July 2022 Patch Tuesday | Microsoft Releases 84 Vulnerabilities with 4 Critical, plus 2 Microsoft Edge (Chromium-Based); Adobe Releases 4 Advisories, 27 Vulnerabilities with 18 Critical.
Microsoft has fixed 84 vulnerabilities (aka flaws) in the July 2022 update, including four (4) vulnerabilities classified as Critical as they allow Remote Code Execution (RCE). This month’s Patch Tuesday cumulative Windows update includes the fix for one (1) actively exploited zero-day vulnerability (CVE-2022-22047). Earlier this month, July 6, 2022, Microsoft also released two (2) Microsoft Edge (Chromium-Based) security updates as well.
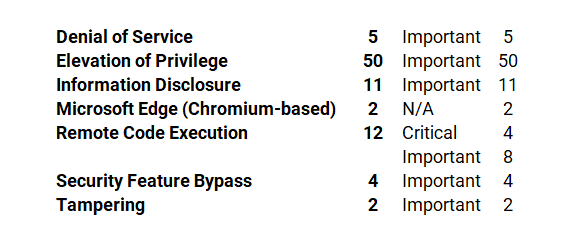
Microsoft has fixed several flaws in its software, including Denial of Service (DoS), Elevation of Privilege, Information Disclosure, Microsoft Edge (Chromium-based), Remote Code Execution (RCE), Security Feature Bypass, and Tampering.
Many of the vulnerabilities patched this month relate to remote code execution, but there are no reports of active exploitation (in the wild) except for CVE-2022-22047, a Windows CSRSS Elevation of Privilege Vulnerability.
The July 2022 Microsoft vulnerabilities are classified as follows:
![]()
![]()
Related Threat Protection Post
CVE-2022-22047 | Windows CSRSS Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 7.8/10.
Elevation of Privilege – Important – An attacker who successfully exploited this vulnerability could gain SYSTEM privileges. (Article 5015874)
Exploitability Assessment: Exploitation Detected
This month’s advisory covers multiple Microsoft product families, including Azure, Browser, ESU, Microsoft Dynamics, Microsoft Office, System Center, and Windows.
A total of 63 unique Microsoft products/versions are affected.
Downloads include Monthly Rollup, Security Only, and Security Updates.
CVE-2022-30221 | Windows Graphics Component Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10.
An attacker would have to convince a targeted user to connect to a malicious RDP server. Upon connecting, the malicious server could execute code on the victim’s system in the context of the targeted user.
Windows 7 Service Pack 1 or Windows Server 2008 R2 Service Pack 1 are only affected by this vulnerability if either RDP 8.0 or RDP 8.1 is installed. If you do not have either of these versions of RDP installed on Windows 7 SP1 or Window Server 2008 R2 SP1, then you are not affected by this vulnerability.
Exploitability Assessment: Exploitation Less Likely
CVE-2022-22029 | Windows Network File System Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 8.1/10.
This vulnerability could be exploited over the network by making an unauthenticated, specially crafted call to a Network File System (NFS) service to trigger a Remote Code Execution (RCE).
Successful exploitation of this vulnerability requires an attacker to invest time in repeated exploitation attempts through sending constant or intermittent data.
Exploitability Assessment: Exploitation Less Likely
CVE-2022-22038 | Remote Procedure Call Runtime Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 8.1/10.
Successful exploitation of this vulnerability requires an attacker to invest time in repeated exploitation attempts through sending constant or intermittent data.
Exploitability Assessment: Exploitation Less Likely
CVE-2022-22039 | Windows Network File System Remote Code Execution Vulnerability
This vulnerability has a CVSSv3.1 score of 7.5/10.
Successful exploitation of this vulnerability requires an attacker to win a race condition.
This vulnerability could be exploited over the network by making an unauthenticated, specially crafted call to a Network File System (NFS) service to trigger a Remote Code Execution (RCE).
Exploitability Assessment: Exploitation Less Likely
Earlier in July, Microsoft released Microsoft Edge (Chromium-based) vulnerabilities CVE-2022-2294 and CVE-2022-2295. The vulnerability assigned to each of these CVEs is in the Chromium Open Source Software (OSS) which is consumed by Microsoft Edge. It is being documented in the Security Update Guide to announce that the latest version of Microsoft Edge (Chromium-based) is no longer vulnerable. Please see Security Update Guide Supports CVEs Assigned by Industry Partners for more information.
Adobe released four (4) advisories with updates to fix 27 vulnerabilities affecting Adobe Acrobat, Character Animator, Photoshop, Reader, and RoboHelp applications. Of these 27 vulnerabilities, 18 are rated as Critical; ranging in severity from a CVSS score of 6.5/10 to 7.8/10, as summarized below.

APSB22-10 | Security update available for RoboHelp
This update resolves one (1) Important vulnerability.
Adobe has released a security update for RoboHelp. This update resolves a vulnerability rated important. Successful exploitation could lead to arbitrary code execution in the context of current user.
APSB22-32 | Security update available for Adobe Acrobat and Reader
This update resolves 22 vulnerabilities; 15 Critical, and seven (7) Important.
Adobe has released security updates for Adobe Acrobat and Reader for Windows and macOS. These updates address multiple critical, and important vulnerabilities. Successful exploitation could lead to arbitrary code execution and memory leak.
APSB22-34 | Security Updates Available for Adobe Character Animator
This update resolves two (2) Critical vulnerabilities.
Adobe has released an update for Adobe Character Animator for Windows and macOS. This update resolves critical vulnerabilities. Successful exploitation could lead to arbitrary code execution.
APSB22-35 | Security update available for Adobe Photoshop
This update resolves two (2) vulnerabilities; one (1) Critical, and one (1) Important.
Adobe has released an update for Photoshop for Windows and macOS. This update resolves a critical vulnerability and an important vulnerability. Successful exploitation could lead to arbitrary code execution and memory leak.
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its KnowledgeBase (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability:( qid:`91921` OR qid:`91922` OR qid:`91923` OR qid:`91924` OR qid:`91927` OR qid:`110411` OR qid:`110412` OR qid:`376725` ) 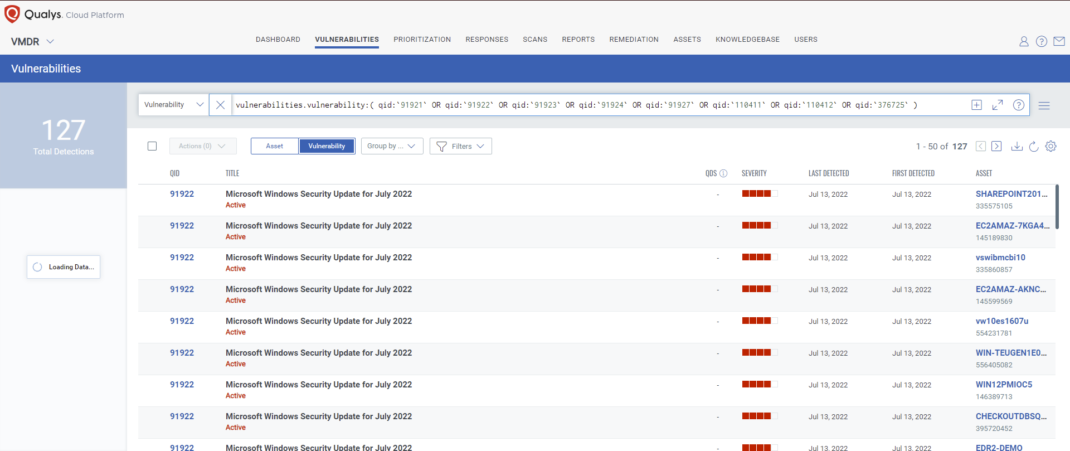
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches in one go.
The following QQL will return the missing patches for this Patch Tuesday:
( qid:`91921` OR qid:`91922` OR qid:`91923` OR qid:`91924` OR qid:`91927` OR qid:`110411` OR qid:`110412` OR qid:`376725` ) 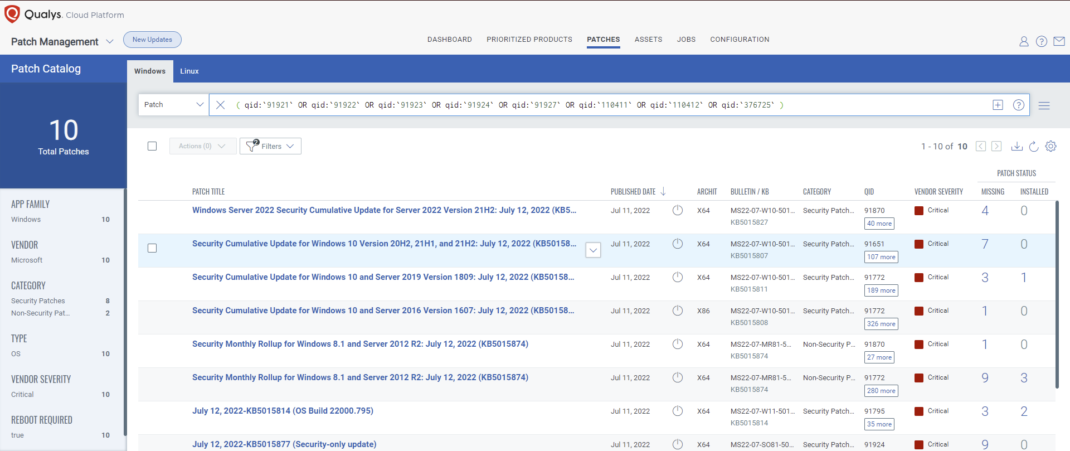
![]()
![]()
Risk-based Remediation Powered by Patch Management in Qualys VMDR 2.0

The Qualys Research team hosts a monthly webinar series to help our existing customers leverage the seamless integration between Qualys Vulnerability Management Detection Response (VMDR) and Qualys Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are part of this month’s Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Qualys Patch Management.
Join the webinar
This Month in Vulnerabilities & Patches
This post was first first published on Qualys Security Blog’ website by Debra M. Fezza Reed. You can view it by clicking here

