Is There Really Such a Thing as a Low-Paid Ransomware Operator?
Lurking in the shadows of every large-scale attack by organized gangs of cybercriminals, however, there can be found a multitude of smaller actors who do not have access to the latest ransomware samples, the ability to be affiliates in the post-DarkSide RaaS world or the financial clout to tool up at speed.

Introduction
Going by recent headlines you could be forgiven for thinking all ransomware operators are raking in millions of ill-gotten dollars each year from their nefarious activities.
By getting creative and looking out for the latest malware and builder leaks they can be just as devastating to their victims and, in this blog, we will track the criminal career of one such actor as they evolve from homemade ransomware to utilizing major ransomware through the use of publicly leaked builders.
So what is a low-paid ransomware operator to do in such circumstances?
With the income of such tactics sometimes running into the millions of dollars, such as with the Netwalker ransomware that generated 25 million USD between 1 March and 27 July 2020, we speculate that much of those ill-gotten funds are subsequently used to build and maintain arsenals of offensive cyber tools, allowing the most successful cybercriminals to stay one step ahead of the chasing pack
The Rich Get Richer
For years, the McAfee Enterprise Advanced Threat Research (ATR) team has observed the proliferation of ransomware and the birth and (apparent) death of large organized gangs of operators. The most notorious of these gangs have extorted huge sums of money from their victims, by charging for decryption of data or by holding the data itself to ransom against the threat of publication on their ‘leak’ websites.
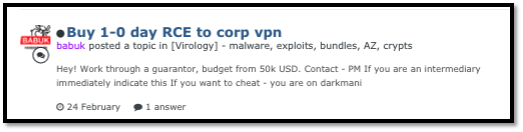
Figure 1: Babuk group looking for a corporate VPN 0-Day
The Lowly-Paid Don’t Necessarily Stay That Way
For smaller ransomware operators, who do not have affiliation with a large group, the technical skills to create their own devastating malware or the financial muscle to buy what they need, the landscape looks rather different.
As seen in the image above, cybercriminals with access to underground forums and deep pockets have the means to pay top dollar for the tools they need to continually generate more income, with this particular Babuk operator offering up 50,000 USD for a 0-day targeting a corporate virtual private network (VPN) which would allow easy access to a new victim.
Away from the gaze of researchers who typically focus on the larger ransomware groups, many individuals and smaller groups are toiling in the background, attempting to evolve their own operations any way they can. One such method we have observed is through the use of leaks, such as the recent online posting of Babuk’s builder and source code.
Unable to build equally effective attack chains, from initial access through to data exfiltration, their opportunities to make illegal profits are far slimmer in comparison to the behemoths of the ransomware market.
Figure 2: Babuk builder public leak on Twitter
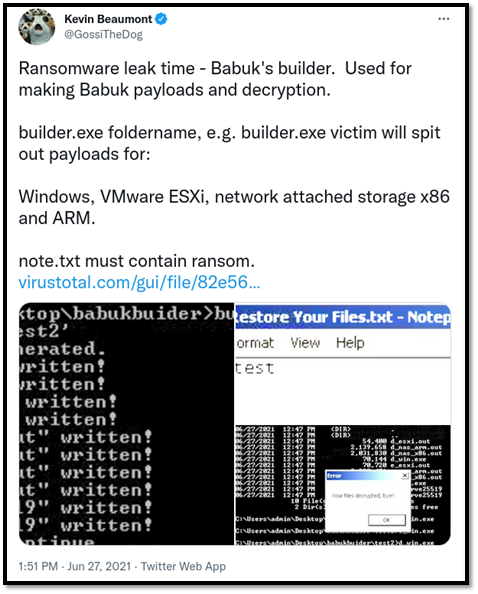
Figure 3: Babuk source code leak on underground forum
Thus, even those operators at the bottom of the ransomware food chain have the opportunity to build on others’ work, to stake their claim on a proportion of the money to be made from data exfiltration and extortion.
McAfee Enterprise ATR has seen two distinct types of cybercriminal taking advantage of leaks such as this. The first group, which we presume to be less tech-savvy, has merely copied and pasted the builder, substituting the Bitcoin address in the ransom note with their own. The second group has gone further, using the source material to iterate their own versions of Babuk, complete with additional features and new packers.
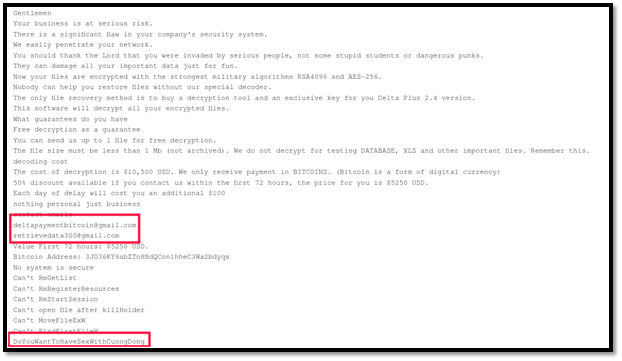
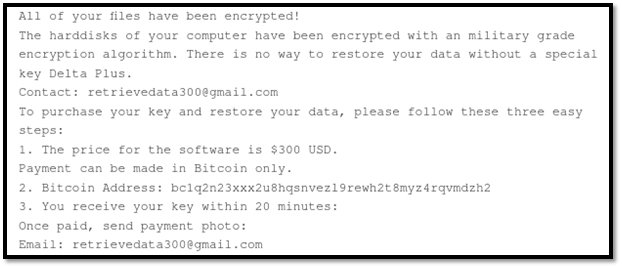
From a quick glance at the sample we can deduce that it is a copied and pasted binary output from Babuk’s builder, with an edited ransom note naming the version “Delta Plus”, two recovery email addresses and a new Bitcoin address for payments:
ATR’s Theory of Evolution
A Yara rule dedicated to Babuk ransomware triggered a new sample uploaded on VirusTotal, which brings us to our ‘lowly-paid’ ransomware actor.
Figure 4: Strings content of “Delta Plus” named version of Babuk
The first email address, retrievedata300@gmail.com, has been used to drop a .NET ransomware mentioning “Delta Plus”:
We’ve seen the two email recovery addresses before – they have been used to deliver random ransomware in the past and, by using them to pivot, we were able to delve into the actor’s resume:
Figure 5: Strings content of .NET ransomware related to previous Delta ransomware activities
| Filename | Setup.exe |
| Compiled Time | Tue Sep 7 17:58:34 2021 |
| FileType | Win32 EXE |
| FileSize | 22.50 KB |
| Sha256 | 94fe0825f26234511b19d6f68999d8598a9c21d3e14953731ea0b5ae4ab93c4d |
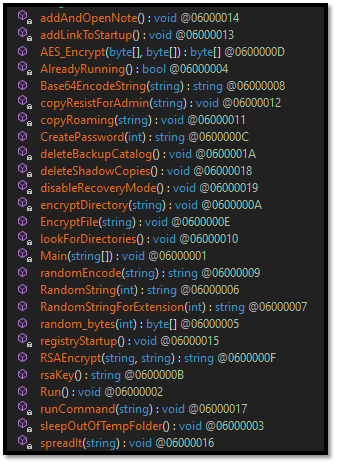
The ransomware is pretty simple to analyze; all mechanisms are declared, and command lines, registry modification, etc., are hardcoded in the binary.
Figure 6: .NET analysis with command line details
By way of contrast, their new project is well developed, easy to use and efficient, no to mention painful to analyze (as it is written in the Golang language) and provides executables for Windows, Linux and network attached storage (NAS) systems.
In fact, the actor’s own ransomware is so poorly developed (no packing, no obfuscation, command lines embedded in the binary and the fact that the .NET language is easy to analyze) that it is hardly surprising they started using the Babuk builder instead.
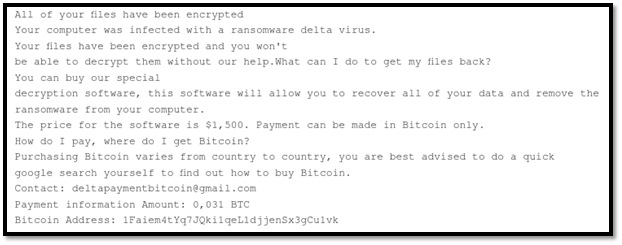
The second email address, deltapaymentbitcoin@gmail.com, has been used to drop an earlier version of the .NET ransomware
| Filename | test2.exe |
| Compiled Time | Mon Aug 30 19:49:54 2021 |
| FileType | Win32 EXE |
| FileSize | 15.50 KB |
| Sha256 | e1c449aa607f70a9677fe23822204817d0ff41ed3047d951d4f34fc9c502f761 |
Tactics, Techniques and Procedures
By checking the relationships between “Delta ransomware”, the Babuk iteration and the domains contacted during process execution, we can observe some domains related to our sample:
Figure 7: Strings content from first version of .NET ransomware
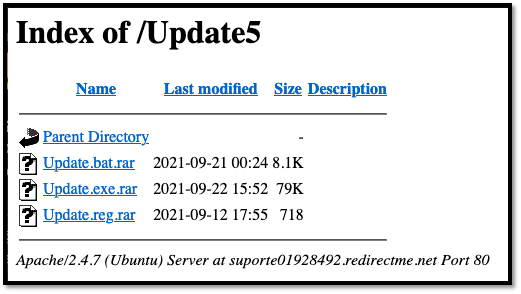
| suporte01928492.redirectme.net |
| suporte20082021.sytes.net |
| 24.152.38.205 |
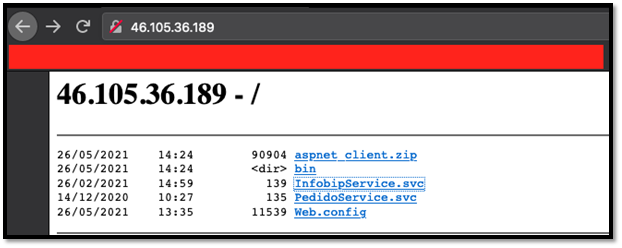
Thanks to a misconfiguration, files hosted on those two domains are accessible through Open Directory (OpenDir), which is a list of direct links to files stored on a server:
Figure 8: Open Directories website where samples are hosted
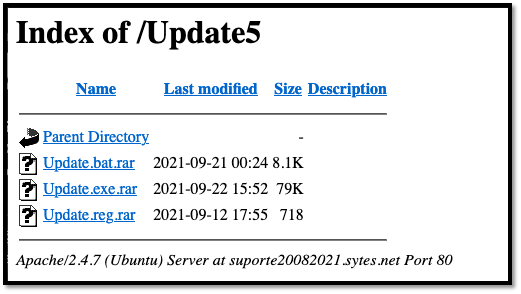
Figure 9: Privilege escalation to get system rights
- bat.rar: A PowerShell script used to perform several operations:
- Try to disable Windows Defender
- Bypass User Account Control (UAC)
- Get system rights via runasti
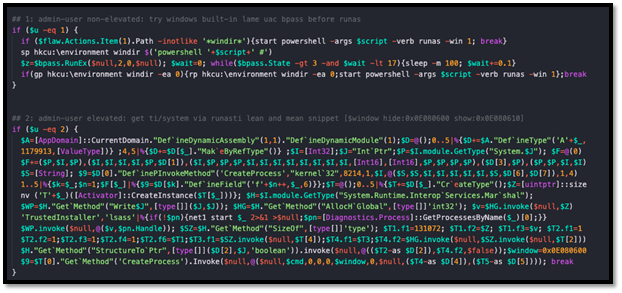
Figure 10: Registry value modifications to disable Windows Defender
- exe.rar: Delta Plus ransomware
- reg.rar: Registry values used to disable Windows Defender
- We’ve found two methods employed by the operator, which we assume to be used for initial access: First, a fake Flash Player installer and, secondly, a fake Anydesk remote tool installer used to drop the ransomware. Our theory about Flash Player initial access has been confirmed by checking the IP that hosts most of the domains:
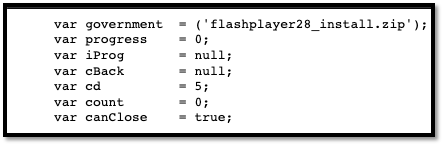
Other domains where files are hosted contain different tools used during attack operations:
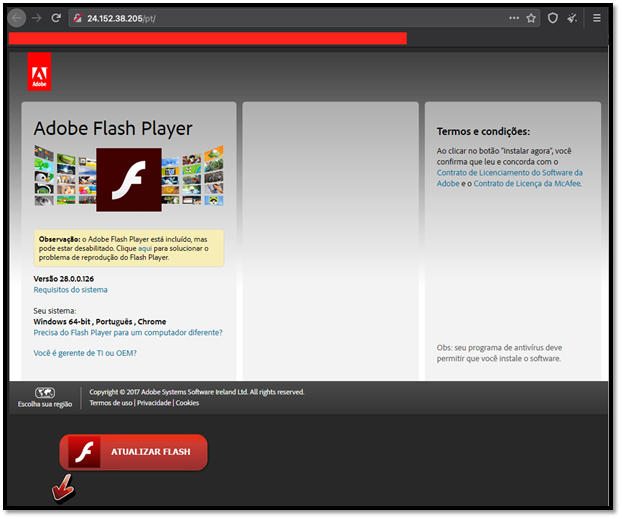
When logging in, the website warns you that your Flash Player version is outdated and tries to download the Fake Flash Player installer:
Figure 11: Fake Flash website used to download fake Flash installer
Figure 12: JavaScript variables used to drop fake Flash Installer
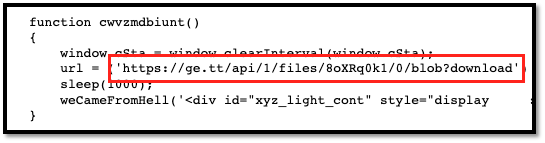
A secondary site appears to have also been utilized in propagating the fake Flash Player, though it is currently offline :
- Portable Executable (PE) files used to launch PowerShell command lines to delete shadow copies, exclude Windows Defender and import registry keys from “Update.reg.rar” to disable Windows defender.
- A PE file used for several purposes: Exfiltrating files from the victim, keylogging, checking if the system has already been held to ransom, getting system information, obtaining user information and to create and stop processes.
Figure 13: JavaScript function to download the fake Flash Installer from another website
Figure 14: Functions and C2 configuration from ransomware sample
- In addition to the above, we also found evidence that this actor tried to leverage another ransomware builder leak, Chaos ransomware.
Infrastructure
The majority of domains used by this actor are hosted on the same IP: “24.152.38.205” (AS 270564 / MASTER DA WEB DATACENTER LTDA).
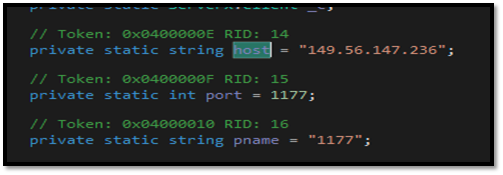
(host used for extraction)
By looking at this IP with Shodan, we can get a dedicated hash for the SSH service, plus fingerprints to use on this IP, and then find other IPs used by the actor during their operations.
But as we saw by “analyzing” the extraction tool used by the actor, another IP is mentioned: “149.56147.236” (AS 16276 / OVH SAS). On this IP, some ports are open, such as FTP (probably used to store exfiltrated data), SSH, etc.
At least 174 IPs are sharing the same SSH pattern (key, fingerprint, etc.); all findings are available in the IOCs section.
By using this hash, we were able to map the infrastructure by looking for other IPs sharing the same SSH key + fingerprintings.
Some IPs are hosting different file types, maybe related to previous campaigns:
Bitcoin Interests
Most of the ransomware samples used by the actor mention different Bitcoin (BTC) addresses which we assume is an effort to obscure their activity.
Figure 15: Open Directory website probably used by the same actor for previous campaigns
From the three samples we researched, we were able to extract the following BTC addresses:
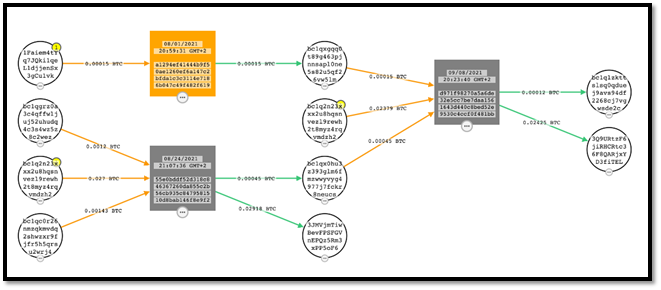
By looking for transactions between those BTC addresses with CipherTrace, we can observe that all the addresses we extracted (see the circle highlighted with a yellow “1” below) from the samples we’ve found are related and eventually point to a single Bitcoin wallet, probably under control of the same threat actor.
Figure 16: Follow the money with CipherTrace
- 3JG36KY6abZTnHBdQCon1hheC3Wa2bdyqs
- 1Faiem4tYq7JQki1qeL1djjenSx3gCu1vk
- bc1q2n23xxx2u8hqsnvezl9rewh2t8myz4rqvmdzh2
While their activity to date suggests a low level of technical skill, the profits of their cybercrime may well prove large enough for them to make another level jump in the future.
Ransomware Isn’t Just About Survival of the Fittest
As we have seen above, our example threat actor has evolved over time, moving from simplistic ransomware and demands in the hundreds of dollars, to toying with at least two builder leaks and ransom amounts in the thousands of dollars range.
In the meantime, such opportunitistic actors will continue to bait their hooks and catch any fish they can as, unlike affiliated ransomware operators, they do not have to follow any rules in return for support (pentest documentation, software, infrastructure, etc.) from the gang’s operators. Thus, they have a free hand to carry out their attacks and, if a victim wants to bite, they don’t care about ethics or who they target.
Even if they stick with copy-pasting builders and crafting ‘stagers’, they will have the means at their disposal to create an efficient attack chain with which to compromise a company, extort money and improve their income to the point of becoming a bigger fish in a small pond, just like the larger RaaS crews.
The good news for everyone else, however, is the fact that global law enforcement isn’t gonna need a bigger boat, as it already casts its nets far and wide.
Detection Mechanisms
Sigma Rules
| – Shadow Copies Deletion Using Operating Systems Utilities: https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/win_shadow_copies_deletion.yml
– Drops Script at Startup Location: https://github.com/joesecurity/sigma-rules/blob/master/rules/dropsscriptatstartuplocation.yml Mitre Att&ck
– Suspicious Svchost Process: https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/win_susp_svchost.yml – File Created with System Process Name: https://github.com/SigmaHQ/sigma/blob/master/rules/windows/file_event/sysmon_creation_system_file.yml – Delete Shadow copy via WMIC: https://github.com/joesecurity/sigma-rules/blob/master/rules/deleteshadowcopyviawmic.yml – System File Execution Location Anomaly: https://github.com/SigmaHQ/sigma/blob/master/rules/windows/process_creation/win_system_exe_anomaly.yml |
– Always Install Elevated Windows Installer: https://github.com/SigmaHQ/sigma/blob/59000b993d6280d9bf063eefdcdf30ea0e83aa5e/rules/windows/process_creation/sysmon_always_install_elevated_windows_installer.yml
description = “Rule to detect Babuk Locker”
Yara Rules
Babuk Ransomware Windows
| rule Ransom_Babuk {
meta: date = “2021-01-19” author = “TS @ McAfee Enterprise ATR” rule_version = “v2” hash = “e10713a4a5f635767dcd54d609bed977” malware_type = “Ransom” malware_family = “Ransom:Win/Babuk”
mitre_attack = “T1027, T1083, T1057, T1082, T1129, T1490, T1543.003” $s1 = {005C0048006F007700200054006F00200052006500730074006F0072006500200059006F00750072002000460069006C00650073002E007400780074} strings: $s2 = “delete shadows /all /quiet” fullword wide // How To Restore Your Files .txt $pattern1 = {006D656D74617300006D65706F63730000736F70686F730000766565616D0000006261636B7570000047785673730000004778426C7200
$pattern3 = {FFB0154000C78584FDFFFFB8154000C78588FDFFFFC0154000C7858CFDFFFFC8154000C78590FDFFFFD0154000C78594FDFFFFD8154 $pattern2 = {004163725363683253766300004163726F6E69734167656E74000000004341534144324457656253766300000043414152435570646174655376630000730071}
$pattern4 ={400010104000181040002010400028104000301040003810400040104000481040005010400058104000601040006C104000781040008 filesize >= 15KB and filesize <= 90KB and condition: } 1 of ($s*) and 3 of ($pattern*) Exfiltration Tool
author = “TS @ McAfee Enterprise ATR” description = “Rule to detect tool used to exfiltrate data from victim systems” hash = “ceb0e01d96f87af0e9b61955792139f8672cf788d506c71da968ca172ebddccd” date = “2021-10-04” strings:
$pattern2 = {B4A6D4DD1BBEA16473940FC2DA103CD64579DD1A7EBDF30638A59E547B136E5AD113835B8294F53B8C3A $pattern1 = {79FA442F5FB140695D7ED6FC6A61F3D52F37F24B2F454960F5D4810C05D7A83D4DD8E6118ABDE2055E4D $pattern4 = {F2A113713CCB049AFE352DB8F99160855125E5A045C9F6AC0DCA0AB615BD34367F2CA5156DCE5CA286CC $pattern3 = {262E476A45A14D4AFA448AF81894459F7296633644F5FD061A647C6EF1BA950FF1ED48436D1BD4976BF8 condition:
} 3 of ($pattern*)
|
http://suporte20082021.sytes.net/Update5/
IOCs
Infrastructure URLs
| http://atualziarsys.serveirc.com/Update4/
http://services5500.sytes.net/Update6/Update.exe.rar http://suporte20082021.sytes.net/Update3/ http://atualziarsys.serveirc.com/update4/update.exe.rar http://atualziarsys.serveirc.com/Update3/ http://suporte01928492.redirectme.net/ http://suporte20082021.sytes.net/update/ http://services5500.sytes.net/update8/update.exe.rar http://suporte01928492.redirectme.net/AppMonitorPlugIn.rar http://suporte20082021.sytes.net/Update5/Update.exe.rar http://services5500.sytes.net/update7/update.exe.rar http://suporte01928492.redirectme.net/Update5/Update.exe.rar http://services5500.sytes.net/Update8/Update.bat.rar http://services5500.sytes.net/Update8/Update.exe.rar http://services5500.sytes.net/Update7/Update.exe.rar http://suporte01092021.myftp.biz/update/ http://suporte01928492.redirectme.net/Update7/Update.exe.rar http://suporte01928492.redirectme.net/Update7/Update.bat.rar http://suporte01092021.myftp.biz/ http://services5500.sytes.net/update6/update.exe.rar http://suporte01928492.redirectme.net/update6/update.exe.rar http://services5500.sytes.net/Update6/Update.bat.rar http://services5500.sytes.net/ http://suporte01928492.redirectme.net/update5/update.exe.rar http://atualziarsys.serveirc.com/Update3 http://suporte01928492.redirectme.net/Update6/Update.exe.rar http://24.152.38.205/pt/flashplayer28_install.zip http://atualziarsys.serveirc.com/update3/update.reg.rar http://atualziarsys.serveirc.com/ http://suporte01928492.redirectme.net/Update7 http://suporte01928492.redirectme.net/update7/update.exe.rar http://atualziarsys.serveirc.com/update3/mylink.vbs.rar http://suporte01928492.redirectme.net/appmonitorplugin.rar http://atualziarsys.serveirc.com/Update4/Update.exe.rar http://suporte20082021.sytes.net/ http://atualziarsys.serveirc.com/update3/update.exe.rar http://atualziarsys.serveirc.com/Update4/Update.exe2.rar http://suporte20082021.sytes.net/update3/update.exe.rar http://suporte20082021.sytes.net/Update5/Update.reg.rar http://suporte20082021.sytes.net/Update3/Update.exe.rar http://atualziarsys.serveirc.com/Update4 http://atualziarsys.serveirc.com/Update4/Update.exe2.rar/ http://suporte01092021.myftp.biz/update http://suporte01092021.myftp.biz/update/WindowsUpdate2.rar http://atualziarsys.serveirc.com/Update3/Update.exe.rar http://atualziarsys.serveirc.com/Update3/Update.reg.rar/ http://suporte01092021.myftp.biz/update/WindowsUpdate2.rar/ http://suporte20082021.sytes.net/Update3/Update.exe.rar/ http://atualziarsys.serveirc.com/Update3/mylink.vbs.rar http://atualziarsys.serveirc.com/Update4/Update.exe.rar/ http://atualziarsys.serveirc.com/update3 http://atualziarsys.serveirc.com/update4 http://suporte01928492.redirectme.net/AppMonitorPlugIn.rar/ http://suporte01092021.myftp.biz/update/Update.rar http://suporte01092021.myftp.biz/update5/update.exe.rar http://suporte20082021.sytes.net/update5/update.exe.rar http://suporte01092021.myftp.biz/update/windowsupdate2.rar http://atualziarsys.serveirc.com/update4/update.exe2.rar http://suporte20082021.sytes.net/update/windowsupdate2.rar http://suporte20082021.sytes.net/update2/update.exe.rar http://atualziarsys.serveirc.com/favicon.ico http://atualziarsys.serveirc.com/Update4/mylink.vbs.rar http://24.152.38.205/1.exe http://24.152.38.205/1.rar http://suporte20082021.sytes.net/update/WindowsUpdate2.rar http://appmonitorplugin.sytes.net/appmonitorplugin.rar http://suporte20082021.sytes.net/appmonitorplugin.rar http://appmonitorplugin.sytes.net/ http://suportmicrowin.sytes.net/ http://suportmicrowin.sytes.net/appmonitorplugin.rar http://appmonitorplugin.sytes.net/AppMonitorPlugIn.rar http://suportmicrowin.sytes.net/AppMonitorPlugIn.rar |
http://24.152.38.205/pt/setup.zip
suporte01092021.myftp.biz
Infrastructure Domains
| services5500.sytes.net
atualziarsys.serveirc.com suporte01928492.redirectme.net suporte20082021.sytes.net appmonitorplugin.sytes.net suportmicrowin.sytes.net Infrastructure IPs
149.56.38.168 54.38.122.66 24.152.36.48 149.56.38.170 66.70.209.174 66.70.170.191 51.79.107.245 142.44.129.70 178.33.108.239 46.105.36.189 24.152.37.115 54.39.193.37 24.152.36.58 144.217.139.134 51.222.97.177 51.38.19.201 144.217.45.69 51.222.53.150 144.217.199.24 87.98.137.173 144.217.29.23 24.152.37.19 54.39.163.60 198.50.246.8 24.152.36.30 54.39.84.55 24.152.37.96 46.105.38.67 178.33.107.134 51.79.63.229 54.39.163.58 164.132.77.246 51.161.120.193 149.56.113.76 176.31.37.238 24.152.36.210 24.152.36.83 176.31.37.237 51.161.76.193 24.152.37.8 137.74.246.224 24.152.36.117 51.79.44.49 51.79.107.134 51.79.124.129 51.222.173.152 51.222.173.148 51.79.107.242 54.36.82.187 144.217.117.172 54.36.82.177 54.39.152.91 54.39.221.163 142.44.146.178 149.56.38.173 51.79.44.57 51.38.19.198 24.152.36.46 198.50.246.11 51.79.44.59 24.152.36.239 24.152.36.35 66.70.209.169 144.217.17.186 54.39.84.50 24.152.36.158 144.217.45.68 51.38.19.200 54.38.164.134 144.217.111.5 51.79.124.130 87.98.171.7 51.255.119.19 66.70.148.142 54.39.239.81 66.70.209.168 51.38.192.225 24.152.36.98 144.217.189.108 144.217.117.10 51.255.55.134 66.70.148.136 66.70.148.137 54.39.137.73 51.79.107.254 54.36.146.230 144.217.61.176 54.39.84.52 149.56.147.236 24.152.36.150 54.39.163.57 51.38.19.196 149.56.68.191 46.105.36.133 158.69.99.10 24.152.36.107 54.39.247.244 51.255.55.136 158.69.99.15 149.56.147.204 149.56.147.205 144.217.32.24 54.39.84.53 144.217.32.213 144.217.233.98 79.137.115.160 24.152.36.195 51.79.44.56 144.217.139.13 142.44.146.190 198.50.246.14 54.36.82.180 24.152.36.176 137.74.246.223 51.161.76.196 51.79.107.250 66.70.209.170 198.50.246.12 51.222.97.189 66.70.148.139 144.217.17.185 54.39.84.49 144.217.45.67 142.44.129.73 144.217.45.64 24.152.36.28 198.27.105.3 24.152.37.39 198.50.204.38 51.38.8.75 51.161.76.197 54.39.221.11 91.134.217.71 54.38.122.64 144.217.32.26 24.152.36.100 54.36.82.188 198.50.246.13 66.70.209.171 54.39.84.25 54.39.8.92 51.38.218.215 54.39.247.228 51.38.19.205 24.152.36.104 24.152.36.103 54.39.152.202 51.79.44.43 24.152.36.25 66.70.134.218 178.32.243.48 149.56.113.79 66.70.173.72 144.217.45.66 54.38.225.81 176.31.37.239 24.152.37.189 158.69.4.173 198.50.246.15 54.36.146.129 51.79.105.91 51.222.102.30 51.222.173.151 51.79.9.91 51.222.173.142 51.79.107.124 149.56.85.98 144.217.17.187 144.217.158.195 51.79.107.244 192.95.20.74 24.152.36.178 |
51.79.117.250
ae6020a06d2a95cbe91b439f4433e87d198547dec629ab0900ccfe17e729cff1
Ransomware Hashes
| 106118444e0a7405c13531f8cd70191f36356581d58789dfc5df3da7ba0f9223
e1c449aa607f70a9677fe23822204817d0ff41ed3047d951d4f34fc9c502f761 63b6a51be736d253e26011f19bd16006d7093839b345363ef238eafcfe5e7e85 c3776649d9c0006caba5e654fa26d3f2c603e14463443ad4a5a08e4cf6a81994 c8d97269690d3b043fd6a47725a61c00b57e3ad8511430a0c6254f32d05f76d6 94fe0825f26234511b19d6f68999d8598a9c21d3e14953731ea0b5ae4ab93c4d 98a3ef26b346c4f47e5dfdba4e3e26d1ef6a4f15969f83272b918f53d456d099 67bc70d4141d3f6aaf8f17963d56df5cee3727a81bc54407e90fdf1a6dc8fe2a |
c3c306b2d51e7e4f963a6b1905b564ba0114c8ae7e4bb4656c49d358c0f2b169
bc1q2n23xxx2u8hqsnvezl9rewh2t8myz4rqvmdzh2
Bitcoin Addresses
| 3JG36KY6abZTnHBdQCon1hheC3Wa2bdyqs
1Faiem4tYq7JQki1qeL1djjenSx3gCu1vk PDB
PowerShell Script
|
Exfiltration Tool
| ceb0e01d96f87af0e9b61955792139f8672cf788d506c71da968ca172ebddccd
c3323fbd0d075bc376869b0ee26be5c5f2cd4e53c5efca8ecb565afa8828fb53 Fake Anydesk Installer
Fake Flash Player installer
The post Is There Really Such a Thing as a Low-Paid Ransomware Operator? appeared first on McAfee Blogs.
This post was first first published on McAfee Enterprise – McAfee Blogs’s website by Thibault Seret. You can view it by clicking here |

