Developing a Repeatable and Sustainable Security Exploitable Risk Reporting Program
Introduction
The key to creating a practical Reporting Philosophy is/are well-written vulnerability management policies, standards, and guidelines. These are often referred to as a Security, Governance, Risk, and Compliance (SGRC) program and a well-defined risk exception and acceptance (RA) program, referred to hereafter as SGRC/RA.
A successful Vulnerability Management (VM) program begins with aligning the configuration of your Qualys subscription with your current corporate SGRC/RA program(s). Without SGRC/RA alignment, a Reporting program can become ambiguous, thereby leaving the content open to debate between teams, business unit management, security leadership, and internal/external audit teams.
This series will help to sharpen the focus on vulnerability risk detection intelligence [data], thereby empowering you to transform Qualys detection data into:
- actionable,
- measurable,
- repeatable,
- data-driven insights, and,
- informed decisions.
It’s All About the Buckets

The key to managing a successful reporting program is breaking data into consumable buckets before identifying which teams have kudos in order or require additional support to overcome challenges. It’s all a process – a repeatable process that must be groomed and maintained to become a reliable source of truth to those who depend upon it.
Starting a Vulnerability Management program or revamping to improve an existing program can often seem like “trying to boil the ocean”. It can be painfully overwhelming to technicians that are most often are already overwhelmed. This situation does not bode well for the vulnerability management security team member who comes calling with a list of hundreds of critical vulnerabilities that need to be addressed. The secret to your success is to start boiling the ocean one bucket at a time.
On we go …
It All Begins with a Review
The key to building a successful Security Exploitable Risk (Vulnerability) Reporting Program is, to begin with:
- a thoughtful,
- purposeful,
- thorough,
- all-encompassing review of,
the current business processes and their alignment with SGRC/RA defined requirements (new or existing).
Reality Check: It is not uncommon to find security teams starting with their Qualys subscription configuration first, then creating policy, standard, and guideline documents second. This approach to building a VM program is not a standard operating procedure (SOP), nor is it recommended best practice. Knowingly putting the “cart before the horse” often leads to having to re-build the program, re-build the subscription(s), often several times, until it is “just right”. Unfortunately, the truth is there is no “one-size fits all” or “magic pill” to accomplish this.
You must begin at the beginning.
The exercise of validating your business process alignment to your SGRC/RA program is paramount to configuring your Qualys vulnerability management (VM/VMDR) subscription appropriately. A solid, quality subscription configuration can then be operationalized sustainably. The purpose of the review is ultimately to ensure you “get good data into” your subscription so that the reporting data is accurate and reliable. [“get good data out”]
Qualys Reporting is intended to generate human-readable reports, not exporting every vulnerability from a subscription into a single report; Qualys provides custom APIs for large-scale data exports.
- Business Process Considerations include, but are not limited to:
- What are your reporting goals?
- What report recipient uses cases (i.e., needs, need-to-know, format, grouping) must be satisfied?
- Who needs to see what data?
- When is the data needed?
- Before Maintenance Window, During Maintenance Window, After Maintenance Window?
- Monday Before Patch Tuesday, Wednesday After Patch Tuesday, and then, the last Friday of the month?
- Beginning of the Quarter, Mid-Quarter, End of Quarter?
- Daily, Weekly, Monthly, some combination thereof?
- What time of day? 5 am, 9 am, 12 Noon.
- Is the time zone relevant to delivery?
- Does the recipient prefer a specific date/time format?
- Does the recipient prefer to have data sorted in a specific way?
- Does the recipient prefer a specific format?
- Comma-Separated Value (CSV)
- Extensible Markup Language (XML)
- HTML pages
- Microsoft Document (DOCX)
- Portable Document Format (PDF)
- Web Archive (MHT) — Internet Explorer for Windows only
- Do the PDF reports have to be created with password protection?
How are your business data consumers organized, and do you need to account for this in your reporting deliverables?
| A. Tiered Reporting | C-Level, VP-Level, D-Level, Manager, Technical Remediation-Level |
| B. Lines of Business within your Organization | Corporate, Subsidiary, Divisional, Regional, Branch, Department |
| C. Infrastructure/Network Segments | Internal/External/DMZ, OnPrem/Cloud, Production, Pre-Production, QA, Test, Development, Sandboxed |
| D. Technical/Remediation Team Structure(s) | Hardware/Software/Out-of-Band (i.e., Mgmt Interfaces), Network, Wireless, Internal/External/DMZ, Appliances, Physical, Virtual, Ephemeral, Domains, Servers, Client Endpoints, Operating Systems, Applications, Databases, Internal/External/DMZ, Web Apps, etc. |
- Technology Infrastructure Process Considerations include, but are not limited to:
- Internal IP Range Assignments,
- Owned External IP Ranges,
- Website Index,
- Domain Names,
- Hardware,
- Software,
- Databases,
- Maintenance Windows,
- Scanning Frequencies,
- Black-Out Windows,
- Patching Cadence
- Reboot Cadence,
- Issue/Ticket Tracking Method(s).
- Escalation Management,
- and any API Usage and/or Third-Party Product Integration(s).
- SGRC/RA Requirement Considerations include parameters associated with, but not limited to:
- Regulatory Requirements,
- Minimum Scanning Frequency,
- Detection Focus,
- In-scope Targets,
- Determination of Actionable,
- Assessment of Risk,
- Assignment of Risk,
- Acceptance of Risk,
- Assignment of Remediation Tasks,
- Remediation Tracking (i.e., an external Ticketing system)
- Remediation Compliance Measurements, etc.
- Considerations Associated with New and Existing Qualys Subscription include, but are not limited to:
- Scanning Windows,
- Black-out Windows,
- Scanning Frequencies,
- Scan Run Times,
- Option Profiles,
- Search Lists,
- Appliance Usage Rates,
- Batch Reporting,
- Batch Reporting Cadence,
- Ad-hoc Batch Reporting Needs,
- Current Dashboard Use,
- Exception Management,
- Patching Cadence,
- Reboot Cadence,
- and any API Usage and/or Third-Party Product Integration(s).
- Qualys Report Scheduling Considerations include, but are not limited to:
- Scheduled Scan Cadence,
- Recurring Scan Frequencies,
- Scan Run Times,
- Option Profiles,
- Search Lists,
- Recurring Batch Reporting,
- Ad-hoc Batch Reporting,
- Batch Reporting Cadence,
- Current Dashboard Use,
- Exception Management,
- Patching Cadence,
- Reboot Cadence,
- and any API Usage and/or Third-Party Product Integration(s).
Real Life Examples
Each installment in this series will include 2-3 real-life examples that can be applied for an immediate return on investment of time and effort.
EXAMPLE 1: Reporting Toolbox: Schema for Qualys Enterprise Reporting
Aligning Corporate Security Policies and Standards with Selective Data Collection and Multi-Level, Multi-Focus Reporting
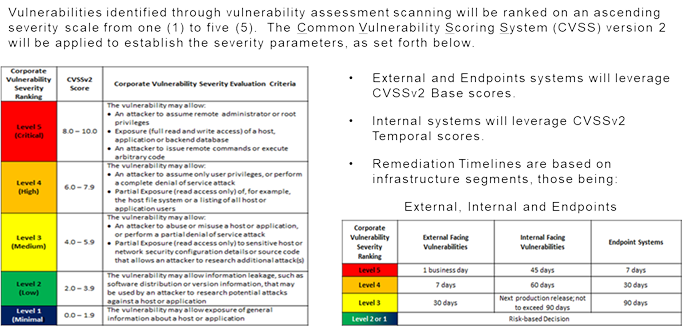
EXAMPLE 2: Trust, but Verify
An effective reporting program enables a comprehensive and focused view of your technology infrastructure to answer the questions associated with validating vulnerability management policy compliance within your estate.
Trust, but Verify – literally means that a responsible person always verifies everything before committing to “X” with “any other person,” even if the “any other person” is presumed to be 100% trustworthy.
Today, Trust, but Verify applies to various routine behavioral and business processes necessary to effectively enforce cyber security fundamentals outlined by your current SGRC/RA program’s Policies, Standards, Procedures, Guidelines, and business processes. One such example is leveraging vulnerability risk detection intelligence [data] to protect your estate by asking the question:
“Are we doing what we say we do?” which is typically followed by: “How well are we doing what we say we do?“
Let’s take a moment to review a sample use case to identify your risk landscape based on your subscription’s available data today.
Reporting Toolbox – Trust, but Verify
I am the only vulnerability management program administrator. I want to be better able to manage my program for an estate containing tens of thousands of assets (physical, virtual, ephemeral), and I need to find a way to identify potential “High Risk” compliance concerns that require immediate attention before I break into my daily routine. In short, a report that should always be empty if we’re doing what we say we do in terms of minimum security baselines.
The Qualys Community article Reporting Toolbox – Trust, but Verify: Focused Search Lists and Queries contains a set of focused search lists and queries. The intent is to produce a portal to quickly spot-check your estate for potentially high-risk compliance indicators. The linked article and bulleted items below include, but are in no way limited to, only these several focus areas.
- enabled default credentials (user-ids and passwords),
- elevated permissions (root),
- enabled default configurations,
- EOL/EOL conditions,
- Network Time Protocol (NTP) synchronization issues,
- the existence of peer-to-peer software, etc.
Producing Trust, but Verify reports or dashboards as an integral component of your normal reporting cycle (daily, weekly, monthly, quarterly, etc.) may prove extremely useful (based on personal experience).
What more can be accomplished today?
Because the responses to the above content can differ significantly from one customer to the next (often one business unit to the next), it is unrealistic to think we could:
- identify each metric, or,
- address every variation of a given metric, or,
- handle every unique customer use case in a blog.
Please permit me to remind everyone about the importance of training and collaboration.
Qualys introduces new feature functionality rapidly and improving your product application knowledge and expertise is paramount to longitudinal success for the Program and for yourself.
Qualys offers Instructor-Led Training (ILT), Self-Paced Training (SP), Video Series (VS), and annual security conferences free of charge. I cannot emphasize enough the importance of training, and training often.
Collaboration is facilitated and nurtured,
- by your participation in the Qualys Community;
- by your interactions and communications with your Technical Account Manager (TAM);
- by your interactions and communications with Qualys Customer Service, Support, Technical Support;
- and through scheduled TAM facilitated engagements with Qualys Solution Architects and Subject Matter Experts.
An Open Invitation to Join Our Digital Transformation!
Let’s suppose you are now interested in exploring more about Reporting, Qualys Unified Dashboards, and the Qualys Cloud Platform product offerings. My first recommendation to you is to visit and join our online Qualys Community, which houses many valuable resources and peer communications about the Qualys Cloud Platform.
The three (3) links below contain curated reporting and dashboard content available in the online Qualys Community:
- Reporting Toolbox: Reporting Best Practices FAQ
- Dashboard & Reporting – Start Here
- Dashboard Toolbox: Dashboarding Best Practices FAQ
Qualys Community
Qualys Training
Qualys Training Resources is/are available in multiple delivery methods: Instructor-Led Training (ILT), Self-Paced Training (SP), and Video Series (VS).
Qualys Application Resources
VM Program Development Resources:
Technology Infrastructure Resources:
SGRC/RA resources:
Subscription Sensor Resources:
Qualys also offers a wealth of information via our product news and events, application-specific and industry-driven webinars, and social media feeds. Below are links to those resources.
This post was first first published on Qualys Security Blog’ website by Debra M. Fezza Reed. You can view it by clicking here

