Microsoft & Adobe Patch Tuesday (November 2021) – Microsoft 55 Vulnerabilities with 6 Critical, 6 Zero-Days. Adobe 4 Vulnerabilities
Microsoft Patch Tuesday – November 2021
Microsoft patched 55 vulnerabilities in their November 2021 Patch Tuesday release, of which six are rated as critical severity and six were previously reported as zero-days.
Critical Microsoft Vulnerabilities Patched
CVE-2021-42298 – Microsoft Defender Remote Code Execution Vulnerability
This vulnerability in Microsoft Defender can be exploited using Maliciously crafted files. The remote code execution vulnerability will be triggered when the malicious file is opened by a user or scanned automatically via an outdated version of Microsoft Defender
CVE-2021-42279 – Chakra Scripting Engine Memory Corruption Vulnerability
The Buffer Overflow vulnerability is because of a boundary error issue in Chakra Scripting Engine, which allows remote attackers to execute arbitrary code by initiating the memory corruption.
CVE-2021-42316 – Microsoft Dynamics 365 (on-premises) Remote Code Execution Vulnerability
This vulnerability is a Remote Code Execution bug in on-prem Microsoft Dynamics 365 setups. There are very few public details regarding this vulnerability.
CVE-2021-26443 – Microsoft Virtual Machine Bus (VMBus) Remote Code Execution Vulnerability
The vulnerability exists when a VM Guest fails to handle communication on a VMBus Channel. An authenticated user can exploit this vulnerability by sending a specially crafted communication on the VMBus Channel from the Guest to the Host, allowing the attacker to execute arbitrary code on the Host.
CVE-2021-3711 – OpenSSL: CVE-2021-3711 SM2 Decryption Buffer Overflow
This is a Buffer Overflow vulnerability in OpenSSL software which is embedded in Microsoft Visual Studio. The vulnerability was introduced due to a miscalculation in the buffer size in OpenSSL’s SM2 function. An attacker can exploit this vulnerability to crash the application and potentially execute arbitrary code with the user’s permission to run the application.
CVE-2021-38666 – Remote Desktop Client Remote Code Execution Vulnerability
This vulnerability in Remote Desktop Clients can be exploited by an attacker who controls a Remote Desktop Server. The attacker can trick a user into connecting to the compromised/malicious Desktop Server, resulting in remote code execution.
Other High Priority Actively Exploited Vulnerabilities:
CVE-2021-42321 – Microsoft Exchange Server Remote Code Execution Vulnerability
This is an actively exploited vulnerability that affects Microsoft Exchange Server 2019 and Microsoft Exchange Server 2016. This is a post-authentication vulnerability that allows code execution. Microsoft has additional details in a public blog post.
CVE-2021-42292 – Microsoft Excel Security Feature Bypass Vulnerability
The vulnerability in Microsoft Excel can be exploited using a Specially Crafted File, allowing an attacker to execute code. The vulnerability affects both Windows and macOS versions; a patch for the latter has not yet been released.
Following were the four of the six zero-day vulnerabilities:
CVE-2021-43208 – 3D Viewer Remote Code Execution Vulnerability
CVE-2021-43209 – 3D Viewer Remote Code Execution Vulnerability
CVE-2021-38631 – Windows Remote Desktop Protocol (RDP) Information Disclosure Vulnerability
CVE-2021-41371 – Windows Remote Desktop Protocol (RDP) Information Disclosure Vulnerability
Adobe Patch Tuesday – October 2021
Adobe addressed 4 CVEs this Patch Tuesday, and 2 of them are rated as critical severity impacting RoboHelp Server, Adobe, and Adobe Creative Cloud.
Discover Patch Tuesday Vulnerabilities in VMDR
Qualys VMDR automatically detects new Patch Tuesday vulnerabilities using continuous updates to its Knowledge Base (KB).
You can see all your impacted hosts by these vulnerabilities using the following QQL query:
vulnerabilities.vulnerability:(qid:`50116` OR qid:`50117` OR qid:`91831` OR qid:`91832` OR qid:`91833` OR qid:`91834` OR qid:`91835` OR qid:`91836` OR qid:`91837` OR qid:`110394` OR qid:`110395` OR qid:`376026`)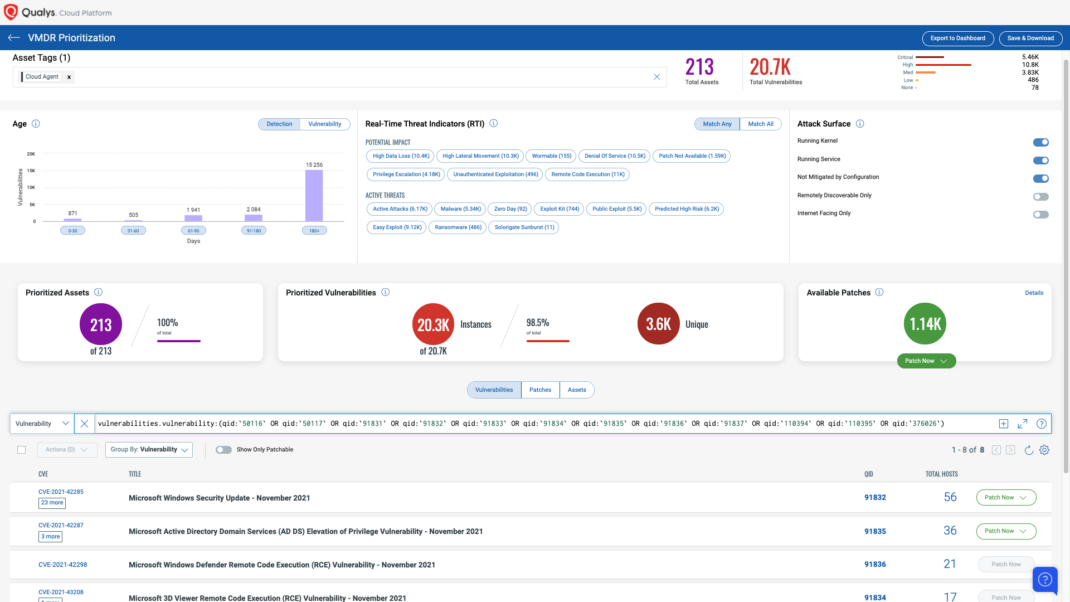
Respond by Patching
VMDR rapidly remediates Windows hosts by deploying the most relevant and applicable per-technology version patches. You can simply select respective QIDs in the Patch Catalog and filter on the “Missing” patches to identify and deploy the applicable, available patches in one go.
The following QQL will return the missing patches pertaining to this Patch Tuesday.
(qid:`50116` OR qid:`50117` OR qid:`91831` OR qid:`91832` OR qid:`91833` OR qid:`91834` OR qid:`91835` OR qid:`91836` OR qid:`91837` OR qid:`110394` OR qid:`110395` OR qid:`376026`)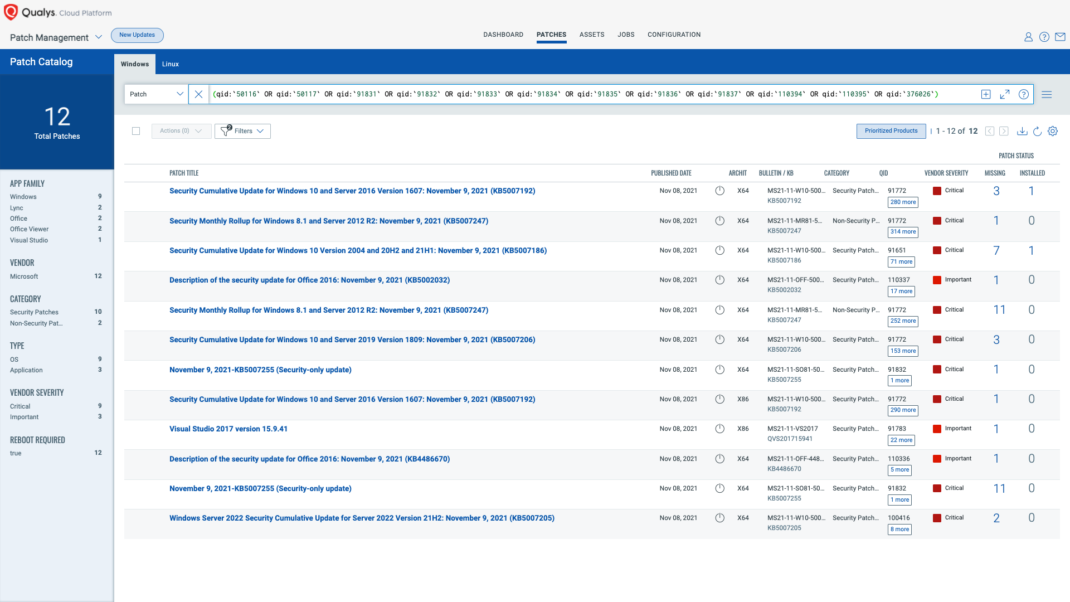
Patch Tuesday Dashboard
The current updated Patch Tuesday dashboards are available in Dashboard Toolbox: 2021 Patch Tuesday Dashboard.
Webinar Series: This Month in Vulnerabilities and Patches
To help customers leverage the seamless integration between Qualys VMDR and Patch Management and reduce the median time to remediate critical vulnerabilities, the Qualys Research team is hosting a monthly webinar series This Month in Vulnerabilities and Patches.
We discuss some of the key vulnerabilities disclosed in the past month and how to patch them:
- Microsoft Patch Tuesday, November 2021
- Adobe Patch Tuesday, November 2021
Join us live or watch on demand!

About Patch Tuesday
Patch Tuesday QIDs are published at Security Alerts, typically late in the evening of Patch Tuesday, followed shortly after by PT dashboards.
This post was first first published on Qualys Security Blog’ website by Ankit Malhotra. You can view it by clicking here

