Third-Party Tests Rate VMware Carbon Black Cloud as a Leader in Protection, Detection; Platform Delivers 379% ROI for Customers
The biggest endpoint protection question for organizations right now is whether or not to upgrade from legacy approaches to cloud-native platforms with built-in EDR.
If you boil this decision down to three key factors (stronger protection, clearer visibility, and faster resolution), the choice becomes abundantly clear.
Stronger Protection — Stopping More Malware with Fewer False Positives
The most urgent trigger for deciding to upgrade your endpoint protection is the proof that current solutions just aren’t stopping enough malware. While there have been a few attempts at independent proving grounds, a major lawsuit threw anti-malware testing into disarray in 2018. Yet, third-party testing remains important for existing customers, new buyers, and vendors. After Carbon Black joined the Anti-malware Testing Standards Organization (AMTSO), we prioritized these independent proof points for our platform by participating in AV-Comparatives and MITRE ATT&CK evaluations.
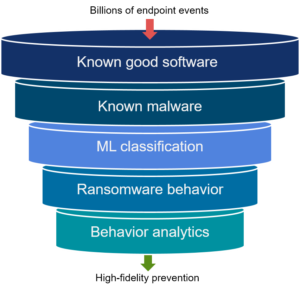
You obviously cannot stop breaches without stopping malware, so this is how we use third parties to substantiate our approach. VMware Carbon Black strongly believes you need multiple layers of prevention to protect you from compromise:
- Known good software – track reputation to avoid false positives
- Known malware – stop the commodity attacks with heuristics
- Novel malware – machine learning to identify files likely to be malicious
- Ransomware – deception to augment heuristics and behavioral analysis
- Malicious behavior – halt the sophisticated attacks as they use zero-days
Our third-party testing results show the strength of this approach as malware is increasingly circumventing machine learning-only prevention. AV-Comparatives provides an evaluation of traditional antivirus (AV) and next-generation antivirus (NGAV) solutions against both real-world malware they obtain online and commodity malware samples they collect over time. The Carbon Black Cloud led Next Generation Antivirus (NGAV) vendors in all three key areas:
- A 99.8% real-world protection rating, with only a single false positive
- A 100% malware protection rating with zero false positives
- Simplest configuration, requiring only the “Advanced” policy setting
To extend our proof points to address regulatory concerns, Coalfire Systems recently assessed the Carbon Black Cloud for protection across Windows, macOS, and Linux. They certified our platform exceeds the needs of PCI-DSS Requirement 5 – anti-malware protection. Using this combination of independent firms to demonstrate stronger protection means a lot to us, but today’s attacks require more. Malware prevention is a must, but there is a great deal more than malware to defend against.
Clearer Visibility — Detecting and Contextualizing Suspicious Activity
The major evolution of endpoint protection platforms was in combining cloud-native advantages with endpoint detection and response (EDR) in the same agent and console. For detecting non-malware attacker behavior, a cloud-native solution provides the same live view and analysis of endpoint activity whether these endpoints are on the corporate network or at home. VMware Carbon Black customers easily contain suspicious activity when both the end users and security teams are remote. Perimeter devices and security appliances see only glimpses of suspicious activity when the user is connected to the VPN.
As a proving ground for these capabilities, VMware places a great deal of value in the MITRE ATT&CK evaluation. Its testing goes beyond scoring whether the necessary data was collected to highlighting correlations around advanced attacker behavior so that security analysts prioritize their actions. Just as with protection, VMware Carbon Black has delivered a layered approach to detection. Unlike many peers, we provide clear visibility into scripting abuse (like PowerShell) in three different stages:
- Pre-execution — reading the script run on the endpoint
- Execution — AMSI shows run-time visibility
- Analytics — cloud-based frequency analysis pinpoints unusual usage
Prevention cannot be sacrificed for this visibility, but must feed off of it. What you detect must be easily turned into a sixth layer of prevention.
Faster Resolution — Cutting the Time to Remediate from Afar
 In addition to bringing stronger protection and clearer visibility, the Carbon Black Cloud greatly speeds the process for getting end users back to productivity faster. Through commissioned research, Forrester, Inc. used VMware customer interviews to determine that our prevention, detection, and remediation capabilities bring a 379% ROI when you switch from other endpoint protection platforms. The full Forrester Total Economic Impact™ report will be available next week, but you can get an early look at the summarized results by viewing this infographic.
In addition to bringing stronger protection and clearer visibility, the Carbon Black Cloud greatly speeds the process for getting end users back to productivity faster. Through commissioned research, Forrester, Inc. used VMware customer interviews to determine that our prevention, detection, and remediation capabilities bring a 379% ROI when you switch from other endpoint protection platforms. The full Forrester Total Economic Impact™ report will be available next week, but you can get an early look at the summarized results by viewing this infographic.
Dropping the need for direct, hands-on access to a compromised endpoint is especially impactful. Eliminating the need for hands-on, root-cause analysis; greatly reducing the number of laptops shipped for remediation;, and having no appliances to manage help customers recoup subscription costs in less than three months. The upgrade may feel like a major change for your organization, but you see the benefit almost immediately.
Download your copy of VMware Carbon Black Cloud Endpoint Standard PCI DSS Attestation Report by Coalfire. To start your evaluation of the VMware Carbon Black Cloud, please reach out to us today.
The post Third-Party Tests Rate VMware Carbon Black Cloud as a Leader in Protection, Detection; Platform Delivers 379% ROI for Customers appeared first on VMware Carbon Black.

