Forcepoint ONE – Built on a Scalable Zero Trust Foundation
Complexity is the main reason. But scalability and performance are also concerns for many. That’s why we’re excited to bring Forcepoint ONE to our customers. Mike Schuricht’s Forcepoint ONE post provides a good overview of how our new cloud platform simplifies security. While reducing complexity is key, we know that can’t come at the expense of scalability or performance.
But in talking to customers, many are early in their Zero Trust journey. Our recent research bears this out—less than one third of customers surveyed have begun implementing a Zero Trust architecture. If it represents the path forward, what’s causing the disconnect?
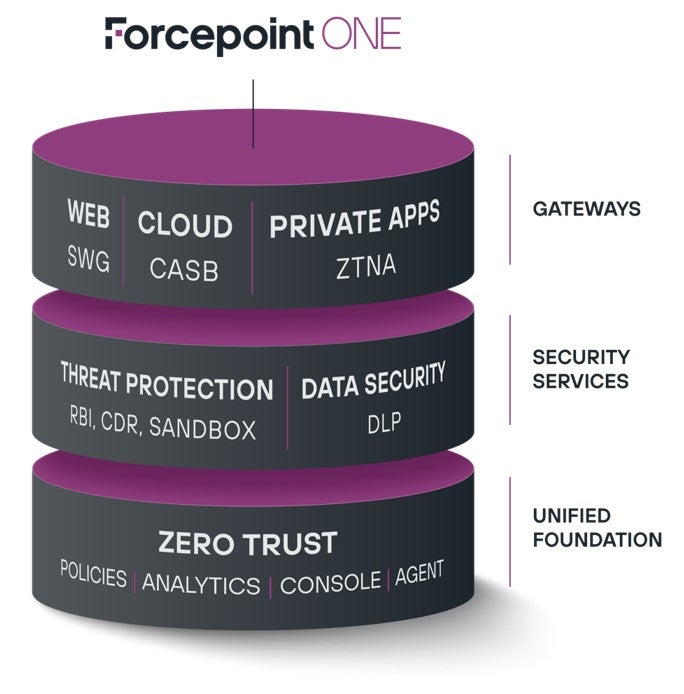
I’ll use this post to talk to the bottom layer of our Forcepoint ONE solution—the unified foundation it’s built on:
Simplicity doesn’t matter without reliability and scalability. Our teams built the platform on an auto-scaling distributed architecture from AWS. Forcepoint ONE is hosted in over 300 points of presence (POPs) on AWS worldwide, including data centers on AWS GovCloud to minimize latency while maximizing uptime. Our auto-scaling architecture means Forcepoint ONE can accommodate surges in user traffic or handle massive data-at-rest scanning jobs while maintaining a 99.99% uptime since 2015. And it can do this across all three of our gateways—SWG, CASB and ZTNA.
Built On a Global Network Hyperscaler
Besides the scalability and performance, our solution allows for simplified enforcement from a single set of policies. Forcepoint ONE allows for configuration, monitoring and reporting from a single management console. It also supports a single set of login policies for controlling access to web, cloud, or private applications based on user location, device type, device posture, user behavior and user group.
Simplified Enforcement from a Single Set of Policies
A Unified Agent Offers Auto-Generated Key and Certificate
And this single set of policies extends to DLP. The platform offers administrators a single set of DLP match patterns for controlling download and upload of sensitive data. In other words, it protects your organization by keeping sensitive data in while keeping hackers out. And it does this seamlessly across all three gateways: web, cloud apps and private apps.
- Unified on-device SWG agent
- Forward proxy CASB function for non-browser applications such as the Outlook for Windows client
- ZTNA for non-web applications such as those using SSH and RDP
True On-Device SWG Architecture Means Better Performance
Our patent-pending technology that uses self-managed keys allows for encrypted communication between the user’s device and the cloud infrastructure. Additionally, this unified agent across Windows and macOS devices performs the following functions:
Sometimes routing traffic up to a cloud proxy is the right approach. But in many other situations, it’s better to enforce web security policies locally on the endpoint. Our on-device SWG allows for smarter traffic routing. Forcepoint ONE SWG traffic is only required to be sent to our AWS infrastructure in two cases 1) when a user attempts to access a new URL that hasn’t been accessed or 2) when a user tries to upload or download a file from an unsanctioned URL associated with a secure SWG content policy. This smart traffic routing improves latency and overall throughput.
Many of our competitors’ solutions require all web traffic to pass through the security provider’s infrastructure for inspection before being forwarded to the destination website. That’s a practice called hairpinning. Hairpinning increases latency and decreases bandwidth, resulting in slower connections your users will notice.
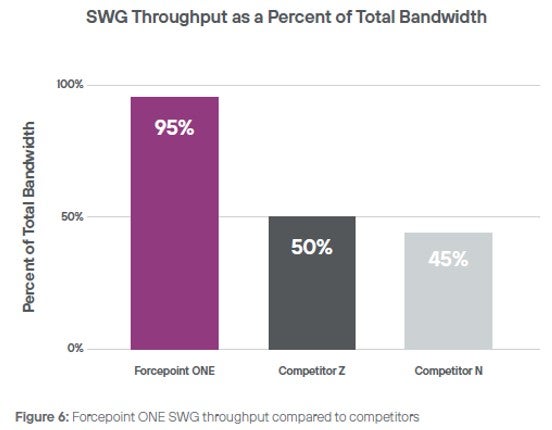
Case in point—Forcepoint ONE recently competed against two other vendors for a SWG deployment for a Fortune 100 company. Forcepoint ONE SWG’s smart routing resulted in 2x the throughput vs. our competitors:
Reach out to your representative to learn more about Forcepoint ONE or to request a demo.
We designed Forcepoint ONE to offer a simple path to a zero trust architecture, and we built it to offer world-class performance, scalability and uptime. We’re proud to offer a robust set of security services via our cloud-based Forcepoint ONE platform, and we’ll be adding more capability throughout 2022 and beyond.
This post was first first published on Forcepoint website by Rees Johnson. You can view it by clicking here

