Hacking Proprietary Protocols with Sharks and Pandas
This course of events demands that both offensively and defensively minded “good guys” band together to remove the unknown from as much technology as possible. One of the most common unknown pieces of technology in cybersecurity that professionals see on a regular basis are proprietary protocols running across their networks. By using both the tactics and perspectives from red and blue teams it is possible to conquer and understand these previously unknown packets. This strategy is exactly what we, Douglas McKee and Ismael Valenzuela, hoped to communicate in our webinar ‘Thinking Red, Acting Blue: Hacking Proprietary Protocols”.

The human race commonly fears what it doesn’t understand. In a time of war, this fear is even greater if one side understands a weapon or technology that the other side does not. There is a constant war which plagues cybersecurity; perhaps not only in cybersecurity, but in the world all around us is a battle between good and evil. In cyber security if the “evil” side understands or pays more attention to a technology than the “good” side, we see a spike in cyber-attacks.
During the webinar we discussed a two-prong approach to tackling these unknown protocols with the goal of a deeper understanding of this data. A red team’s purpose may be to look for vulnerabilities, while a blue team may be more interested in detecting or flagging unusual behavior in this traffic. We discuss how this can be accomplished through visual inspection using Wireshark to compare the traffic across multiple conversations, and we complemented this analysis with python libraries like pandas, numpy and matplotlib, for data exploration and visualization.
Proprietary protocols are typically a mystery to many practitioners. Vendors across many industries develop them for very specific purposes and technologies. We see them in everything from the Internet of Things (IOT), to Industrial Controls Systems (ICS), to medical devices and more. Since by its nature “proprietary” technology is not shared, there is generally no public Request for Comments (RFC) or public disclosure on how they work. This provides an opportunity for attackers and a challenge for defenders. Attackers are aware these networking protocols are less reviewed and therefore more susceptible to vulnerabilities, while defenders have a hard time understanding what valid or benign traffic looks like. Unfortunately, attackers are generally more financially motivated to spend the time reversing these protocols than defenders, since the rewards can be very substantial.
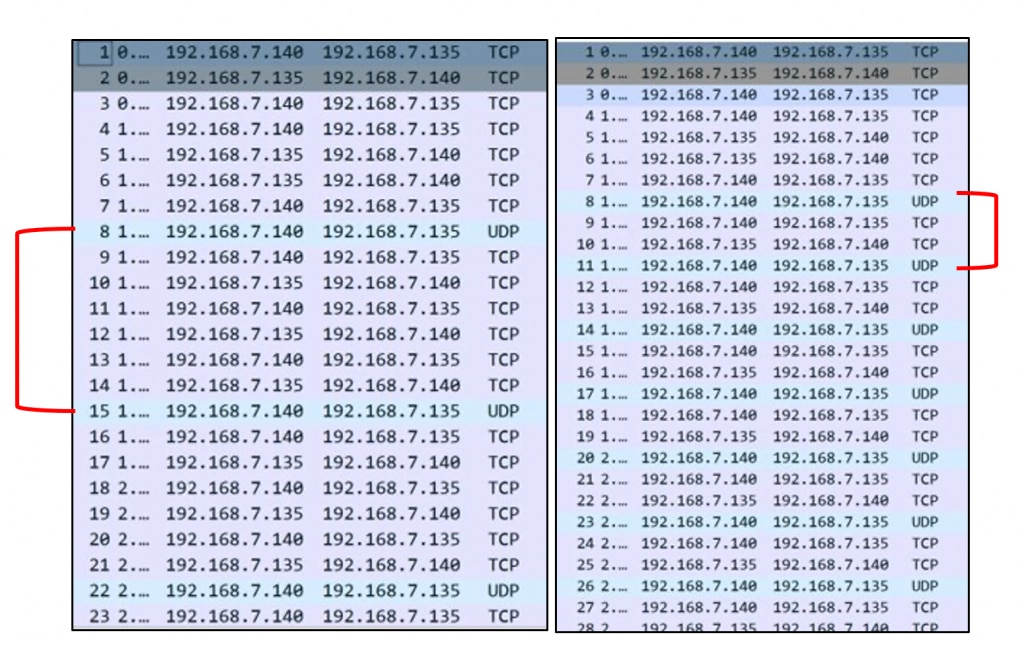
For example, consider the packets in the Wireshark captures side-by-side in Figure 1. An astute reader may notice that the UDP packets are evenly spaced between each other within the same PCAP, yet differently spaced between pcaps.
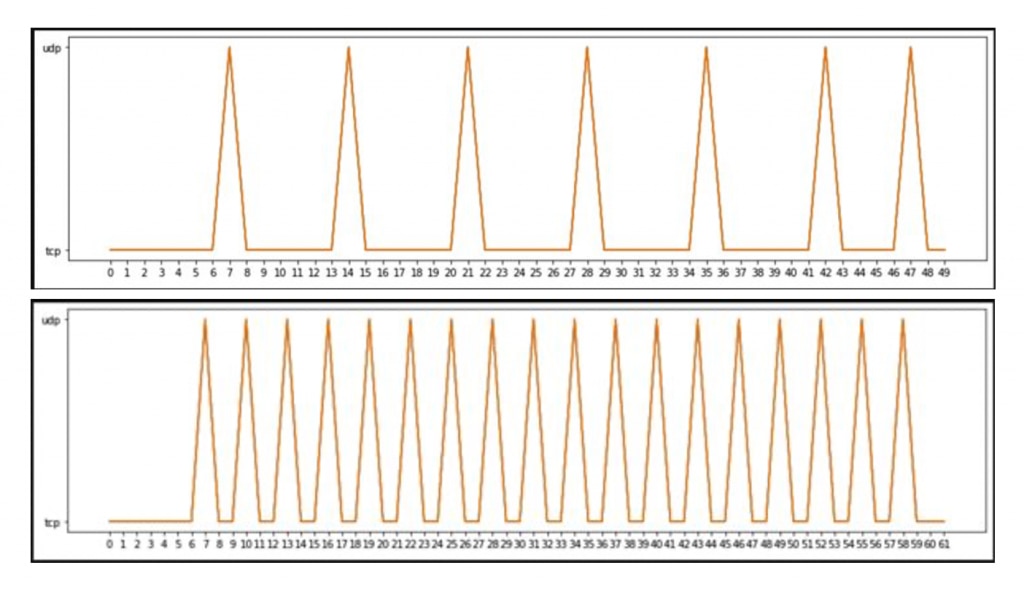
In protocol analysis this can indicate the use of a status or “heartbeat” packet, which may contain some type of data where the interval it is sent is negotiated for each conversation. We have seen this as a common trait in proprietary protocols. This can be difficult for a cybersecurity professional to discern with a small amount of data, but could be very helpful for further analysis. If we import the same data into pandas dataframes and we add matplotlib visualizations to our analysis, the behavior becomes much clearer as seen in Figure 2.
By using the reverse engineering perspective of a vulnerability researcher combined with the data analysis insight of a defender, we can strengthen and more quickly understand the unknown. If this type of deep technical analysis of proprietary protocols interests you, we encourage you to check out the recording of our presentation below. We have made all of our resources public on this topic, including pcaps and python code in a Jupyter Notebook, which can be found on Github and Binder. It is important as an industry that we don’t give into fear of the unknown or just ignore these odd looking packets on our network, but instead lean in to understand the security challenges proprietary protocols can present and how to protect against them.
The post Hacking Proprietary Protocols with Sharks and Pandas appeared first on McAfee Blogs.
This post was first first published on Enterprise – McAfee Blogs’s website by Ismael Valenzuela. You can view it by clicking here

