Network Security: The Invisible Defender
The shift to remote work and the increasing complexity of the technology landscape – with most organizations now running hybrid infrastructures with multi-cloud deployments – we are entering the era of “not if, but when” an attack occurs. According to a recent Forrester report, the leading cause of confirmed breaches was due to external attacks. “Of these cases, 38% were caused by a web application attack, 32% by malware, and 30% by exploiting a lost or stolen asset.”
In 2020, we saw a stark increase in the velocity of attacks – more attacks happened more often. Increased automation, the rise of organized eCrime, and the ease of demanding ransomware payments thanks to the anonymity of cryptocurrency has set fire to the technology landscape. Gone are the days of trusting payment services like PayPal and Stripe to crack down to protect corporations and consumers alike. Cryptocurrency is decentralized and unregulated – meaning we are entering the era of a digital economy that is the equivalent to the Wild West (at least until regulation comes).
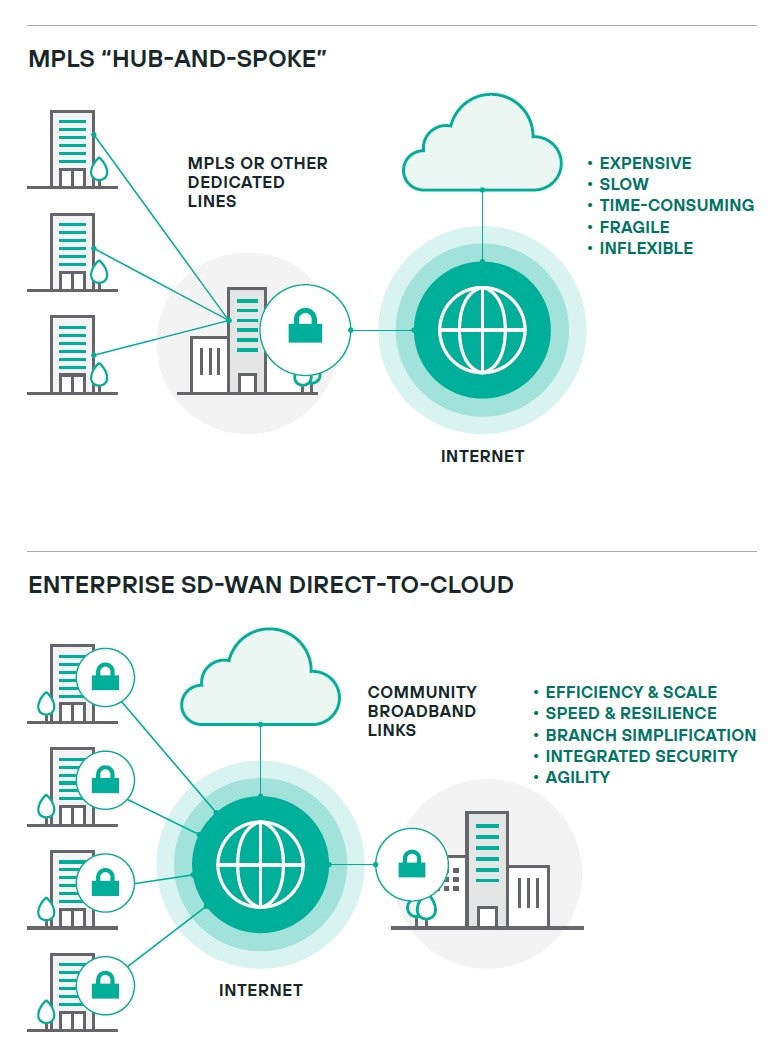
Successful next-gen firewall implementations can enhance your team’s ability to block and tackle incoming attacks by leveraging Zero Trust controls and advanced automation. Our built-in Secure SD-WAN solution opens the doors for network administrators to easily replace outdated MPLS connections, spin up complex network topologies with just a few clicks, and even build a zero-knowledge distributed architecture with our secure SD-WAN Broker. Our goal is to provide the best tools designed for administrators do their job not just effectively, but efficiently, because we recognize that when an attack is detected – every second counts. When you add in advanced capabilities, like our Endpoint Context Agent (ECA), you can gain valuable insights into granular details about every device on your network as well as enforce policies to prevent unauthorized user actions, like those that violate privacy regulations.
Though network security isn’t the most popular security topic, there is no denying that it is your first line of defense against any external threat. After all, not securing your edge and only focusing on internal threats is a lot like building your house to be highly secure – with locks, cameras, and secret codes – only to leave all of your doors and windows open with no one home. Many times, being an easy target is all it takes to catch attention, from something as mundane as randomized port scans. Though crime is also experiencing its own digital revolution, it’s important to understand that the criminals are still largely opportunistic and, like all humans, looking to exert the smallest amount of energy with the largest return on investment.
Are your workers constantly on the go, using their mobile devices to access your sensitive networks? Simply spin up a secure VPN for your that is accessible on mobile devices so your workforce can take the advanced firewall protection with them anywhere.
Though the only constant in cyber security is change, one thing is certain: leaders are continuing to increase investments in securing their edge because it is a key element to a resilient cyber defense. It is time to implement edge protection that is secure, yet flexible – solutions that help upgrade your teams from the dense chainlink armor of the Middle Ages to the lightweight fabrics of today that are just as effective. Arm your organization with the leading network security solutions from Forcepoint and join us in stopping the bad and freeing the good.
This post was first first published on Forcepoint website by Cat Allen. You can view it by clicking here

