Unify Network and Security Operations | NetSecOps Collaboration | Riverbed
For decades network operations and security operations teams have functioned separately. That’s starting to change and with good reason, even though their fundamental goals are diametrically opposed. The network team focuses on ensuring access to applications and services while the security team focuses on locking down data and limiting connectivity. But, EMA has found strong evidence that over the last couple of years network operations teams are working more closely than ever with IT security teams. In fact, 63% of enterprises have formalized collaboration between the network team and the security team.
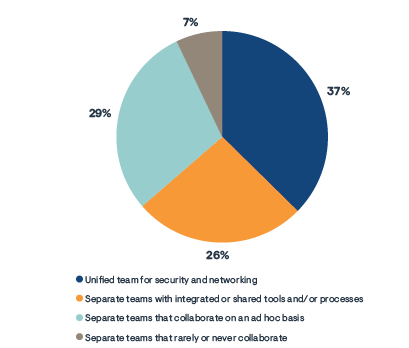
Figure 1. Relationships between today’s network ops and security ops teams. Only 37% can be considered NetSecOps!
What’s more, they found a very strong correlation between close NetOps and SecOps (henceforth NetSecOps) collaboration and overall network operations success. Successful teams are very likely to have converged groups or share integrated tools and processes. Bridging the gap between groups is more likely to ensure a secure, highly performant network. Here are five reasons why your Network Operations and Security Operations teams should collaborate in a more formal manner:
1. Better network performance. Data shows that organizations with unified NetSecOps teams spend less time on reactive troubleshooting and more time on proactive problem prevention. This enables collaborative teams to focus on improving network performance, leading to a better user experience and business results.
Security system problems and security incidents are common root causes of IT service problems, so by joining forces, NetSecOps teams are also better equipped to root out security problems that affect network performance. For example, DDoS issues that take the network offline might formerly be considered a network issue but can now be properly diagnosed as a security problem and can be mitigated more quickly.
2. Accelerated security incident detection and response. Unified NetSecOps teams (36%) and teams that share tools and processes (27%) are focused more often on accelerating security incident detection and response. These teams identify and respond more quickly to incidents and breaches than separate NetOps and SecOps teams. Together they can investigate malware, breaches, and misconfigurations that can affect both security and performance. Surprisingly, infrastructure management (SNMP, WMI, etc.) is a key tool of unified teams. It can detect unusual activity on a network device, such as saturation of an interface by an attack or a misconfiguration and is not a tool that is typically in the security toolbox.
3. Cost efficiency. A side benefit of this collaboration is both operational and capital cost efficiency. By sharing tools—full-fidelity flow monitoring, packet capture and analysis, network infrastructure monitoring, NACs, etc.—then teams share one solution, and don’t have to purchase two very similar products. That also means there’s only one support contract and fewer devices to support in the data center (less power costs, rack space, etc.). It’s a win all around: faster, more secure network performance at a cost savings!
4. Faster response to business change. When two teams are comfortable working together, they get comfortable planning for changes together—like cloud migrations or work for home (WFH). Integrated plans are always more comprehensive and reduce the risk that change introduces, which brings me to my last benefit…
5. Risk reduction. When network operations and security operations work well together, the outcome is risk reduction. This is the ultimate measure of success for any NetSecOps team. As the adage goes, more hands make light work. Even if NetOps aren’t complete security experts, they are bound to notice some issues, because they are covering different ground, often in the network’s deepest recesses. And, as we established above, incident detection and response is accelerated, then malware and the like stays in the network for a shorter time. All of this is goodness when you have more brains thinking security.
The benefits of unifying your NetOps and SecOps teams should be clear by now. Ensuring your integrated NetSecOps team has the tools to enable full visibility from cloud to edge, assuring your network is always secure and high performing. Your enterprise-wide visibility toolset should include:
- Full-fidelity flow data (no sampling)—enterprise-wide traffic and security visibility; behavioral analysis; threat detection; threat hunting
- Packet data, not just metrics—network and application analysis; forensic analysis; encrypted traffic analysis; certificates analysis, etc.
- Infrastructure management (SNMP, WMI, CLI, API, synthetics, etc.)—performance metrics; configuration/change management; device compliance; path analysis; network diagrams
To learn more about unifying your network and security operations teams and the benefits you can achieve, check out this EMA analyst paper, The Convergence of Network and Security Operations.
This post was first first published on Riverbed Blog’s website by Heidi Gabrielson. You can view it by clickinghere

