Up and Coming Phishing Campaign Is Taxing to Users
With U.S. tax season upon us, it’s time to remind our users to watch for emails hitting their inboxes related to tax documents. Threat actors are tuned to the seasonal theme to lure users. The Cofense Phishing Defense Center (PDC) has observed a new phishing campaign that steals Microsoft credentials by acting as a file share from the U.S. Internal Revenue Service.
By Ashley Tran, Cofense Phishing Defense Center
Figure 1 Email Body
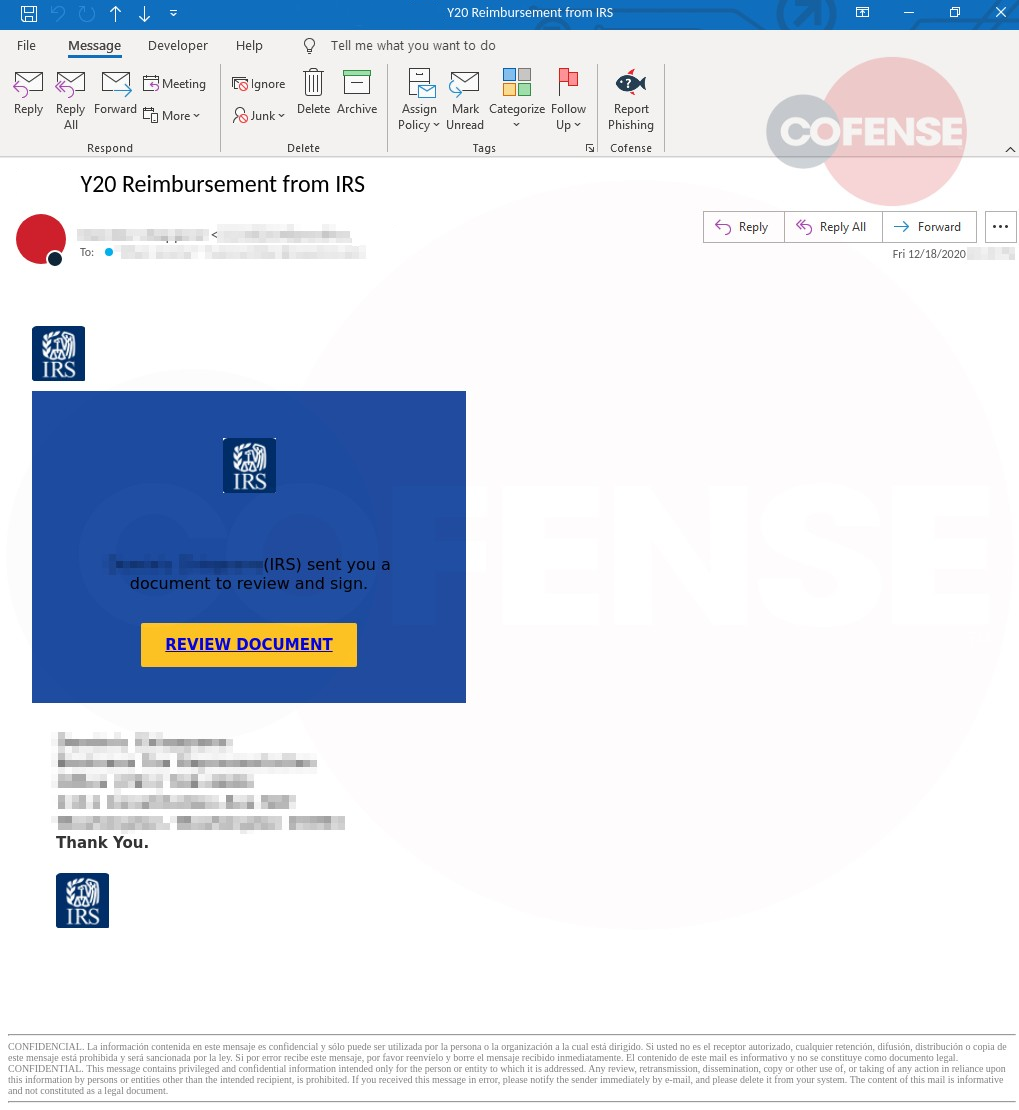
For this attack, the threat actor has spoofed both email and sender information. The email appears to come from a government website, and the “from” name is that of an actual IRS tax representative. Should a recipient attempt to verify the sender’s identity, they’ll find a corresponding LinkedIn profile.
To begin with, the subject of the phishing email, “Y20 Reimbursement from IRS,” is topical given the current tax year, and is sure to draw attention.
The use of redirect links as shown above has become increasingly common with such phishing campaigns. Hovering over the “Review Document” button reveals the destination is embedded into a redirect link:
The email body, seen in Figure 1, is similar to other document–sharing messages. It particularly resembles DocuSign with its blue background and yellow “Review Document” button.
The final URL users would be redirected to when clicking the button is: hXXps://quip[.]com/9IvtAsTmnGGb
hXXps://t[.]yesware[.]com/tt/54912e30621e9039398d9d491631724ad94e5bcb/9308138a9b8ab6ba555023132ac7eee6/e580d1654666d58406f070acdce3bbb7/internal-revenue-service.quip.com/9IvtAsTmnGGb/Internal-Revenue-Service-2020-Reimbursement
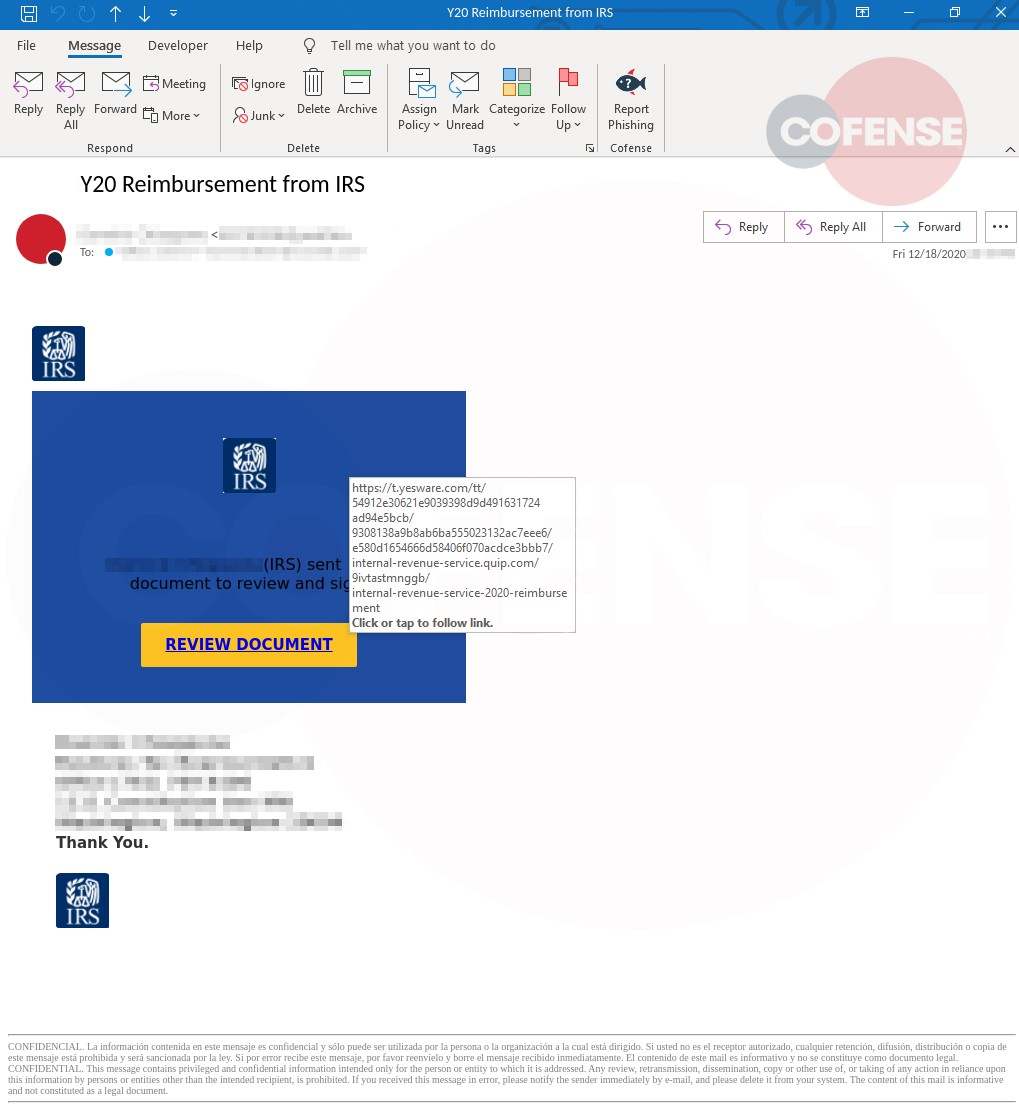
The corresponding page for this URL is shown in Figure 2.
For this attack, the threat actor has utilized Quip[.]com’s collaborative document feature to host a document with the title “Internal Revenue Service (2020 Reimbursement)” directing the recipient to click. It includes the readily recognizable IRS logo.
Figure 2: Secondary Lure Page
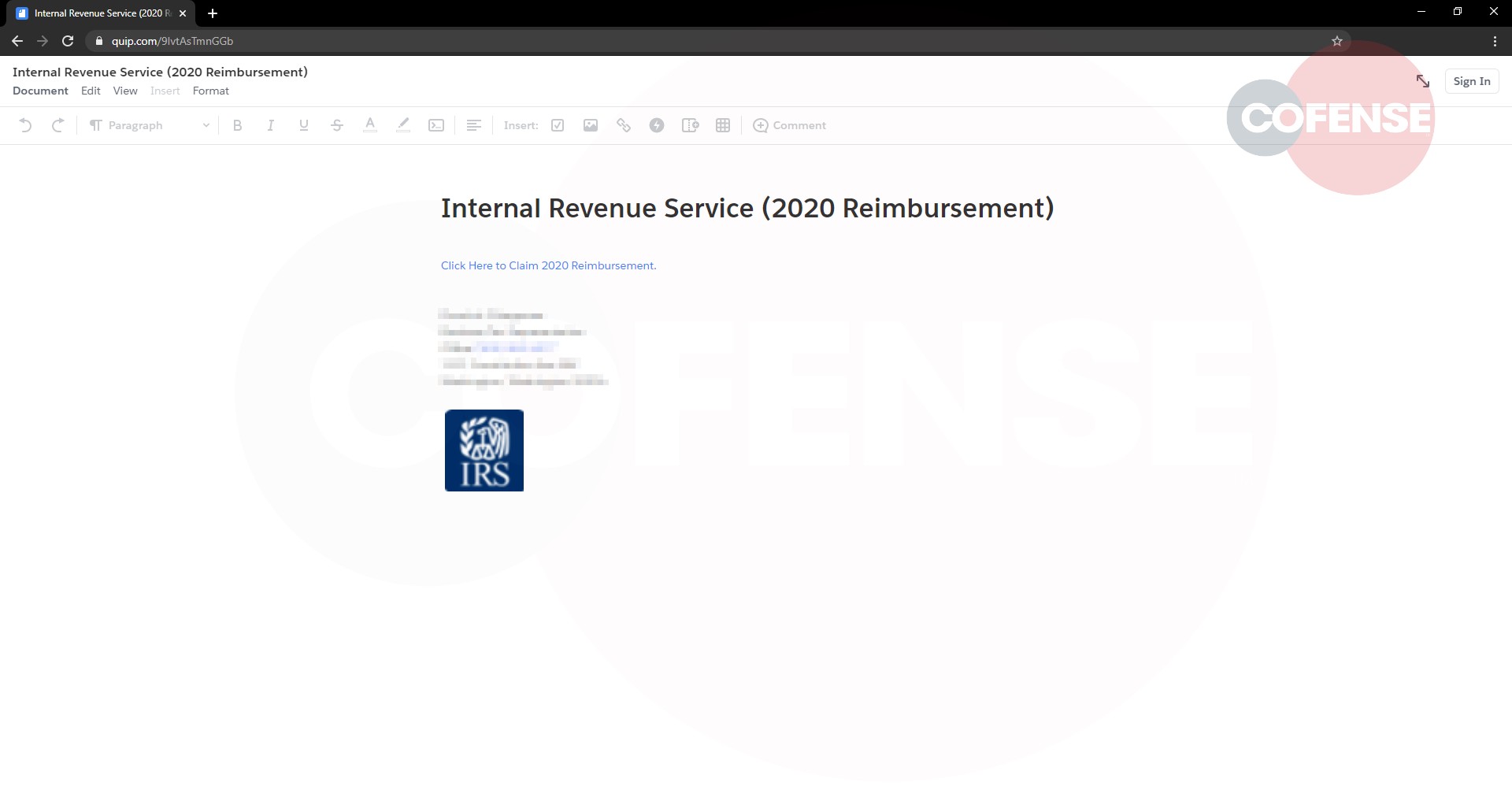
Upon clicking the link to “Claim 2020 Reimbursement,” users are redirected to the start of a Microsoft phish seen in Figures 3-4.
Figure 3–4: Phishing Page
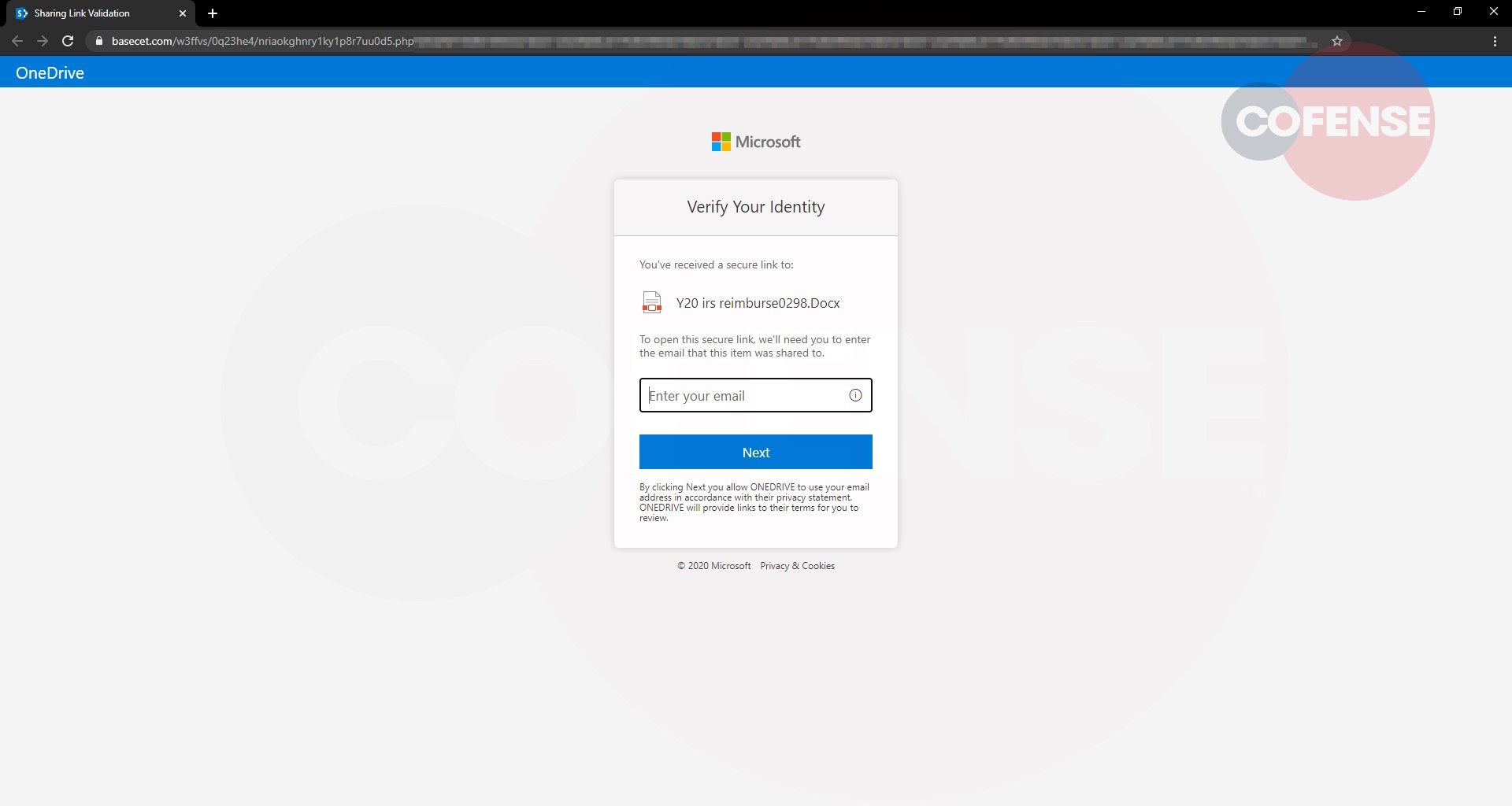
Figure 4, the last stop in the attack, shows a generic Microsoft login page prompting for the user’s password; the email address provided from the previous step appears in the login box above it.
Figure 3 shows the first step of the attack which imitates a typical Microsoft SharePoint page that verifies the identity of users before they can access a document for their eyes only. On this page, users are prompted for their email address and then redirected to the final step of the attack.
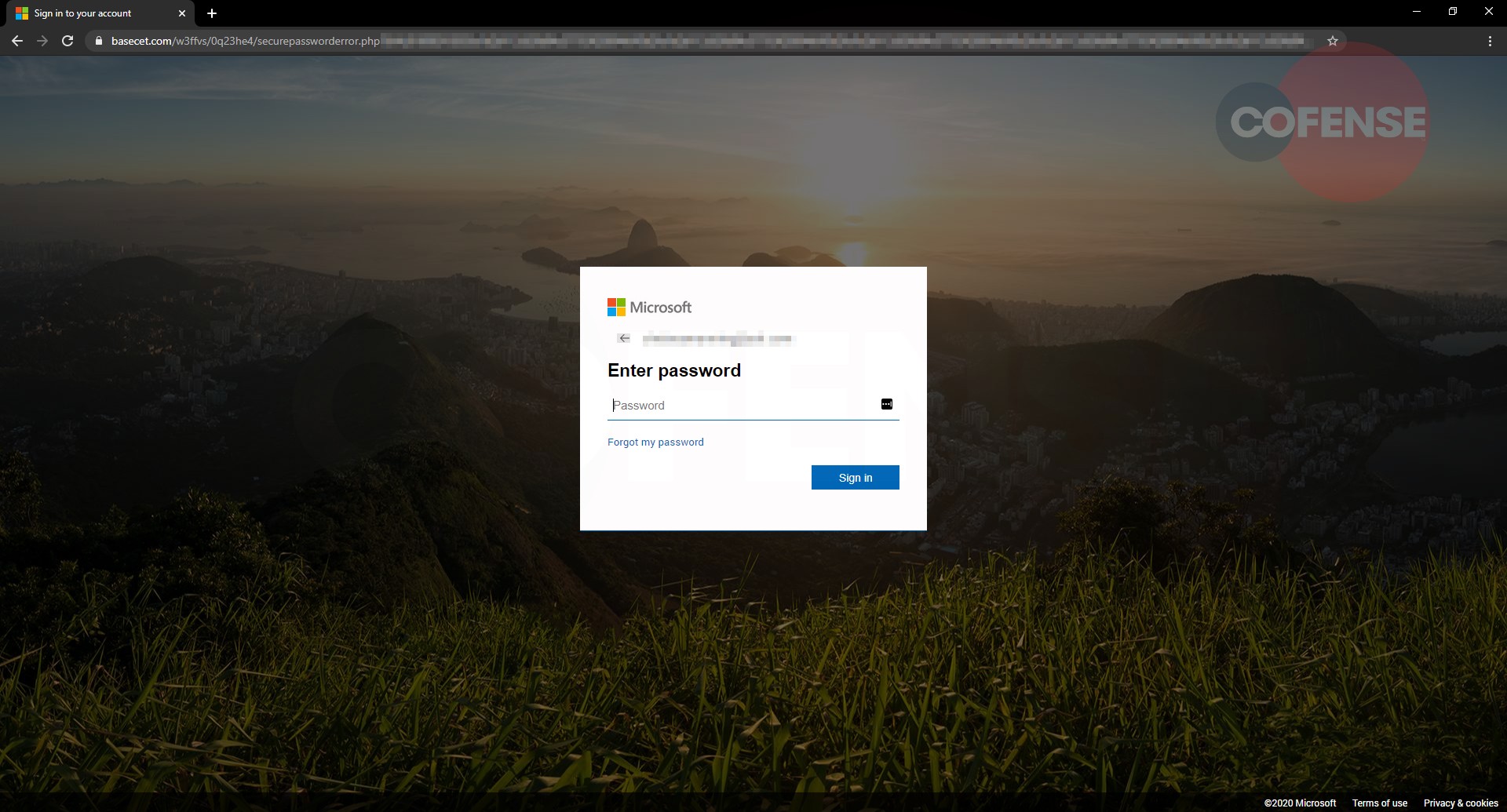
After entering their password, users are prompted to re-enter their password, another common tactic threat actors use to obtain an additional password. Users are then redirected to a legitimate Microsoft Office error page as seen in Figure 5. This is also a tactic commonly used by threat actors to ward of suspicion and distract users from the credential harvesting.
Indicators of Compromise
Figure 5: Error Page
| hXXps://t[.]yesware[.]com/tt/54912e30621e9039398d9d491631724ad94e5bcb/9308138a9b8ab6ba555023132ac7eee6/e580d1654666d58406f070acdce3bbb7/internal-revenue-service.quip.com/9IvtAsTmnGGb/Internal-Revenue-Service-2020-Reimbursement | 35.239.71.225 |
| hXXps://quip[.]com/9IvtAsTmnGGb | 50.112.33.205 |
| hXXps://basecet[.]com/w3ffvs/0q23he4/nriaokghnry1ky1p8r7uu0d5.php | 162.0.232.161 |
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.
This post was first first published on Cofense’s website by Cofense. You can view it by clicking here

