New Security Approach to Cloud-Native Applications
”IDC predicts, by 2025, nearly two-thirds of enterprises will be prolific software producers with code deployed daily, over 90% of new apps cloud native, 80% of code externally sourced, and 1.6 times more developers”

With on-premises infrastructure, securing server workloads and applications involves putting security controls between an organization’s network and the outside world. As organisations migrate workloads (“lift and shift”) to the cloud, the same approach was often used. On the contrary to lift and shift, many enterprise businesses had realized that in order to use the cloud efficiently they need to redesign their apps to become cloud-native. Cloud native is an approach to building and running applications that exploits the advantages of the cloud computing delivery model. Cloud native development incorporates the concepts of DevOps, continuous delivery, microservices, and containers.
Monolithic Apps vs Cloud Native Apps
Cloud Security Posture Management (CSPM):
So, how do you ensure the security of your cloud–native applications?
Successful protection of cloud-native applications will require a combination of multiple security controls working together and managed from one security platform. First, the cloud infrastructure where is the cloud-native application is running (containers, serverless functions and virtual machines) should be assessed for security misconfigurations (security posture ), compliance and for known vulnerabilities. Second, securing the workloads needs a different security approach. Workloads are becoming more granular with shorter life spans as development organizations adopt DevOps-style development patterns. DevOps delivers faster software releases , in some cases, several times per day. The best way to secure these rapidly changing and short-lived cloud-native workloads is to start their protection proactively and build security into every part of the DevOps lifecycle.
Cloud Workload Protection Platforms (CWPP):
The biggest cloud breaches are caused by customer misconfiguration, mismanagement, and mistakes. CSPM is a class of security tools to enable compliance monitoring, DevOps integration, incident response, risk assessment, and risk visualization. It is imperative for security and risk management leaders to enable cloud security posture management processes to proactively identify and address data risks.
CWPP is an agent-based workload security protection technology. CWPP addresses unique requirements of server workload protection in modern hybrid data center architectures including on-premises, physical and virtual machines (VMs), and multiple public cloud infrastructure. This includes support for container-based application architectures.

What is MVISION CNAPP
MVISION CNAPP is the industry’s first platform to bring application and risk context to converge Cloud Security Posture Management (CSPM) for multi public cloud infrastructure, and Cloud Workload Protection (CWPP) to protect hybrid, multi cloud workloads including VMs, containers, and serverless functions. McAfee MVISION CNAPP extends MVISION Cloud’s data protection – both Data Loss Prevention and malware detection – threat prevention, governance and compliance to comprehensively address the needs of this new cloud-native application world thereby improving security capabilities and reducing the Total Cost of Ownership of cloud security.
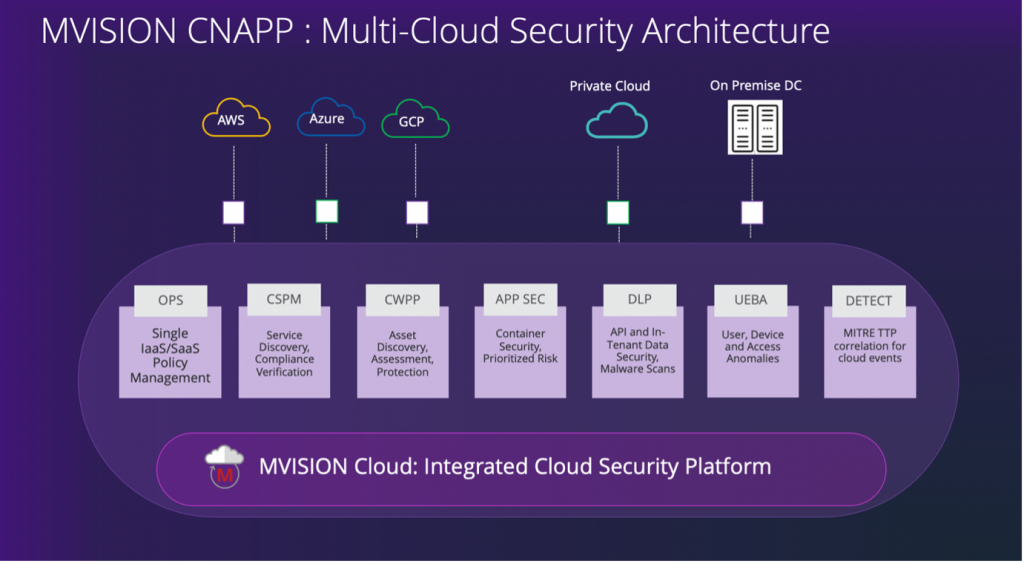
7 Key elements of MVISION CNAPP:
1. Single Hybrid multi cloud security platform: McAfee MVISION Cloud simplify multi-cloud complexity by using a single, cloud-native enforcement point. It’s a comprehensive cloud security solution that protects and prevents enterprise and customer data, assets and applications from advanced security threats and cyberattacks across multiple cloud infrastructures and environments.
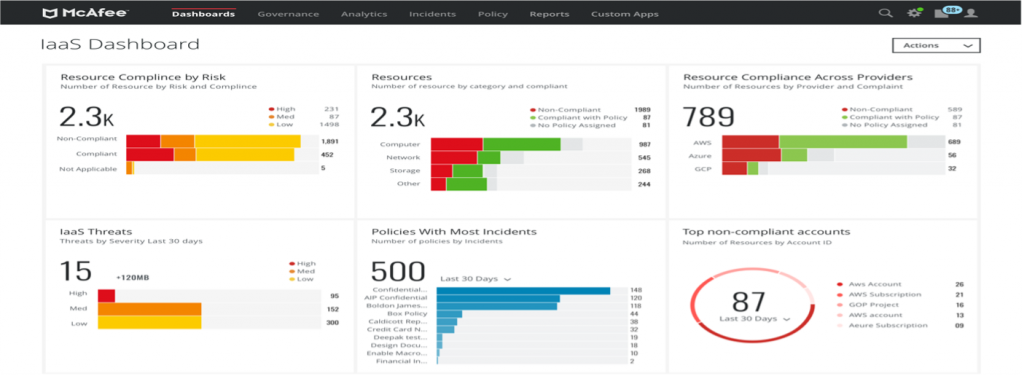
2. Cloud Security Posture Management: McAfee MVISION Cloud provide a continuous monitoring for multi cloud IaaS / PaaS environments to identify gaps between their stated security policy and the actual security posture. At the heart of CSPM is the detection of cloud misconfiguration vulnerabilities that can lead to compliance violations and data breaches.
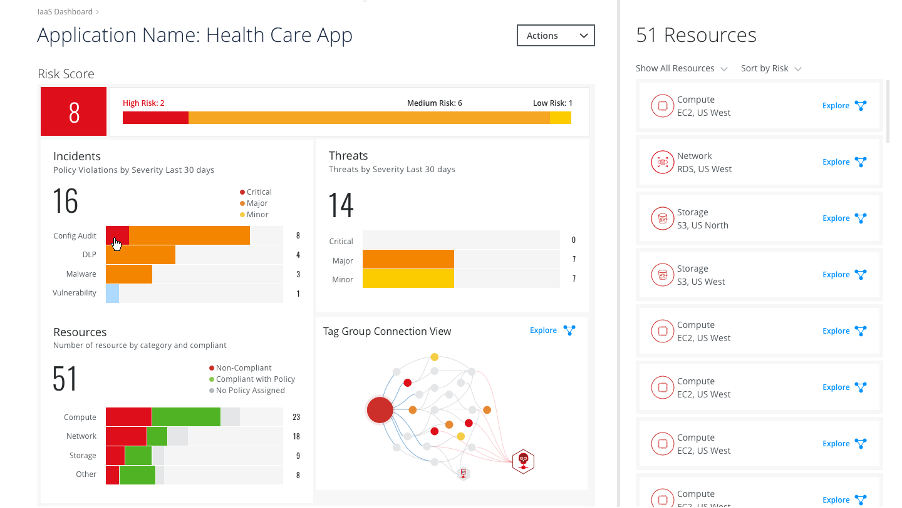
3. Deep discovery and risk based application:You can’t protect what you can’t see. Discovering all cloud resources and prioritise them based on the risk. MVISION CNAPP uniquely provided deep discovery of all workloads, data, and infrastructure across endpoint, networks, and cloud. If you can quickly understand those risks relative to each other, you can quickly prioritize your remediation reducing overall riskMas quickly as possible.
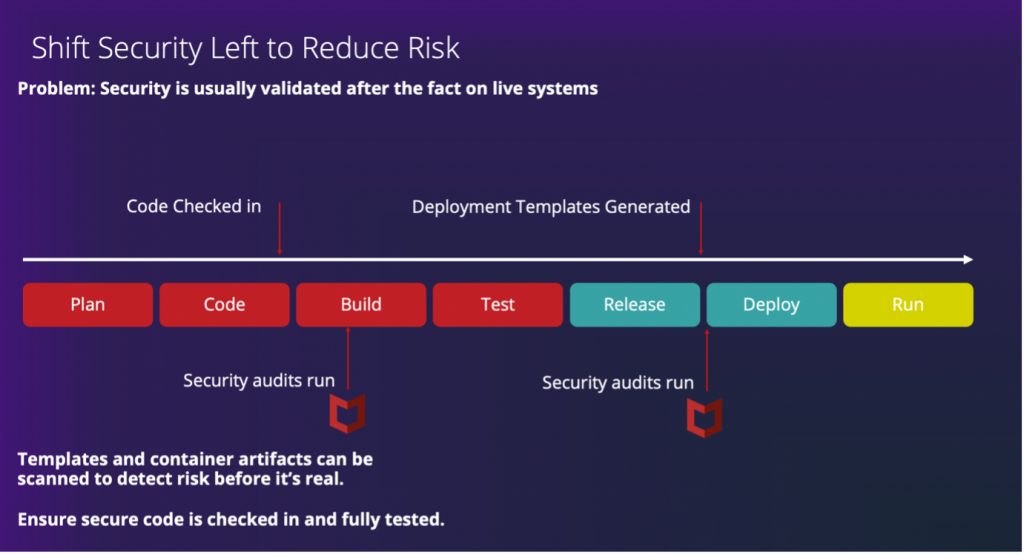
4. Shift Left posture and vulnerability:By moving security into the CI/CD pipeline and make it easy for developers to incorporate into their normal application development processes and ensuring that applications are secure before they are ever published reduces the chance of introducing new vulnerabilities and minimizing threats to the organization.
6. Unified Threat Protection:CWPP unifies threat protection across workloads in the cloud and on-premise. Including OS Hardening, Configuration and Vulnerability Management, Application Control/Allow-Listing and File Integrity control. It also synthesizes workload protections and account permissions into the same motion. Finally, by connecting cloud-native application protection to XDR, you are able to have full visibility, risk management, and remediation across your on-premise and cloud infrastructures.
5. Zero Trust policy control: McAfee’s CNAPP solution supported by CWPP focus on Zero Trust network and workload policies. This approach not only allows you to gain analytics about who is accessing your environment and how an important component of your SOC strategy but it also ensures that people and services have appropriate permissions to perform necessary tasks.
Business value:
- One Cloud Security Platform for all your CSPs
- Scan workloads and configurations in development and protect workloads and configurations at runtime.
- Better security by enabling standardization and deeper layered defenses.
- The convergence of CSPM and CWPP
7. Governance and Compliance:The ideal solution for protecting cloud-native applications includes the ability to manage privileged access and address threat protection for both workloads and sensitive data, regardless of where they reside
The post New Security Approach to Cloud-Native Applications appeared first on McAfee Blogs.
IDC FutureScape: Worldwide IT Industry 2020 Predictions
https://www.idc.com/research/viewtoc.jsp?containerId=US45599219
This post was first first published on Enterprise – McAfee Blogs’s website by Boubker Elmouttahid. You can view it by clicking here

