Phish Found in SEG-Protected Environments Week ending February 12, 2021
100% of the phish seen by the Cofense Phishing Defense Center (PDC) have been found in environments protected by Secure Email Gateways (SEGs), were reported by humans, and analyzed and dispositioned by Cofense Triage.
Are phishing emails evading your Proofpoint Secure Email Gateway? The following are examples of phishing emails recently seen by the PDC in environments protected by Proofpoint.
Cofense solutions enable organizations to identify, analyze and quarantine email threats in minutes.
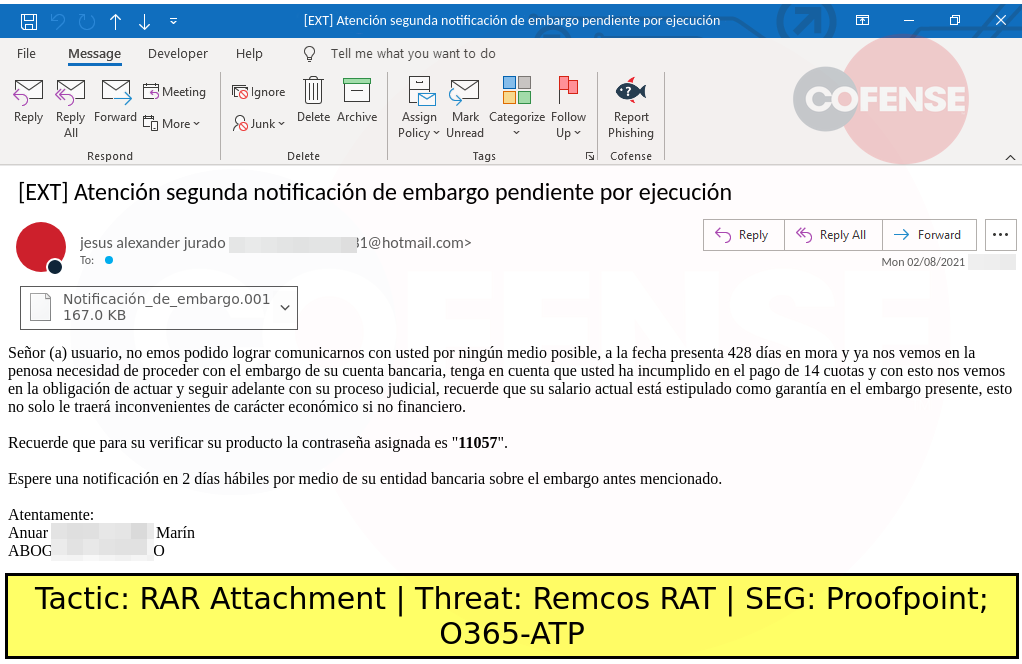
DESCRIPTION: Finance-themed emails found in environments protected by Proofpoint and Microsoft Defender O365 deliver an attached malware downloader that downloads Amadey and runs Remcos RAT.
TYPE: Ava_Maria_Stealer
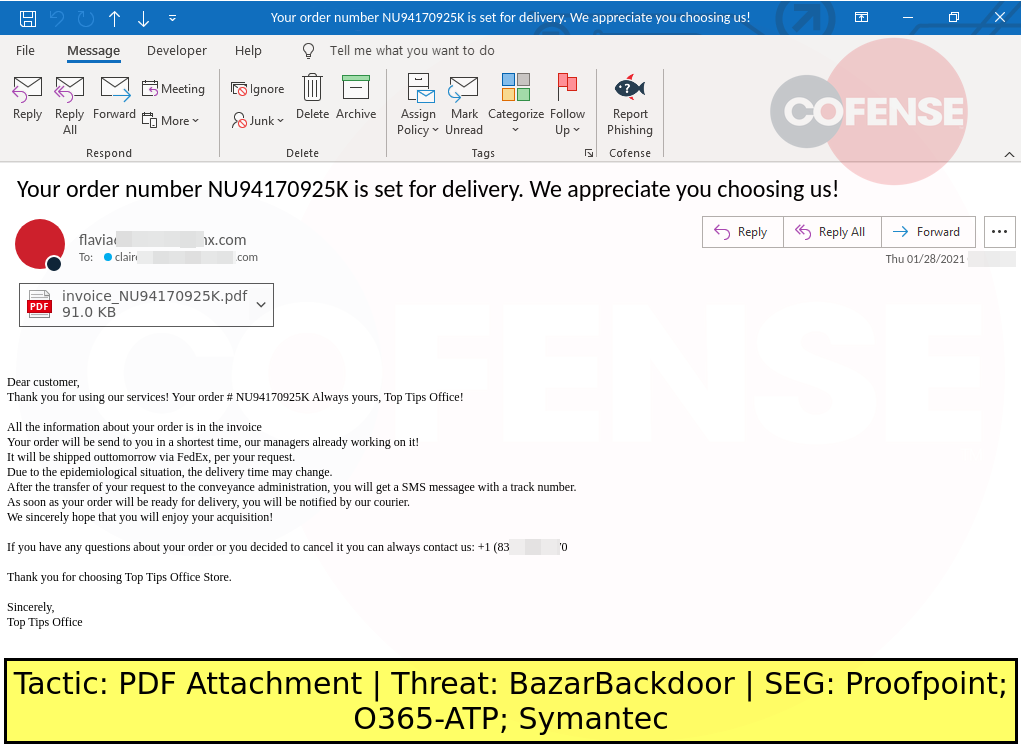
DESCRIPTION: Invoice-themed emails found in environments protected by Proofpoint, Microsoft Defender O365 and Symantec deliver BazarBackdoor via PDF attachments. The attached PDF redirects to a site that collects invoice order numbers. Once the order number is entered, it redirects to a payload URL that downloads an Office macro. The Office macro downloads and runs BazarBackdoor.
Malicious emails continue to reach user inboxes, increasing the risk of account compromise, data breach, and ransomware attack. The same patterns and techniques are used week after week.
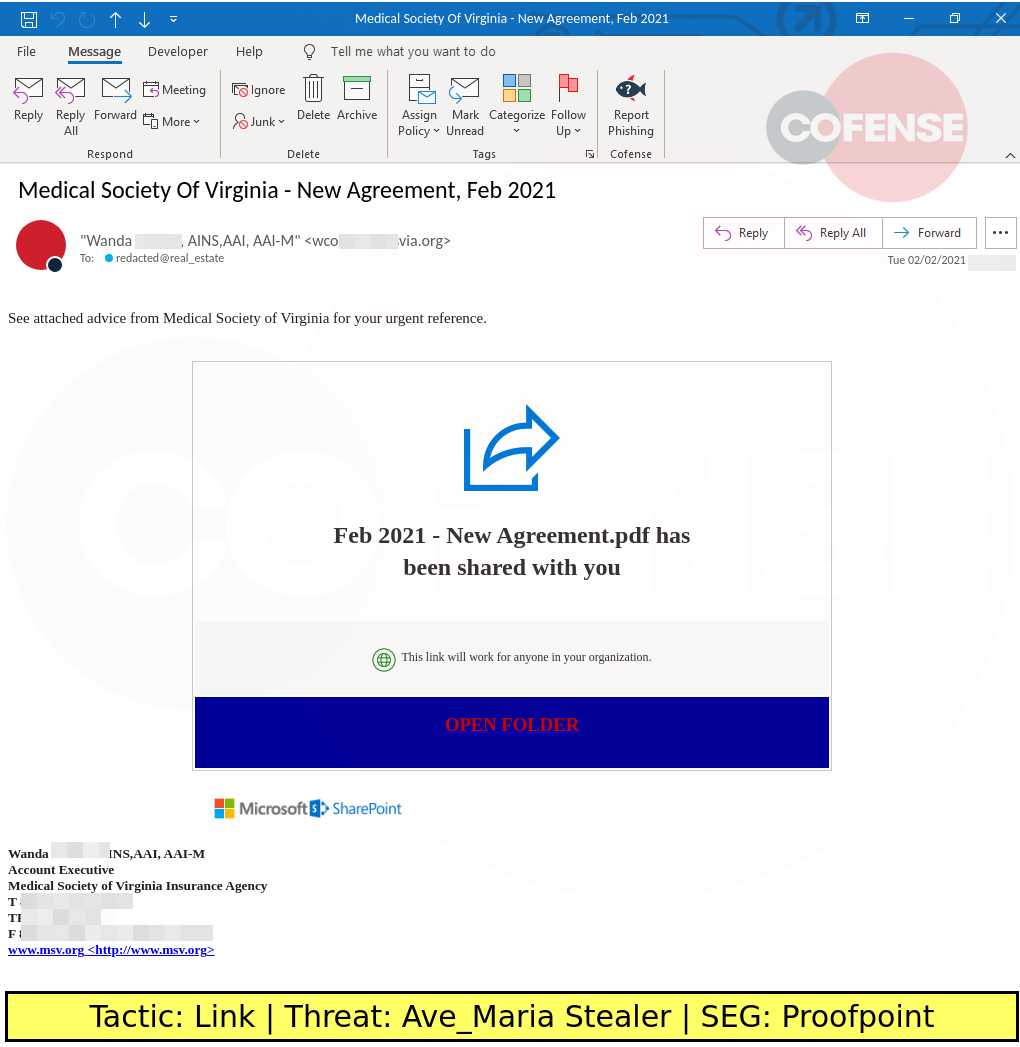
DESCRIPTION: Notification-themed emails found in environments protected by Proofpoint deliver Ave_Maria stealer via embedded links. The embedded links download an Office macro that downloads an Ave_Maria executable.
Cofense recommends that organizations train their personnel to identify and report suspicious emails. Cofense PhishMe customers should use SEG Miss templates to raise awareness of these attacks. Organizations should also invest in Cofense Triage and Cofense Vision to quickly analyze and quarantine the phishing attacks that evade Secure Email Gateways.
Recommendations
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats.
Interested in seeing more? Search our Real Phishing Threats Database.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.
This post was first first published on Cofense’s website by Cofense. You can view it by clicking here