Informed Decision Making Regardless of the Tools or Controls in Use
The cyber security industry has been its own enemy as each security vendor focuses on their own specific toolset and unique detection algorithm, lacking a single, holistic repository of adversary tactics, techniques and procedures (TTPs). As a result, security organizations are constrained with fragmented views caused by “tool creep.” Threat detection has often been based on individual signatures or binary indicators of compromise, making it easier for threat actors to use fast changing tactics or “living off the land” techniques to take advantage of vulnerabilities.
A decade ago, the “attack” or “kill chain” methodology was introduced as compensation and mapped out the specific phases that an adversary follows—step by step—as it approaches an asset to attack, from reconnaissance to deployment to command and control to actions on the objective. By understanding the full kill-chain (a term originally coined in the military), defenders can better position their security controls to mount an effective defense.
This framework was adopted by MITRE and described as ATT&CK, and it gained significant momentum in the public and private sectors as a globally vetted, all-source repository of adversary threat behaviors. The initiative got immediate traction for two reasons; First as it shines a light on unknown actor activities. Secondly, the descriptions and models are using a vendor neutral methodology leaving bias out for certain security technologies.
How Mandiant Advantage Uses MITRE ATT&CK
The mission of Mandiant Advantage is to augment and automate every security team in the world with our expertise and intelligence, regardless of SIEM/controls deployed. Mandiant insights are based on more than 100,000 hours spent annually in incident response. This front-line visibility forms a perfect base for timely threat intelligence and allows users to understand the steps a threat actor or malware can take to reach its goal.
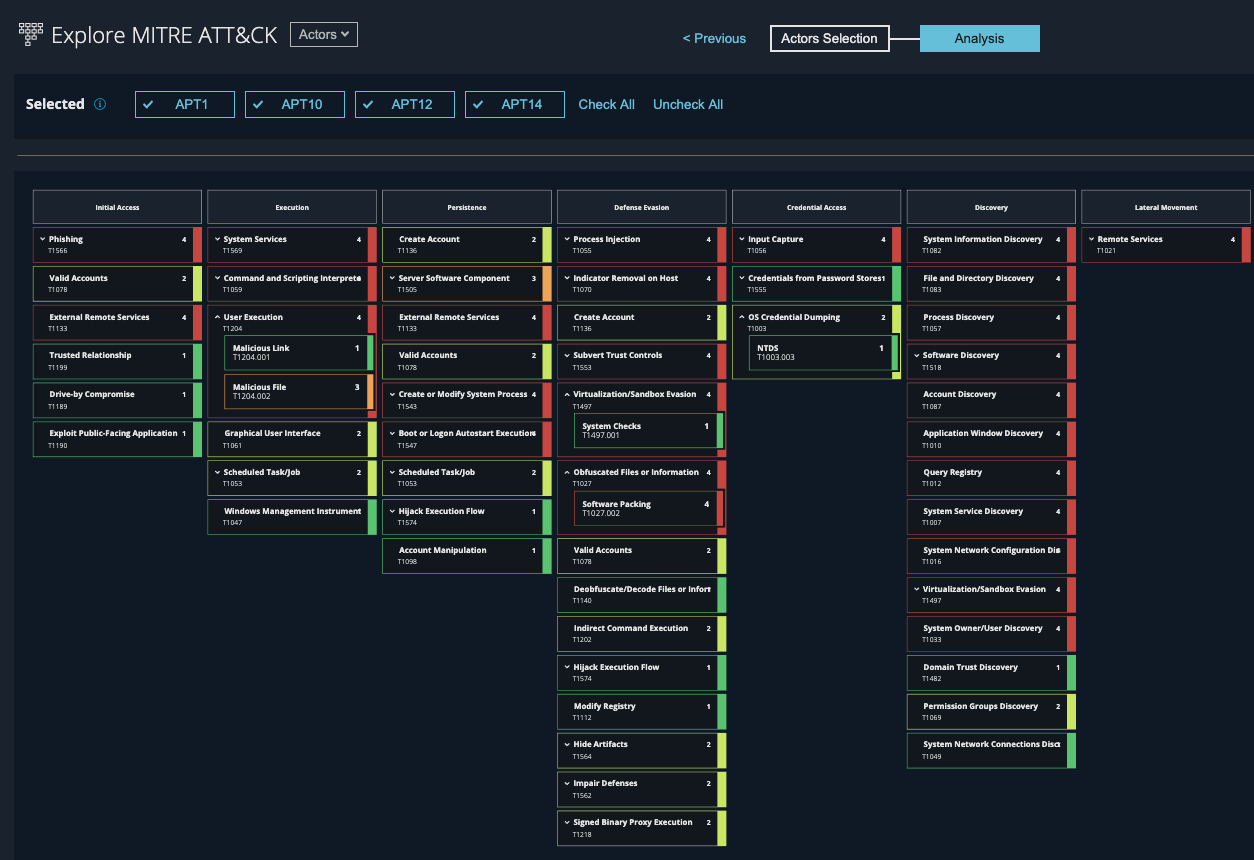
Over the past few months, Mandiant Advantage has continued evolving its MITRE ATT&CK view in accordance with the latest standards, providing security teams a more in-depth behavior map for hundreds of threat actors or malware, including hundreds of techniques and sub-techniques—from types of scripts/shells to services exploited to evasion methods.
So what are the benefits for security teams? In brief, Mandiant Advantage with MITRE ATT&CK V7 allows security operations center (SOC) teams to make informed decisions independently from vendor specific tools. Here are three examples:
First, by using the MITRE ATT&CK Explorer, security analysts can hunt for an actor more accurately and with confidence. By using the actor’s unique techniques represented within Mandiant Advantage MITRE ATT&CK Explorer, security analysts get a starting point for a specific threat and don’t have to rely on guesswork.
Next, MITRE ATT&CK can assist with incident response. When a critical event or evidence is found, analysts can—after looking up the malware—understand which actions the attacker may have taken and now eradicate all adversarial activity by understanding steps, post or prior to the discovered threat.
Lastly, MITRE ATT&CK can be seen when defining effective protection strategies. By overlaying multiple MITRE ATT&CK maps from industry or region prevalent actors or malware, risk managers can identify the most common techniques and use these as a basis to define protection programs or validate controls in place.
Security requires intelligence. By shifting focus from tools to understanding the latest adversarial tactics provided by MITRE ATT&CK, teams can not only improve detection or response efforts, but ultimately invest more effectively and protect their businesses against the threats that matter right now.
Know the threats that matter most to you—register for Mandiant Advantage Free.
This post was first first published on
‘s website by Bart Lenaerts-Bergmans. You can view it by clicking here

