Microsoft & Adobe Patch Tuesday (February 2022) – Microsoft 70 Vulnerabilities with 0 Critical; Adobe 17 Vulnerabilities with 5 Critical
Microsoft Patch Tuesday – February 2022
Microsoft addresses 70 vulnerabilities in their February 2022 Patch Tuesday release. While none of the vulnerabilities in this month’s Microsoft release cycle have been assigned as critical risk, several have been given a High risk rating (CVSSv3.1 score of 7.0 – 8.9). As of this writing, none of this month’s list of vulnerabilities is known to be exploited in the wild.
Microsoft has fixed problems in their software including Remote Code Execution (RCE) vulnerabilities, a former zero-day vulnerability (CVE-2022-21989), privilege escalation security flaws, spoofing bugs, information disclosure, feature bypass, and Denial of Service (DoS) issues.
The advisory covers Microsoft products such as Azure Data Explorer, Kestrel Web Server, Microsoft Edge (Chromium-based), Windows Codecs Library, Microsoft Dynamics, Microsoft Dynamics GP, Microsoft Office and Office Components, Windows Hyper-V Server, SQL Server, Visual Studio Code, and Microsoft Teams.
Important Microsoft Vulnerabilities Patched
CVE-2022-21984 – Windows DNS Server Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10. The Microsoft DNS server has a Remote Code Execution (RCE) flaw that has been fixed with this patch. The server is only affected if dynamic updates are enabled, but this is a relatively common configuration. An attacker might entirely take control of your DNS and execute code with elevated privileges if you have this set up in your environment.
Exploitability Assessment: Exploitation Less Likely.
CVE-2022-21989 – Windows Kernel Elevation of Privilege Vulnerability
This vulnerability has a CVSSv3.1 score of 7.8/10. A low-privilege AppContainer could be used to launch a successful attack. The attacker could get elevated privileges, allowing them to run code or access resources with a greater level of integrity than the AppContainer execution environment.
Exploitability Assessment: Exploitation More Likely.
CVE-2022-22003 – Microsoft Office Graphics Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 7.8/10. This Remote Code Execution (RCE) vulnerability affects Microsoft Office Graphics. For successful exploitation, a user needs to be tricked into running malicious files.
Exploitability Assessment: Exploitation Less Likely.
CVE-2022-22005 – Microsoft SharePoint Server Remote Code Execution (RCE) Vulnerability
This vulnerability has a CVSSv3.1 score of 8.8/10. This Remote Code Execution (RCE) vulnerability affects Microsoft SharePoint Server. An attacker must be authenticated and have page creation access on SharePoint to exploit the flaw.
Exploitability Assessment: Exploitation More Likely.
Adobe Patch Tuesday – February 2022
Adobe released updates to fix 17 CVEs affecting Premiere Rush, Illustrator, Photoshop, AfterEffects, and Creative Cloud Desktop Application. Of these 17 vulnerabilities, five (5) are treated as Critical.
Adobe has released security updates for Illustrator, Photoshop, and AfterEffects for Windows and macOS. These updates address multiple critical, important, and moderate vulnerabilities.
Successful exploitation of these vulnerabilities could lead to application denial-of-service (DoS), arbitrary code execution, privilege escalation, and memory leaks.
Discover and Prioritize Patch Tuesday Vulnerabilities in VMDR
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledge Base (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability:( qid:`91857` OR qid:`91858` OR qid:`91859` OR qid:`91860` OR qid:`91861` OR qid:`91863` OR qid:`91866` OR qid:`110400` OR qid:`110401` OR qid:`110402` OR qid:`376382` ) 
Respond by Patching
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches in one go.
The following QQL will return the missing patches pertaining to this Patch Tuesday:
( qid:`91857` OR qid:`91858` OR qid:`91859` OR qid:`91860` OR qid:`91861` OR qid:`91863` OR qid:`91866` OR qid:`110400` OR qid:`110401` OR qid:`110402` OR qid:`376382` ) 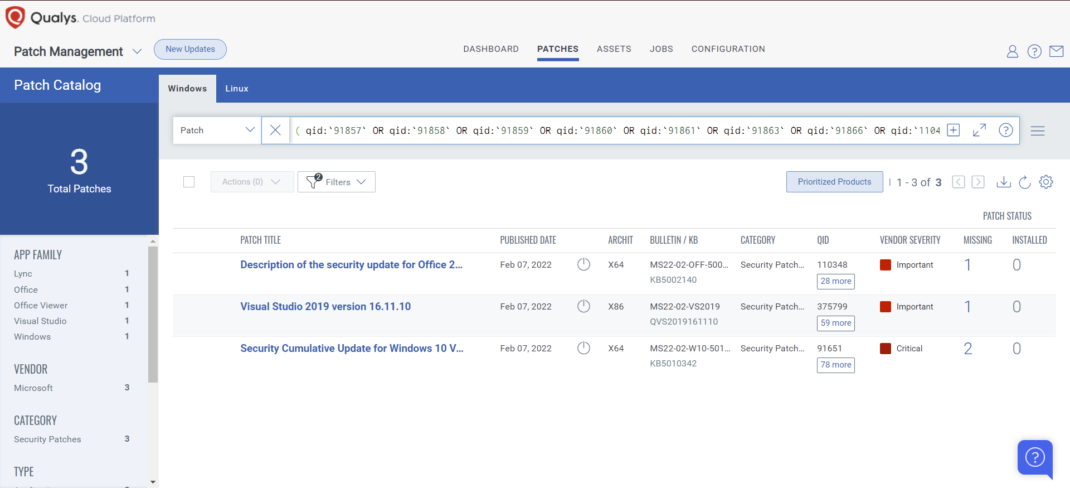
Webinar Series: This Month in Vulnerabilities & Patches

The Qualys Research team is hosting a monthly webinar series to help our existing customers leverage the seamless integration between Qualys VMDR and Patch Management. Combining these two solutions can reduce the median time to remediate critical vulnerabilities.
Register for the webinar: This Month in Vulnerabilities and Patches.
During the webcast, we will discuss this month’s high-impact vulnerabilities, including those that are part of this February 2022 Patch Tuesday alert. We will walk you through the necessary steps to address the key vulnerabilities using Qualys VMDR and Patch Management.
We will cover the significant vulnerabilities published this month:
Join us live or watch on demand!
About Patch Tuesday
Qualys Patch Tuesday QIDs are published as Security Alerts, typically, late in the evening on the day of Patch Tuesday, followed later by the publication of the monthly queries for the Unified Dashboard: 2022 Patch Tuesday (QID Based) Dashboard.
Contributor
Debra M. Fezza Reed, Solutions Architect, Subject Matter Expert Dashboards and Reporting
This post was first first published on Qualys Security Blog’ website by Diksha Ojha. You can view it by clicking here

