Home Buyers Beware – Tax-Themed Phish Hosted on Typeform
Purchasing a home can be exciting for potential buyers. However, the loan application process can at times be both stressful and exhausting as it requires a lot of correspondence between the loan applicants and lender. At times, these correspondences may take place via email. As a result, threat actors are ramping up their efforts to fool unsuspecting loan applicants. Extreme caution should be used when opening emails related to this topic.
By Ashley Atkins, Cofense Phishing Defense Center
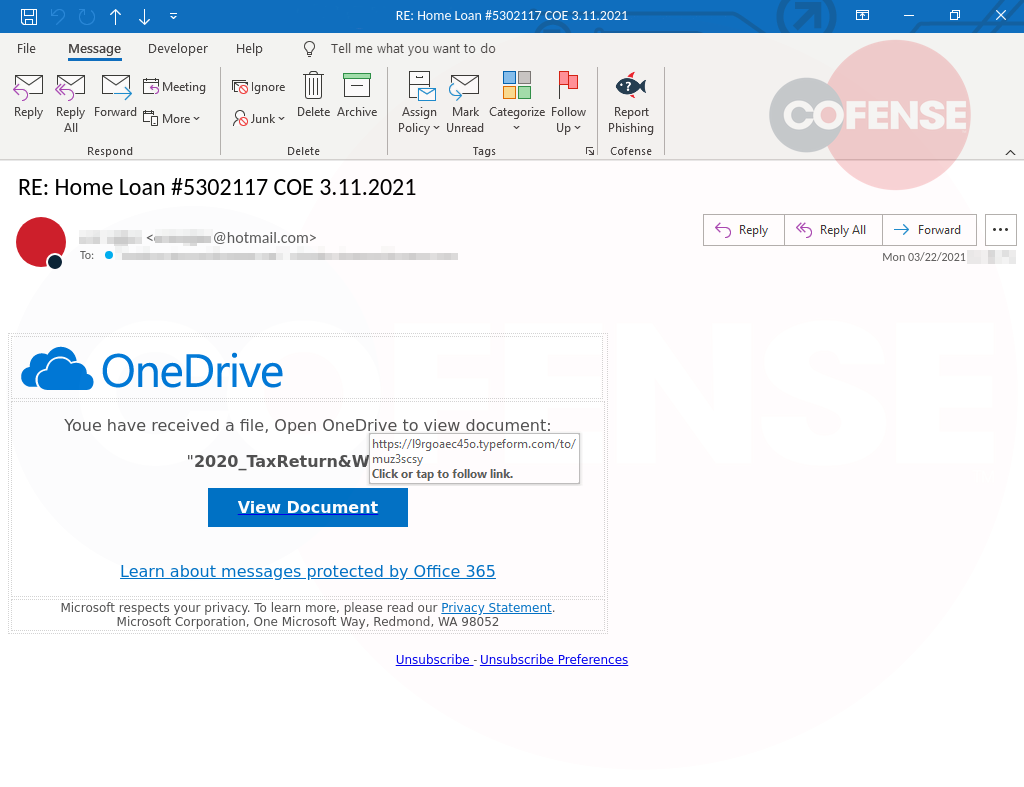
Recently, a well–conditioned user reported an email with the subject “Home Loan #5302117 COE 3.11.2021” to the Phishing Defense Center. After investigation, the email was deemed a credential phish that utilized two popular brands to lure recipients. Looking at the email body shown in Figure 1, we find that Microsoft’s OneDrive is the initial brand attackers used to trick recipients into believing that they had received a OneDrive file. The name of the file is “2020_TaxReturn&W2.pdf” which draws attention and yields an increased likelihood of interaction by the recipient. It is important to note that while W–2s and other tax–related documents may be required during the loan application process, these sensitive documents should not be sent or received via email.
When hovering over the “View Documents” button as shown in Figure 1, the destination is not a OneDrive link, as expected, but a typeform.com link:
Figure 1: Email Body
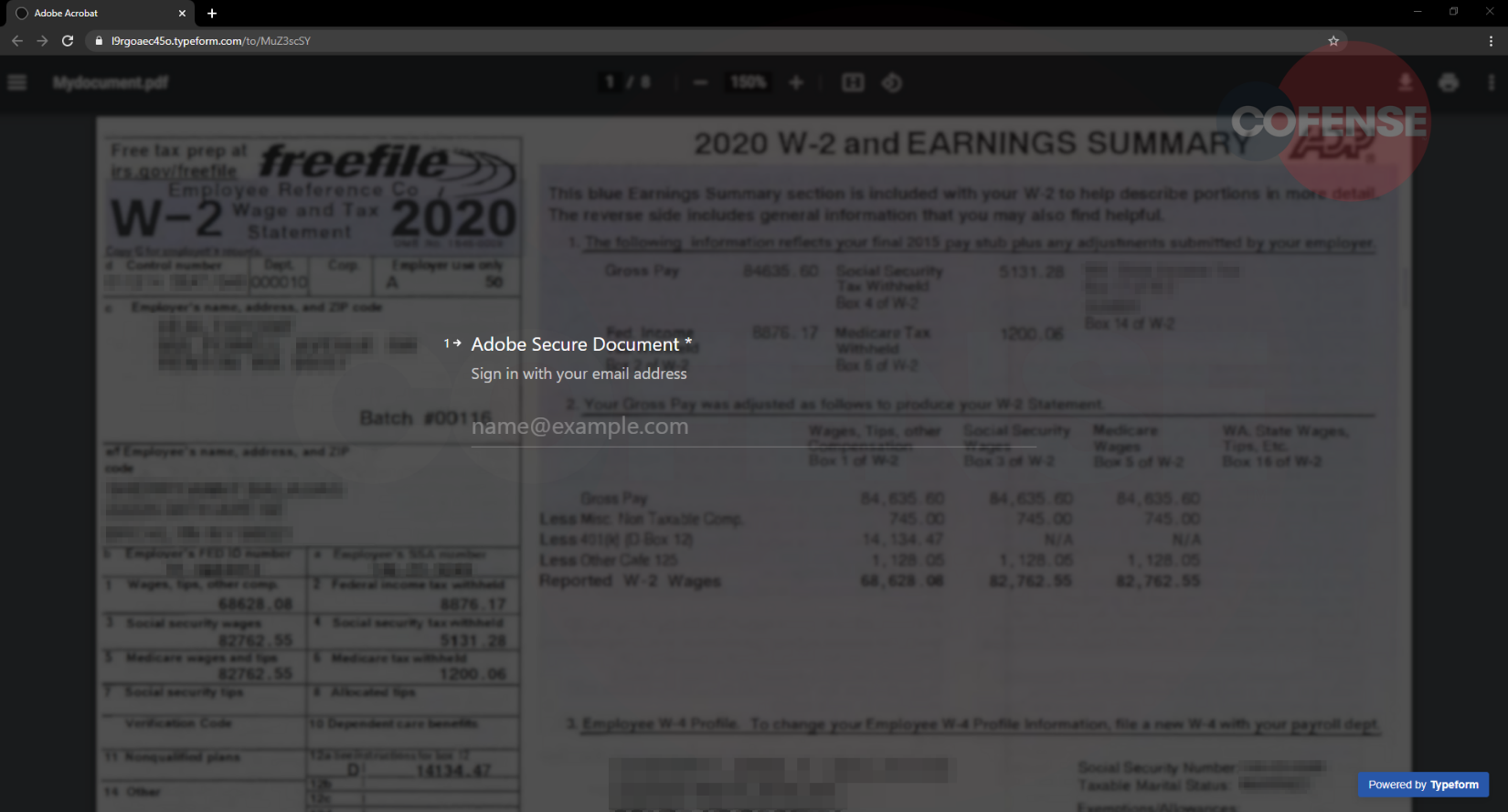 Figure 2: Phishing Page Hosted on TypeForm
Figure 2: Phishing Page Hosted on TypeForm
hxxps://l9rgoaec45o[.]typeform[.]com/to/MuZ3scSY
Creating a form is quite simple and straightforward. To set up a basic form, the content owner can insert questions along with optional descriptions and include a section for entering short answers. Instead of creating a traditional question/answer form, this threat actor intentionally made the form look like a login screen with an image of a W-2 tax form as the background (Figure 2). This was accomplished by entering “Adobe Secure Document” as a question with a description of “Sign in with your email address.” This same tactic was used for the passwords as well—Question: “Enter Password.”
After navigating to the typeform.com link, the recipients are taken to a fake Adobe login screen hosted on TypeForm, as seen in Figure 2. TypeForm is a service that allows users to create customizable forms, surveys, quizzes and more for free, making it attractive for phishing purposes.
If an email address is entered, the subsequent questions as shown in Figures 3 and 4 request a password. After submitting a password once (Figure 3), it is requested again (Figure 4) but this time with a description suggesting that the password entered previously was invalid. This may cause the user to think that they mistakenly mistyped their password. In actuality, the attacker is using this verification step to confirm the password is correct. This is a common tactic used by threat actors to increase the legitimacy of the input form. After the password is entered a second time, a “View Document” button appears. When the button is clicked, the form is submitted, and the responses are sent to the threat actor.
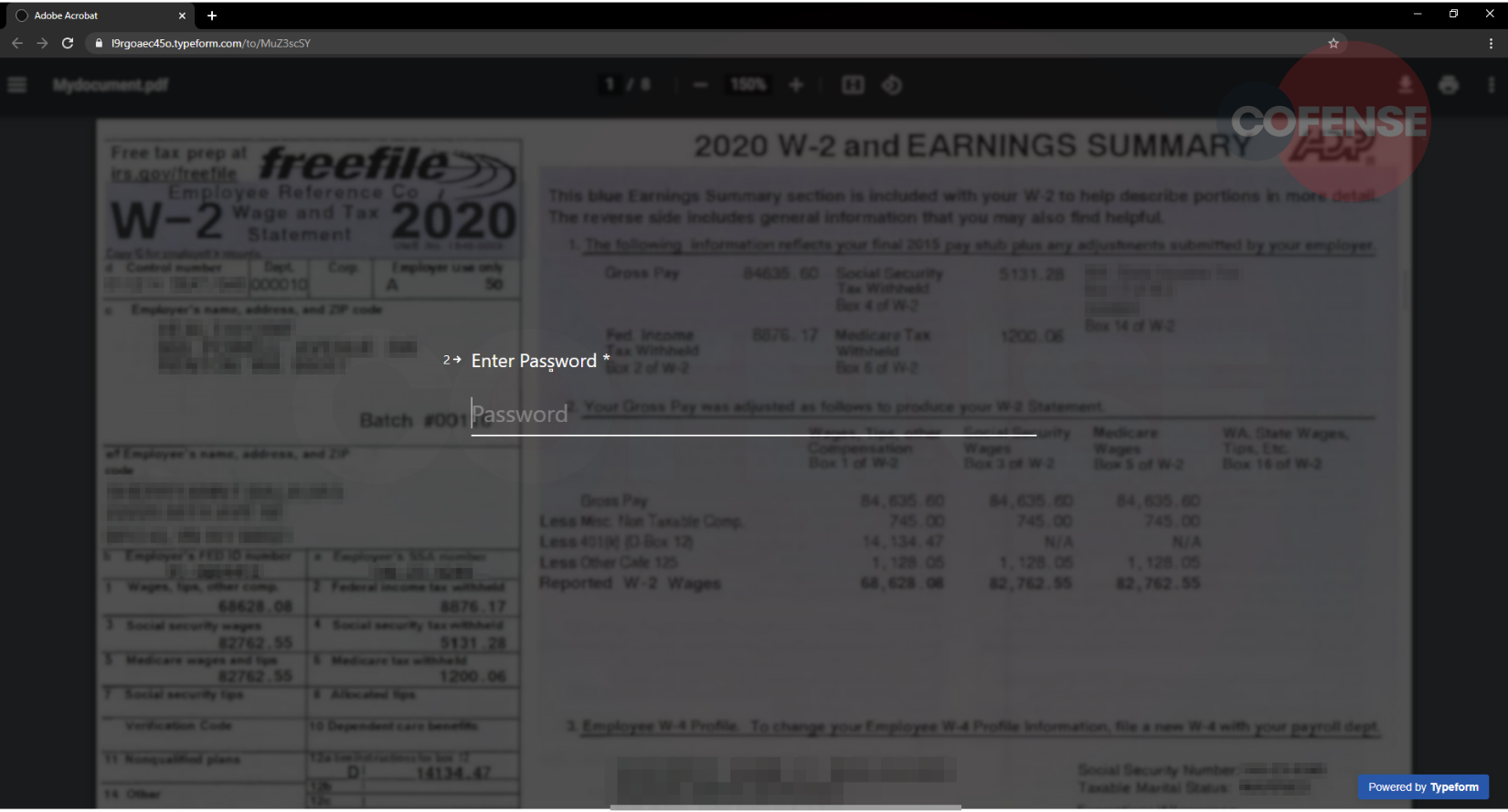
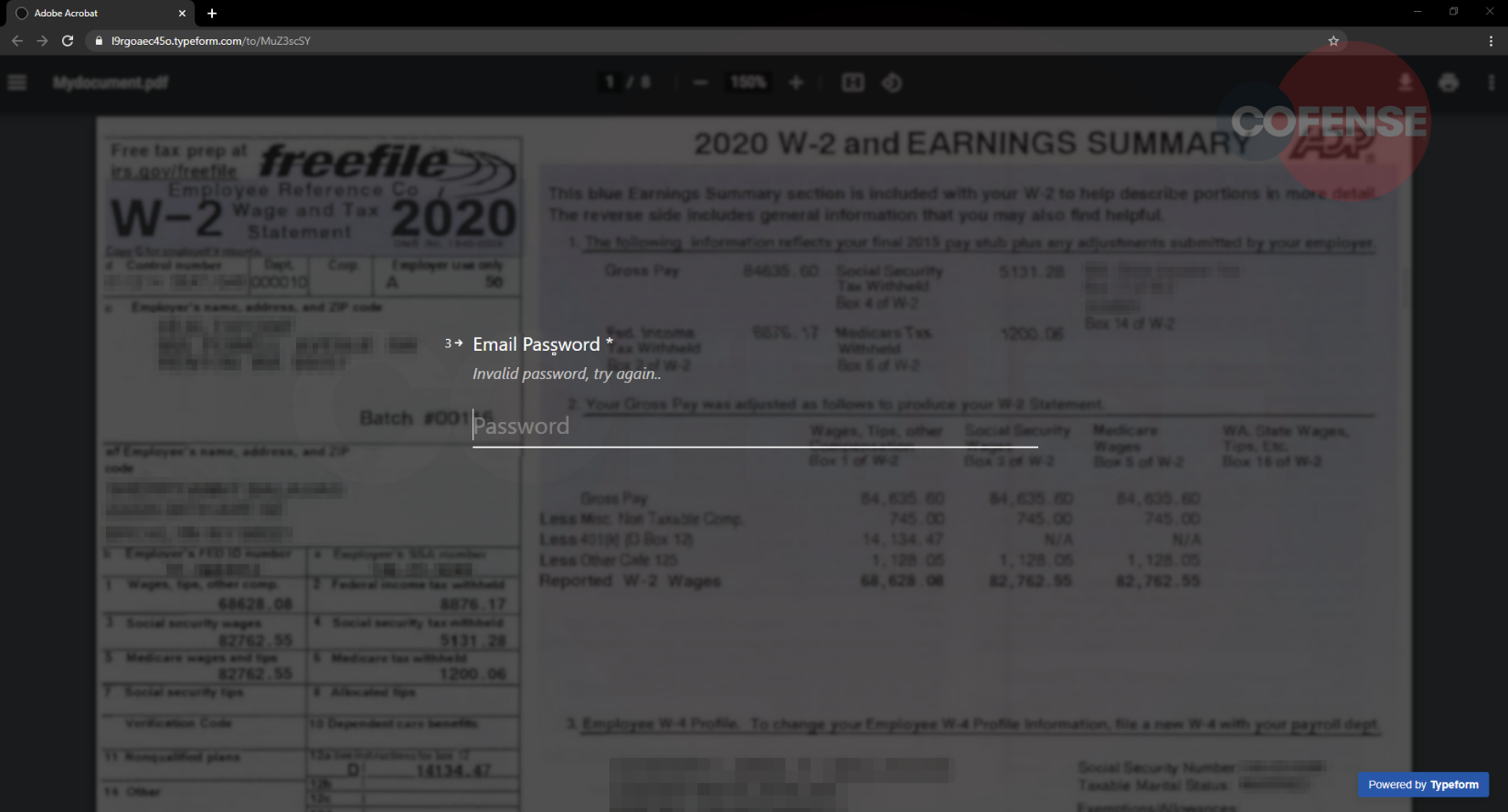 Figure 3-4: Stage 2 of the Attack
Figure 3-4: Stage 2 of the Attack
Once the credentials are obtained, the next page shown in Figure 5 displays “This document is secured” with a description claiming that the user’s identity could not be verified. This may cause the user to revisit the typeform.com phishing link and re-enter their credentials multiple times giving the threat actors further verification of their email and password.
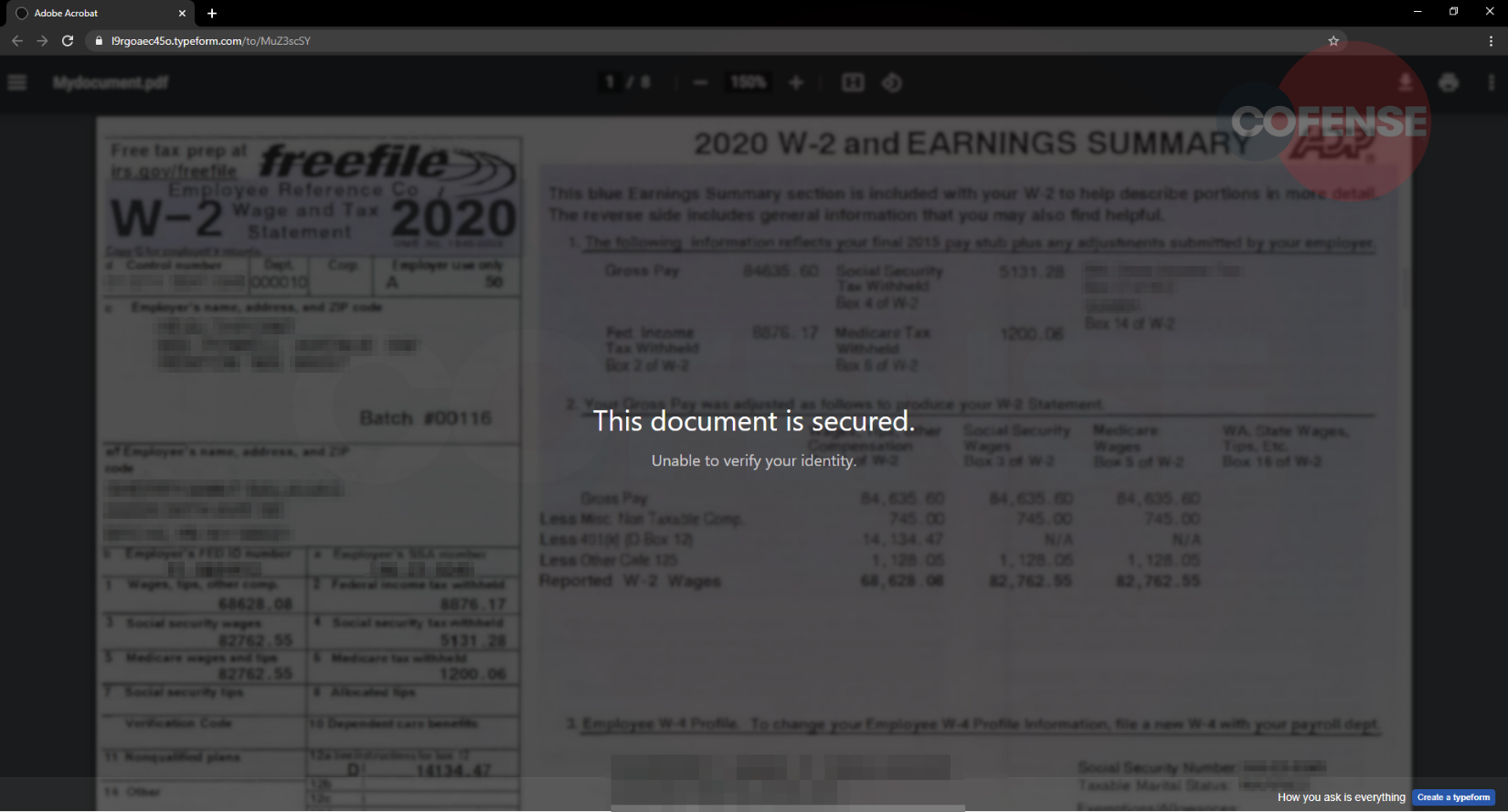 Figure 5: Final Step of Attack
Figure 5: Final Step of Attack
| Indicators of Compromise | IP |
| hxxps://l9rgoaec45o[.]typeform[.]com/to/MuZ3scSY | 104.18.27.71
104.18.26.71 As noted in previous blogs, and specifically this campaign, threat actors are always crafting their attacks around topics or events of interest in order to stay topical with users. In this case, the threat actor has even gone as far as to utilize a W-2 to further sell the illusion of relevance to their home loan. This particular recipient recognized that the email was suspicious and reported it via the Cofense Reporter where the Phishing Defense Center leveraged Cofense Triage to swiftly take action. |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats. Past performance is not indicative of future results.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.
This post was first first published on Cofense’s website by Cofense. You can view it by clicking here

