Effectively meeting and exceeding the requirements of the SAMA Cyber Threat Intelligence Principles
Effectively meeting and exceeding the requirements of the SAMA Cyber Threat Intelligence Principles
Munaf Kazi
Responsible for supervising nearly $1Trillion of assets across 30 banks and financial institutions, SAMA plays a crucial role in ensuring economic and financial stability within the Kingdom of Saudi Arabia.
The SAMA Cyber Security Framework and Threat Intelligence Principles are mandatory regulations for all member organisations regulated by the Saudi Arabian Monetary Authority (SAMA) operating within the Kingdom of Saudi Arabia. Based on my twenty years of experience in technology, security and threat intelligence I will outline the SAMA intelligence principles and detail areas I feel are important to member organisations as they mobilise to comply with these regulations.
Released in 2017 SAMA’s Cyber Security Framework outlined a common approach for managing cyber security risks. This was supplemented in 2022 with the Financial Sector Threat Intelligence Principles which seek specifically to expand upon the requirements within the Threat Management subdomain of the Framework by detailing best practices on the operational application of threat intelligence.
Outline
The SAMA Cyber Threat Intelligence Principles are divided into four areas:
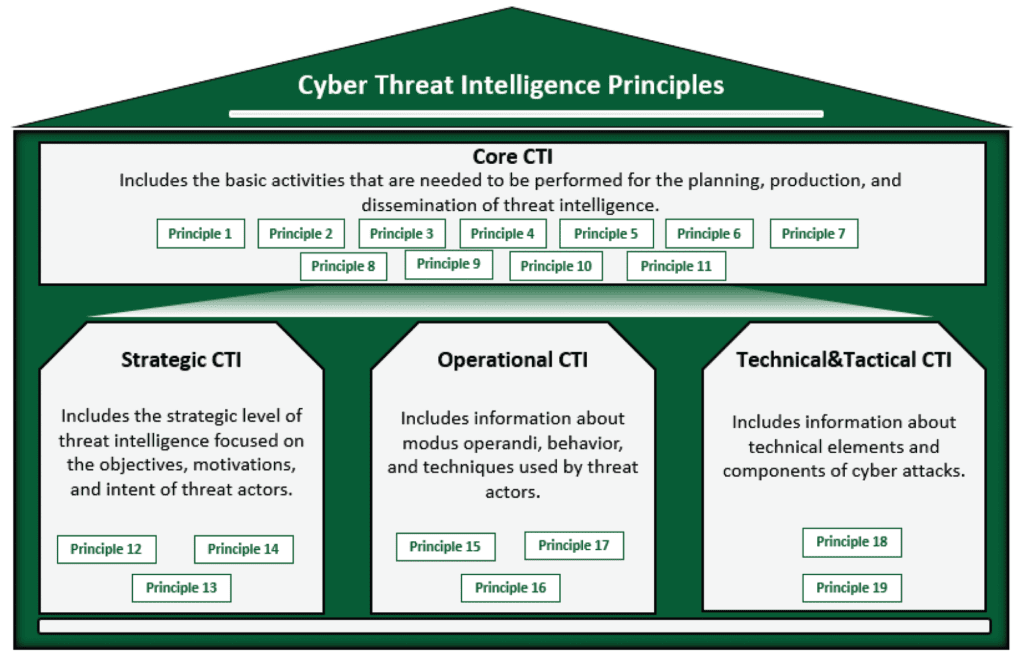
From the Financial Sector Cyber Threat Intelligence Principles V1.0 Pg 6.4
Core
Foundational policies and plans to equip the organisation to utilise threat intelligence effectively. This ranges from definition of threats to the member organisation and the creation of teams in order to develop and apply policies to mitigate those threats. This creates the capability within the organisation to generate and utilise threat intelligence and a scope for the to focus their activities significantly improving the efficacy of an intelligence programme.
Strategic
Expanding upon the defined threat to understand the risks posed by relevant threat actors, what their motivations are and what capabilities they have. For a finance organisation this could mean threat actors targeting them, it could mean actors with a specific geographic region that operate in or in some cases both. Use cases for mitigation aligned with the risk posture of the organisation can be created and mapped against these risks, these use cases should be utilised to inform the approach taken to manage these risks such as appropriate tools and resources and sufficient budget to acquire these. It is at this stage that threat intelligence management should be introduced as a central part of operation security planning.
Operational
Development of the capability of the member organisation to analyse intelligence data whether sourced externally or related to attacks observed by internal security teams. This information should be classified based on its relevance, attack phase,TTPs and catalogued within the threat intelligence platform.
For organisations operating under the the SAMA Cyber Security Framework and Threat Intelligence Principles they gain the ability to store, classify and analyse intelligence data which would provide actionable information allowing anticipation and therefore proactive mitigation of upcoming attacks.
Technical and Tactical
This relates to utilisation of process and technology to manage threats, i.e. the architecture and interoperability of technical controls such as XDR, SOAR, Perimeter Security with the Threat Intelligence Platform to allow for acquisition, prioritisation and dissemination of threat intelligence to allow it to be used as an extremely effective protection mechanism.
Usage
SAMA’s Threat Intelligence Principles cover many of the best practices required for a mature cyber security function and positively highlights that threat intelligence is no longer an optional add-on that can be tacked onto a cyber security programme and instead must be considered and integrated into its core. This is due to the role threat intelligence plays in reducing the impact of new threats but also in drastically reducing the dwell time that attackers have within an organisation where they can really cause significant damage to its brand as well as halting day to day operations, both resulting in cost due to clean-up of the attack and potential share price reduction leading to shareholder loss of confidence.
The principles include areas that need to be considered on policy, process and technical fronts, from definition of intelligence priorities to the acquisition and application of intelligence related to those priorities. Sensible tooling which can expand and adapt to the varying needs for collection, management and dissemination of intelligence across member organisations can make the task of dealing with the breadth of the requirements much simpler.
For example, the principles create the requirement for a Threat Intelligence Platform (TIP) which can automatically pull information (Principle 18) in from sources relevant to the member organisation’s requirements (Principle 12) and then apply this intelligence (Principle 18) to detecting and blocking attacks such as Spear Phishing via integration with XDR Platforms and Mail Security tooling (Principle 9) as well as assisting with improving alert triage efficiency.
Requests for information (Principle 14) can be handled in a more effective way by allowing individual aspects of a threat (Principles 16&17) to be managed independently ensuring that as a threat adapts it is quick and easy to update relevant information – maintaining the accuracy of the wider picture for executives and stakeholders down to support teams and analysts (Principle 8).
I have observed that threat intelligence providers indeed do supply immensely valuable data – but cannot practically cover all threats to an organisation. The ability to classify and store artefacts (Domain 4) from attacks a member organisation has directly experienced enables the capability to identify malicious actors but also allows identification of relevant TTPs with certainty and any related to attack vectors and potential vulnerabilities.
These vulnerabilities can then be managed via the member organisations standard Vulnerability Management programme (Principle 19). The benefit of capturing and maintaining data on the vulnerabilities which affect the specific technologies used by the member organisations within the intelligence platform as part of its extensible data set provides the ability to prioritise remediation, especially when combined with asset, campaign, malware and TTP information. This can be automated through orchestration and the ability to integrate with vulnerability management tooling as described by the diagram below:
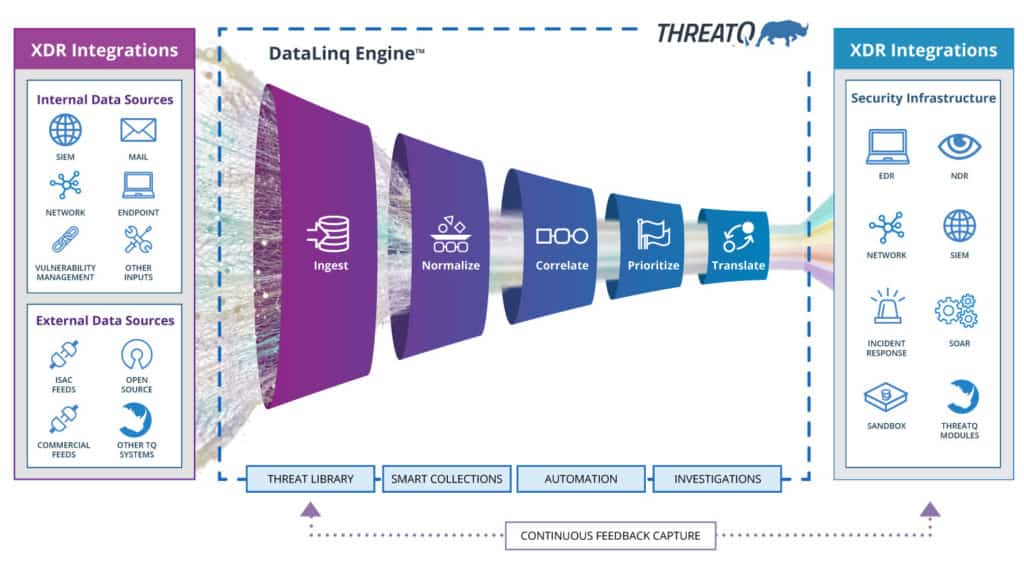
Conclusion
The SAMA Cyber Threat Intelligence Principles set the guidelines for the financial sector in the Kingdom of Saudi Arabia on how to increase the maturity of their Threat Intelligence Practice, it covers all the aspects from people, processes, and technology. But more than this they have set an effective roadmap to security excellence not just within the region but globally and not just for financial institutions but for any organisation which chooses to follow them.
ThreatQ will assist organisations to cover the technology part of the principles and will also serve to automate processes through its Automation and XDR capabilities. This will not only aid organisations in complying with the principles, but it will also help them towards a maturer and more efficient overall security programme within the member organisation.
The post Effectively meeting and exceeding the requirements of the SAMA Cyber Threat Intelligence Principles appeared first on ThreatQuotient.

