Inside the James Webb Attack Image
Appending data to an image is a well-known way of hiding malware. In this case, the executable data is Base64 encoded and surrounded by markers indicating it is a certificate. This allows the attack to use the standard “certTool” utility to unpack the Base64 data – an example of “living off the land.”
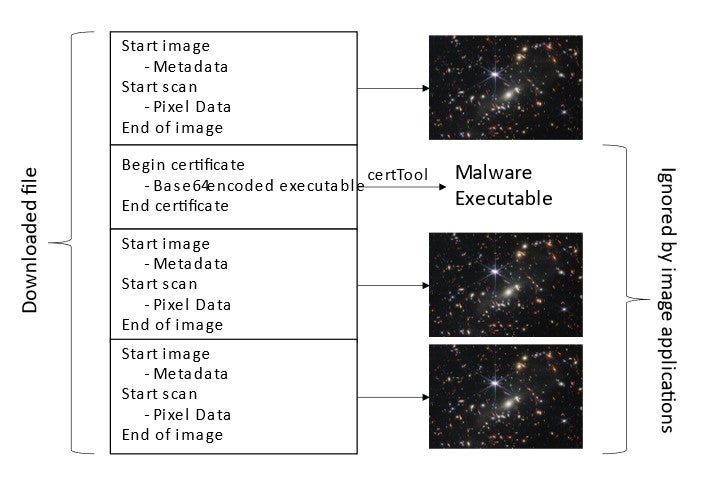
The downloaded file isn’t a simple image. It is, in fact, a jpeg image packed with more data that is ignored by any applications that display the file. This is where the malware is hidden.
But what is strange about this file is there are two more copies of the James Webb picture following the “certificate.” It is not clear why this is the case. One possibility is that any defences that make sure it is a valid jpeg by checking the start and end would be fooled by this. But why have a third? All it seems to do is make the file bigger.
Although there is a lot of discussion around hiding malware by appending it to images, recent attacks have taken a more sophisticated approach. They include the malware inside the image by either storing it as metadata or encoding it in the colour values of the pixels – a technique called steganography. It is interesting that the attack has taken the simple approach of appending data, yet still managed to defeat protection-based defences.
By comparison, Forcepoint’s Zero Trust Content Disarm & Reconstruction (CDR) is not fooled by this trick. CDR extracts the pixels from the first copy of the image in the file and ignores the rest of the data. Then it creates a new jpeg containing those pixels. So, no matter how the data is appended to the image, it always gets left behind.
Learn more about how Zero Trust CDR can strengthen your organisations cyber environment.
Even if this attack had taken more steps to hide the malware, Zero Trust CDR would still have stopped it getting through. Zero Trust CDR transforms and constrains image metadata and resamples the pixels to remove any hidden information.
This post was first first published on Forcepoint website by Ellie Moore. You can view it by clicking here

