Why MITRE ATT&CK Matters?
To enable practitioners in operationalizing these strategies, the knowledge base provides the “why” and the “what” with comprehensive documentation that includes the descriptions and relational mappings of the behaviors observed by the execution of malware, or even when those weapons were used by known adversaries in their targeting of different victims as reported by security vendors. It goes a step further by introducing the “how” in the form of adversary emulation plans which streamline both the design of threat-models and the necessary technical resources to test those models – i.e., emulating the behavior of the adversary

MITRE ATT&CK enterprise is a “knowledge base of adversarial techniques”. In a Security Operations Center (SOC) this resource is serving as a progressive framework for practitioners to make sense of the behaviors (techniques) leading to system intrusions on enterprise networks. This resource is centered at how SOC practitioners of all levels can craft purposeful defense strategies to assess the efficacy of their security investments against that knowledge base.
This approach is transformative for cyber security, it provides an effective way to evolve from constraints of being solely dependent on IOC-centric or signature-driven defense models to now having a behavior-driven capability for SOCs to tailor their strategic objectives into realistic security outcomes measured through defensive efficacy goals. With a behavior-driven paradigm, the emphasis is on the value of visibility surrounding the events of a detection or prevention action taken by a security sensor – this effectively places context as the essential resource a defender must have available to pursue actionable outcomes.
For scenarios where SOCs may not have the capacity to do this testing themselves, the MITRE Corporation conducts annual evaluations of security vendors and their products against a carefully crafted adversary emulation plan, and it publishes the results for public consumption. The evaluations can help SOC teams assess both strategy concerns and tactical effectiveness for their defensive needs as they explore market solutions.
| Detection | Gives SOC Analysts higher event actionability and alert handling efficiencies with a focus on most prevalent adversarial behaviors – i.e., let’s tackle the alert-fatigue constraint! |
| Prevention | Gives SOC Leaders/Sponsors confidence to show risk reduction with minimized impact/severity from incidents with credible concerns – e.g., ransomware or destructive threats. |
| Response | Gives SOC Responders a capacity to shorten the time between detection and activating the relevant response actions – i.e., knowing when and how to start containing, mitigating or eradicating. |
| Investigative | Gives SOC Managers a capability to improve quality and speed of investigations by correlating low signal clues for TIER 1 staff and streamlining escalation processes to limited but advanced resources. |
| Hunting | Enables SOC Hunters a capacity to rewind-the-clock as much as possible and expand the discovery across environments for high value indicators stemming from anomalous security events. |
Cool! So what is this “efficacy” thing all about?
I believe that to achieve meaningful security outcomes our products (defenses) must demonstrate how effective they are (efficacy) at enabling or preserving the security mission we are pursuing in our organizations. For example, to view efficacy in a SOC, let’s see it as a foundation of 5 dimensions:
Strategy (Investment) |
Portfolio Focus |
Efficacy Goals |
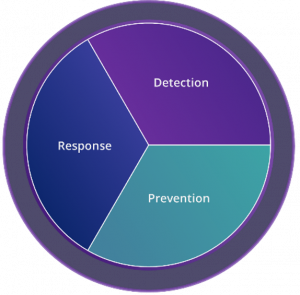 |
Balanced Security |
Ability to:
Caveats: So how does “efficacy” relate to my SOC?Efficacy at the Security and Technical Leadership levels confirms how the portfolio investments are expected to yield the defensive posture of our security strategy, for example, compare your investments today to any of the following:
|
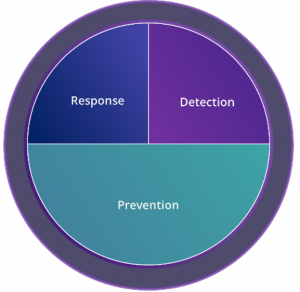 |
Prevention Focus |
Ability to:
Caveats:
|
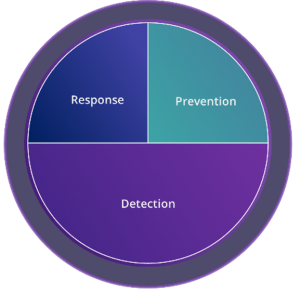 |
Detection Focus |
Ability to:
Caveats:
|
- Hard to implement across the business without disrupting user experience and productivity
- Typically for regulated or low tolerance network zones like PCI systems
- Needs high TCO for the management of prevention products
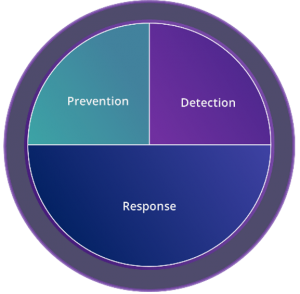
Response Focus
- Respond effectively to different scenarios identified by products or reported to the SOC
Caveats:
Consequently, it allows practitioners to overcome crucial limitations from the reliance on indicator-driven defense models that skew realistic efficacy goals, thereby maximizing the value of a security portfolio investment.
MITRE ATT&CK matters as it introduces the practical sense-making SOC professionals need so they can discern attack chains versus security events through visibility of the most prevalent behaviors.
The post Why MITRE ATT&CK Matters? appeared first on McAfee Blogs.
This post was first first published on Enterprise – McAfee Blogs’s website by Carlos Diaz. You can view it by clicking here

