Emotet Disrupted but Likely to Return
Background
Originally a banking Trojan, Emotet evolved to become more of a gateway for other malware families such as Ryuk, TrickBot, and QakBot. For the last few years, it has been among the top producers of malicious emails, using innovative and regularly updated techniques. For example, recently it harvested email reply chains from victims, and used those to create effective lures to send to the victims’ contacts. It also uses several tactics to avoid detection, such as delivery via password-protected zip file attachments and hosting itself on a large collection of legitimate but compromised websites. Emotet’s authors have shown remarkable patience and willingness to experiment and innovate: the botnet regularly ceases spam activity for weeks or months, during which time the authors issued updates to existing installations.
By Brad Haas, Cofense Threat Intelligence
Operation LadyBird
On January 27, authorities from eight countries conducted a disruption operation against Emotet. According to the Europol press release, the action—named Operation LadyBird—targeted several hundred servers worldwide. Authorities took over Emotet’s primary servers, which give updates to infected computers. They issued an update that replaces the list of Emotet command-and-control (C2) servers with a list of C2 servers under law enforcement control. Ukrainian police also identified two Emotet operators, from whom they seized cash, computers and other associated equipment. Finally, Dutch authorities recovered a trove of data stolen from Emotet victims, including email addresses, user names and passwords. They published a website allowing users to check whether their email address was in the compromised data.
What Happens Next
Although Operation LadyBird had an immediate and substantial impact on Emotet operations, we assess that the botnet will likely return within the year. Despite the arrests in Europe, the threat actors ultimately in charge of Emotet remain at large. It is possible that they will simply retire, but even in that case the remnants of the botnet and the business relationships with other malware operators would likely be passed on to others. Emotet has been so effective that abandoning it entirely would very likely represent a lost opportunity for considerable profit.
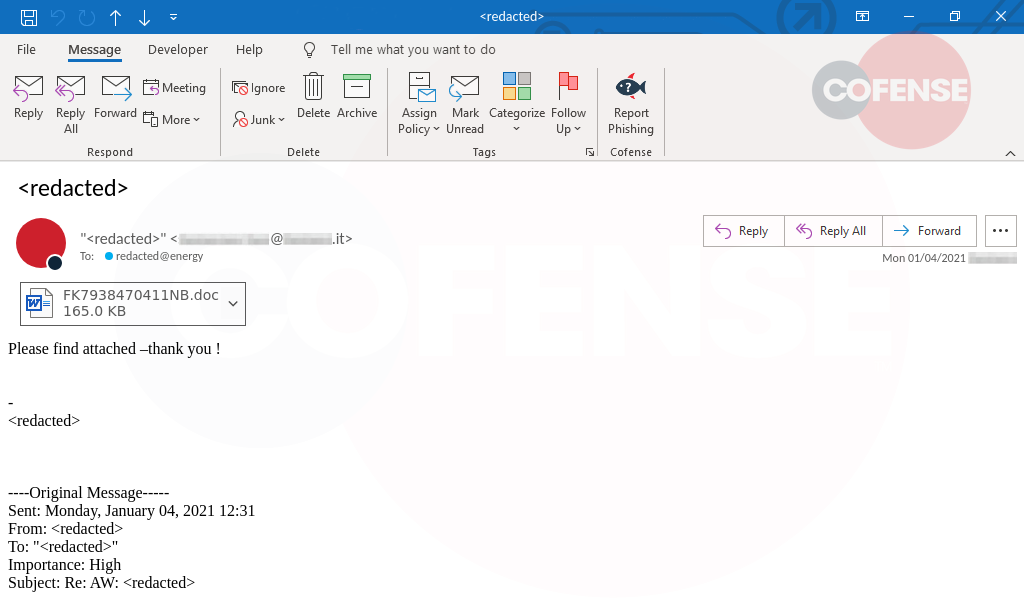
Figure 1: An Emotet email, with an attached malicious Miscrosoft Office document, found in an environment protected by Microsoft Office 365 Advanced Threat Protection.
Note to Cofense Intelligence customers: You can refer to our July 2020 Flash Alert and our December 2020 Flash Alert for more details on previous Emotet lulls.
TrickBot survived a similar takedown in October 2020—it was built with a backup C2 configuration that allowed it to return to operation within a few weeks. Emotet has no such backup, but its operators can likely leverage its operators’ close relationship with the operators of TrickBot and other families to regain a broad base of installations on infected computers. Emotet’s operators also very likely have copies of the compromised data seized by the authorities, and there may be other data sets that were not seized. As we discussed above, they were already in the habit of taking long breaks in order to make improvements. We assess that they will likely withdraw again for at least a few months and improve their infrastructure to be more resilient against future law enforcement action, and then begin rebuilding their botnet.
All third-party trademarks referenced by Cofense whether in logo form, name form or product form, or otherwise, remain the property of their respective holders, and use of these trademarks in no way indicates any relationship between Cofense and the holders of the trademarks. Any observations contained in this blog regarding circumvention of end point protections are based on observations at a point in time based on a specific set of system configurations. Subsequent updates or different configurations may be effective at stopping these or similar threats.
The Cofense® and PhishMe® names and logos, as well as any other Cofense product or service names or logos displayed on this blog are registered trademarks or trademarks of Cofense Inc.
This post was first first published on Cofense’s website by Cofense. You can view it by clicking here

