Detect FritzFrog and Other Malware Infections with Inventory Data
Recently, Guardicore researchers discovered a new type of malware called “FritzFrog,” which targets multiple industry verticals, including government, finance, and healthcare. It employs brute-forcing SSH credentials as an initial attack vector, uses a proprietary P2P protocol to efficiently distribute and execute commands, and delivers payloads such as cryptominers.
While it is important to deploy EDR technologies to detect the presence of new malware, often the initial threat hunting can be performed directly against a rich asset inventory, such as what is available to all Qualys Cloud Platform applications like Qualys VMDR.
The FritzFrog malware attempts to hide itself in multiple ways, including running fileless processes and using SSH connections for the C2 traffic. However, it gives itself away by creating a local listener on TCP port 1234 to funnel the commands to the malware itself.
Threat Hunting with Inventory Data
With a complete asset inventory, it is easy to perform threat hunting against this type of infection. For example, in Qualys Global IT Asset Inventory, a user can run the following QQL query:
operatingSystem.category1:`Linux` and openPorts.port:1234
This will return a list of all potentially impacted hosts.
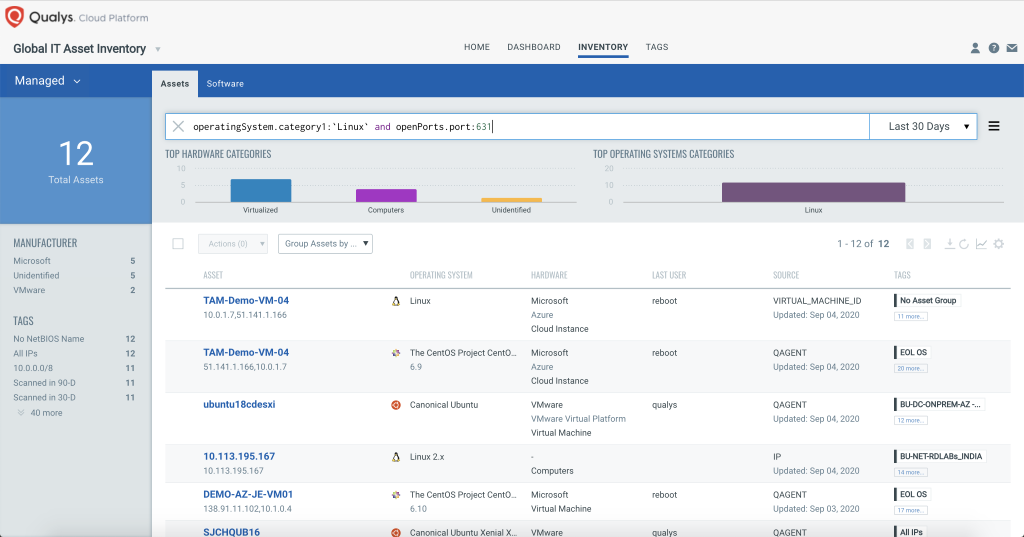
This query, based on normalized data sourced from the Qualys Cloud Agent, will allow users to quickly identify any assets that may be infected with FritzFrog. While there is a chance of seeing false positives, this will immediately narrow down the lists of systems that may need to be investigated further. This technique is not limited to FritzFrog and could be used for any port-based IOCs.
Fileless Process Detection
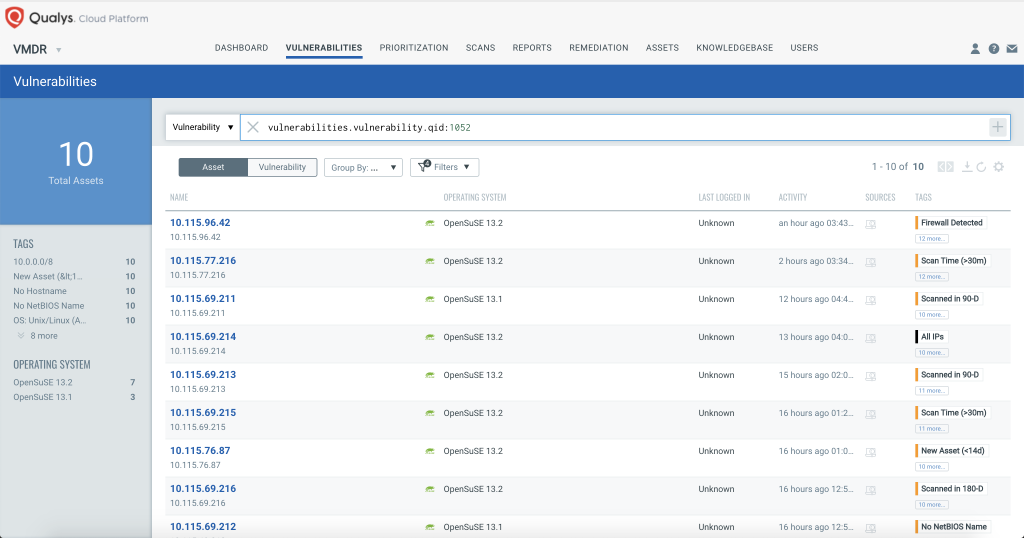
In addition, Qualys is releasing a new QID 1052 that will detect FritzFrog’s fileless processes running on Linux systems. This QID will work for both authenticated scanning as well as the Qualys Cloud Agent.
To detect the presence of FritzFrog, users can run the following QQL query in VMDR:
vulnerabilities.vulnerability.qid:1052
This will return a list of all impacted hosts.
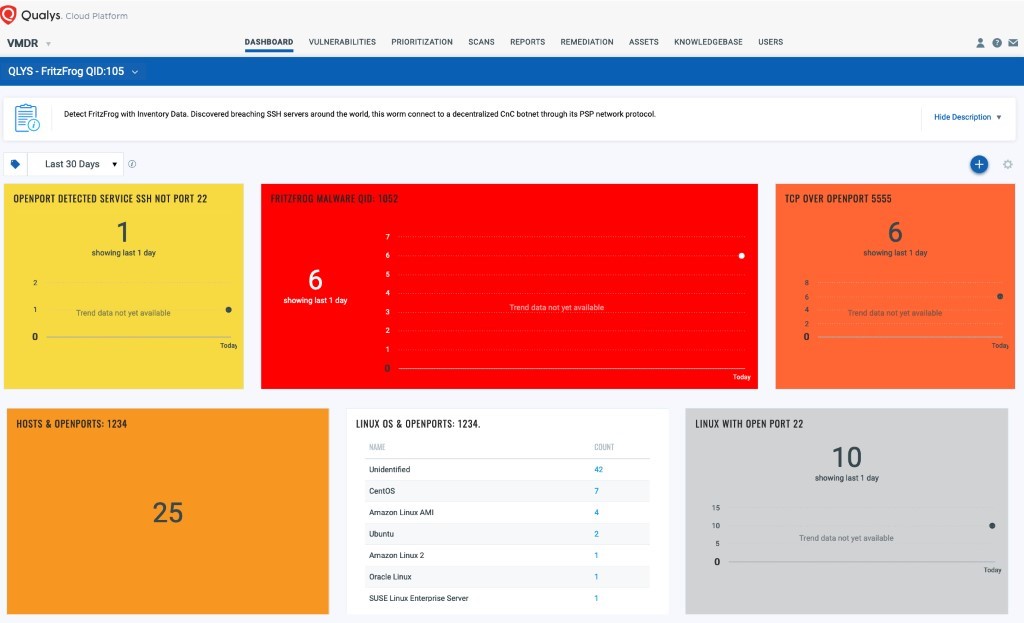
Tracking via Dashboards
With the Qualys Unified Dashboard, you can track FritzFrog infections and potentially infected hosts in real-time by importing the FritzFrog Dashboard into Qualys VMDR.
Get Started Now
Reserve your place for a Qualys Multi-Vector EDR trial (available late Q3, 2020), or start your Qualys VMDR trial for building a complete asset inventory, detecting and preventing malware, and prioritizing and patching critical vulnerabilities.
This post was first first published on Qualys Security Blog’ website by Jimmy Graham. You can view it by clicking here

