New Research – Are headlines hype or are U.S. federal cybersecurity threats growing?
In the latest Ponemon Institute research, “Cybersecurity Risks in the Federal Government,” sponsored by Forcepoint, Ponemon took a deeper look at the state of U.S. cybersecurity to determine whether the news headlines are simply hype or is U.S. cybersecurity really a growing problem? Most importantly, what can we do to fix this?
Cybersecurity Risks in the Federal Government
The research confirmed that U.S. cybersecurity attacks are, in fact, a growing problem. In the past 12 months, both the volume and severity of cybersecurity incidents have increased.
The Ponemon Institute surveyed 615 IT and IT security practitioners across the United States federal government, to understand the state of security across government, identify security gaps in achieving a strong security posture and to determine steps the federal government is taking to close these gaps.
- 63 percent of respondents say the volume of cybersecurity incidents is increasing.
- 65 percent of respondents say the severity of these incidents is getting worse.
- 54 percent of respondents say their agencies had a cybersecurity incident that resulted in a significant disruption to their agencies’ IT and agency processes in the past two years.
- 61 percent of respondents say that in order to mitigate security risks created by remote workers it is important to understand human behavior.
Beyond that, only 15% of respondents reported that their IT security teams could detect a security incident in less than 40 days. Other agencies reported a detection time of anywhere from 41 days to more than 200. Also concerning is the fact that most agencies rate their ability to prevent and detect a cyberattack as very low. Only 34 percent of respondents rate the ability to prevent and quickly detect a cyberattack as high or very high.
According to the survey:
Despite all of the investment and cybersecurity initiatives the U.S government have focused on, the adversaries appear to be winning. In the current environment, agencies must rethink their cybersecurity approach. And recently, Biden has mandated in his 2021 Executive Order on Improving the Nation’s Cybersecurity that Federal agencies must adopt security best practices. It appears that Biden and the majority of agencies believe that advancing toward a Zero Trust architecture will help rectify the problem. The Ponemon study found 83% of agencies believe a Zero Trust architecture is important to improving their security posture. 31% of agencies surveyed have deployed a Zero Trust architecture and another 69% of agencies find their Zero Trust security architecture effective in improving their security posture.
What will it take to improve U.S. Federal cybersecurity?
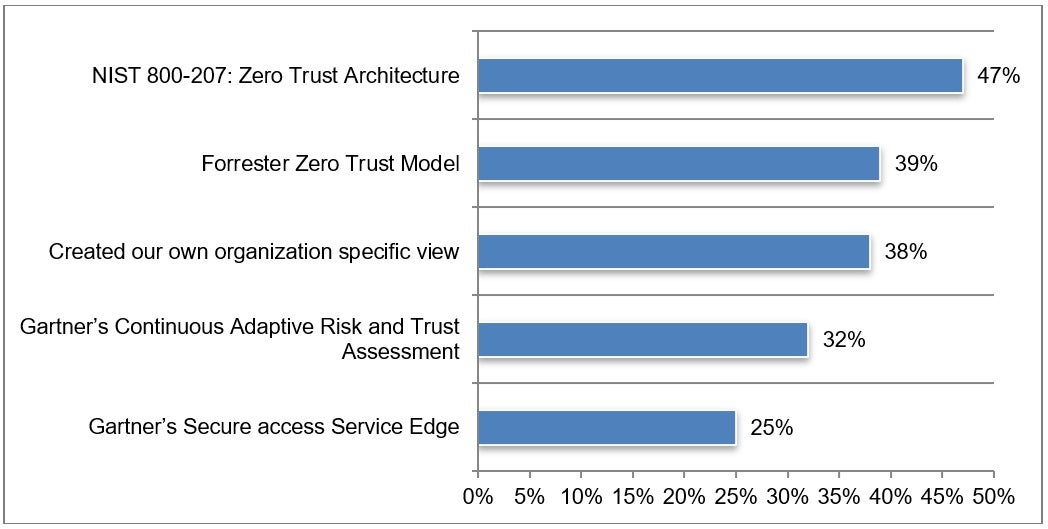
This may help to provide a standard definition and framework upon which agencies can and should build. And the good news is the majority of agencies indicated in the Ponemon study that they are relying on the NIST 800-207 Zero Trust architecture as they build out their Zero Trust solutions. While those are positive developments, the survey showed that many agencies are using multiple models to execute against their Zero Trust plans:
Previously there were quite a few models and definitions for Zero Trust that agencies have been working toward implementing. However, the EO suggests that agencies should “incorporate, as appropriate, migration steps that the National Institute of Standards and Technology (NIST)…has outlined in standards and guidance.”
61% of agencies surveyed also suggested understanding human behavior is important to proactively detect risks and secure data and human behavior. This aligns with the NIST Zero Trust tenet that states, “Access to resources is determined by dynamic policy—including the observable stateof client identity, application/service, and the requesting asset—and may includeother behavioral and environmental attributes.”
Download the full report to find more details on the specific threats agencies are seeing and for visibility into other approaches and technologies agencies are adopting to move left of breach and stay ahead of adversaries.
This post was first first published on Forcepoint website by George Kamis Biography. You can view it by clicking here

