CB TAU Threat Intelligence Notification: SEON Ransomware Distributed via Drive-By Attack Campaign

SEON Ransomware ver 0.2 was found being distributed by the GreenFlash Sundown exploit kit via a drive-by-attack campaign. After performing the encryption, SEON will drop and display the following ransom note and append ‘.fixt’ as the extension to the encrypted file.
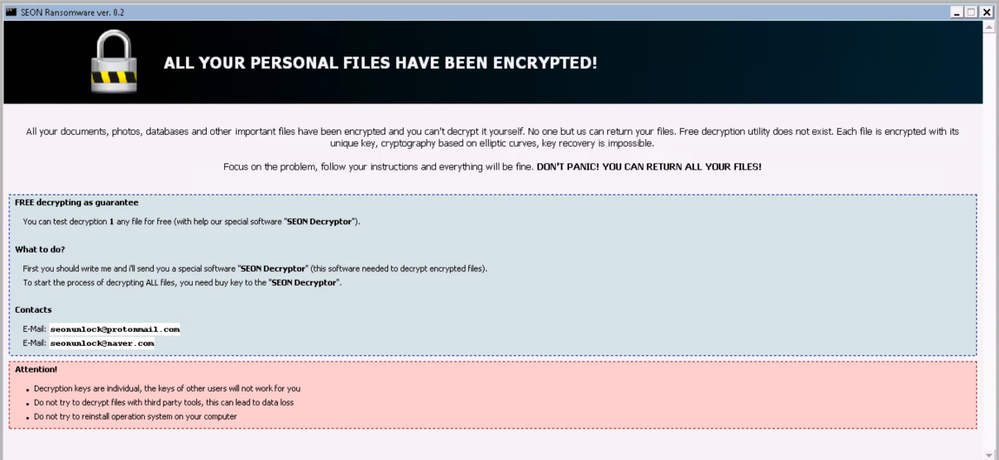
Figure 1: Screenshot of the ransom note
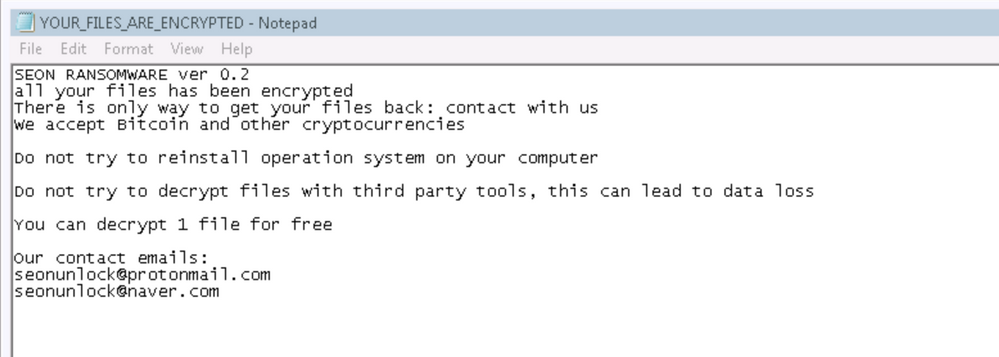
Figure 2: Screenshot of the ransom note text file ‘YOUR_FILES_ARE_ENCRYPTED.txt’
Behavioral Summary
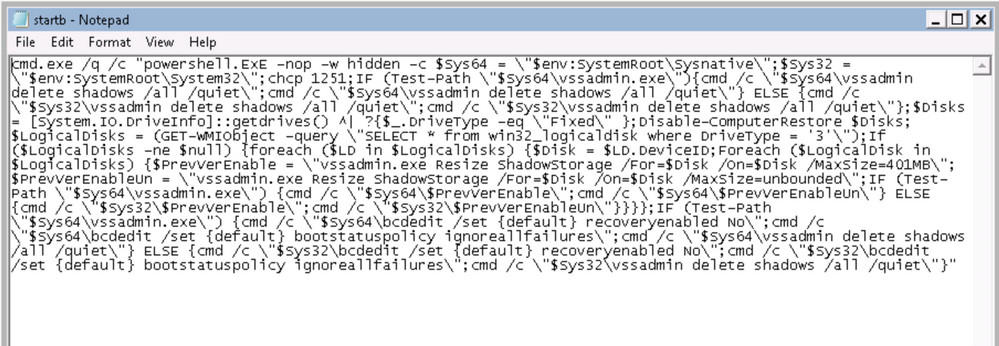
After the encryption routine, SEON will use a batch script which is located at ‘%AppData%LocalTempstartb.bat’ to perform the deletion of volume shadow copies to ensure all the data cannot be restored easily.
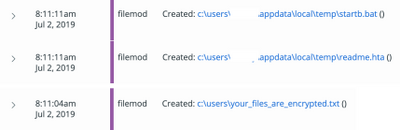
The CB Threat Hunter events logs show the dropping of the batch script file and ransom note shown in the following screenshot.
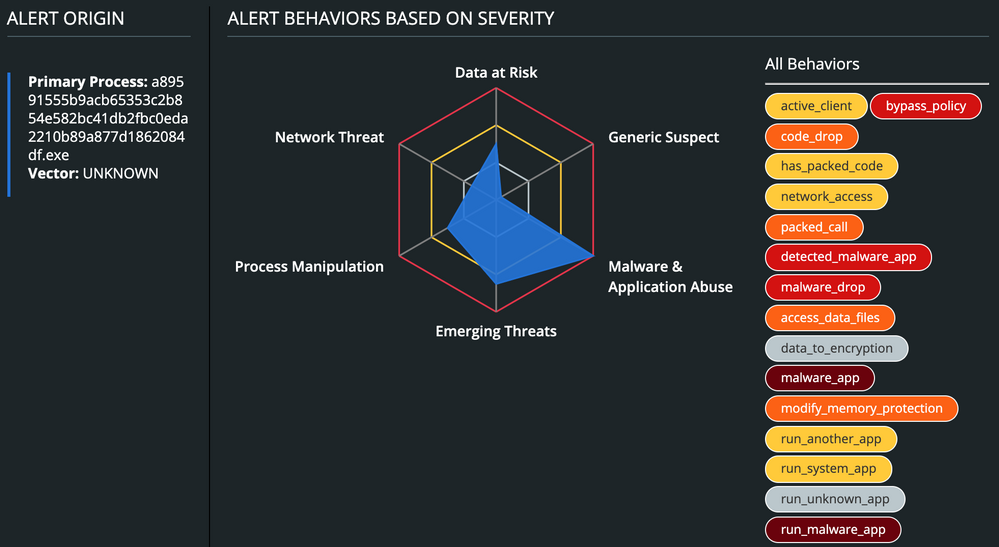
Other than that, CB Defense will display the malware’s overall triggered TTPs.

If you are a Carbon Black customer looking to learn how to defend against this attack, click here.
Remediation:
MITRE ATT&CK TIDs
| TID | Tactic | Description |
| T1189 | Initial Access | Drive-by Compromise: SEON was delivered via drive-by-attacks campaign |
| T1059 | Execution | Command-Line Interface: Cmd used to run batch script |
| T1064 | Defense Evasion, Execution | Scripting: It will run a batch script to execute powershell and delete shadow copies |
| T1086 | Execution | PowerShell: PowerShell was used to execute vssadmin |
| T1486 | Impact | Data Encrypted for Impact: Ransomware encrypts file and then demands a ransom be paid for decrypting the file |
| T1107 | Defense Evasion | File Deletion: Shadow Copy Deletion by VSSAdmin |
| T1067 | Persistence | Bootkit: BCDEdit Or BCDBoot Use |
| T1490 | Impact | Inhibit System Recovery: It use vssadmin and bcdedit to delete and disable operating system recovery features |
Indicators of Compromise (IOCs)
| Indicator | Type | Context |
| a89591555b9acb65353c2b854e582bc41db2fbc0eda2210b89a877d1862084df
1a6820fec1c45cd9c928533090e7908d |
SHA256
MD5 |
SEON Ransomware |
| 591e7f5eb141c22919a406508f63a558e3bd732fe38844cedbbea938d666e78b
eb5d62f37c2a7cdd355b483d06ff7278 |
SHA256
MD5 |
SEON Ransomware |
The post CB TAU Threat Intelligence Notification: SEON Ransomware Distributed via Drive-By Attack Campaign appeared first on Carbon Black.

