Don’t Underestimate Credential Theft Malware

As 2018 came to a close, I stopped to reflect about the various threats we saw this year – particularly in Europe. While Europe continued to struggle with targeted attacks from organized cyber criminal groups and cyber espionage groups, there was yet another threat that we observed challenging numerous organizations in nearly every industry. Some may think the answer is ransomware. Sure, ransomware continues to be a threat, but we have actually observed a continued decrease in ransomware detections. This is a trend that started back in late 2017 and has been fairly consistent.
Nope, what I’m talking about is credential theft malware. In 2018, we observed a continued use of credential theft malware by cyber criminals and other attackers. We’re talking about everything from credential theft malware as attachments in phishing emails to distribution of the malware via exploit kits.
Credential Theft Malware vs Other Categories
By analyzing threat detections from our Dynamic Threat Intelligence (DTI) for Jan. 1, 2018, to Dec. 31, 2018, we can see that nearly 50 percent of all detected threats in Europe were within the category of credential theft malware (Figure 1). The data includes detections from both FireEye email and network appliances.
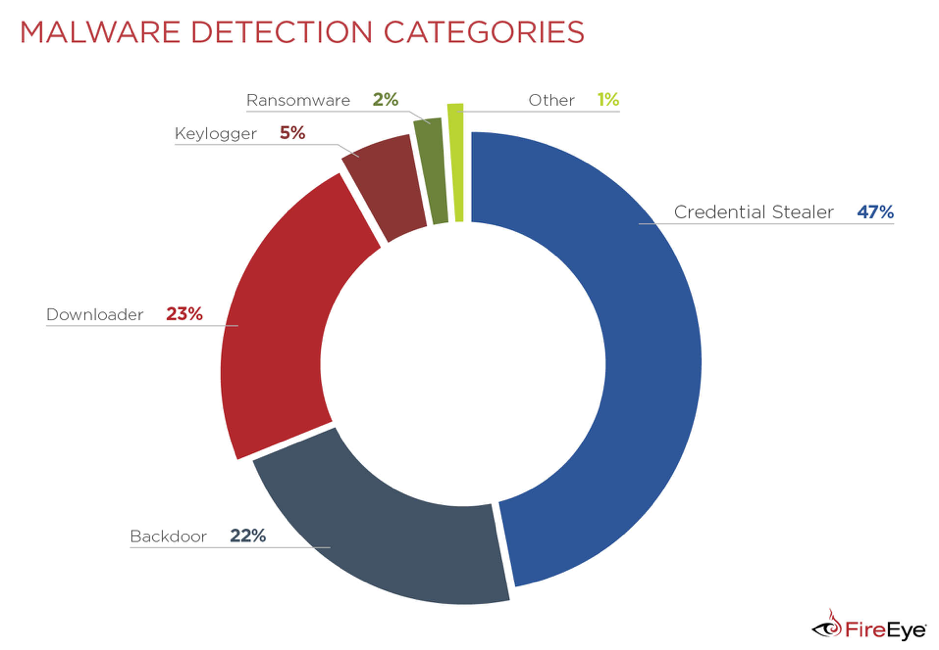
Figure 1: Malware detection categories in Europe from Jan. 1, 2018, to Dec. 31, 2018.
An Emerging Challenge in Europe
Credential theft malware is certainly a global problem and organizations from all across the world are at risk, but in Europe and especially for members of the European Union (EU), it is a particularly tough challenge and something to keep in mind for 2019. One reason is the EU’s continued, long-time focus on digitalization. These digitalization initiatives focus on a variety of categories, ranging from ensuring high-speed connectivity for EU citizens to how EU citizens interact with their governments, as well as the possibilities for EU enterprises and citizens to do business online.
Graph: DESI 2018 Ranking
From a threat perspective, the improved connectivity expands the surface area for cyber threats, but more critical, the continued expansion within Digital Public Services could potentially be an area of interest when it comes to stealing credentials and potential sensitive information submitted via government web-portals.
-
- In 2017, 58 percent of the EU citizens who needed public services chose to go online, submitting forms and using governmental portals.
- On Sept. 29, 2018, the EU-wide legislation on election identification (eIDAS Regulation) entered into force enabling cross-border recognition of the electronic ID. Several of these initiatives under the Digital Single Market strategy are designed to improve efficiency for EU citizens, governments and businesses, and potentially cut down government costs.
Potential Threat Scenarios
Previously we had observed credential theft malware primarily targeting customers within the financial services industry; however, this uptick in credential theft malware use throughout 2018 could potentially mean that we will see a scenario where credentials for EU centric systems – such as government, healthcare, payroll systems, and other sensitive systems – will be adopted in future malware configuration files. Some other things to note:
-
- Throughout 2018, we have observed a variety of cyber criminals putting both larger volumes of stolen credentials up for sale, as well as alleged direct access to company infrastructure.
- Notable credential theft malware families have throughout the years expanded their targeting to include major online retailers, gambling sites and other sites outside the financial services Industry.
- From a cyber espionage threat perspective, it might make more sense for a threat actor to purchase alleged access to either stolen credentials or access to infrastructure, bypassing the initial intrusion steps.
In our M-Trends 2018 report, we also cover the lack of basic security fundamentals, where identity and access management is still a challenge for many organizations. The fact that many have yet to implement multi-factor authentication will only make it easier for threat actors and malware to efficiently harvest credentials, which could allow access to sensitive systems.
Throughout the years, we have published numerous reports and blog posts on how threat actors – from organized cyber criminals to espionage groups – have utilised legitimate credentials in their cyber attacks. Here are a few examples:
-
- In 2014, we published findings on the financially motivated FIN4, a group that used spear phishing emails to steal legitimate credentials, thus gaining access to merger and acquisition information.
- In October 2015, we published findings on a cyber criminal group we track as FIN5. This group hacked payment systems and gained access to credit card records by using legitimate credentials stolen in their intrusions.
- In April 2016, we published a report on FIN6. Similar to FIN5, this group was using legitimate credentials in attacks targeting point-of-sale systems, scraping their memory for credit card records.
Conclusion
While other malware categories such as ransomware tend to steal most headlines, I believe that organizations and governments need to be more aware of the threat posed by credential theft malware. While it is a global threat, it is particularly problematic in Europe, especially considering the fast-paced digitalization strategies. Ultimately, EU organizations cannot neglect the value credentials have in cyberspace, and therefore must make sure to factor in the risks on how stolen credentials can be misused in both sensitive and non-sensitive communications.

