Managing CISA Known Exploited Vulnerabilities with Qualys VMDR
CISA recently released a directive recommending urgent and prioritized remediation of actively exploited vulnerabilities. Both government agencies and corporations should heed this advice. This blog outlines how Qualys Vulnerability Management, Detection & Response call be used by any organization to efficiently and effectively respond to this directive.
Situation
Last November, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) released a Binding Operational Directive 22-01 called “Reducing the Significant Risk of Known Exploited Vulnerabilities.” This directive recommends urgent and prioritized remediation of the vulnerabilities that adversaries are actively exploiting. It establishes a CISA-managed catalog of Known Exploited Vulnerabilities that carry significant risk to the federal government and sets requirements for agencies to remediate these vulnerabilities.
This directive requires federal agencies to review and update internal vulnerability management procedures to remediate each vulnerability according to the timelines outlined in CISA’s vulnerability catalog.
Directive Scope
This CISA directive applies to all software and hardware found on federal information systems managed on agency premises or hosted by third parties on an agency’s behalf.
However, CISA strongly recommends that public and private businesses as well as state, local, tribal, and territorial (SLTT) governments prioritize the mitigation of vulnerabilities listed in CISA’s public catalog. This is truly vulnerability management guidance for all organizations to heed.
CISA Catalog of Known Exploited Vulnerabilities
In total, CISA posted a list of 343 Common Vulnerabilities and Exposures (CVEs) that pose the highest risk to federal agencies. CISA’s most recent update was issued on January 21, 2022. The Qualys Research team has mapped all of these CVEs to applicable QIDs (Qualys vulnerability identifiers).
Interested parties can view the complete list of CVEs and the corresponding QIDs here.
Out of these vulnerabilities, Directive 22-01 urges all organizations to reduce their exposure to cyberattacks by prioritizing timely remediation of these as a priority.
CISA has ordered U.S. federal agencies to apply patches as soon as possible. The remediation guidance is grouped into multiple categories by CISA based on attack surface severity and time-to-remediate. The timelines are available in the Catalog for each of the CVEs.
Detect CISA Vulnerabilities Using Qualys VMDR
Qualys helps customers to identify and assess the risk to their organizations’ digital infrastructure, and then to automate remediation. Qualys’ guidance for rapid response to Directive 22-01 follows.
The Qualys Research team has released several remote and authenticated detections (QIDs) for these vulnerabilities. Since the directive includes 343 CVEs, we recommend executing your search based on QQL (Quintly Query Language), as shown here: vulnerabilities.vulnerability.threatIntel.cisaKnownExploitedVulns:”true”
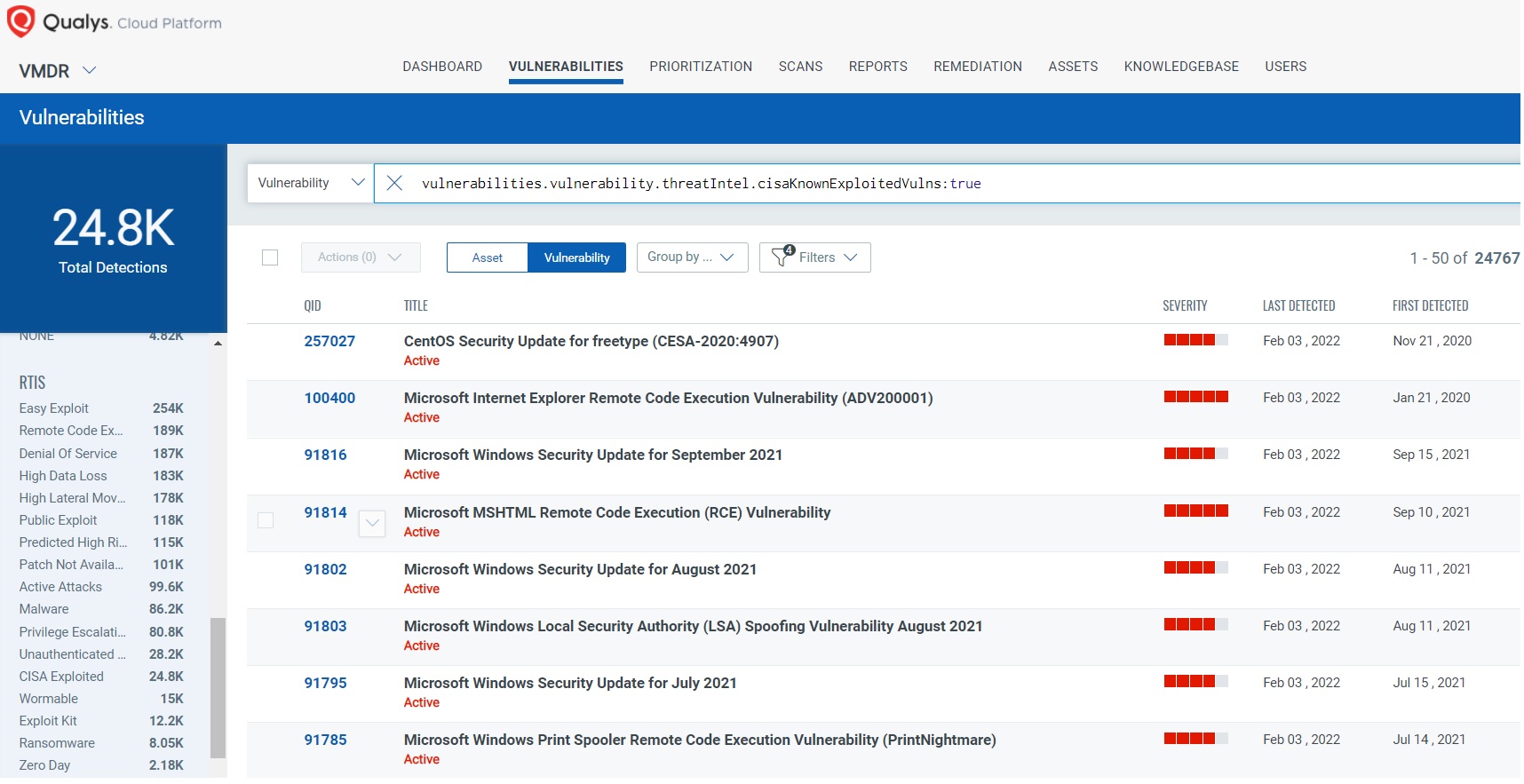
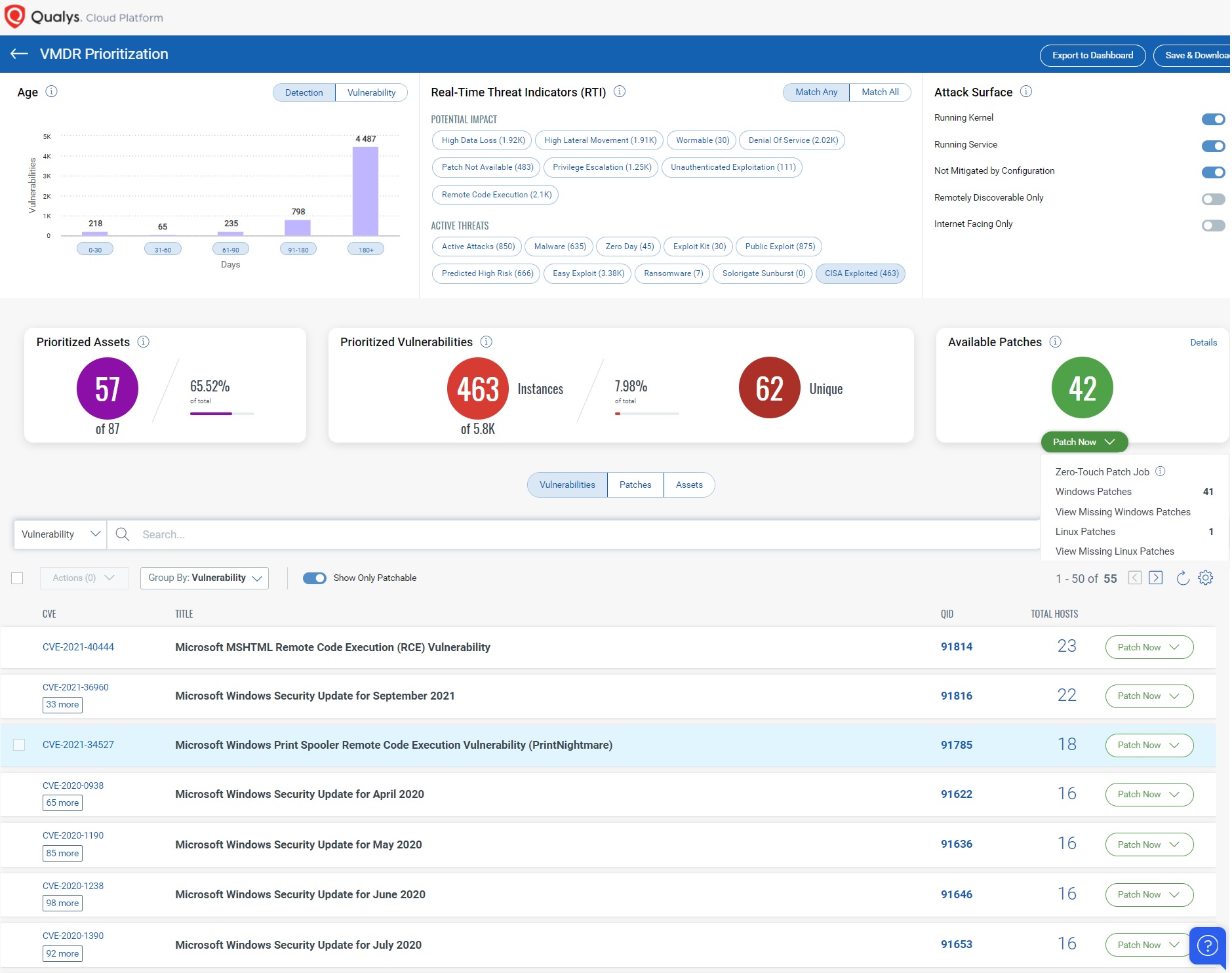
Using Qualys VMDR, you can effectively prioritize those vulnerabilities using VMDR Prioritization. Qualys have introduced new RTI Category as CISA Exploited Vulnerability.
CISA Exploited RTI
CISA maintains a catalog of the top publicly known vulnerabilities being exploited in the wild. Organizations are advised to patch affected systems on a priority basis. This RTI as shown indicates that the vulnerabilities are associated with the CISA catalog, with CVE mappings to respective QIDs.
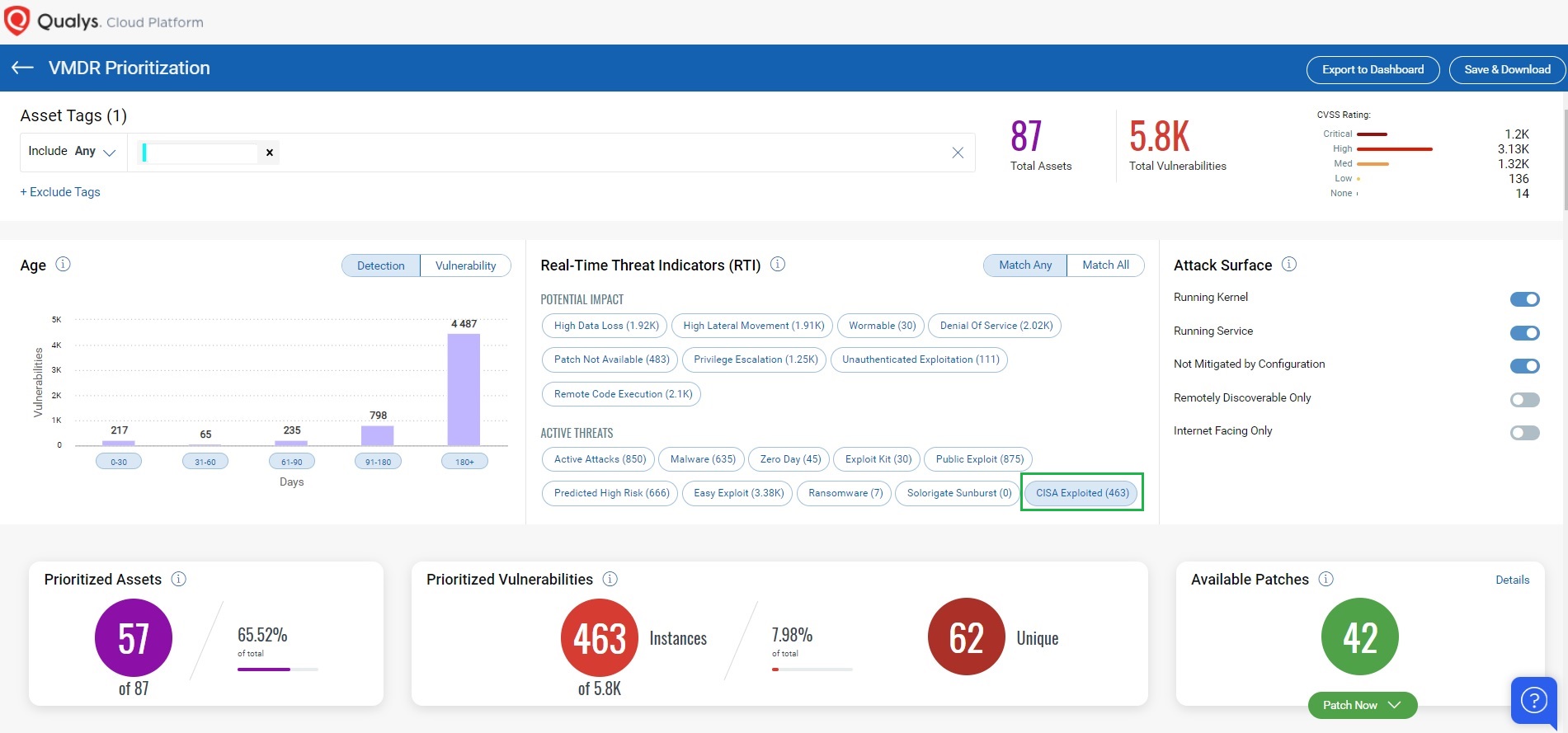
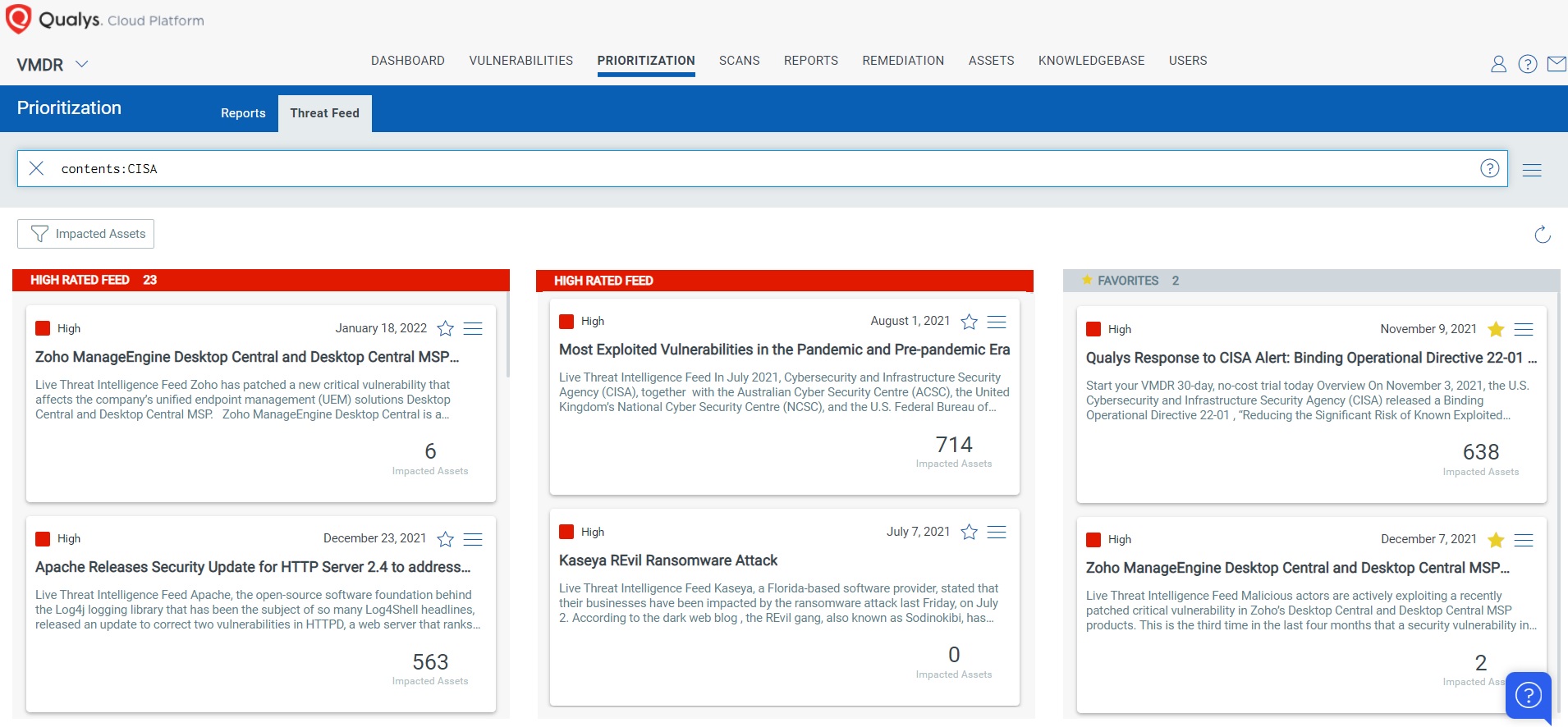
In addition, you can locate a vulnerable host through Qualys Threat Protection by simply clicking on the impacted hosts to effectively identify and track this vulnerability.
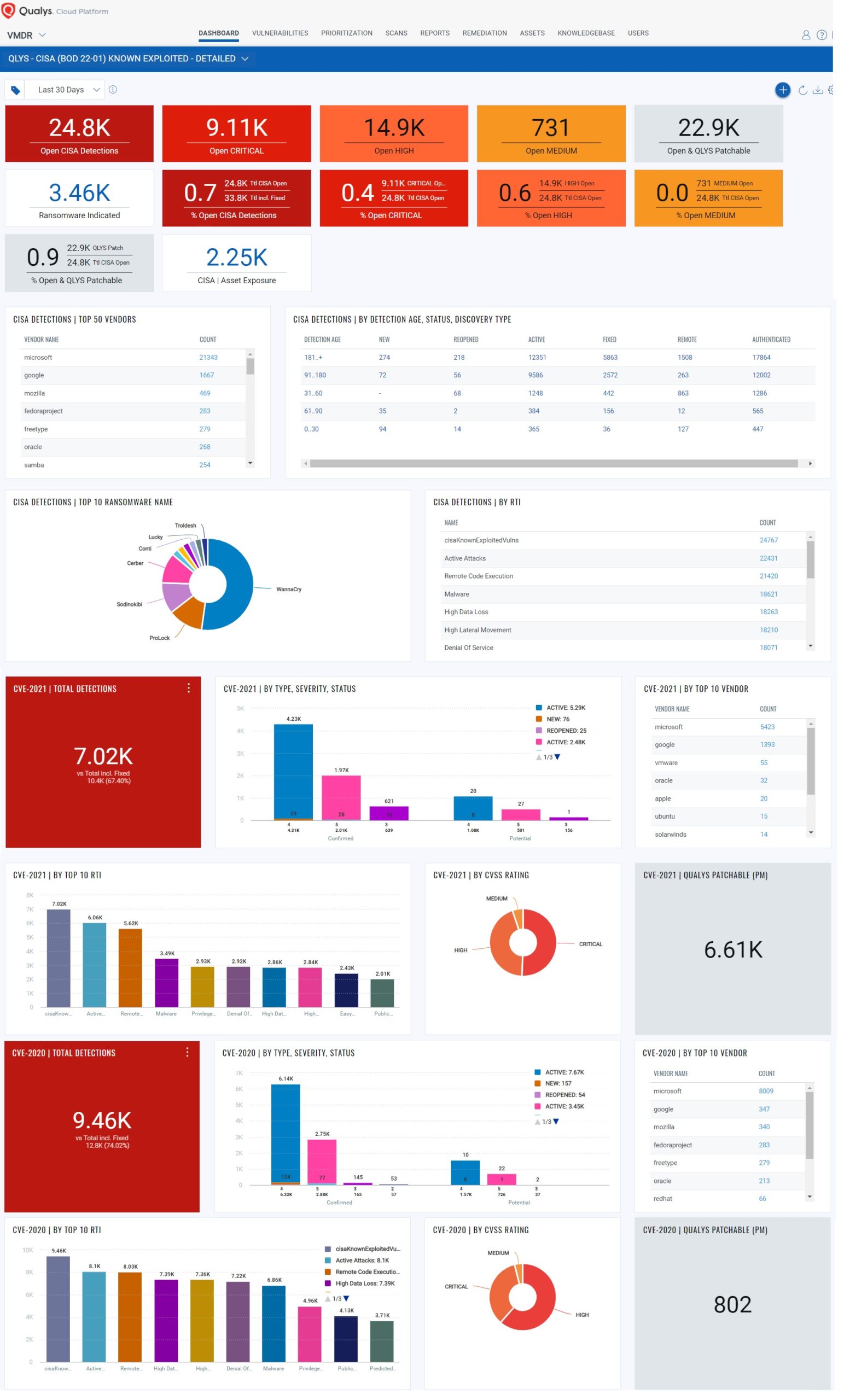
With Qualys Unified Dashboard, you can track your exposure to CISA Known Exploited Vulnerabilities and track your status and overall management in real-time. With trending enabled for dashboard widgets, you can keep track of the status of all vulnerabilities in your environment using the “CISA 2010-21| KNOWN EXPLOITED VULNERABILITIES” Dashboard.
Detailed Operational Dashboard
Remediation
To comply with this directive, federal agencies must remediate critical vulnerabilities by July 21, 2022. Qualys Patch Management can help streamline the remediation of many of these vulnerabilities.
Customers can run a query in the Patch Management app to comply with the directive’s aggressive remediation timelines.
Running this query for specific CVEs will find all required patches and allow quick and efficient deployment of those missing patches to all assets directly from within Qualys Cloud Platform.
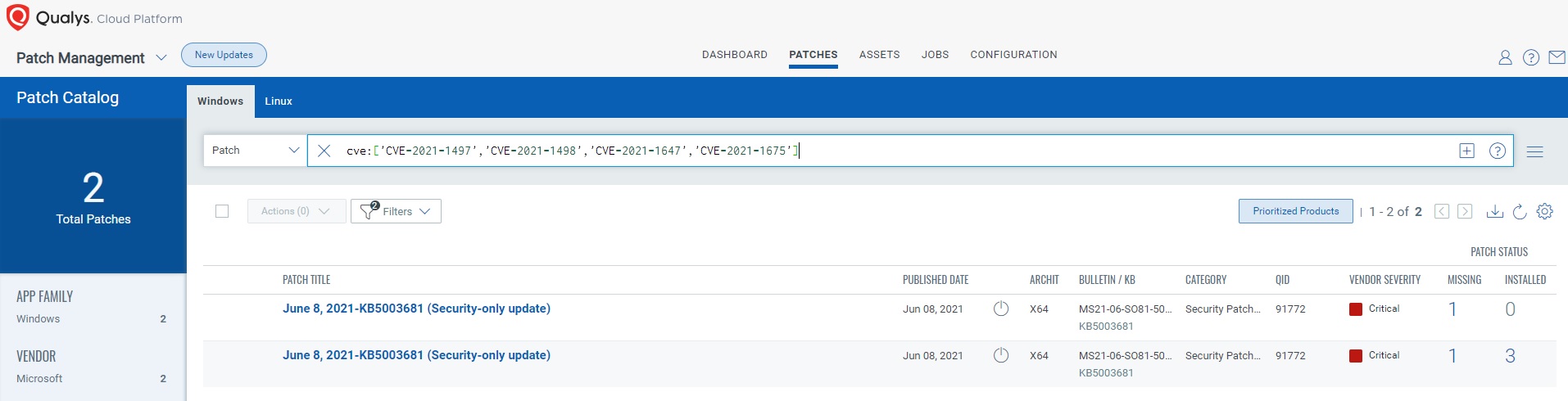
Vulnerabilities can be validated through VMDR and a Patch Job can be configured for vulnerable assets.
Qualys patch content covers many Microsoft, Linux, and third-party applications. However, some of the vulnerabilities introduced by CISA are not currently supported out-of-the-box by Qualys. To remediate those vulnerabilities, Qualys provides the ability to deploy custom patches. The flexibility to customize patch deployment allows customers to patch all of the remaining CVEs in their list.
Federal Enterprises and Agencies Can Act Now
For federal agencies and enterprises, it’s a race against time to remediate these vulnerabilities across their respective environments and achieve compliance with this binding directive. Qualys solutions can help your organization to achieve compliance with this binding directive. Qualys Cloud Platform is FedRAMP authorized, with 107 FedRAMP authorizations to our credit.
Here are a few steps Federal entities can take immediately:
- Run vulnerability assessments against all of your assets by leveraging our various sensors such as Qualys agent, scanners, and more
- Prioritize remediation by due dates
- Identify all vulnerable assets automatically mapped into the threat feed
- Use Qualys Patch Management to apply patches and other configuration changes
- Track remediation progress through our Unified Dashboards
Summary
Understanding just which vulnerabilities exist in your environment is a critical but small part of threat mitigation. Qualys VMDR helps customers discover their exposure, assess threats, assign risk, and remediate threats – all in a single unified solution. Qualys customers rely on the accuracy of Qualys’ threat intelligence to protect their digital environments and stay current with patch guidance. Using Qualys VMDR can help any size organization efficiently respond to CISA Binding Operational Directive 22-01.
Getting Started
Learn how Qualys VMDR provides actionable vulnerability guidance and automates remediation in one solution. Ready to get started? Sign up for a 30-day, no-cost VMDR trial.
This post was first first published on Qualys Security Blog’ website by Ramesh Ramachandran. You can view it by clicking here

