Bridge the Gap between Security and IT in Cloud Workload Protection
It often feels as though Security and IT are trying to build the same house from different blueprints. Security works tirelessly to stay ahead of a threat landscape that is moving at warp speed by managing hundreds of thousands of vulnerabilities. Meanwhile, IT tries to strike a precarious balance between the directive to patch the tidal wave of vulnerabilities and its fundamental duty of keeping infrastructure and applications up and running to serve the business.
Both teams are on difficult missions that often appear incompatible. Friction seems inevitable, and it’s no wonder that many organizations struggle to bridge the gap between these two critical entities. Getting these two teams to start working off the same blueprint can change the game when it comes to security-oriented efforts like vulnerability assessment and remediation—and that objective that has been at the heart of the development of VMware Carbon Black Cloud Workload.
Vulnerability management—a foundational component of cloud workload protection—is traditionally rife with perils. With the increasingly high volume of vulnerabilities in the average enterprise, patching everything simply isn’t feasible. There are not enough resources and not enough time. And without an effective approach to risk assessment and prioritization, your vulnerability management effort may feel akin to pushing water uphill with a rake.
It’s this often-futile effort that has led many IT teams to reluctantly take part in vulnerability management efforts rather than being an active, willing participant. IT is most often concerned about infrastructure risk and downtime. They have a day (and often night) job, and they can’t afford unnecessary and unplanned tasks. They need to know why they’re being asked to patch the things they’re patching.
Imagine your Security team sends two patch lists to your infrastructure admins for remediation:
- The first list starts with SOFTWAREPATCH14-2020, which covers a vulnerability with a Common Vulnerability Scoring System (CVSS) score of 8 and has no known exploits.
- The second list starts with SOFTWAREPATCH88-2020, which fixes a vulnerability score of 99 that has been used in a breach, is leveraged by more than 200 pieces of malware, and has at least 10 published exploits.
Which patch list do you think your infrastructure admin will have more confidence in?
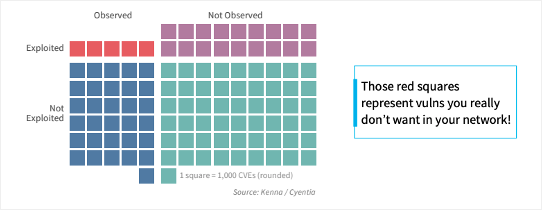
Here’s the reality: Only 5 percent of vulnerabilities are both observed and known (see Figure 1). IT needs to see justification that the vulnerabilities they spend their limited time on are ones that are actually going to make a difference to their company’s security posture. We understood that to achieve this, we needed to deliver a solution that:
- Is able to accurately, efficiently identify the vulnerabilities that matter
- Provides evidence of why vulnerabilities are scored as they are
Carbon Black Cloud Workload does exactly this with the inclusion of Kenna Security’s risk prioritization technology.
Every vulnerability in our workload protection solution receives a unique Kenna risk score. This score isn’t just a simple pass-through of static scoring like CVSS. Instead, this data-science-driven risk score looks at more than 15 threat and exploit intelligence feeds and evaluates multiple variables, using predictive modeling that forecasts the weaponization of a vulnerability, the exploitability of a vulnerability, the availability of a recorded exploit in exploit sources, and more. (You can learn more about the ins and outs of this risk score in our recent blog, Risk Score 101: What to look for in a Risk Score.)
This proven scoring methodology is accompanied by easy-to-understand justifications within the Carbon Black Cloud Workload user interface that indicate characteristics uncovered by Kenna’s vulnerability risk assessment, such as whether or not the vulnerability is easily exploitable, whether it is actively exploited by malware, and more (see Figure 2).
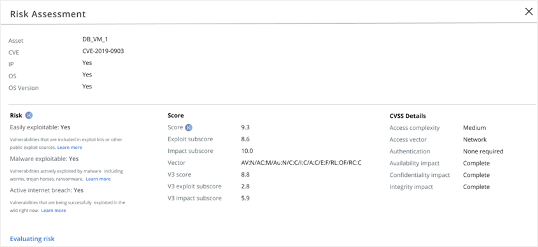
This level of justification or risk score transparency drastically reduces questions and increases confidence on the IT side. As a result, the traditional friction between security and IT starts eroding. For once, Security and IT have the information necessary to work together to eliminate the riskiest vulnerabilities and avoid opinion-driven arguments by relying on clear evidence. No more weekly patch debates. No more friction.
Infrastructure admins understand why they’re being asked to remediate vulnerabilities and believe those actions will make a difference. IT leaders can have confidence that resource allocation to vulnerability management is efficient. Suddenly, these two teams are working from the same blueprint, and the house they’re building is set up to be both sturdy and safe.
With Carbon Black Cloud Workload and Kenna, your Security team is relieved, your IT is empowered, and your organization is more secure.
Register now for our upcoming webinar, Vulnerability Prioritization: Bridging the Gap Between Security and IT with Tom Corn, SVP of Security Products at VMware, and Jason Rolleston, Chief Product Officer at Kenna Security to learn more about Carbon Black Cloud Workload and Kenna Security
The post Bridge the Gap between Security and IT in Cloud Workload Protection appeared first on VMware Carbon Black.

