How Secure Is Your Remote Work Infrastructure?
Most organizations couldn’t even conceive a completely remote workforce, but earlier this year the world experienced an unpredictable circumstance that forced professionals to take on a new form of “business as usual.” Virtual meetings and business collaboration tools, previously used in the background, suddenly became the primary form of communication. This transition from physical office to work-from-home felt instantaneous, and it was particularly tough on security teams that had to balance business enablement with risk.
Fast forward to today, where we at Mandiant are seeing several security challenges brought on by the unexpected shift to remote work. Let’s discuss some of those challenges in detail, and then we’ll explain how our new Mandiant Remote Security Assessment can help organizations identify gaps in their remote infrastructure—and ultimately put them to rest.
Cyber Security Issues Triggered by Remote Work
These days security teams must maintain rapidly changing infrastructure and grant security-related concessions—that were once off-limits and sometimes outside of the security team’s purview—to maintain business continuity. With this change comes significant security risks, most of which fall under the following issues that continue to enable cyber adversaries:
- Misconfigured remote access and collaboration technologies: A rushed introduction of new remote access technologies or scaling up of existing remote access infrastructure has led to the use of out-of-box or insecure configurations. Many organizations lack the resources required to alter their infrastructure post-deployment, and express hesitance in applying the latest security patches for remote work assets due to fear of impacting availability.
- Improper hardening of user workstations or over reliance on endpoint controls: Deployment of technology to newly remote workers has caused many endpoint-based security measures to be sacrificed in the name of expedience. Computers or other digital assets are often shipped to remote workers (or other stakeholders) at a rapid pace to keep up with demand, and in turn may not implement security checks as a primary concern within the process. For example, user workstations may not possess fine-tuned endpoint protection (or have endpoint protection at all), properly configured security policies, or security controls to protect intellectual property from falling into the wrong hands if a workstation is stolen or compromised.
- Exposure of privileged actions and administrative interfaces: Many privileged users must access highly sensitive assets to fulfil their job responsibilities. Some organizations allow users to access such highly sensitive assets directly from their workstations or personal devices via an Internet-exposed web portal, or an Internet-accessible administrative service (such as Terminal Services/Remote Desktop Services). Others may require privileged users to use Virtual Desktop Infrastructure (VDI), which is often prone to compromise and session breakouts. If remotely accessible administrative services are not properly locked down, an attacker can take advantage of these lax security controls to compromise critical business assets and internal corporate networks.
- Reduced visibility or monitoring of Internet-bound traffic: To manage the rapid increase and daily needs of a remote workforce, network administrators are moving to previously undesirable approaches such as split tunnelling, IP safe-listing removal and access from unmanaged devices. Traffic routed to malicious destinations over the Internet may be unchecked and unmonitored, along with previously established baselines for anomaly detection, forgoing their accuracy.
Mandiant consultants are on the front lines of the world’s most impactful breaches, seeing the lofty risks of these gaps first-hand. Notably, remote access and business collaboration tools are continuously being compromised to launch targeted social engineering attacks against employees that, when successful, can provide access to the internal network, that could lead to further compromise of VDI and Cloud resources.
A Dedicated Assessment
To address these immediate concerns, we have developed the Mandiant Remote Security Assessment to help evaluate a client’s remote infrastructure, policies, procedures and overall security posture. This assessment can be tailored to a company’s needs and, unlike many typical assessments, does not require large amounts of time, resources and coordination. Mandiant consultants begin the assessment by discussing potential security pain-points surrounding the client’s remote operations. Next, Mandiant performs specific testing of the client’s remote infrastructure by emulating real-world attacker tactics, techniques and procedures to determine what gaps (if any) exist. Depending on the service scope, Mandiant may perform staff interviews across a variety of departments (i.e., security, legal, marketing) and tabletop exercises to better understand the client’s specific environment, policies, processes, procedures, and security controls.
The Mandiant Remote Security Assessment focuses solely on aspects related to remote infrastructure, therefore minimizing the risks of impacting business continuity while still delivering high-impact feedback that can empower an organization to identify and remediate potential security concerns associated with its remote workforce and operations.
A Success Story
In a recent assessment of a financial services industry client, Mandiant determined that client-related credentials within databases of publicly-leaked information could be used to successfully log in to several collaboration portals. This included access to the organization’s bring your own device (BYOD) portal (Figure 1), which possessed sensitive employee credentials such as registered mobile devices. Obtaining this information would enable the attacker to register additional devices and gain access to enterprise-wide resources.
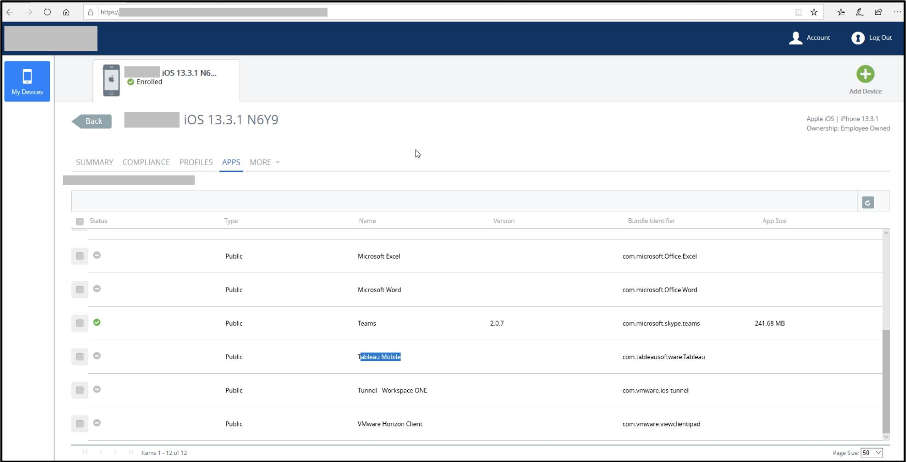
Figure 1: Access to MDM solution
While evaluating other client-owned remote access portals, Mandiant experts identified an Internet-accessible ManageEngine employee password reset, self-service portal. Mandiant discovered they could identify valid usernames within the application to enumerate user password reset questions, as shown in Figure 2.
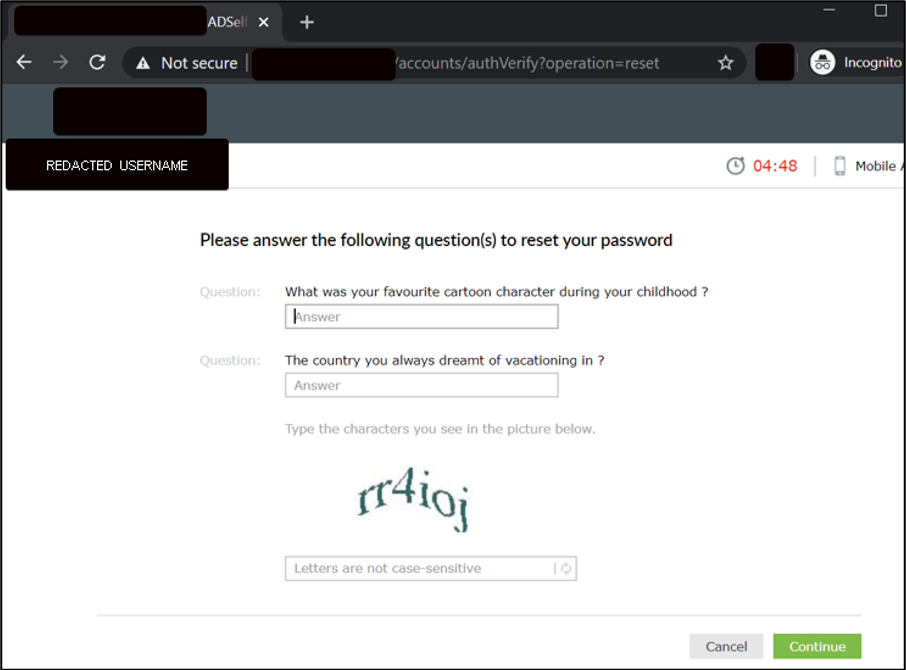
Figure 2: Sample password reset questions
Mandiant used this information to write a custom Python script to validate usernames within the client’s organization and obtain the respective user password reset questions (Figure 3).
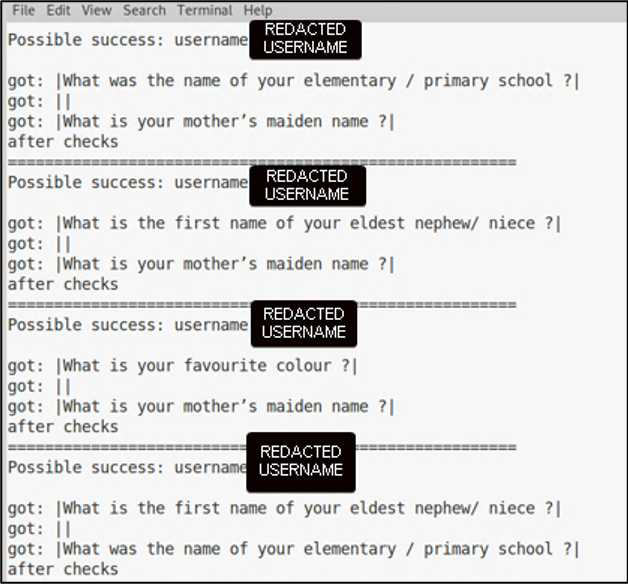
Figure 3: Custom python script to scrape password reset questions from ManageEngine
Next, Mandiant consultants performed open source intelligence (OSINT) reconnaissance to identify the answers to several user password reset questions. Figure 4 illustrates our experts finding an employee’s grandmother’s first name on a genealogy site, and Figure 5 highlights how Mandiant successfully obtained the capability to reset the employee’s Active Directory password. , and Figure 5 highlights how Mandiant successfully obtained the capability to reset the employee’s Active Directory password.
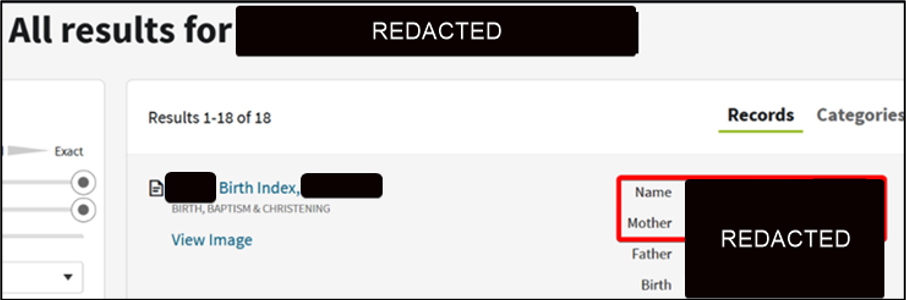
Figure 4: Target employee family information obtained via a genealogy website
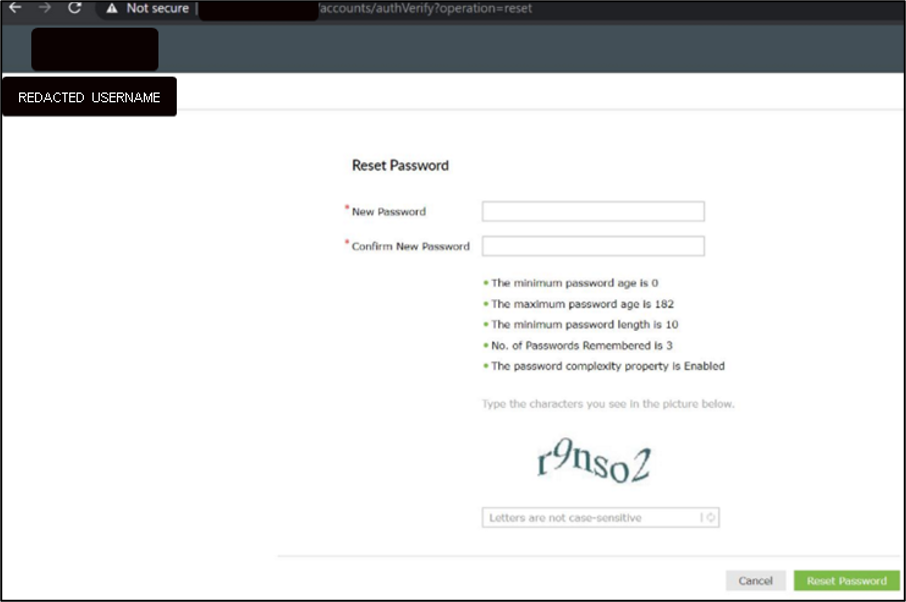
Figure 5: Successfully obtaining password reset capability of a targeted employee
Lastly, Mandiant performed password spray attacks against Internet-facing employee portals. Out of 1,873 employee usernames, Mandiant leveraged MailSniper to identify 27 users within the client’s Active Directory environment who all selected the same exact password (Figure 6).
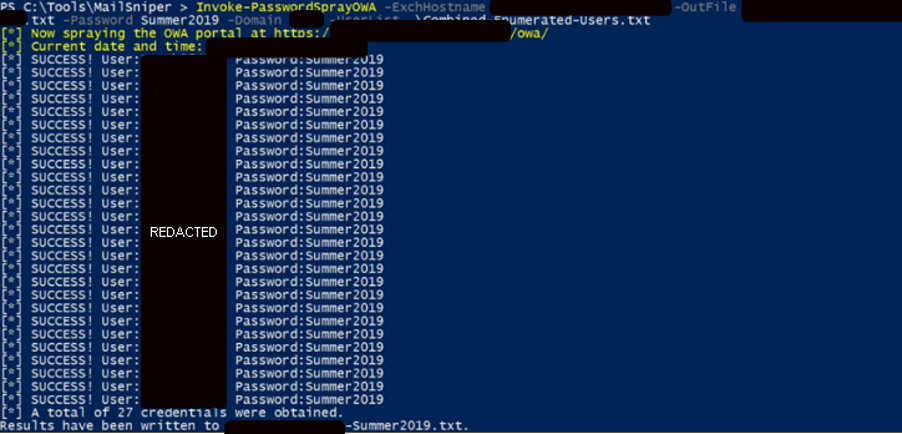
Figure 6: Password spraying via MailSniper
Mandiant used the credentials obtained via password sprays to access multiple assets, including an Internet-facing Citrix portal. A constrained session within the Citrix portal was established, followed by our experts escaping the session to possess complete control over the target’s computer, allowing free internal access to the client’s environment, resources and assets (Figure 7).
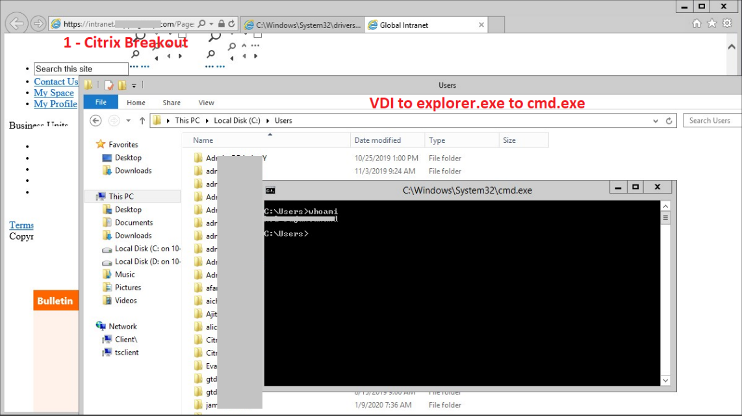
Figure 7: Citrix session compromise and breakout
Upon completion of the engagement, Mandiant provided a detailed feedback report outlining security program vulnerabilities that Mandiant consultants uncovered. Step-by-step instructions of how to recreate Mandiant’s testing and findings were also included within the report, so the client could re-test affected assets in the future after any remediation activities. Mandiant also provided best practice recommendations on how to mitigate such vulnerabilities from being exploited in the future. After the client received this data, they worked with Mandiant to implement the suggested remediation techniques. Mandiant consultants then performed remediation testing to confirm the vulnerabilities did not persist within the client’s environment.
In Conclusion
Global circumstances have driven many businesses, large and small, to implement remote work solutions—and quickly. And such changes are not likely to disappear anytime soon; the remote work revolution is likely here to stay in some form or another.
Developing remote work solutions with speed was a necessity early on, to maintain business continuity, but now that operations are settling into the new norm, we can look back and see how these massive changes have introduced unintended (and potentially unknown) vulnerabilities into digital enterprise environments.
The Mandiant Remote Security Assessment is a laser-focused service, solely concerned with evaluating a client’s remote access solutions. Because of the lean and dedicated nature of this assessment, clients can expect to receive fast, impactful findings and improvement recommendations surrounding their organization’s remote security posture, ultimately mitigating an attacker’s ability to compromise remote operations and disrupt business continuity.
Visit our Mandiant Remote Security Assessment page to learn more.
This post was first first published on
‘s website by Atul Kanwal. You can view it by clicking here

