Defeating a brand new Microsoft Office zero-day attack with ZT CDR
Initially, at the time of writing, only five of sixty vendors available marked this file, now known as CVE-2022-30190, as malicious. And as of 30/05/2022, only twenty-two of sixty vendors are flagging this now known file as malicious.
1. Here is a user opening the document:
We have reverse engineered the malware and provided some initial analysis, including running it through the Zero Trust Content Disarm & Reconstruction (ZTCDR) engine. Some initial analysis of this malicious DOCX reveals that it firstly initiates a remote HTML page and pulls this into the document. Details of this are redacted to avoid any opportunity for attackers:
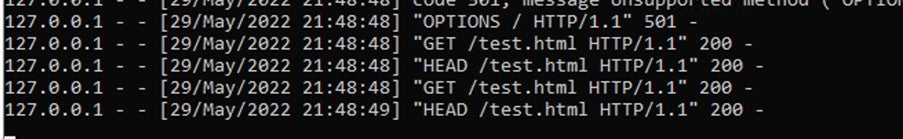
2. This is where the DOCX contacts the server for the HTML file. The web server serves an html page laced with the exploit.
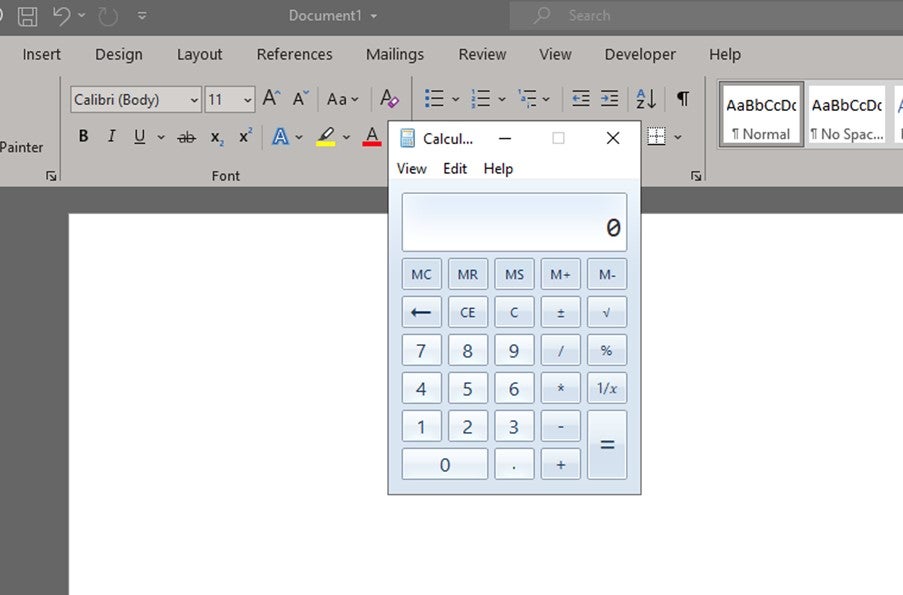
3. The document gets the HTML page and opens it with permissions. This then opens the calculator application via an ms-msdt widget within the HTML page that is served locally. Again, this code has been redacted to avoid opportunity for attackers.
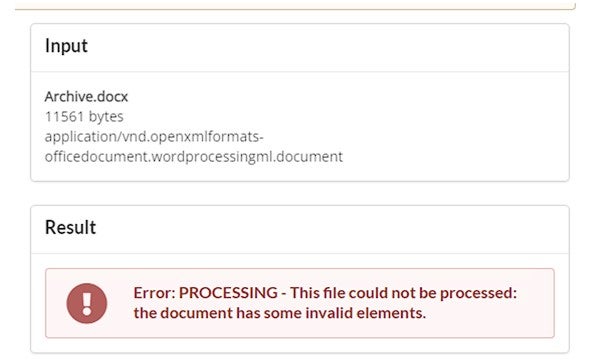
Using the ZT CDR engine, this file with its invalid elements is rightfully blocked due to its malicious behaviour, replicated across all ZT CDR products:
Unlike ZT CDR, many malware prevention solutions can often be deployed in environments where downtime must be minimised and updates must be limited. ZT CDR ensures that uptime requirements can be met without sacrificing on security posture.
This means that all businesses protected by Zero Trust CDR are automatically protected from the new Microsoft Office Zero-day vulnerability, regardless of whether they are running an up-to-date system or not. Forcepoint have not had to send a further update to the core engine to address this vulnerability.
The Zero Trust CDR engine ensures that your business is safe from known and unknown threats, zero-day attacks and malware. Always delivering safe and functional content so users can have utter confidence in the files they are receiving from outside their organisation.
This post was first first published on Forcepoint website by Aaron Mulgrew, Forcepoint Senior Solutions Architect . You can view it by clicking here

