XDR – Please Explain?
Security vendors have spent the last two decades providing more of the same orchestration, detection, and response capabilities, while promising different results. And as the old adage goes, doing the same thing over and over again whilst expecting different results is…? I’ll let you fill in the blank yourself.

SIEM, we need to talk!
Albert Einstein once said, “We cannot solve our problems with the same thinking we used when we created them”.
The expanding attack surface, which now spans Web, Cloud, Data, Network and more, has also added a layer of complexity. The security industry cannot only rely on its customers’ analysts to properly configure a security solution with such a wide scope. Implementing only the correct configurations, fine-tuning hundreds of custom log parsers and interpreters, defining very specific correlation rules, developing necessary remediation workflows, and so much more – it’s all a bit too much.
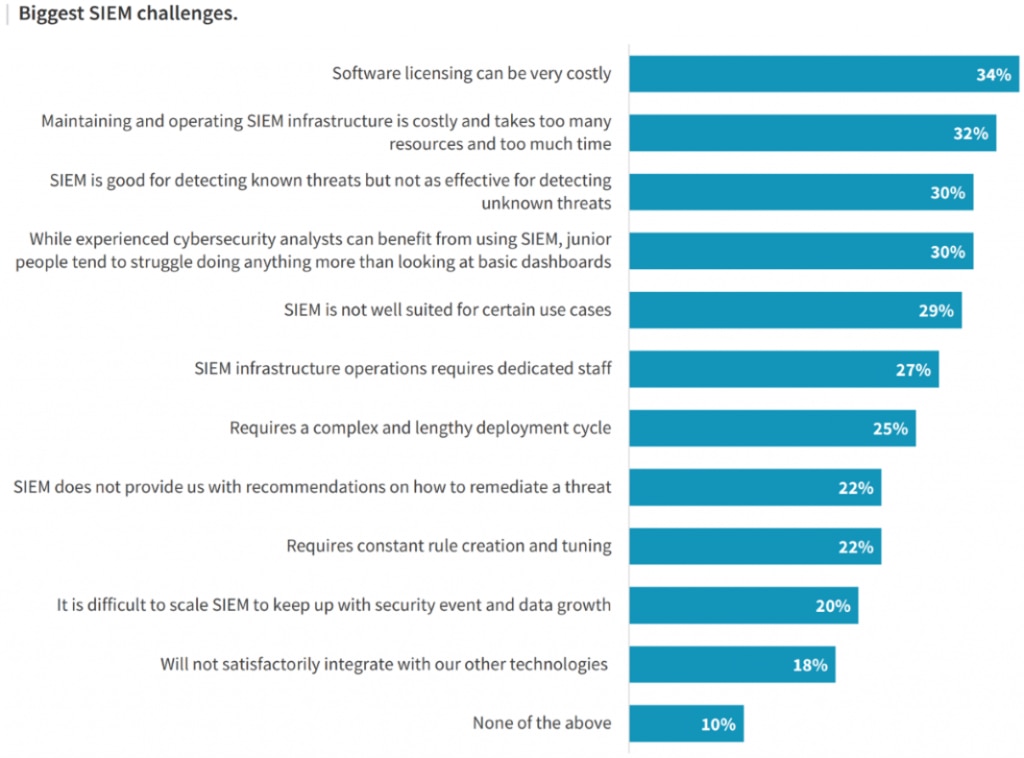
SIEM! SOAR! Next Generation SIEM! The names changed, while the same fundamental challenges remained: they all required heavy lifting and ongoing manual maintenance. As noted by ESG Research, SIEM – being a baseline capability within SOC environments – continues to present challenges to organisations by being either too costly, exceedingly resource intensive, requiring far too much expertise, and various other concerns. A common example of this is how SOC teams still must create manual correlation rules to find the “bad” connections between logs from different products, applications and networks. Too often, these rules flooded analysts with information and false alerts and render the product too noisy to effective.
There is also no ‘R’ in SIEM – that is, there is no inherent response built into SIEM. You can almost liken it to a fire alarm that isn’t connected to the sprinklers.
Detections now bubble up from many siloed tools, too, including Intrusion Prevention Systems (IPS) for network protection, Endpoint Protection Platforms (EPP) deployed across managed systems, and Cloud Application Security Broker (CASB) solutions for your SaaS applications. Correlating those detections to paint a complete picture is now an even bigger challenge.
Now, Endpoint Detection and Response (EDR) solutions are absolutely on the right track – enabling analysts to sharpen their skills through guided investigations and streamline remediation efforts – but it ultimately suffers from a network blind spot. Similarly, network security solutions don’t offer the necessary telemetry and visibility across your endpoint assets.
SIEMs have been the foundation of security operations for decades, and that should be acknowledged. Thankfully, they’re now being used more appropriately, i.e. for logging, aggregation, and archiving.
That sounds awfully similar to SIEM, so how is an XDR any different from all the previous security orchestration, detection, and response solutions?
Considering the alternatives
Of Gartner’s Top 9 Security and Risk Trends for 2020, “Extended detection and response capabilities emerge to improve accuracy and productivity” ranked as their #1 trend. They noted, “Extended detection and response (XDR) solutions are emerging that automatically collect and correlate data from multiple security products to improve threat detection and provide an incident response capability…The primary goals of an XDR solution are to increase detection accuracy and improve security operations efficiency and productivity.”
SIEMs are data-driven, meaning they need data definitions, custom parsing rules and pre-baked content packs to retrospectively provide context. In contrast, XDR is hypothesis driven, harnessing the power of Machine Learning and Artificial Intelligence engines to analyse high-fidelity threat data from a multitude of sources across the environment to support specific lines of investigation mapped to the MITRE ATT&CK framework.
The answer is: An XDR is a converged platform leveraging a common ontology and unifying language. An effective XDR must bring together numerous heterogeneous signals, and return a homogenous visual and analytical representation.. XDR must clearly show the potential security correlations (or in other words, “attack stories”) that the SOC should focus on. Such a solution would de-duplicate information on one hand, but would emphasize the truly high-risk attacks, while filtering out the mountains of noise. The desired outcome would not require exceeding amounts of manual work; allowing SOC analysts to stop serving as an army of “translators” and focus on the real work – leading investigations and mitigating attacks. This normalized presentation of data would be aware of context and content, be advanced technologically, but simple for analysts to understand and act upon.
XDR isn’t a single product. Rather, it refers to an assembly of multiple security products (and services) that comprise a unified platform. An XDR approach will shift processes and likely merge and encourage tighter coordination between different functions like SOC analysts, hunters, incident responders and IT administrators.
The MITRE ATT&CK framework is effective at highlighting “how bad guys do what they do, and how they do it.” While traditional prevention measures are great at “spot it and stop it” protections, MITRE ATT&CK demonstrates there are many steps taking place in the attack lifecycle that aren’t obvious. These actions don’t trigger sufficient alerting to generate the confidence required to support a reaction.
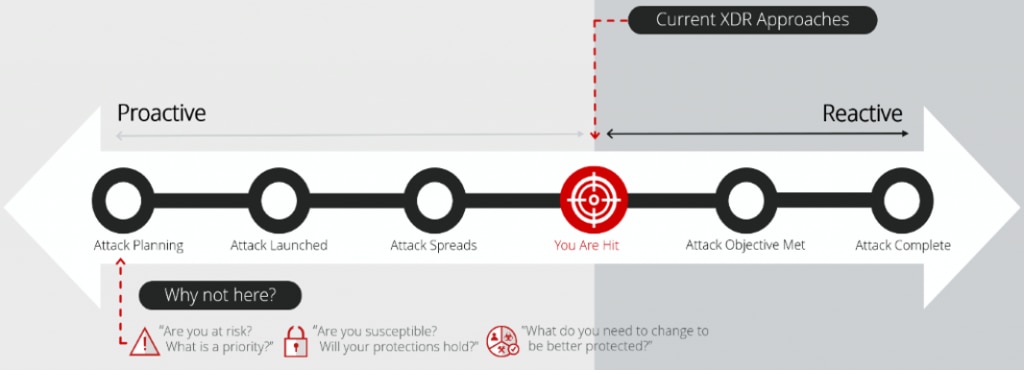
McAfee’s MVISION XDR solution does just that, by empowering the SOC to do more with unified visibility and control across endpoints, network, and cloud. McAfee XDR orchestrates both McAfee and non-McAfee security assets to deliver actionable cyber threat management and support both guided and automated investigations.
The ideal XDR solution must provide enhanced detection and response capabilities across endpoints, networks, and cloud infrastructures. It needs to prioritise and predict threats that matter BEFORE the attack and prescribe necessary countermeasures allowing the organisation to proactively harden their environment.
“Many firms want to be more proactive but do not have the resources or talent to execute. McAfee can help bridge this gap by offering organisations a global outlook across the entire threat landscape with local context to respond appropriately. In this way, McAfee can support a CISO-level strategy that combines risk and threat operations.”
What if you could find out if you’re in the crosshairs of a top threat campaign, by using global telemetry from over 1 billion sensors that automatically tracks new campaigns according to geography and industry vertical? Wouldn’t that be insightful?
But, hang on… Is this all just another ‘platform’ play?
– John Oltsik, ESG Senior Principal Analyst and Fellow
Over the past decade, the security industry proposed solving many of the challenges presented in SOC contexts through integrations. You would buy products from a few different vendors, who promised it would all work together through API integration, and basically give you some form of pseudo-XDR outcomes we’re exploring here.
Take a moment to consider how ‘platform’ offerings have evolved over the years. Initially designed to compensate for the heterogeneity and volume of internal data sources and external threat intelligence feeds, the core objective has predominantly been to manifest data centrally from across a range of vectors in order to streamline security operations efforts. We then saw the introduction of case management capabilities.
And what about the lack of any shared ontology, meaning little to no common objects or attributes? There were no shared components, such as UI/UX, incident management, logging, dashboards, policy definitions, user authentication, etc.
Frankly, there are significant limitations in that approach. There is no data persistence; you basically make requests to the lowest API denominator on a one-to-one basis. The information sharing model was a one-way ‘question and answer’ leveraging a scheduled push-pull methodology. The other big issue was the inability to pull information in whatever form – you were limited to the API available between the participating parties, with the result ultimately only as good as the ‘dumbest’ API.
Is XDR, then, a solution or product to be procured? Or just a security strategy to be adopted? Potentially, it’s both. Some vendors are releasing XDR solutions that complement their portfolio strengths, and others are just flaunting XDR-like capabilities.
What’s desperately been needed is an open underlying platform – essentially like a universal API gateway scaled across the cloud that leverages messaging fabrics like DXL that facilitate easy bi-lateral exchange between many security functions – where vendors and partner technologies create tight integrations and synergies to support specific use cases benefitting SOC ecosystems.
For most organisations, XDR will be a journey, not a destination. Their ability to become more effective through XDR will depend on their maturity and readiness to embrace all the required processes. In terms of cybersecurity maturity, if you’d rate your organisation at a medium to high level, the question becomes how and when.
Closing Thoughts
SIEMs still deliver specific outcomes to organisations and SOCs, which cannot be replaced by XDR. In fact, with XDR, a SIEM can be even more valuable.
If you’d like to know more about how McAfee addresses these challenges with MVISION XDR, feel free to reach out!
Most organisations using an Endpoint Detection and Response (EDR) solution are likely quite ready to embrace XDR’s capabilities. They are already investigating and resolving endpoint threats and they’re ready to expand this effort to understand how their adversaries move across their infrastructure, too.
The post XDR – Please Explain? appeared first on McAfee Blogs.
This post was first first published on Enterprise – McAfee Blogs’s website by Rodman Ramezanian. You can view it by clicking here

