ACSC Essential 8 Cybersecurity Strategies, Maturity Levels, and Best Practices
Table of Contents
Originally published in 2017 as an evolution of the Australian Signals Directorate’s Strategies to Mitigate Cyber Security Incidents, the Australian Cyber Security Centre (ACSC) Essential 8 (E8) consists of a set of strategies that can make it harder for threat actors to compromise a firm’s cybersecurity defenses. This blog examines specific aspects of E8 and its maturity levels and recommends best practices and solutions that can improve your ability to implement these strategies quickly and affordably.
Over the years, the E8 has matured from a mostly baseline approach for cybersecurity for Australian federal government agencies to a well-known set of best practices used by local and state governments, as well as more security conscious private sector firms. The impetus for more adoption stems from a raft of recent cyberattacks on some of Australia’s largest firms, with breaches reported by at least eight companies including health insurance provider Medibank Private Ltd, as well as Optus, which is owned by Singapore Telecommunications Ltd.
According to Infosecurity Magazine and Surfshark, there were 489 percent more data breaches in Australia during the last quarter of 2022 than previously reported. Alarming statistics published in a report released by the Australian Information Commissioner on Notifiable Data Breaches from July to December 2022 include:
- Forty large-scale data breaches occurred in the second half of 2022
- Notifications were issued for 497 data breaches—a 26 percent increase from 1H22
- The healthcare sector reported the most breaches with 71, followed by the financial sector with 68
The Australian Cyber Security Centre (ACSC) recommends implementing the Essential Eight strategies and attaining the highest maturity level possible.
E8 Maturity Levels
The ACSC updated the E8 a few years ago to include maturity levels (MLs). Each level outlines requirements that relate to strategy implementation. When selecting an appropriate ML, organisations should decide which one ensures the right balance between adequate security, staff capabilities, and budgets. Within the updates, ML 0 was reintroduced, and ML 3 remains the highest and most protected level. ML 1 is recommended for most small to medium businesses (SMBs), ML 2 for larger enterprises, and ML 3 for enterprises or government agencies with more critical infrastructures or higher threat environments. Recommendations for ML 3 increased from 29 to 69 requirements to address the need for more stringent protections against escalating attacks. For all levels, the requirements became more precise and detailed. Firms that have not yet implemented all the changes, or are planning for higher maturity levels, often struggle with solutions that are too complex, difficult to implement, require too many agents and dashboards, and don’t cover all the requirements.
Each ML is divided into eight components, which include patching and vulnerability management, configuration management, application security testing, and more. By working through these components at each level, you can measure your progress toward compliance.
Implementing Essential 8 Can Be Challenging
Implementing E8 can be challenging due to the following reasons:
- Lack of visibility – Identifying security controls related to specific mitigation strategies followed by maturity levels requires fine-grained visibility.
- Manual efforts – Without automation, ensuring your network is hardened and protected by following E8 or other industry standards may require time-consuming manual efforts.
- Lack of resources – Significant time, money, and expertise may be required to map controls, which can be difficult if an organisation does not have the necessary resources.
- Constant changes – As the E8 is constantly updated, and new systems are introduced as part of digital transformation, mitigation strategies must also be applied. In the absence of such measures, it can be extremely difficult to maintain control effectiveness while managing cybersecurity risks.
- Continuous monitoring and maintenance – It’s critical to monitor and maintain ASD E8 controls after their implementation to ensure their effectiveness. Lack of resources or processes to monitor and maintain controls can make it difficult to maintain effectiveness over time.
How Qualys Cloud Platform Helps With E8 Security Controls
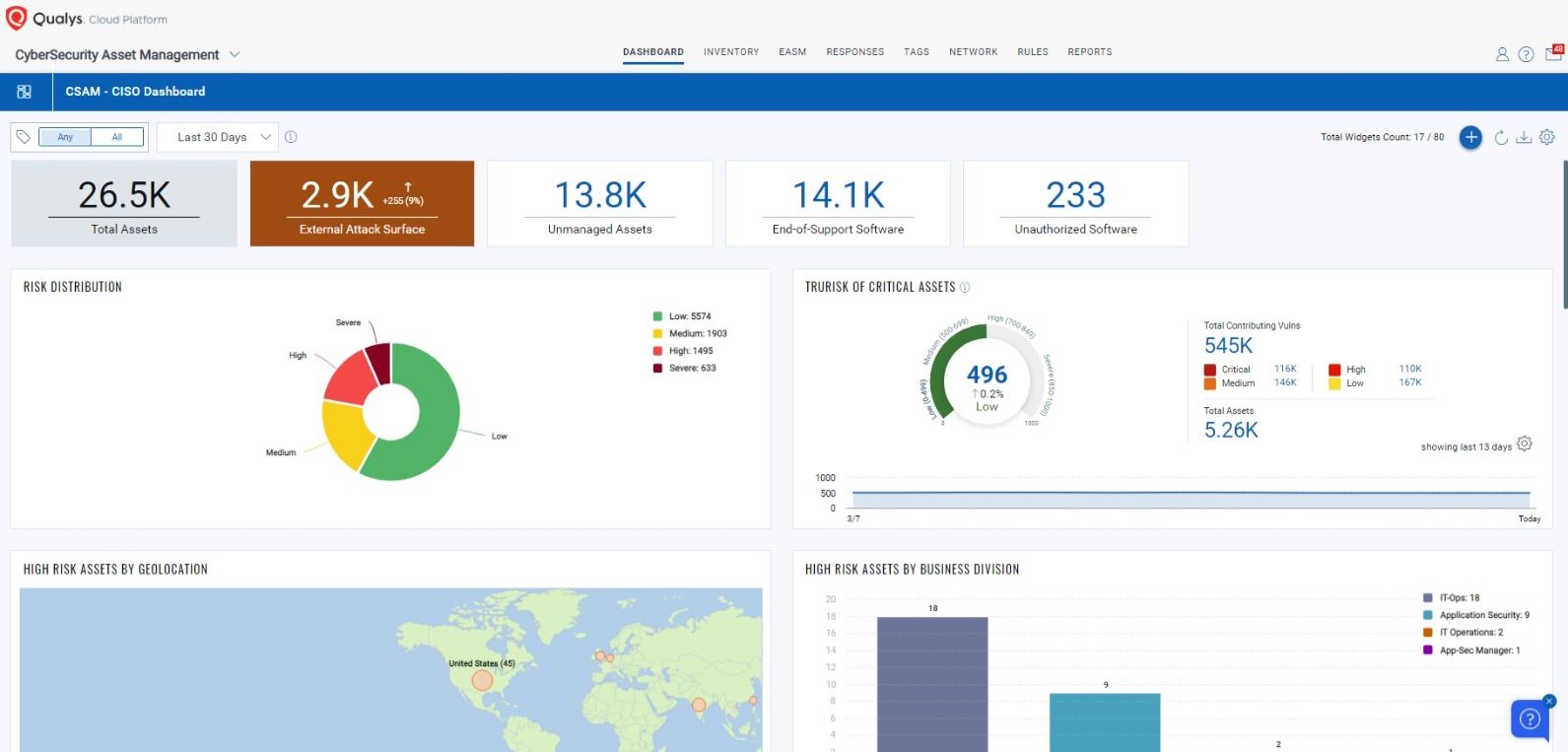
The Qualys Cloud Platform is a comprehensive solution designed to meet your security and compliance requirements for E8 security controls. With the Qualys Unified Dashboard, IT and security professionals can view the overall compliance status for their entire environment.
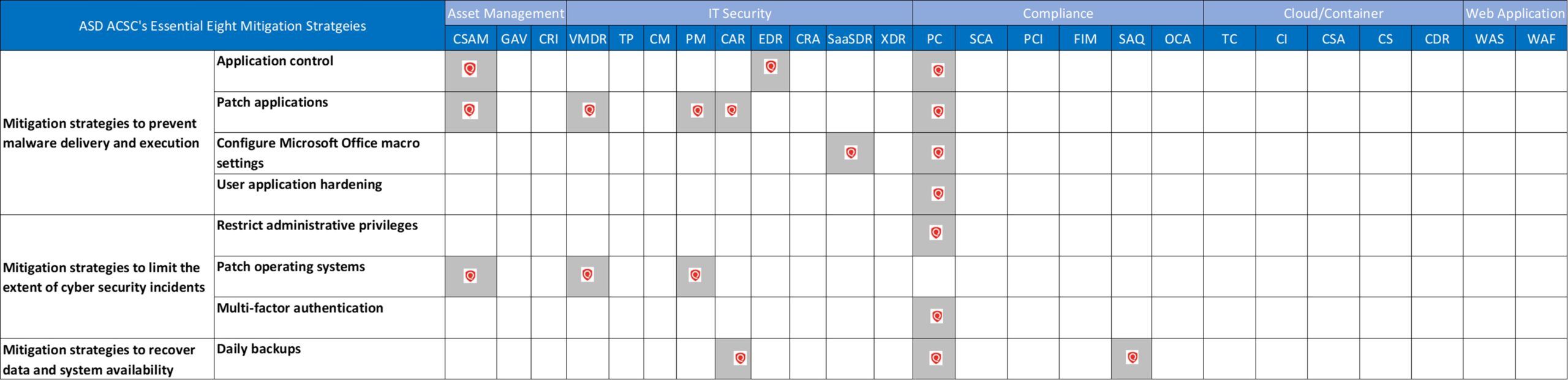
Unified View of E8 mitigation strategy with Qualys Cloud Platform
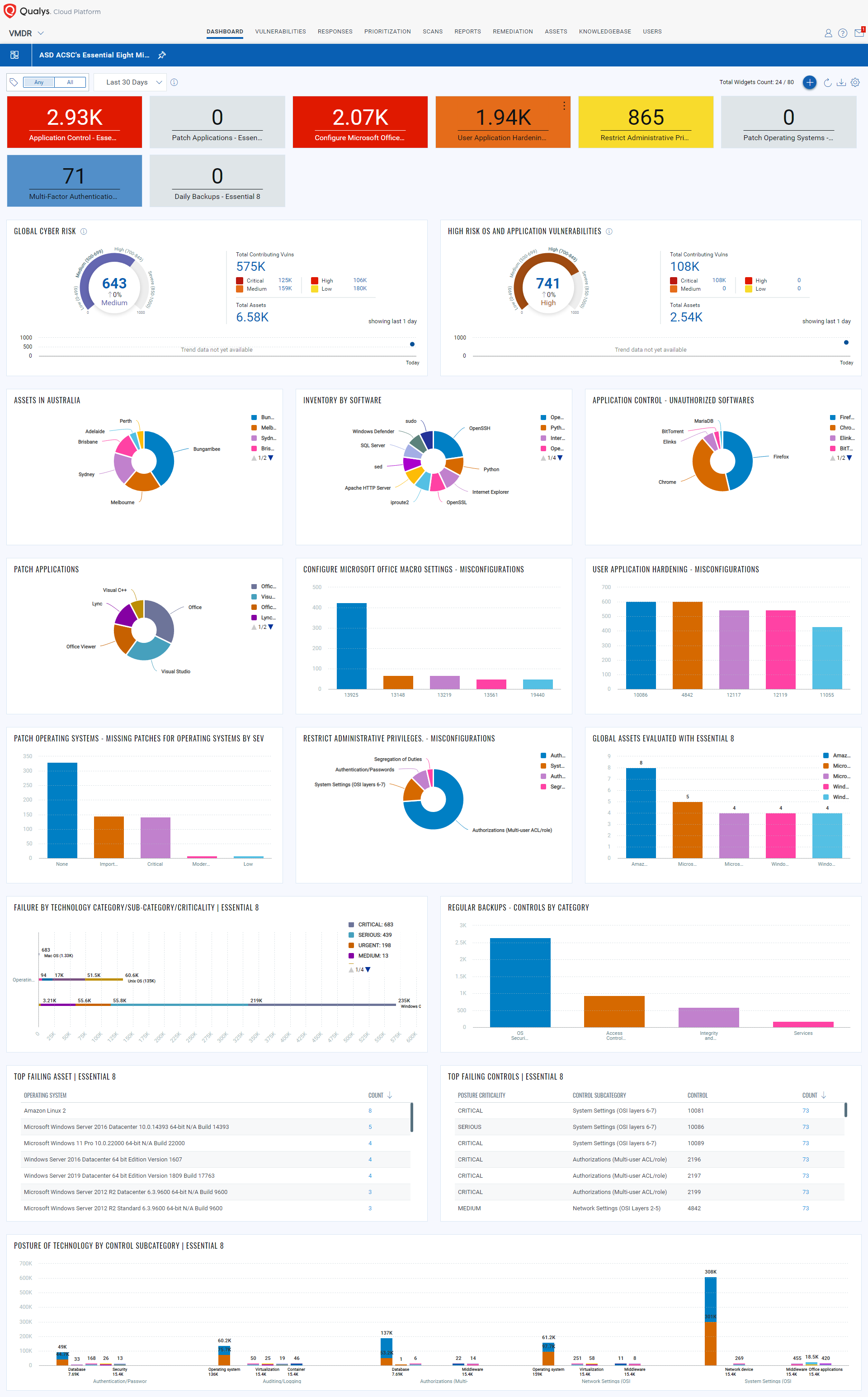
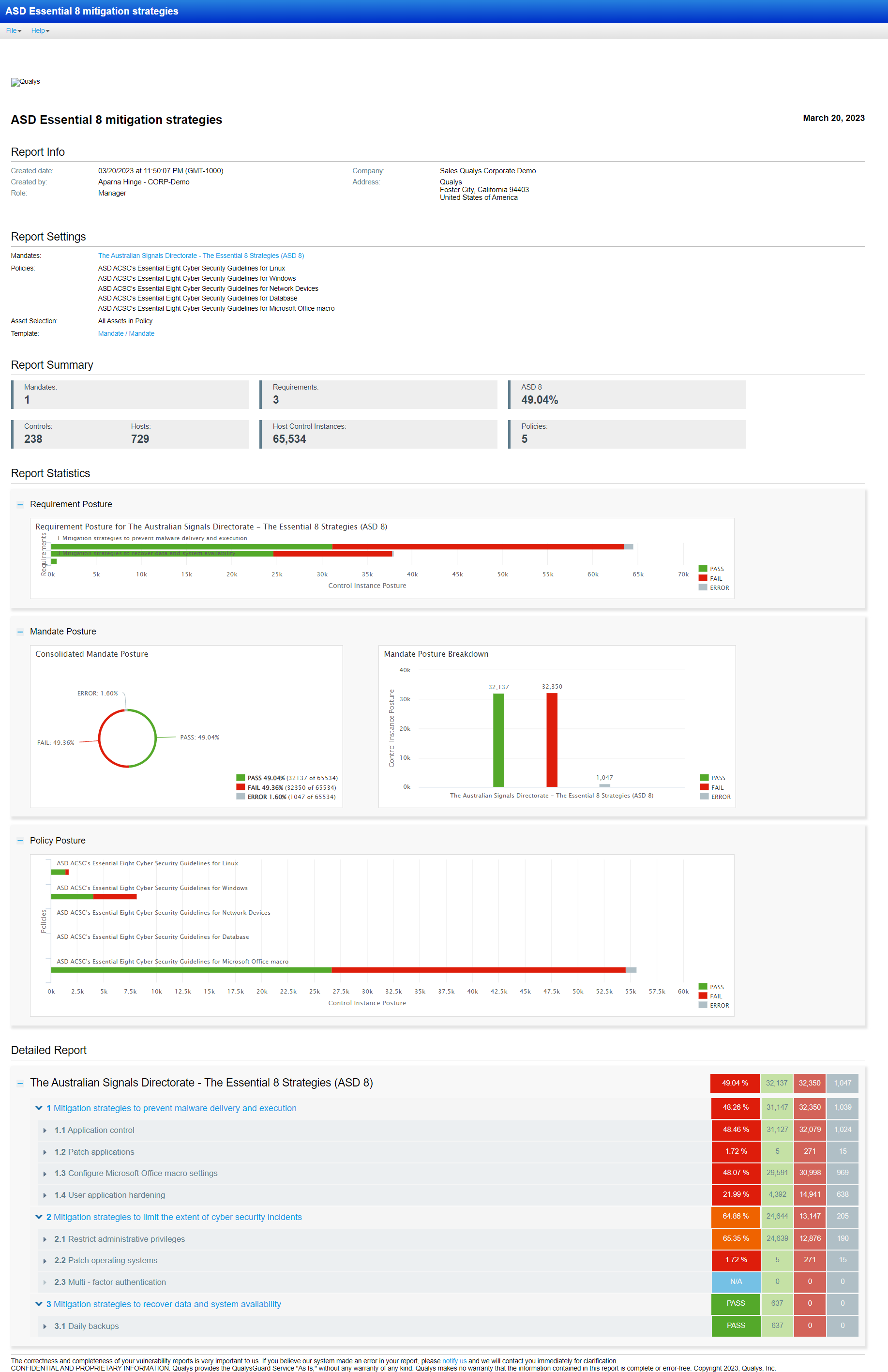
Let’s review how each E8 Security Control is covered by specific Qualys modules:
1. Application Control
This security control is used to approve or deny the execution of applications on your network. Only authorized applications are allowed to run in your environment, and other applications are denied access to your data. It’s designed to prevent the execution of unauthorized/malicious programs, including .exe, DLL, scripts (e.g., Windows Script Host, PowerShell and HTA) and installers.
How Qualys Helps
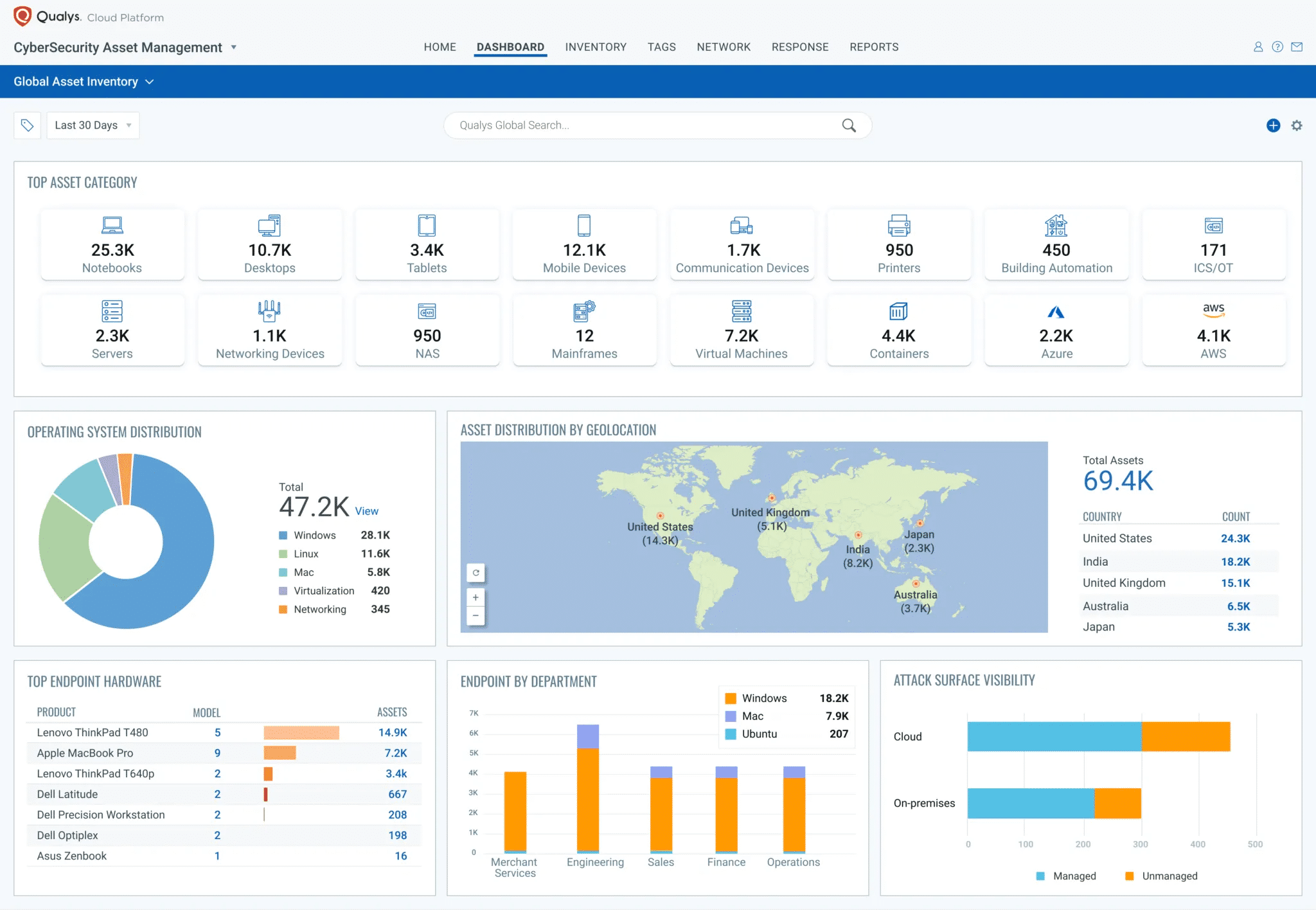
Qualys CyberSecurity Asset Management (CSAM) continuously discovers and monitors your entire attack surface, including internal known and previously unknown internet-facing assets, across your on-premises, cloud, and multi-cloud environments. It delivers natively integrated External Attack Surface Management (EASM) to enable Cybersecurity teams to identify all assets visible on the internet, including previously unknown assets and any potential security issues—before attackers find them.
It helps to build a Comprehensive Asset Inventory by automatically discovering and classifying all IT assets, including software, on-prem devices and applications, mobile devices, clouds, containers, and enterprise IoT devices using both agent and agentless methods. Users can define and create lists of both authorized and unauthorized software and track the results in your IT environment. Proactive tracking of unauthorized and authorized software is a key capability to help reduce security risks and improve the health of your inventory. If an organisation aspires to attain higher E8 MLs, then application control is a first step and Qualys allows you to identify which software is being used and whether it’s approved.
How Qualys Endpoint Security Helps
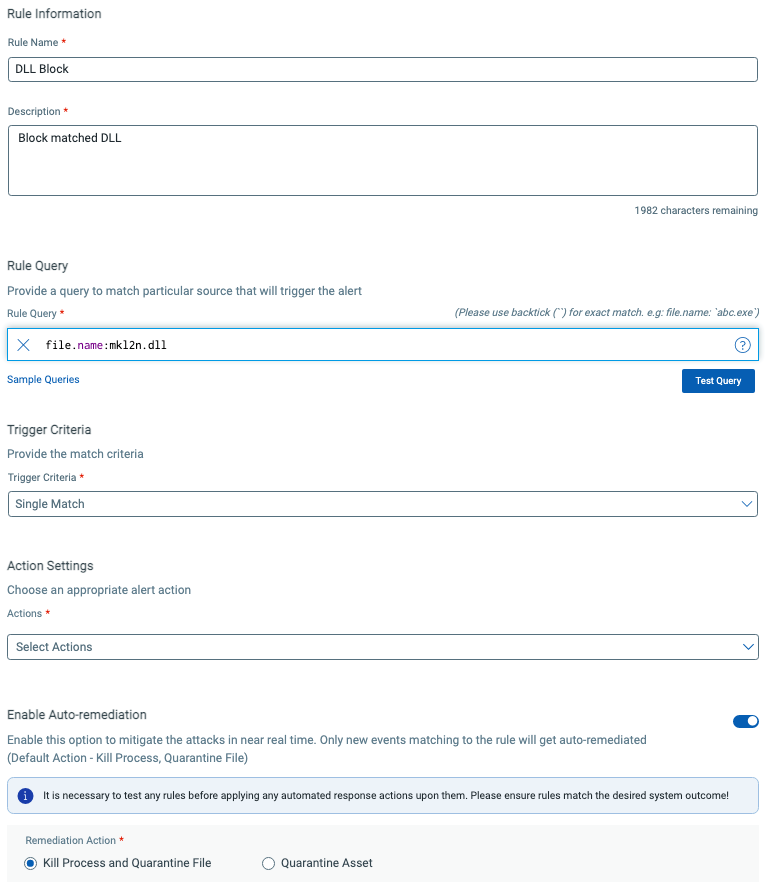
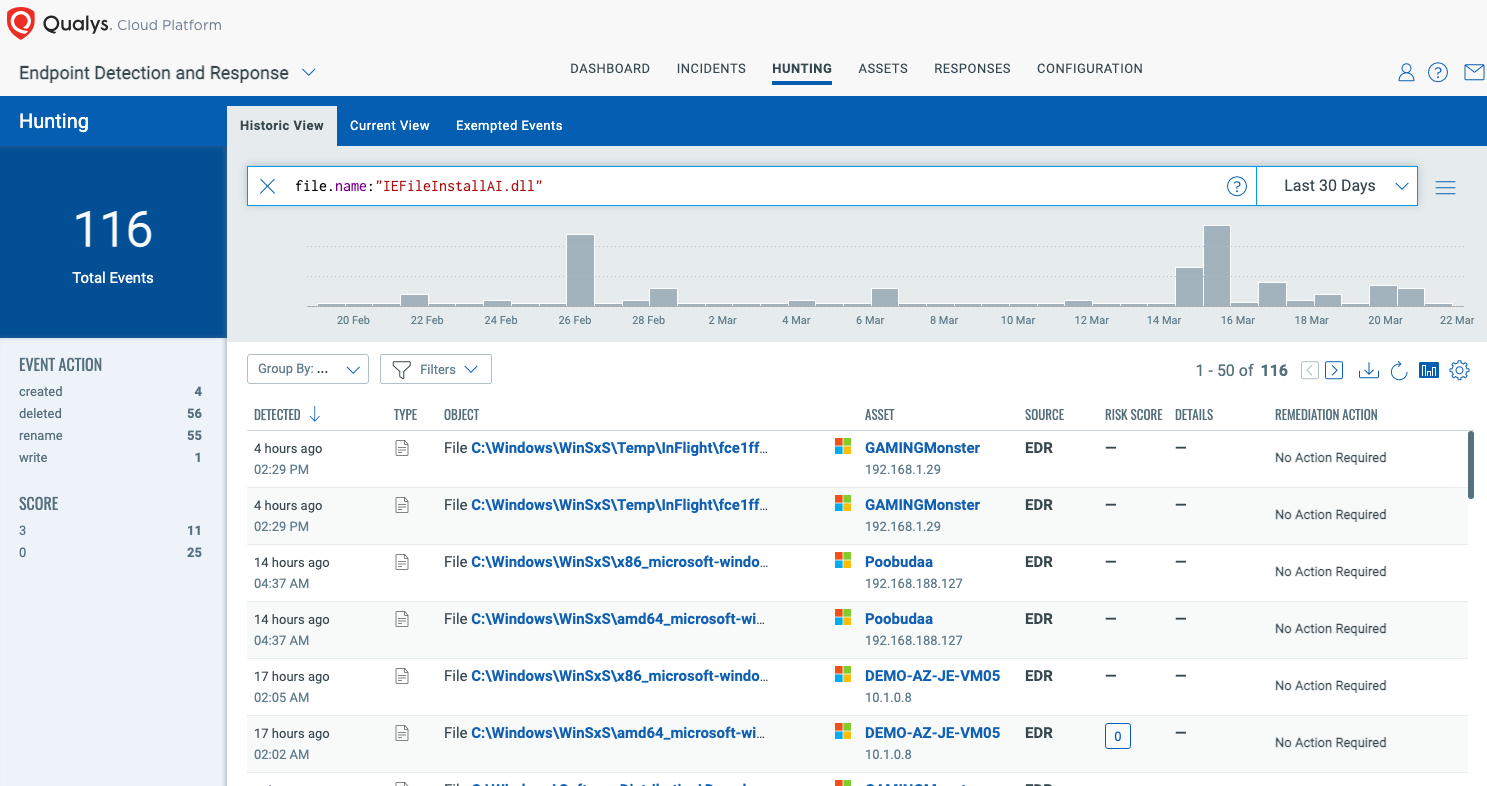
Qualys Endpoint Security consists of modern antivirus, EDR, anti-exploit, and endpoint controls. It prevents known and unknown attacks such as ransomware and phishing attempts. It provides the ability to block applications based on various criteria such as file name, file hash, file path and more. It can not only block the application but optionally, temporarily quarantine the asset also if needed.
2. Patch Applications
Unpatched applications are a prime target for attackers. Patching applications in a timely manner to reduce vulnerability, such as Flash, web browsers, Microsoft Office, Java, and PDF viewers, is key requirement. You need to patch/mitigate computers with vulnerabilities with ‘extreme risk’ within 48 hours and use the latest version of applications.
How Qualys Helps
Qualys Patch Management helps security and IT professionals efficiently remediate vulnerabilities and patch systems. Qualys allows you to identify (every 4 hours) missing patches on machines, detect and report on expiring software and hardware, and deploy patches automatically or manually. There is also support for Microsoft Office productivity and web browser extensions. Qualys offers industry-leading vulnerability scanning and patching that lets you create and validate patches. When you apply a patch, Qualys validates if it was applied correctly.
3. Configure Microsoft Office Macro Settings
Microsoft Office macros can be used to automate tasks across an Office productivity suite, but the macros can also be used for malicious purposes. At the highest maturity level, the E8 recommendations include disabling Microsoft Office macros for users where there is no demonstrated business need. You should configure Microsoft Office macro settings to block macros from the Internet, and only allow verified macros that are either in ‘trusted locations’ with limited write access or were digitally signed with a trusted certificate.
How Qualys Can Help
Qualys Policy Compliance (PC) has several assessment controls that can access and validate whether macros are appropriately configured and running from appropriate locations.
4. User application hardening
Application hardening focuses on reducing the likelihood that end-user applications will execute malicious code. The E8 user application hardening strategy recommends configuring web browsers to block Flash (ideally uninstalled), advertising, and Java on the web. Also, disabling unneeded features in Microsoft Office (e.g., OLE), web browsers, and PDF viewers. Auto-discovery for databases and middleware are important requirements to ensure hardening, so any solution should include this.
How Qualys Can Help
Qualys PC provides a rich library of 19,000 controls across 350 technologies that can help harden user applications with recommended security settings to ensure organizations have adequate security controls in place. Qualys PC helps you assess, prioritize, and remediate misconfigurations to ensure the strength of your security and compliance strategy. Qualys PC also includes auto-discovery for databases and middleware.
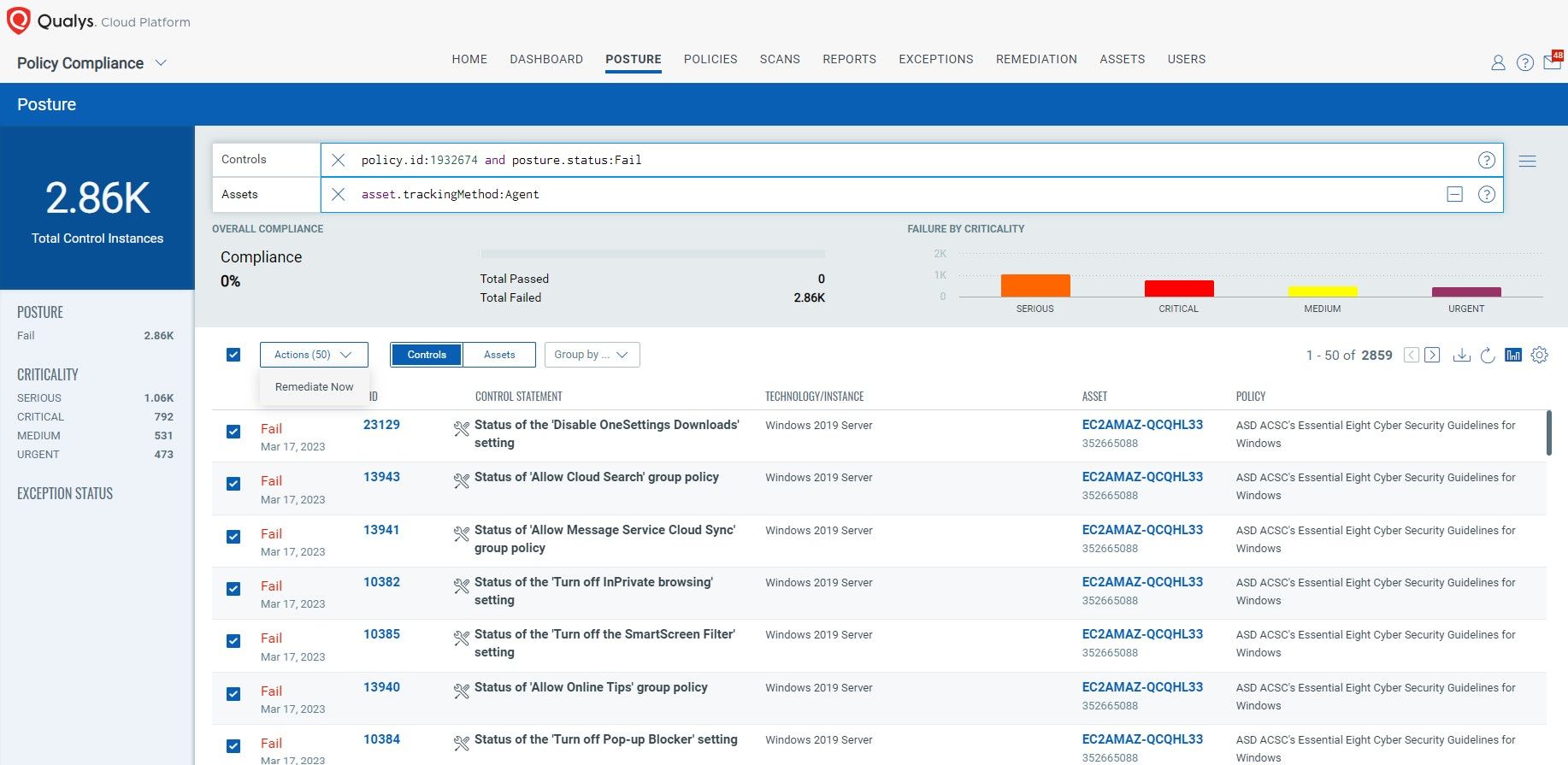
5. Restrict Administrative Privileges
Restricting administrative privileges is an ideal step toward preventing accidental or malicious system compromises and data breaches. It provides general recommendations for managing privileged access to systems and applications. You should limit administrative privileges for operating systems and applications based on user tasks. Also, periodically review the need for privileges. Restrict the use of privileged accounts for reading email and browsing the Internet. Privileged access should be validated, limited to specific tasks, and automatically disabled after periods of inactivity.
How Qualys Can Help
With Qualys PC, users are able to report on administration privileges and validate if proposed changes are needed. It also helps validate and report the level of administrative privilege compliance.
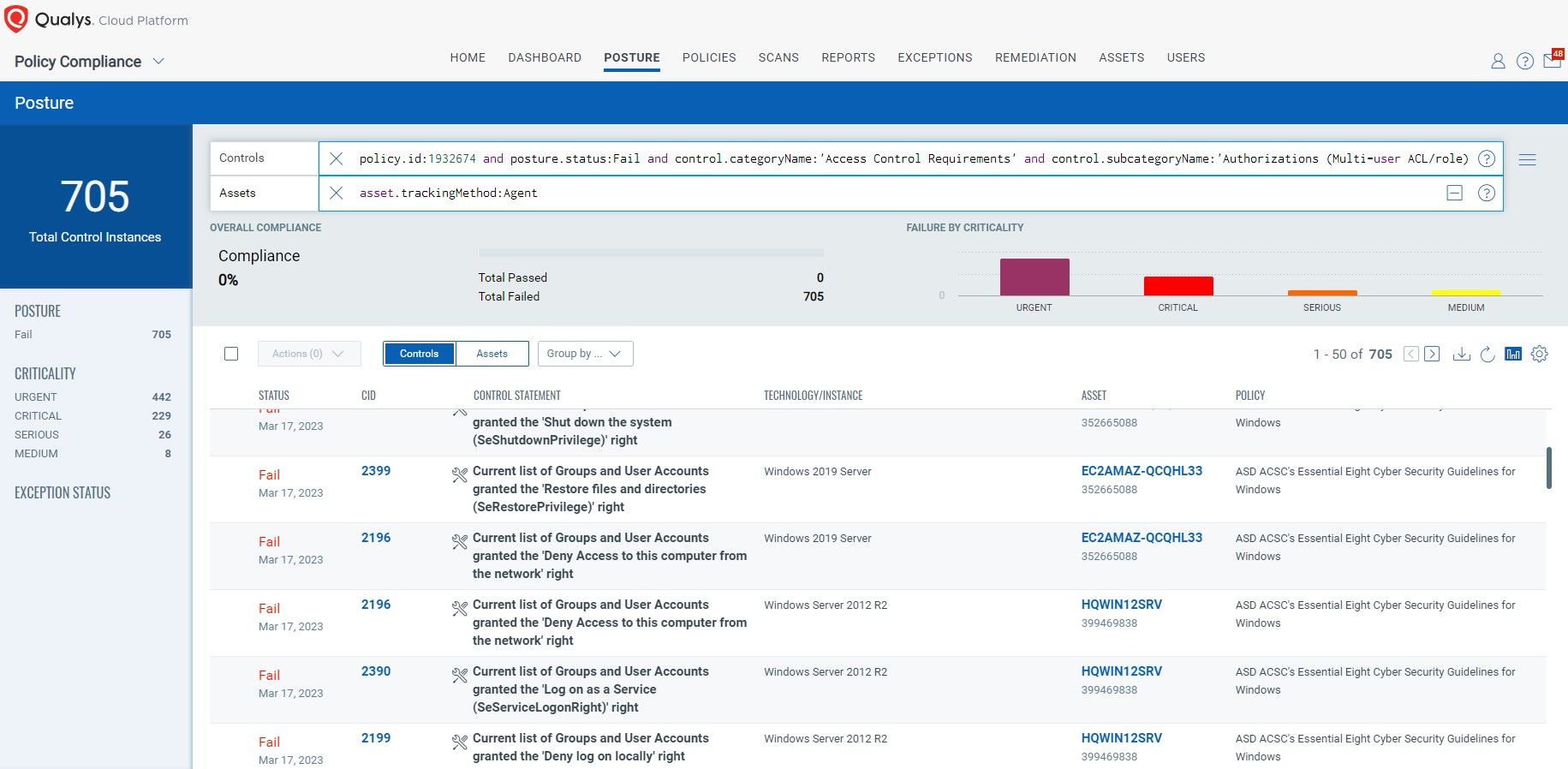
6. Patch Operating Systems
Operating system patching is sixth on the list, and focuses on timely application of vendor patches, updates, or remediation for vulnerabilities in workstation operating systems and Internet-based services. This should be done within 48 hours if a vulnerability exists. You should patch/mitigate computers (including network devices) with ‘extreme risk’ vulnerabilities within 48 hours and use the latest version of the operating system. Don’t use unsupported versions.
How Qualys Can Help
Qualys has market-leading vulnerability scanning that allows users to detect vulnerabilities and patch operating systems. It also allows you to report on assets that have either reached the end of their lifecycle or the end of support, as well as plan upgrades or other approaches to keep systems patched. This type of data may not be included in a typical vulnerability scan.
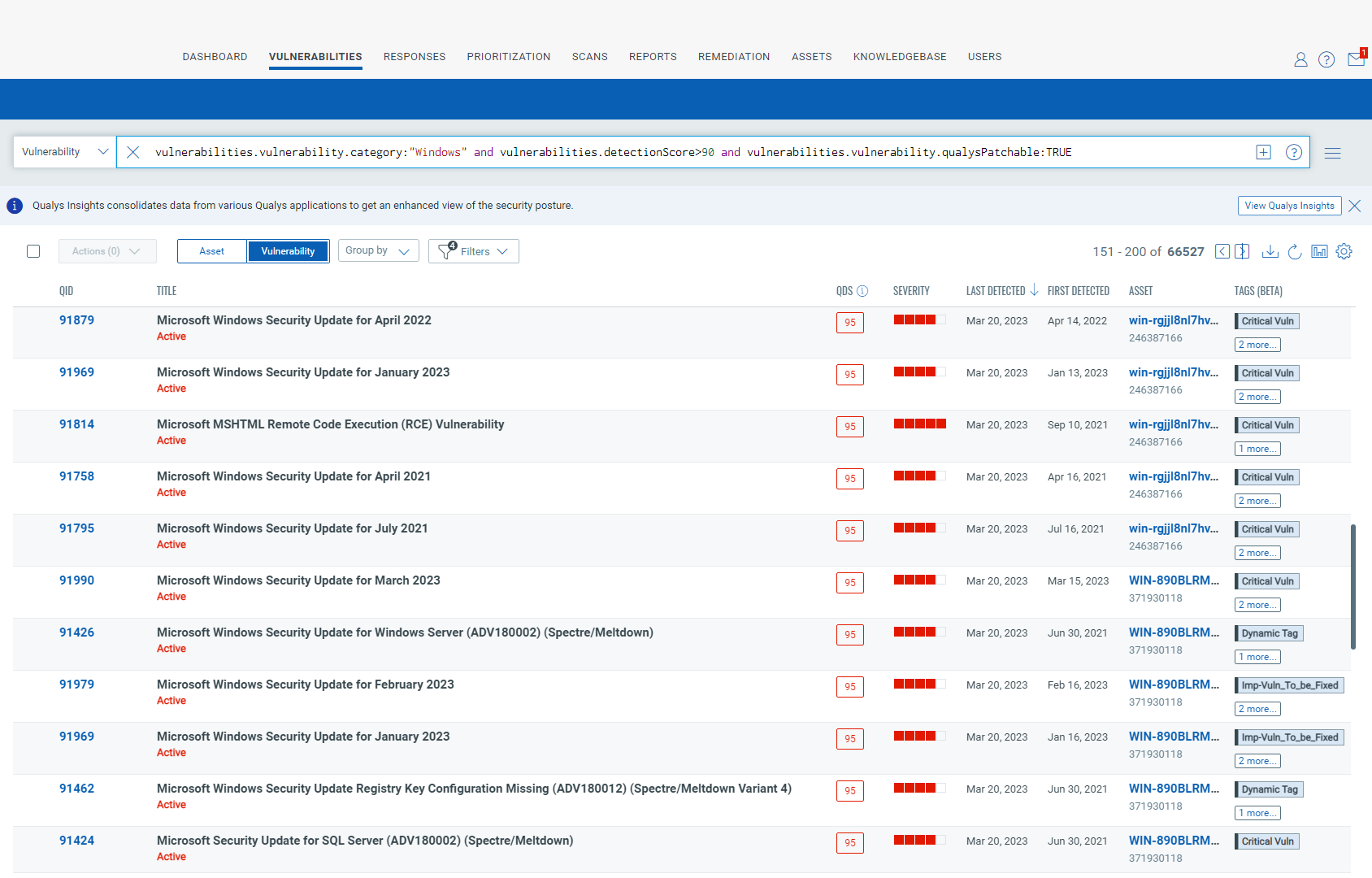
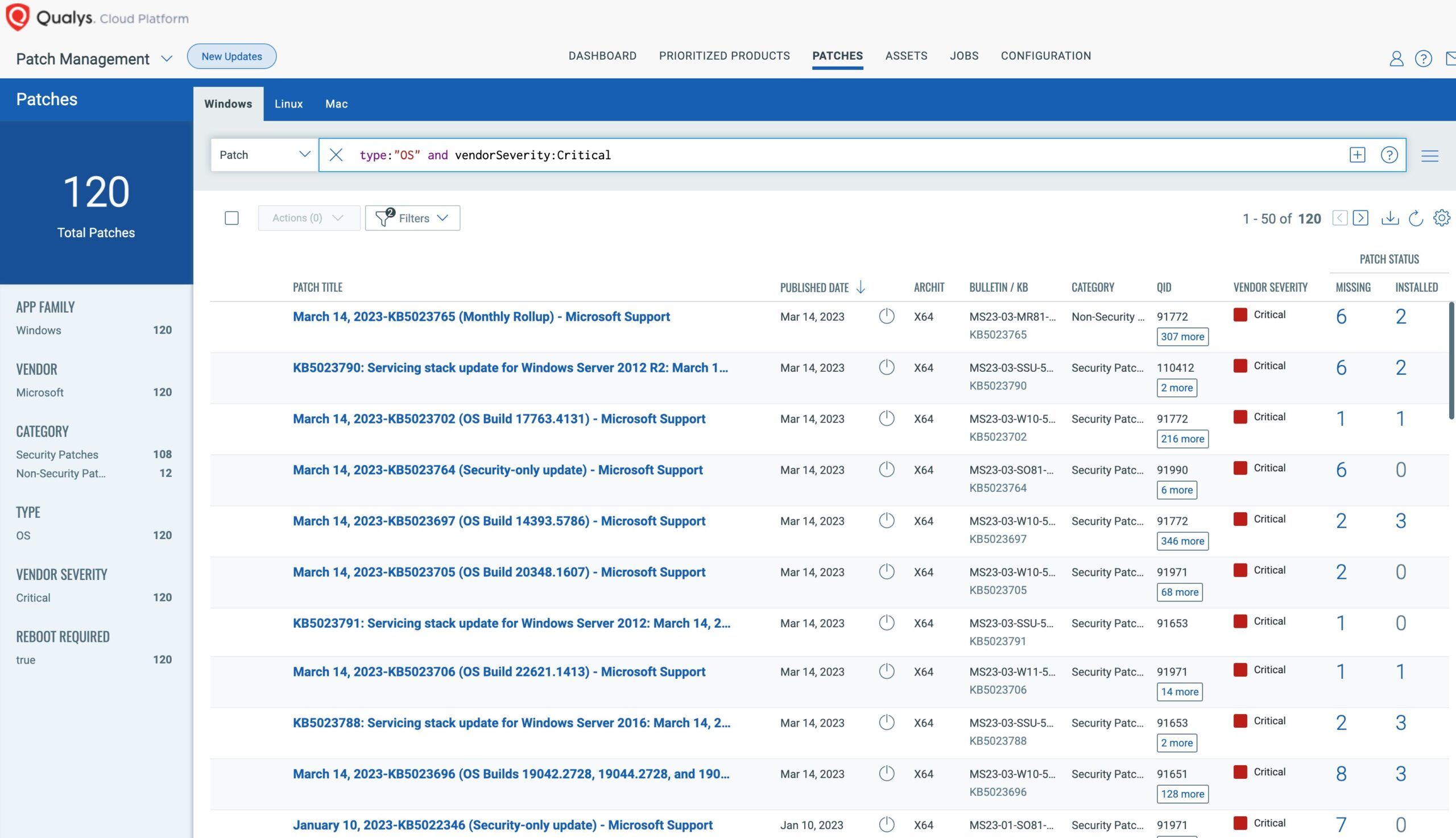
7. Multi-Factor Authentication
Number seven on the list of E8 strategies is the recommendation that employees use multi-factor authentication for Internet-based services. Also, for third-party Internet-based services for sensitive and non-sensitive corporate data, and generally for all users performing a privileged action or accessing an important (sensitive/high-availability) data area to prevent impersonation, including VPNs, RDP, SSH, and other remote access. Multi-factor authentication (MFA) has become a well-known standard to improve access to systems and services that rely on a single password.
How Qualys Can Help
Qualys validates MFA, a setting on Mac and Windows, and determines if MFA is enforced on several popular Internet services and third-party SaaS and PaaS platforms. Qualys also has partnerships with industry-leading MFA providers and the Qualys Cloud Platform supports MFA for access control.
8. Regular Backups
The final E8 strategy relates to a set of guidelines for backups and data protection. Daily backups should be done for important new or changed data, software, and configuration settings stored separately and retained for at least three months. In addition, recovery of systems, software, and critical data from backups should be tested in a coordinated manner during disaster recovery exercises (DR).
Qualys PC allows you to ensure backup related controls are in place and configured to ensure the continuity of the business.
How Qualys Can Help
Qualys checks whether backups have been created and whether the appropriate backup software or agent is running on the target computers, Qualys also checks the backup settings on the local computer.
Conclusions
The E8 is a set of mitigation strategies developed by the ACSC to help organisations reduce risks associated with cyberthreats. There are four maturity levels (MLs), with ML 3 being the highest. SMBs should strive to attain at least ML 2, and enterprises or government agencies, ML 3. Doing so often means cobbling together disparate point solutions that require separate agents and management. Some security products also lack automation and capabilities and therefore increase manual efforts and costs.
By using the Qualys Cloud Platform with the Qualys solutions covered in this blog, such as Qualys Policy Compliance, Patch Management, and CyberSecurity Asset Management, you can implement all of the E8 strategies and attain the highest ML desired. Also, you can assess and harden your entire technology stack without needing to set up controls from scratch. Your organisation will be able to implement the E8 recommendations quickly, easily, and effectively. With Qualys, you can become always audit-ready and able to reduce the risk of compliance failures, security breaches, brand damage, and litigation.
For government agencies and private sector enterprise firms needing to attain ML 3, the Qualys GovCloud Platform offers one of the only U.S. FedRAMP Ready solutions at the High Impact level, ensuring full compliance with all 421 controls covered in the National Institute of Standards and Technology (NIST) Special Publication 800-53 rev5. This platform will help you easily attain E8 ML 3.
Avoiding damaging cyberattacks by reaching ML 2 or above under Australia’s E8 does not need to be an arduous or expensive endeavor. Australian businesses can now enhance their cyber resilience with a single agent and robust cybersecurity platform from Qualys.
More Information
We invite you to join us on the journey to becoming always audit ready. Start your free trial of the Qualys Cloud Platform today. No software to download or install. You can also email us or call us at +1 (800) 745-4355 to request a demo from one of our technical account representatives.
Learn More
Authors
- Aparna Hinge, Senior Manager, Compliance Research Analysis, Qualys
- Bill Reed, Compliance Product Marketing
This post was first first published on Qualys Security Blog’ website by Aparna Hinge. You can view it by clicking here

