What Is Security Service Edge (SSE)?
Security Service Edge (SSE), first introduced by Gartner in early 2021, is a single-vendor, cloud-centric converged solution that accelerates digital transformation by securing enterprise access to the web, cloud services, Software-as-a-Service, and private applications and is considered an essential component to building cloud and networking security capable of accommodating improved performance and growth.
According to Gartner, SSE is primarily delivered as a cloud-based service and may include a hybrid of on-premises or agent-based components. SSE cloud-based components and capabilities include:
- Access control
- Threat protection
- Data security
- Security monitoring
- Acceptable use control enforced by network-based and API-based integration
What’s the difference between SASE and SSE?
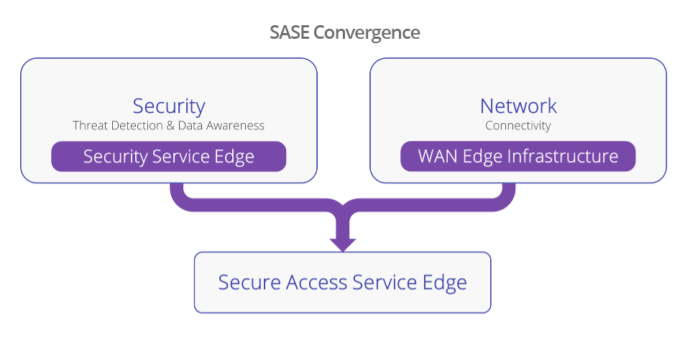
Secure Access Service Edge (SASE), introduced by Gartner in 2019, is the convergence of networking and security technologies into a single cloud-delivered platform to enable secure and fast cloud transformation. In this next evolution of SASE, Gartner introduces a two-pronged vendor approach bringing together a highly converged Wide Area Network (WAN) Edge Infrastructure platform alongside a highly converged security platform – known as Security Service Edge (SSE).
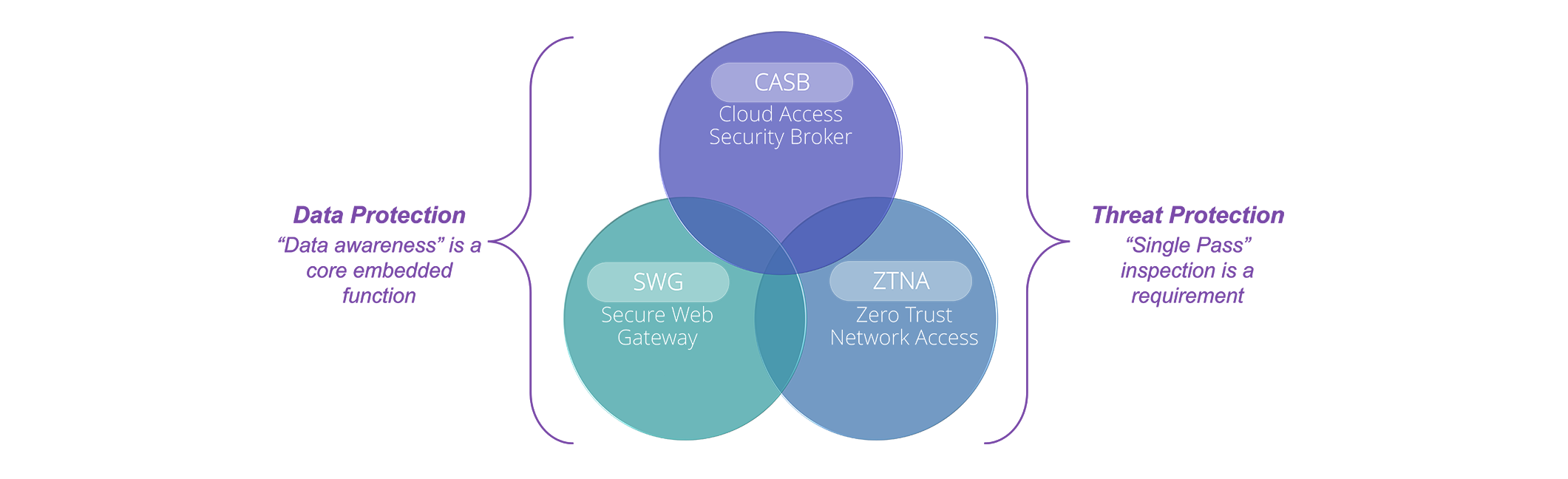
Security Service Edge (SSE), is the security component of SASE that unifies all security services, including Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), and Zero Trust Network Access (ZTNA), to secure access to web, cloud services, and private applications. WAN Edge Infrastructure, the networking component in the SASE framework, focuses on the network connectivity element by transforming network architectures to enable a more efficient direct-to-cloud connectivity.
Within the SASE framework, both networking and security are consumed in a unified manner and delivered as a cloud service. SSE converges with WAN Edge Infrastructure to achieve a complete SASE platform. SSE security services include:
- Cloud Access Security Broker (CASB)
CASB acts as an intermediary between users and cloud service providers as enterprises move their sensitive assets to the cloud, helping to address the gaps in data visibility, security, and compliance, extending security policies from existing on-premises infrastructure, and creating new policies for cloud specific content. Integrated CASB in an SSE model automatically discovers and controls Software-as-a-Service (SaaS) risks and serves as an API-based security process for scanning SaaS applications for data, malware, and policy violations while leveraging User and Entity Behavior Analytics (UEBA) and artificial intelligence (AI) capabilities for real-time threat prevention. - Secure Web Gateway (SWG)
SWG is a cyberbarrier that acts as a checkpoint preventing unauthorized traffic from entering an enterprise’s network. A SWG allows users to access approved, secure websites and protects users from web-based threats by connecting the user and website while running protective functions such as URL filtering, web visibility, malicious content inspection, and web access controls. - Zero Trust Network Access (ZTNA)
ZTNA enforces granular, adaptive, and context-aware policies for providing secure Zero Trust access to private applications hosted across clouds and corporate data centers from any remote location and device. ZTNA acts as a key enabler for Secure Access Service Edge (SASE), transforming the security perimeter to a dynamic, policy-based, cloud-delivered edge, to support the access requirements of the digital transformation. - Data Loss Prevention (DLP)
DLP enables policy-based classification of information content contained within an object, typically a file, while in storage, in use or in motion across a network. DLP tools are used to apply these policies in real-time to extend necessary protection to sensitive data elements, and to limit the access and flows of this information, especially outside of the organization, as required by the organization’s policies. - Remote Browser Isolation (RBI)
RBI is a powerful form of web threat protection which contains web browsing activity inside an isolated cloud environment. RBI protects users from any malware or malicious code that may be hidden on a website and eliminates the opportunity for malicious code to touch the end user’s device. - Firewall as a Service (FWaaS)
FWaaS is a cloud-based firewall solution that secures data and applications on the internet. SSE utilizes FWaaS to aggregate traffic from a variety of sources including on-site data centers, cloud infrastructure, branch offices, and mobile users. FWaaS also delivers consistent application and security enforcement of policies across all locations and users, while providing complete network visibility and control.
How to deploy and manage SASE?
There are two directions an enterprise can take to create an effective SASE solution:
- One-vendor approach. Assess and engage a single vendor offering which combines a WAN Edge Infrastructure and an SSE solution. Although this approach can satisfy the SASE requirements for an organization by simplifying operations, it may include giving up advanced security features that only an SSE vendor can provide. In the long run, the lack of advanced security features may end up being more costly if additional security vendor solutions need to be acquired to fill the gaps.
- Two-vendor approach. Assess and engage a two-vendor solution that provides a best-of-breed WAN Edge Infrastructure solution and SSE security solution converging CASB, SWG, ZTNA, RBI, and FWaaS components within an integrated offering. This two-vendor approach simplifies and streamlines system deployment, management, and maintenance long-term.
What are the benefits of SSE?
As the demands of a remote workforce and customer base have increased, enterprises have struggled with the challenge of reducing the complexity of their security strategy while improving security and user experience. Security Service Edge (SSE) consolidated technologies have proven effective in decreasing the complexity of endpoint protection while increasing cloud services security throughout an enterprise.
A complete SSE strategy offers enterprises a comprehensive set of security technologies that provide benefits to employees and stakeholders – on-site and remote:
- Direct, safe internet access to applications, tools, data, and resources from anywhere in the world, while reducing processing traffic for unauthorized access, data, risk, and threats, improving processing traffic for unauthorized access, data risk, and threats, eliminating the need to route traffic back through the datacenter
- Faster, secure, more efficient connectivity to web, cloud, and private apps when accessing application resources from any user, any device, anywhere
- Monitoring and tracking behavior of users accessing the network
- Threat defense within the cloud and from any web destination, detecting both cloud-native attacks and advanced malware
- Data protection through the internet, within the cloud, and moving from cloud-to-cloud
- Enabling secure Zero Trust access to data and applications based on user identity, context, and least privileged access
What are top challenges SSE addresses?
SSE addresses the fundamental security challenges of remote work, digital business enablement, and cloud transformation. As adoption of SaaS, PaaS, and IaaS grows, there is more data outside of the data center, users are increasingly working remotely, and the VPNs are slow and often easily exploited. All of this is difficult to secure using legacy network architectures.
SSE helps organizations address key use cases:
- Simplifying administration and management of security controls.
Organizations must administer cloud and on-premises with a patchwork of different and disparate security controls that vary between cloud providers and on-premise infrastructure. SSE helps reduce cost and complexity, allowing for simplified adoption and deployment of policies across on-premises, cloud, and remote work environments. - Replacing VPNs to secure remote workers accessing private applications.
Enterprises must implement a more secure solution to protect against the rapid increase of remote workers accessing private apps in highly vulnerable environments. VPNs present an inherent security risk by implicitly granting unrestricted trust-based access to the entire corporate network once authenticated. SSE’s ZTNA capability helps provide granular resource access, permitting the appropriate levels of access for any user, anywhere. - Preventing advanced malware and ransomware to protect web users.
Enterprises need detection and mitigation of advanced malware and other threats. Many modern attacks use techniques like social engineering to exploit the features of cloud providers and mimic user behavior with legitimate credentials. SSE’s SWG capability helps by providing an inline cyberbarrier responsible for monitoring web traffic and preventing unauthorized traffic. - Providing visibility and control over SaaS applications.
Organizations need visibility and control over data accessed and stored in the cloud, while protecting it and stopping threats in the cloud from a single, cloud-native enforcement point. SSE’s CASB capability provides multi-mode support by enforcing granular policies to monitor and regulate access to sanctioned and unsanctioned cloud services. - Protecting sensitive data in any location.
Organizations require the protection of data that resides in or moves completely outside the scope of the perimeter’s security to be used, shared, and accessed in a secure way. SSE’s DLP capability provides a centralized and unified approach for data protection, by where data classifications are set once and applied in policies across web, cloud, and endpoint.
Source: https://www.skyhighsecurity.com/

