Dealing with insider risk in the era of remote work
Forrester and Forcepoint together recently conducted a study to understand insider threat initiatives worldwide with 300 decision-makers.
Forrester Insider Threat Assessment
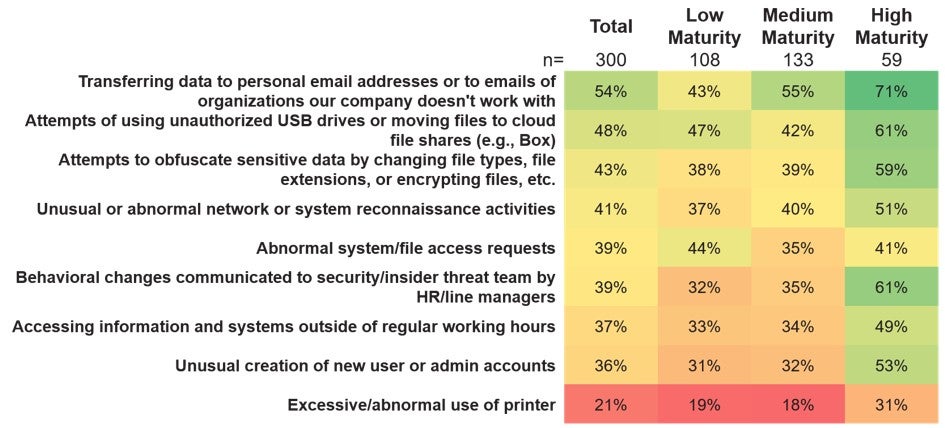
They are much more likely to collaborate with Human Resources on this front and monitor attempts to obfuscate sensitive data and abnormal network or system reconnaissance activities.
We used the results to create an insider threat maturity model that mapped various attributes to organizational capabilities. These results highlighted various strengths of high-maturity organizations e.g. these organizations using more indicators to detect insider threats.
On the other hand, a large share of companies in the low maturity category still think of themselves as mature and consider their technology effective, although many of them are lacking collaboration between stakeholders. These organizations experience difficulties setting up processes in a way that doesn’t impede employee productivity while not violating their privacy. Additionally, low maturity companies are often not able to enforce the defined policies to protect data and systems.
To ensure true data protection across endpoint, infrastructure, and cloud security, leaders not only have to provide secure access to enable work from everywhere but also understand the insider risk and adopt automated risk adaptive data protection technology that secures data at rest, in-motion, and in-use across hybrid environments.
One other insight from the survey: it is critical that organizations be transparent with their employees as they evolve their insider threat programs, including what is being monitored, what kicks off an investigation and who has access to data and how the data is used.
Take the short 5-minute self-assessment to see how your organization’s insider threat program compares to your peers. In return, you’ll receive actionable steps to advance your insider threat maturity.
This post was first first published on Forcepoint website by Ashish Malpani. You can view it by clicking here

