch on how applying Zero Trust principles—requiring explicit permission for every usage of sensitive data—are playing an increasing role as well.
This post was first first published on Forcepoint website by Jim Fulton. You can view it by clicking here

