What A Threat Analyst Really Thinks of Intelligence

When I was a threat analyst, too long ago for me to actually put in writing, I remember the thrill of discovery at the apex of the boredom of investigation. We all know that meme:
And the idea that these intelligence sources could spur an entirely new mechanic in the SOC, which we affectionately now refer to as Threat Hunting, was incredibly empowering. It allowed us to move beyond what was already analyzed (and most likely missed) by the SIEM and other security control technologies. True, we had to assume that the threat was already present and that the event had already established a foothold in the organization, but it allowed us to begin discovery at enterprise scale for indicators that perhaps we were compromised. I mean, remember we need to know a problem exists before we can manage it. But again, bad threat data (I once received a list of Windows DLL’s as IoCs in a fairly large campaign) and overly unimportant threat data (another provider listed hashes associated with polymorphic malware) led us down a rabbit hole we were all but too happy to come out from.
And over the years, investigation leads became a little more substantial. It would begin in one of a few ways, but the most common began through an alert as a result of SIEM correlation rules firing. In this situation, we already knew for what we were looking… the SIEM had been configured to alert us on regex matches, X followed by Y, and other common logistics often mis-named as “advanced analytics”. As we became more mature, we would ingest Threat Intelligence feeds from third party sources. Eager and enthusiastic about the hunt, we would voraciously search through a deluge of false alarms (yes, the IPS did find a perimeter attack against Lotus Notes, but we had been using MS Exchange for over 5 years) and false positives (no, that’s not Duqu… just someone who cannot remember their AD credentials).
In most mature organizations, Threat Intelligence is a critical component to the SecOps strategy. Of course, it is; it must be. How else could you defend against such a copious amount of threats trying to attack from every angle? We have ontological considerations. Which threat actors are targeting my industry vertical or geography? Have I discovered any of the associated campaign indicators? And, most importantly, will my existing controls protect me? None of which could be addressed without a Threat Intelligence capability.
So, did all of that threat data guised under the marketing of “Threat Intelligence” really help us uncover threats otherwise acting in the shadows like a thief in the night? Or did it just divert our attentions to activity that was largely uninteresting while the real threats were just another needle in a stack of needles?
Threat intelligence is supposed to help you filter the signals from the noise. At some point, without context and understanding, it is likely just more noise.
I remember working with a customer who was just beginning to expand their security operations resources, and they were eager and excited to be bringing in Threat Intelligence capabilities. The board was putting pressure on the CISO to increase the scope of accountability for his response organization, and the media was beginning to make mincemeat out of any business which was compromised by threat actors. The pressure was on and the intelligence began to flow in… like a firehose. About a month after it began, we spoke over lunch when he was interrupted at least 3 times for escalations. “What’s going on,” I asked. He told me that he was getting called day and night now about findings for which his team lacked complete context and understanding. Surely, they had more threat data, but if you asked him, that feature did not include “intelligence.”
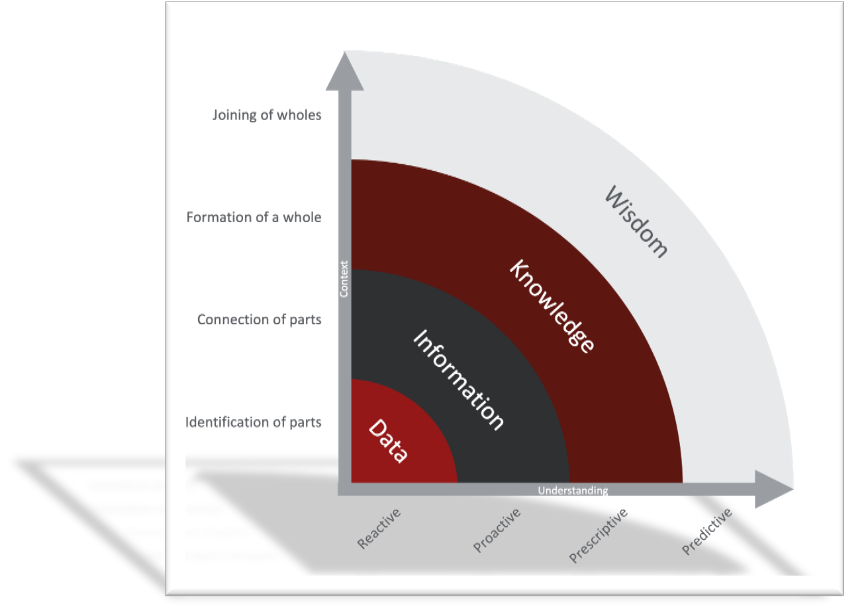
Consider the Knowledge Hierarchy: Data, Information, Knowledge, and Wisdom.
When Data is correlated in the form of context using ontology, such as grouping by specific types of malware, we gain just enough to classify the relationships as information. When we know that certain malware and malware families will exhibit groups of indicators, we can better ready our controls, detection mechanisms, and even incident response efforts and playbooks. But, still, we lack the adequate context to understand if, in general, this malware or family of malware activities will apply to my organization. We still need more context.
Intelligence is defined by dictionary.com as “knowledge of an event, circumstance, etc., received or imparted; news; information.” If we think of Threat Intelligence as a form of data feeding your Security Operations with a listing of parts, or atomic elements that in and of themselves serve little in the way of context, the SOC will regularly be forced to be reactive. With millions of indicators being pushed daily in the form of file hashes, names, URLs, IP addresses, domains, and more, this is hardly useful data.
- Ensure exploit prevention rules exist for .lnk drops
- McAfee Credential Theft Protection enabled to protect LSASS stack
- Monitor for PSExec activity and correlate to other APT29 indicators
- Monitor/Block for access to registry run keys
- et al.
However, it seems the one instrument lacking in this race to context and understanding is predictability. Surely, we can predict with the knowledge we have whether or not we may be targeted; but isn’t it much more difficult to predict what the outcome of such an attack may be? Operationally, you may have heard of dry runs or table-top exercises. These are effective operational activities required by functions such as Business Continuity and Disaster Recovery. But what if you could take the knowledge you gleaned from others in the industry, compiled with the security footprint tied to your environment today, and address the elephant in the room which every CISO brings up at the onset of “Threat Intelligence”…
So, at this point we form an entire story. It’s nice to know that malware exists and exhibits key behavior, but its even better if we know which threat actors tend to use that malware and in what way. These threat actors, like most businesses, operate in structured projects. Those projects, or campaigns, seek to find an outcome. They are targeting specific types of businesses through industry. At the writing of this article, COVID-19 has created such a dramatic vacuum in the pharmaceuticals industry that there is a race to create the first vaccine. The “winner” of such race would reap incredible financial rewards. So, it stands to reason that APT29 (also known as Cozy Bear) who notoriously hacked the DNC before the US 2016 election, would target pharmaceutical R&D firms. Now, KNOWLEDGE of all of this allows one to deduce that if I were a pharmaceutical R&D company, especially one working on a COVID-19 vaccine, that I should look at how APT29 typically behaves and ask some very important questions: what procedures do they typically follow, which tactics are typically witnessed and in what order/timing, which techniques are executed by which processes, and so on. If I could answer all of these questions, I could be reactive, proactive, and even prescriptive:
– Every CISO, Ever
Will I be protected?
Wisdom as it relates to anti-threat research is not necessarily new. The Knowledge Hierarchy has been a model in Computer Science since about 1980. What is new, is McAfee’s ability to provide a complete introspective of your stakeholder’s landscape. McAfee has one of the largest Threat Intelligence Data Lakes with over 1 billion collection points; a huge Advanced Threat Research capability responsible for converting data gleaned from the data lake, incident response consultations, and underground investigations into actionable information and knowledge; and one of the largest Cybersecurity pure-play portfolios providing insights into your overall cybersecurity footing. This unique position has led way for the creation of MVISION Insights. MVISION Insights provides context in that we have the knowledge of campaigns and actors potentially targeting your vertical. Then, it can alert you when your existing security control configuration is not tuned to prevent such a threat. It then prescribes for you the appropriate configuration changes required to offer such protection.
This level of context and understanding is what leads to Wisdom. Do not wait until the threat makes landfall in your organization. My grandfather always said, “A smart [knowledgeable] man learns from his own mistakes, but a wise man learns from everyone else’s.” I think that rings true with SecOps and Threat Intelligence as well. Once we are able to correlate what we know about our industry vertical, threat actors, campaigns, and geo- and socio-political factors with our own organization’s ability to detect and prevent threats we will truly be wise. Thanks, Pop!
MVISION Insights allows an organization to immediately answer the question, “Am I protected?” And, if you are not protected it prescribes for your environment appropriate settings which will defend against threat vectors important to you. This methodology of tying together threat data with context of campaign information and the knowledge of your security control configuration allows MVISION Insights to offer a novel perspective on the effectiveness of your security landscape.
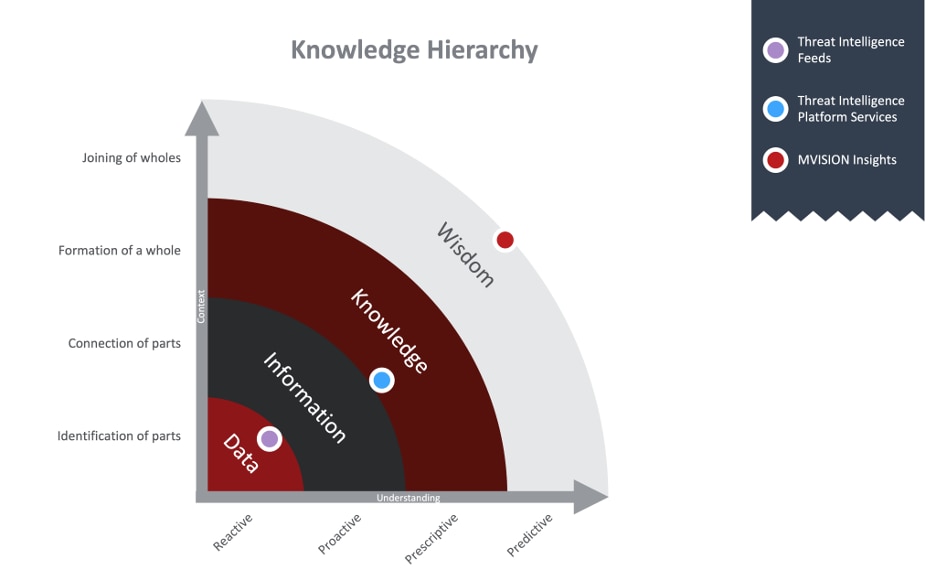
To take MVISION Insights for a spin, check out McAfee’s MVISION Insights Preview.
When I think back to all of the investigations that led me down the rabbit hole, I wonder what my days would have been filled with had I such a capability. Certainly, there is an element of “fun” in the discovery. I loved the hunt, but I think having the ability to quickly arm myself with the context and understanding of what I was searching for and why I was searching would have accelerated those moments (read hours or days). I’m excited to discuss and demonstrate how McAfee is using MVISION Insights to turn knowledge into wisdom!
This post was first first published on Enterprise – McAfee Blogs’s website by Jesse Netz. You can view it by clicking here


