Ease Your Cybersecurity Maturity Model Certification Journey With Qualys
The Cybersecurity Maturity Model Certification (CMMC) is a cybersecurity training, certification, and assessment program from the United States Department of Defense (DoD). CMMC is designed to provide increased assurance to the DoD that a contractor can adequately protect controlled unclassified information (CUI), including accounting for information flow to subcontractors in a multi-tier supply chain.
The CMMC security framework governs Defense Industrial Base (DIB) contractors. Compliance with the CMMC framework incorporates processes and security implementations of several U.S. federal cybersecurity standards such as the National Institute of Standards and Technology (NIST), Federal Acquisition Regulation (FAR), and Defense Federal Acquisition Regulation Supplement (DFARS). If your organization wants to be a U.S. DoD contractor, it must comply with CMMC.
Why Is CMMC Compliance Important?
With CMMC compliance, an organization can ensure continuous monitoring and upgrading of cybersecurity to prevent a bad actor from successfully executing malicious attacks. CMMC will protect data shared within the defense industry that the DIB uses to produce parts, systems, and components for national defense. DIB contractors hold and use sensitive government data to develop and deliver these goods and services. The CMMC helps contractors ensure that they secure this information by using identical processes implemented by military departments and civilian government agencies.
CMMC helps DIB organizations:
- Safeguard sensitive information through proper cybersecurity hygiene with a “trust but verify” model to improve cybersecurity and address new emerging threats
- Ensure accountability while streamlining hurdles for compliance with DoD requirements
- Introduce a collaborative culture of cybersecurity and cyber resilience
- Maintain public trust through high professional and ethical standards
What Happens if DIBs are Not CMMC Compliant?
If a DIB does not meet minimum CMMC level requirements, it may be unable to bid on DoD contracts and lose that source of revenue. In extreme cases, a DIB could even face business closure. Noncompliance may also expose the DIB to other cyber threats. Engaging with the CMMC compliance process now will help guide your DIB toward a more secure future.
The CMMC 1.0 framework was published in January 2020 and updated as CMMC 2.0 in November 2021. CMMC 2.0 is published on the DoD CMMC website.
How CMMC 2.0 Helps Streamline Compliance
The intent of CMMC 2.0 is to streamline the original framework by reducing the number of compliance requirements and processes to simplify how DIB contractors self-certify their compliance. The key changes between CMMC 1.0 and CMMC 2.0 are:
- The number of CMMC levels was reduced from five to three.
- Level 1 (Foundational)
- Level 2 (Advanced)
- Level 3 (Expert)
- CMMC 2.0 dropped 20 security requirements to align completely with the 110 security controls of NIST SP 800-171 Rev. 2. The new Level 2 certification will indicate that an organization can securely store and share controlled unclassified information.
- Unlike the 1.0 framework, CMMC 2.0 will allow for limited use of Plans of Action and Milestones (POAMs). POAMs can only be used for 1- and 3-point controls and a very limited number of 5-point controls.
- Waivers for certification will be permitted in very limited circumstances.
The transition from CMMC 1.0 to 2.0 can be seen in the image below:
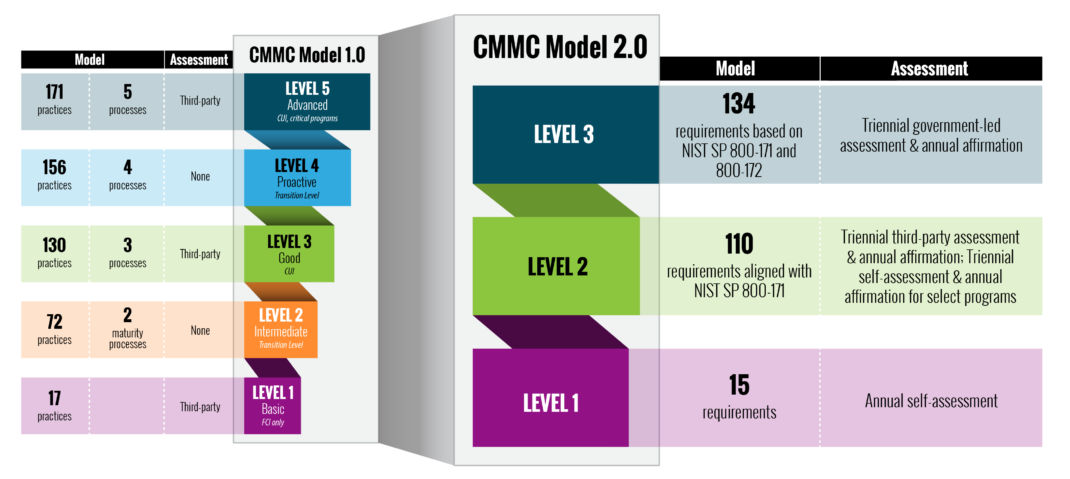
Figure 1. Transition from CMMC 1.0 to 2.0
Challenges with CMMC Implementation
- The biggest challenge is to map other frameworks, which include FAR Clause 52.204.21, NIST-SP 800-71 Rev. 2, and NIST-SP 800-172; these are spread across 14 domains and 100+ practices.
- The time-consuming and resource-intensive task to implement 14 domains and 100+ practices manually.
- Understanding the Controls, practices, and domains in detail is a huge task.
- It’s an enormous challenge to achieve compliance without using a tool to guide the CMMC compliance process.
Ease Your Path to CMMC Compliance with Qualys
Qualys Policy Compliance (PC) is a cloud-based tool that provides DIB contractors with a holistic view of CMMC compliance posture using mandate-based reporting against the CMMC 2.0 framework.
- Qualys gives DIB stakeholders the ability to select an individual CMMC level that is applicable to the organization.
- The PC Comprehensive Compliance report includes section-by-section compliance status against each CMMC 2.0 domain and all the best practices.
- Our tool makes your task easy to see which sections need remediation for achieving full compliance with CMMC 2.0.
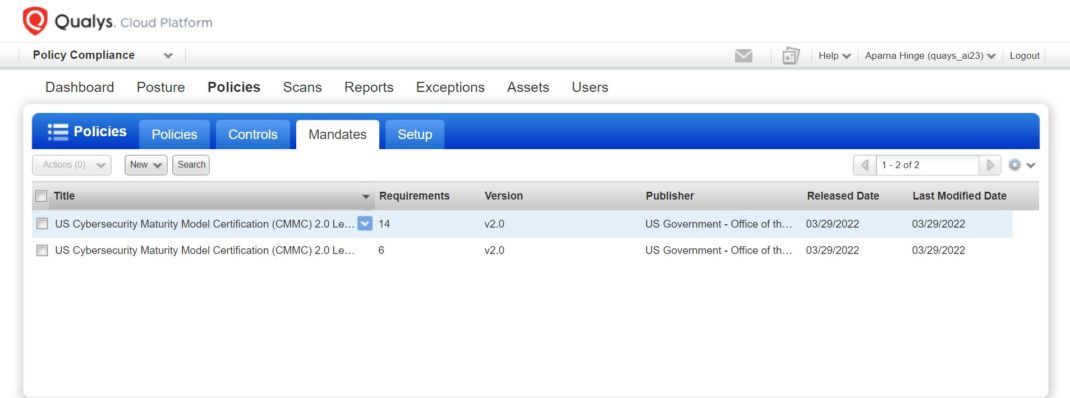
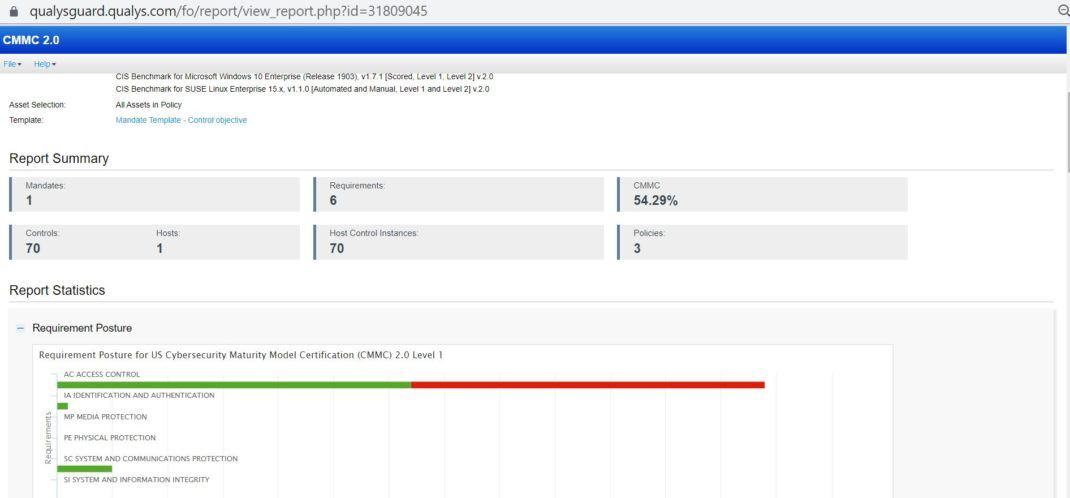
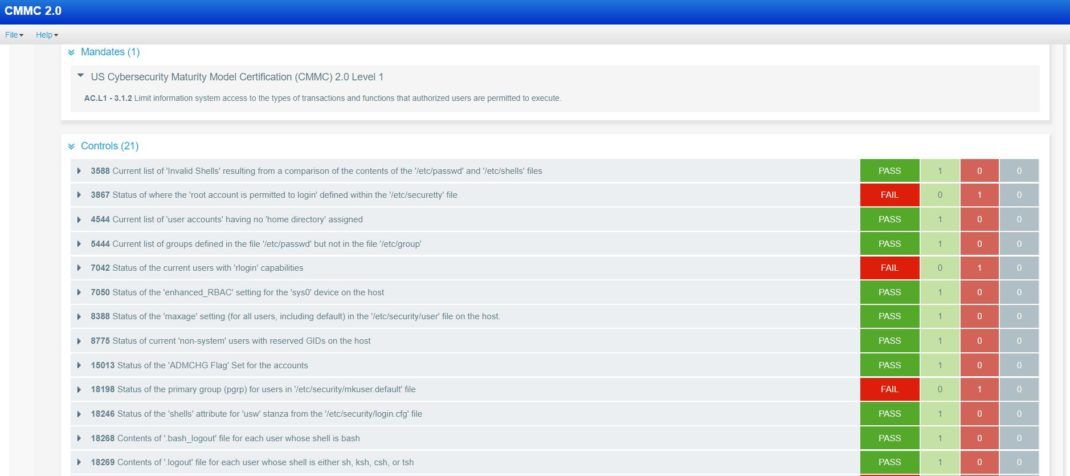
Qualys PC Screenshots for CMMC Compliance
The screenshots below provide a sense of how easy it is to instantly see CMMC compliance posture and where remediation may be required.
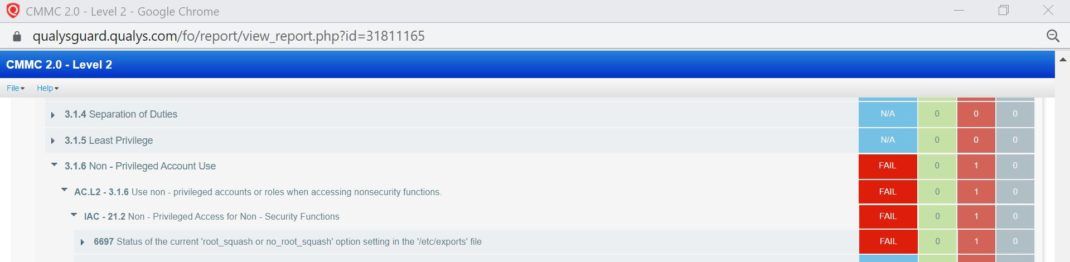
Summary
The Cybersecurity Maturity Model Certification framework is a critical requirement for U.S. Defense Industrial Base contractors to ensure that sensitive information is protected from malicious attacks throughout the supply chain. The framework also helps contractors to streamline compliance – but even the new slimmed-down CMMC 2.0 can be a major challenge without using a tool to automate its many moving parts. The cloud-based Qualys Policy Compliance tool will help a DIB contractor immediately get the full picture of CMMC compliance posture and simplify processes to achieve full compliance with this federal mandate. You can learn more about Qualys PC on our website. We also invite you to get a free trial of the PC by clicking here or by contacting your Qualys Technical Account Manager.
Resources
Enhancements to Control Mappings for Mandate Based Reporting
Control Mappings for Mandate Based Reporting
This post was first first published on Qualys Security Blog’ website by Aparna Hinge. You can view it by clicking here

