Monitor Windows Registry Changes with Qualys File Integrity Monitoring
With Windows registries storing a large number of programs and OS security settings and a large amount of raw data, threat actors have begun to use those registries as a data store for their malicious activity. It is therefore imperative for organizations to monitor changes in Windows registries as part of their file integrity monitoring program.
The Importance of Registry Integrity Monitoring
A tactic that has been growing increasingly common is the use of registry keys to store and hide the next-step code for malware after it has been dropped on a system. Adversaries may interact with the Windows registry to hide configuration information within registry keys, remove information as a part of cleaning up, or as a part of other techniques to aid in persistence and execution.
Around 80 MITRE techniques/sub-techniques have “Windows Registry” as a data source, indicating that it covers a significant attack surface area. The registry contains the configuration information for the hardware and software and may also contain information about recently used programs and files. Footprints of an adversary having installed a program or application may also be found in the registry.
How Qualys Can Help You
The new “Monitoring Profile for Windows Registry Settings” in Qualys File Integrity Monitoring enables you to track changes in the Windows registry, so you can take proactive steps towards securing your Windows assets.
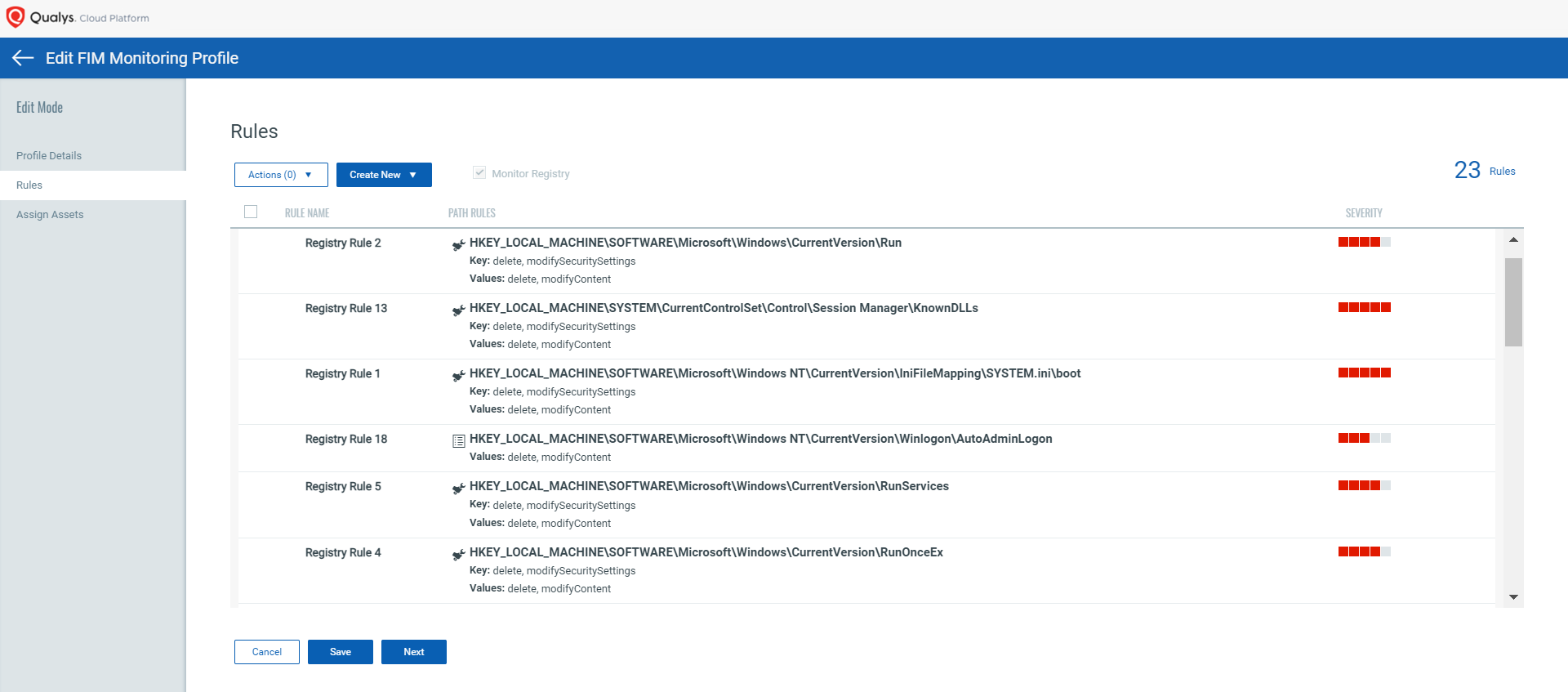
Coverage of Crucial Windows Registry Objects
The Windows registry can be compromised by storing malicious codes in the registry with Autorun capabilities, so that attacks refresh in the background even after a computer reboot.
As documented by Microsoft, “Run keys are added in the registry so that the payload runs every time the machine starts and every time a new user signs in.”
The common registry keys modified by the malware are:
- HKEY_LOCAL_MACHINESOFTWAREWOW6432NodeMicrosoftWindowsCurrentVersionRunOnceEx
- HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRunServices
- HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRunOnce
- HKEY_LOCAL_MACHINESOFTWAREWOW6432NodeMicrosoftWindowsCurrentVersionRunServices
- HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRunOnceEx
- HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRunServicesOnce
- HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionRun
- HKEY_LOCAL_MACHINESOFTWAREWOW6432NodeMicrosoftWindowsCurrentVersionRunServicesOnce
- HKEY_LOCAL_MACHINESOFTWAREWOW6432NodeMicrosoftWindowsCurrentVersionRunOnce
- HKEY_LOCAL_MACHINESOFTWAREWOW6432NodeMicrosoftWindowsCurrentVersionRun
Qualys FIM’s out-of-the-box monitoring profile includes the important registry objects to detect unauthorized changes to the autoruns, boot sequence, firewalls, and other critical functionalities. Users can easily import these profiles, assign the profiles to assets and start monitoring them. This profile is based on the recommendations provided by Microsoft and research based on CIS, DISA benchmarks.
Qualys FIM rules enable users to specify the depth they to want to traverse for real-time scans. In addition to this, inclusion/exclusion filters can be added to specify what needs to be monitored and what doesn’t, ensuring minimal load on the CPU.
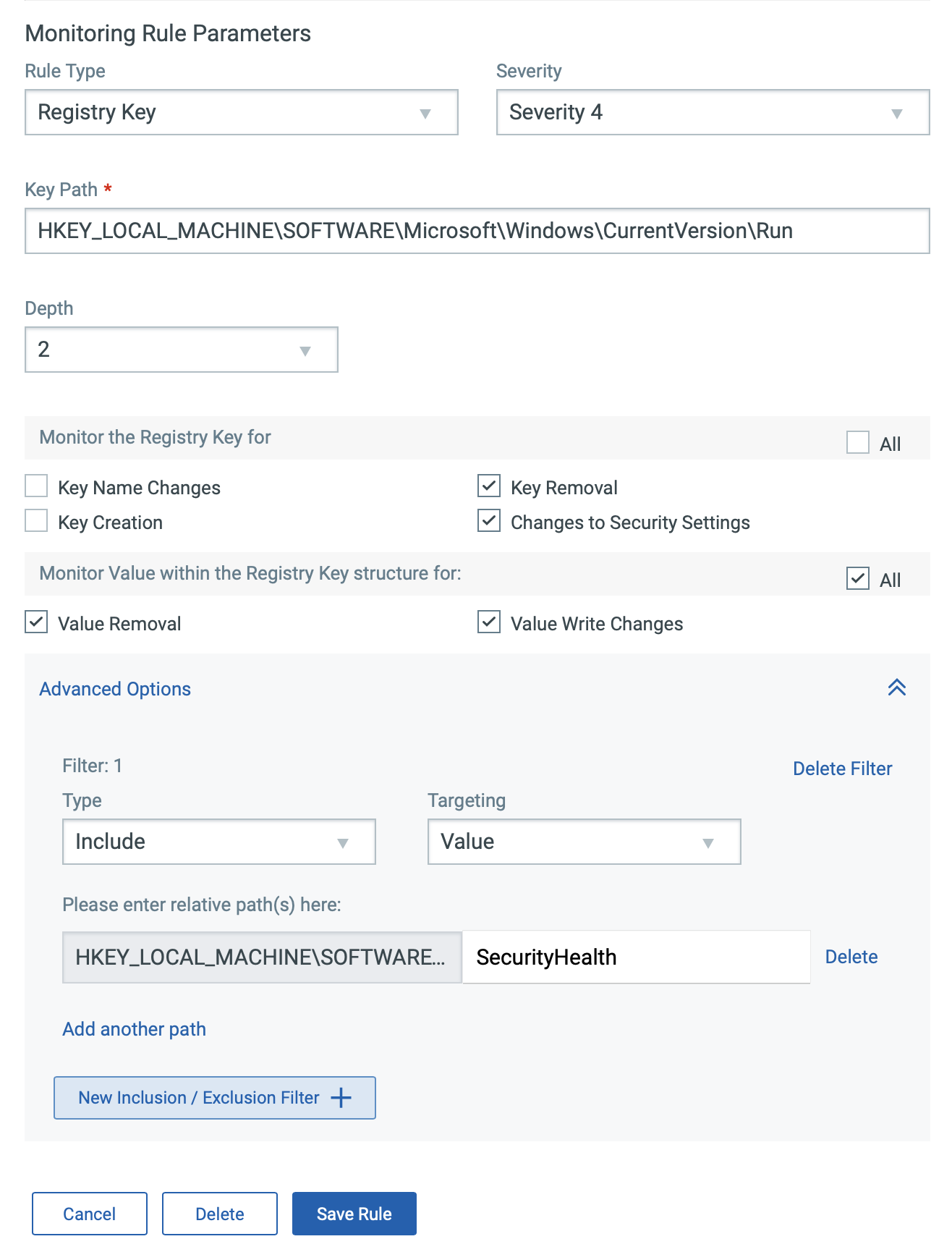
Filter, Review, and Analyze Registry Events for Unauthorized Activities
With Qualys FIM, you can quickly review the events that are generated using the appropriate query.
For example, use the following query to get a list of registry events on the Qualys Cloud Platform:
(type:Key or type:Value) and not actor .userName: 'NT AUTHORITYSYSTEM'
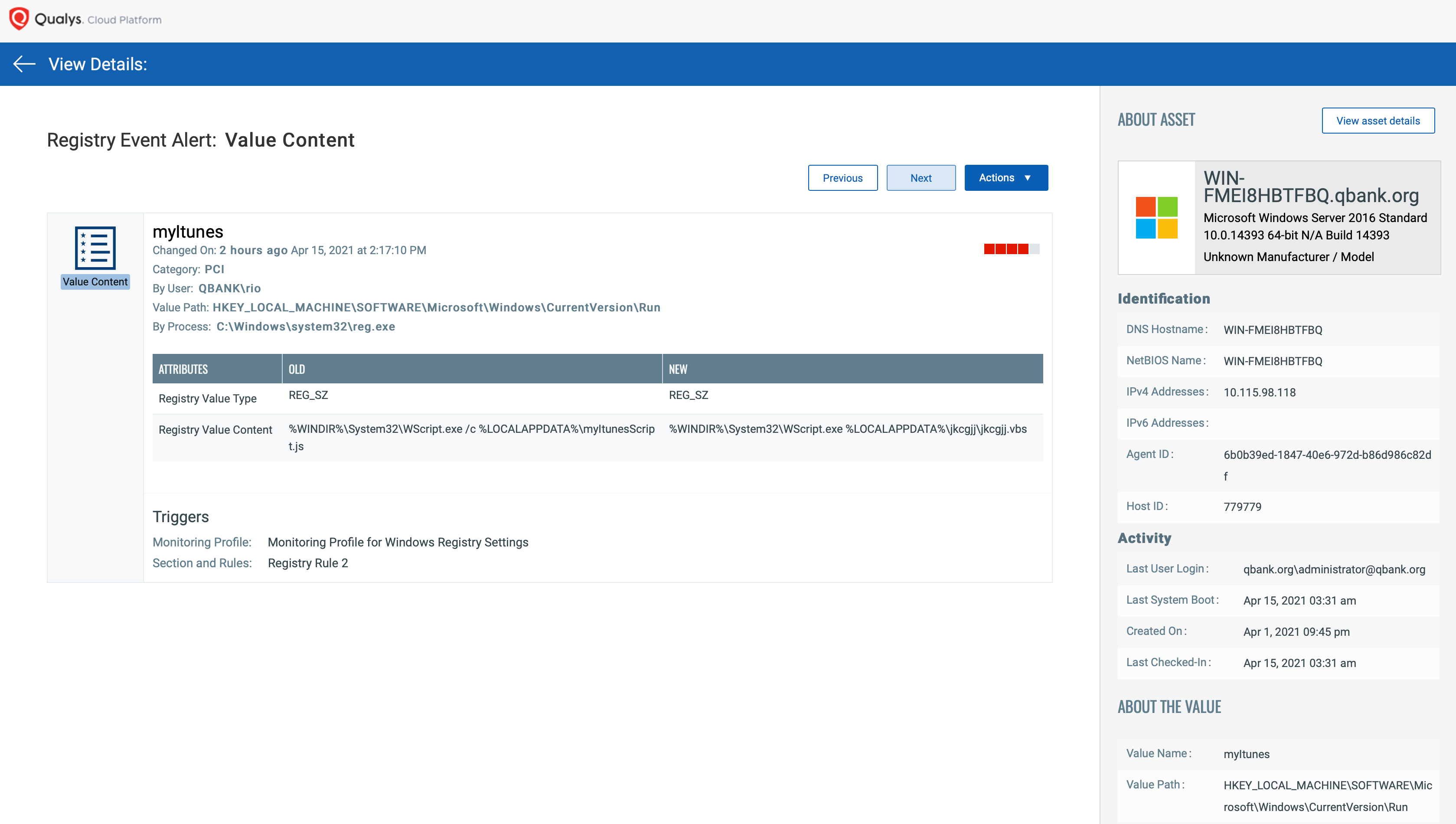
Capture Granular Event Details
Qualys FIM records all granular details along with ‘who-data’ for registry events.
In the following example, the autostart entry has been modified in the Run key to run its
malicious .vbs file with wscript.exe (Windows Script Host) at system startup as a
persistence mechanism.
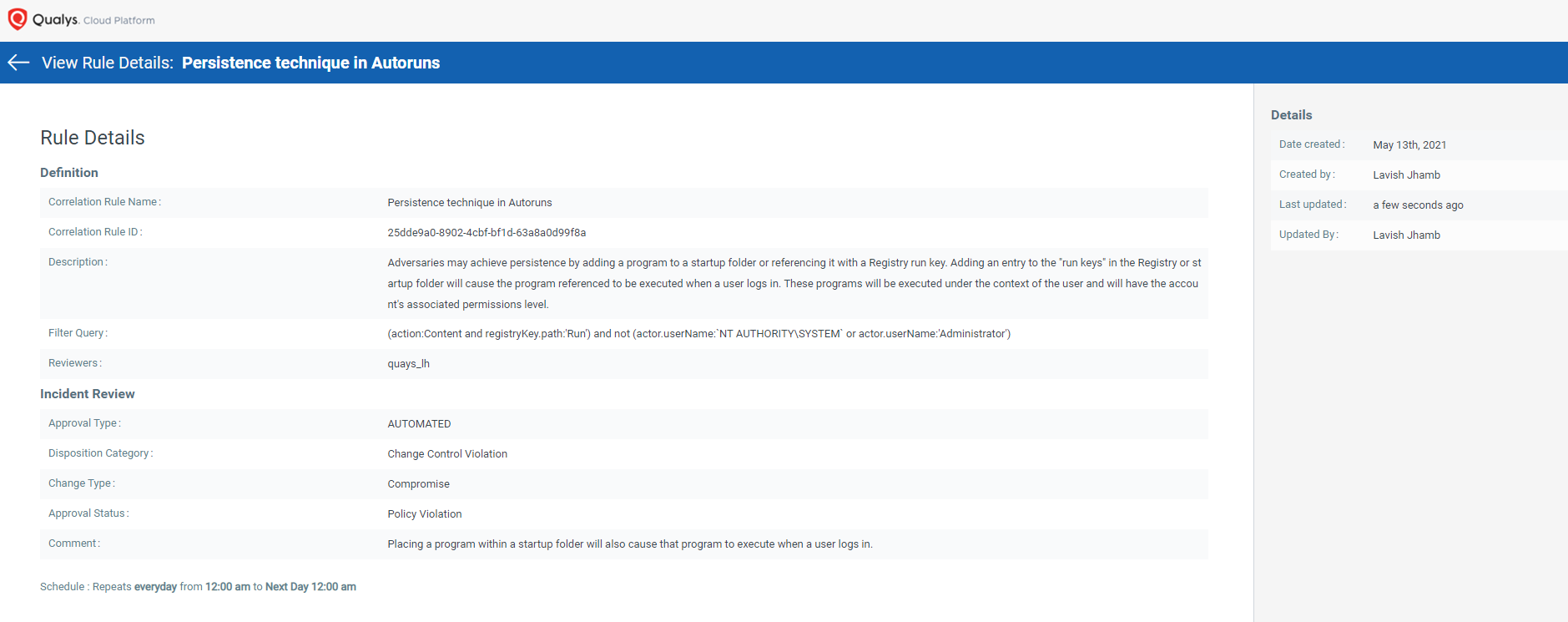
Automated Incidents and Alerts Generation
Qualys FIM generates automated incidents for unauthorized activities in the Windows registry using correlation rules.
Report or Push data to External Data Lake for Further Correlation
Export to the ELK Stack
Qualys FIM APIs are devised to enable easy custom integrations. The Rich FIM API set produces data in well-defined and structured JSON format which can be easily exported to the ELK stack.
Native Integration with Splunk
The Qualys App for Splunk Enterprise with TA provides a dashboard for FIM events data. This App is dependent on TA – Qualys Cloud Platform, which pulls and indexes the data to produce dashboards and reports. The dashboard gives quick information bites on total changes, events by severity, file and directory changes by change action. It also has widgets to show you top changes by user, process and operating system. You also have options to search for FIM events, ignored events and incidents.
Registry Monitoring to Prevent Attacks
Without effective registry monitoring, your organization’s efforts to monitor change events can never be sufficient. Qualys FIM’s enhanced threat intelligence to include monitoring capabilities for Windows registry makes sure that this powerful component of the operating system is protected from nefarious actors. Being a soft target for cybercriminals, the registry needs closer tracking methods to keep attacks at bay, and Qualys FIM enables you to achieve that with deep insight and round-the-clock tracking of events.
Resources
This post was first first published on Qualys Security Blog’ website by Lavish Jhamb. You can view it by clicking here

