CB TAU Threat Intelligence Notification: Danabot Trojan Targets Financial Services Industry via Stolen Credentials

Summary
Danabot is a banking trojan written in the Delphi programming language. Delivery methods are typically via phishing emails that contain malicious attachments, which further call out to download the main payload using PowerShell or VBScript. Danabot is modular in nature and has capabilities to perform web injection and man-in-the-browser styles of attack, in order to steal sensitive credentials pertaining to banking credentials. The banking and financial services sectors are likely the prime targets for Danabot.
Behavioral Summary
Typical infection vectors include phishing and spear-phishing emails which may carry malicious email attachments to infect the system. Danabot makes use of common “living off the land” binaries (LOL-bins) to execute processes such as Regsvr32 and Rundll32 on the host system. It exhibits multiple nested child Rundll32 processes in order to load certain modules, such as listening on a fixed TCP port, harvesting credentials from LSASS, setting browser proxy settings, and connecting to remote C2 IP addresses. To maintain persistence, it writes a new service to the Windows Registry. TTP’s are shown below:
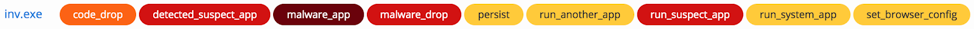

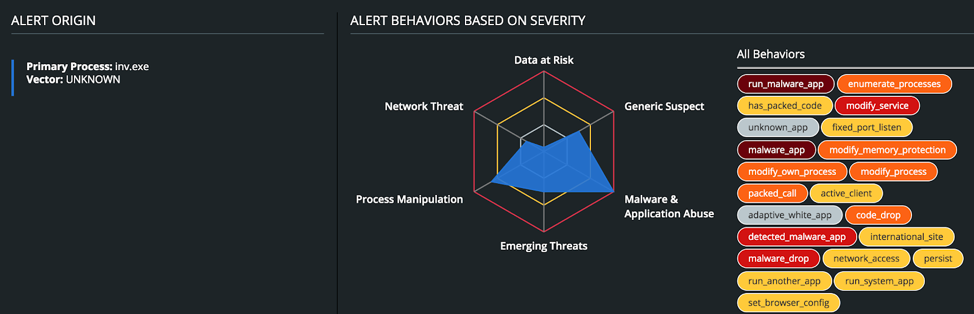
The full process diagram is shown below.

If you are a Carbon Black customer and looking for more information on how CB products defend against this attack, click here.
Remediation:
MITRE ATT&CK TIDs
| TID | Tactic | Description |
| T1193 | Initial Access | Spearphishing Attachment |
| T1106 | Execution | Execution through API |
| T1158 | Persistence, Defense Evasion | Hidden Files and Directories |
| T1117 | Defense Evasion, Execution | Regsvr32 |
| T1085 | Defense Evasion, Execution | Rundll32 |
| T1050 | Persistence, Privilege Escalation | New Service |
| T1057 | Discovery | Process Discovery |
| T1105 | Command and Control, Lateral Movement | Remote File Copy |
| T1185 | Man in the Browser | Collection |
| T1041 | Exfiltration Over Command and Control Channel | Exfiltration |
| T1043 | Commonly Used Port | Command and Control |
Indicators of Compromise (IOCs)
| Indicator | Type | Context |
| e0830e58a7f2fe46848fe
8493d3511f94d969fca8 deb5e089537839e4d752ad3 b31862f60c886dd5d8ff1b85cf79efc0 |
SHA256
MD5 |
Danabot
executable launcher |
| 21.192.187.178 | IP address | C2 |
| 212.11.77.202 | IP address | C2 |
| 217.149.189.121 | IP address | C2 |
| 139.228.235.22 | IP address | C2 |
| 209.28.99.7 | IP address | C2 |
| 105.215.102.124 | IP address | C2 |
| 27.217.226.127 | IP address | C2 |
| 185.92.222.238 | IP address | C2 |
| 172.205.217.104 | IP address | C2 |
| 89.144.25.243 | IP address | C2 |
The post CB TAU Threat Intelligence Notification: Danabot Trojan Targets Financial Services Industry via Stolen Credentials appeared first on Carbon Black.

