Cloud Security: Separating Fact From Fiction
Cloud technologies offer cost and efficiency benefits to organizations in every industry worldwide; however, inexperience in working with cloud solutions has led to numerous assumptions that place organizations at risk of a security breach and competitive disadvantage.
The Cloud is Unsafe
94% of small businesses have reported security benefits after moving to the cloud
When used properly, the cloud is just as safe as a typical data center. Across the Mandiant incident response engagements conducted in public clouds, our experts have yet to see a case where cloud infrastructure itself was exploited. Improper cloud configuration or vulnerable customer code has been discovered, but flaws in the cloud provider’s code or infrastructure was not. In fact, 94% of small businesses have reported security benefits after moving to the cloud.
For many organizations, granting and administrating permissions to customize a cloud environment creates vulnerabilities, which can often be the cause of security issues.
My Organization Doesn’t Use the Cloud
By the end of this year, it is predicted that 83% of U.S. enterprise workloads will be in the cloud
While an organization may not currently store data in the cloud, they are most likely using cloud technologies. The term “cloud” includes the category of software as a service, and virtually every organization uses some form of web service—be it for human resources, banking, shipping, content management, web hosting or any other activities that take place in the modern business world.
My Cloud Provider Will Keep Me Secure
Through 2022 at least 95% of cloud security failures will be the customer’s fault*
Under the shared responsibility model, the cloud tenant is the ultimate custodian of their data and is responsible for safeguarding it. A cloud provider ensures that data center facilities are secure, the hardware is uncompromised, and underlying software and operating systems of any services offered are protected. It is the customer’s responsibility to ensure virtual machines are patched, applications are not susceptible to threats and permissions are appropriate.
The Cloud is Just Someone Else’s Computer
Securing the cloud is not like securing a computer in someone else’s data center. Hundreds or thousands of computers can be in use in a multi-cloud environment, enabling simple requests to execute—or complete—tasks to be completed in fractions of a second. Traditional data forensic analysis should still take place, but now it should happen in a very different way. Tools used to secure fewer users in the on-premises model won’t be as beneficial here. Additional visibility requirements, and further planning, are required to provide security controls and instrumentation around distributed cloud environments.
Advanced Adversaries Aren’t Attacking the Cloud
Approximately 1/4 of Mandiant incident response engagements involves assets housed on a public cloud
Attackers will go wherever their objectives take them, so the more the cloud is being used, the more it will be targeted. Approximately one quarter of our Mandiant incident response engagements involve assets housed in a public cloud and nearly all of them involve the public cloud in some way. The cloud does not hinder threat actors—instead, adversaries will modify their tactics, techniques and procedures to compromise cloud accounts for various reasons, including gaining access to confidential data, stealing computing resources, and spying on targets.
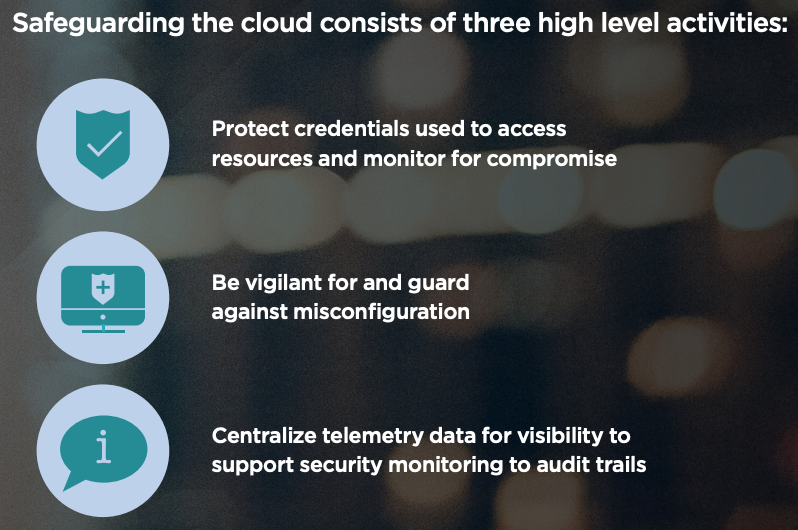
An organization can move quicker and lower costs by migrating to the cloud, but they should understand that anything of value that they place in the cloud will be a target, and therefore safeguarding it is vital. Organizations should not only implement best practices for cloud security, but also have their security operations ready to actively hunt for advanced attackers that pursue data in the cloud.
Visit our Clarity in the Cloud page for more on cloud security.
*Gartner, Clouds Are Secure: Are You Using Them Securely?, Jay Heiser, 7 October 2019
This post was first first published on
‘s website by Greg Smith. You can view it by clicking here

