Infographic: Log4Shell Vulnerability Impact by the Numbers
The full scope of risk presented by the Log4Shell vulnerability is something unprecedented, spanning every type of organization across every industry. Hard to find but easy to exploit, Log4Shell immediately places hundreds of millions of Java-based applications, databases, and devices at risk. Remediating this vulnerability has turned out not to be a simple, one-and-done process. Multiple detection methods are required.
Log4Shell Research Study Reveals Enterprise IT Exposure & Response
To shed a unique light on Log4Shell’s impact one month after its disclosure, the Qualys Research Team analyzed anonymized security data from across its global network. This infographic reveals enterprise IT’s exposure and response to Log4Shell across criteria such as the threat landscape, vulnerability trends, remediation trends, and attack patterns.
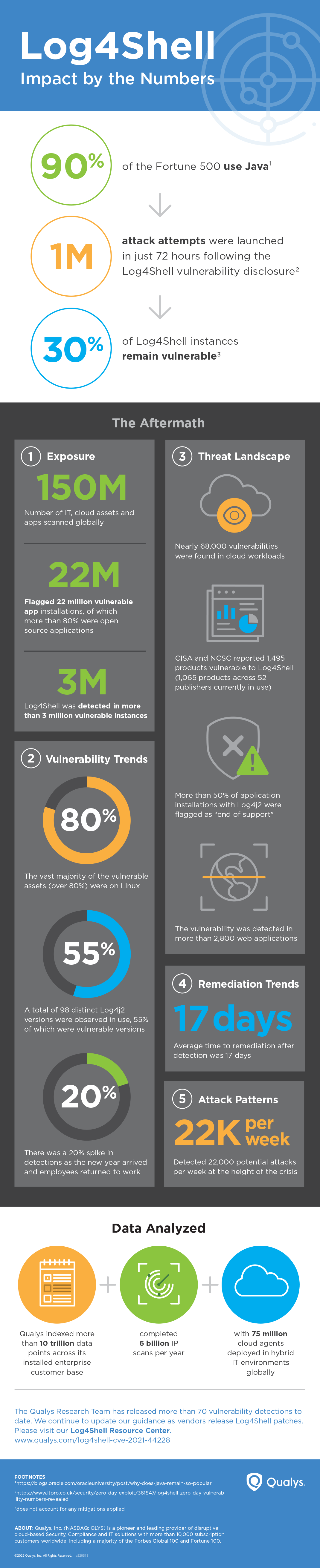
* 30% statistic does not account for any mitigations applied
Post this infographic to your social media by using the share buttons at the bottom of the page.
To add this infographic to your blog or article, copy/paste the following:
Source: Qualys Inc.

This post was first first published on Qualys Security Blog’ website by Qualys Research Team. You can view it by clicking here

